HackTheBox Challenge Fishy HTTP (Forensics)
Writeup for HackTheBox Challenge Fishy HTTP
Challenge Synopsis
I found a suspicious program on my computer making HTTP requests to a web server. Please review the provided traffic capture and executable file for analysis. (Note: Flag has two parts) (Source)
Solution
1
2
❯ ls
'Fishy HTTP.zip' smphost.exe sustraffic.pcapng
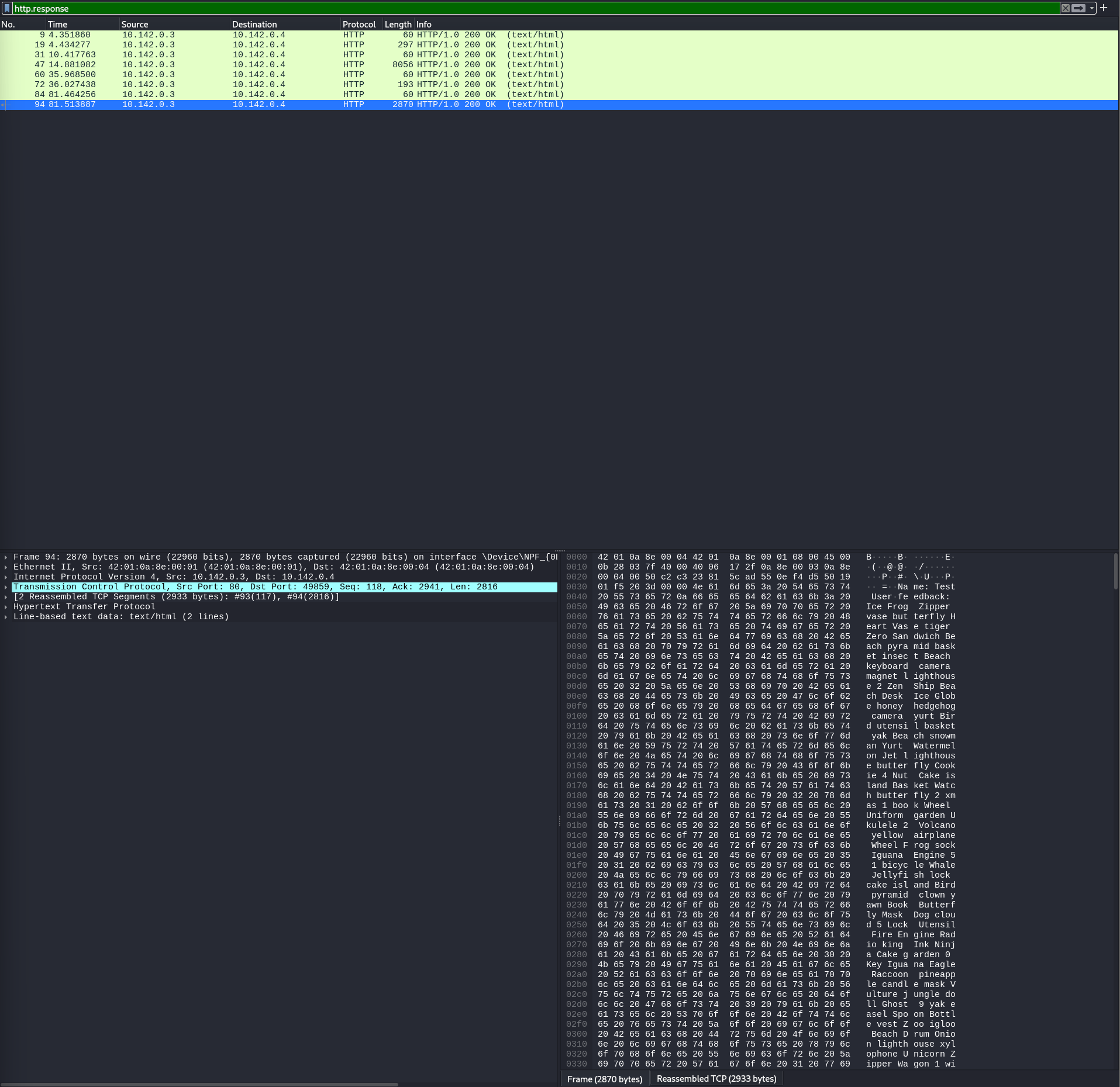
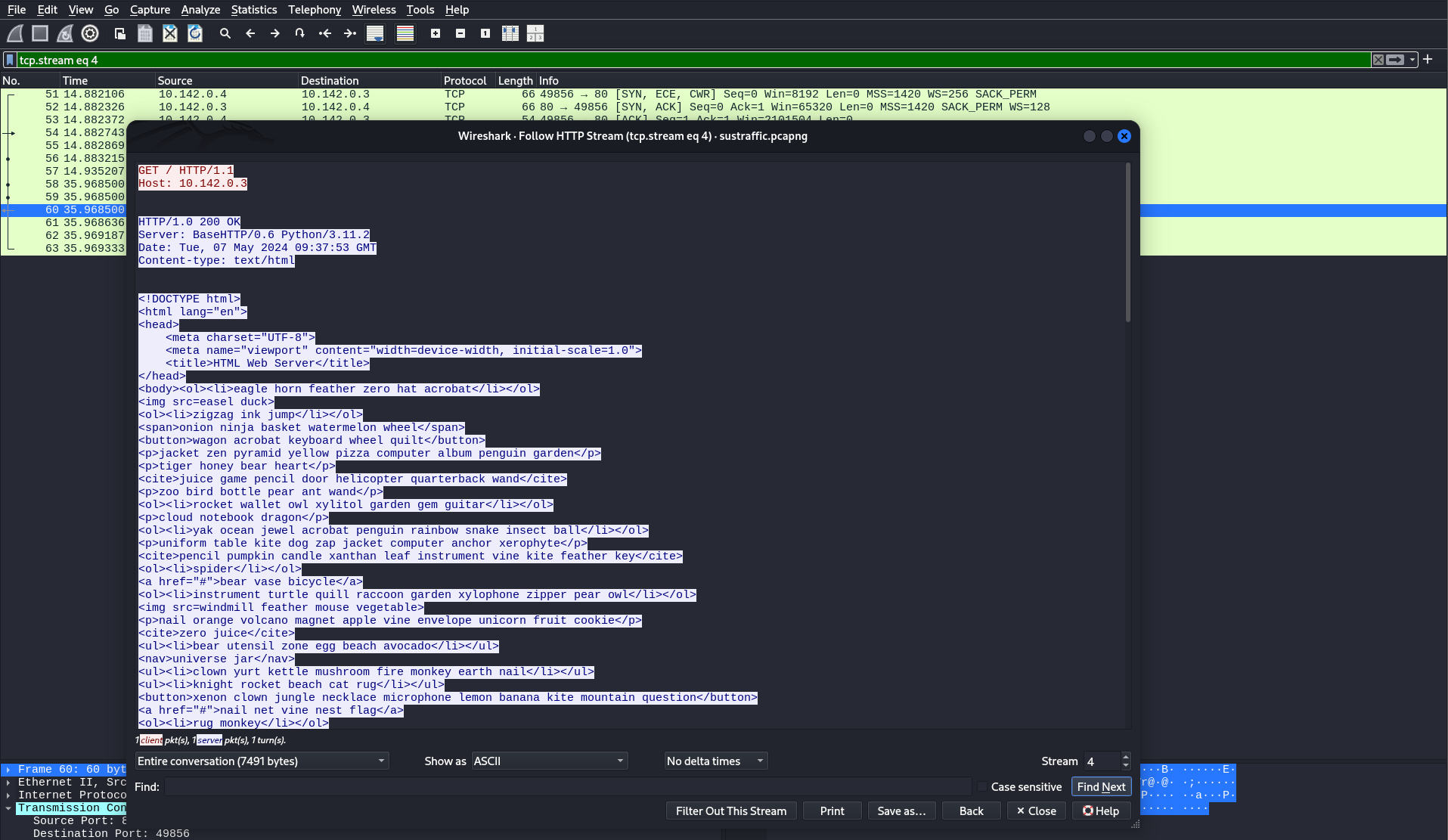
First, we open the sustraffic.pcapng file in Wireshark and then filter for http.response.
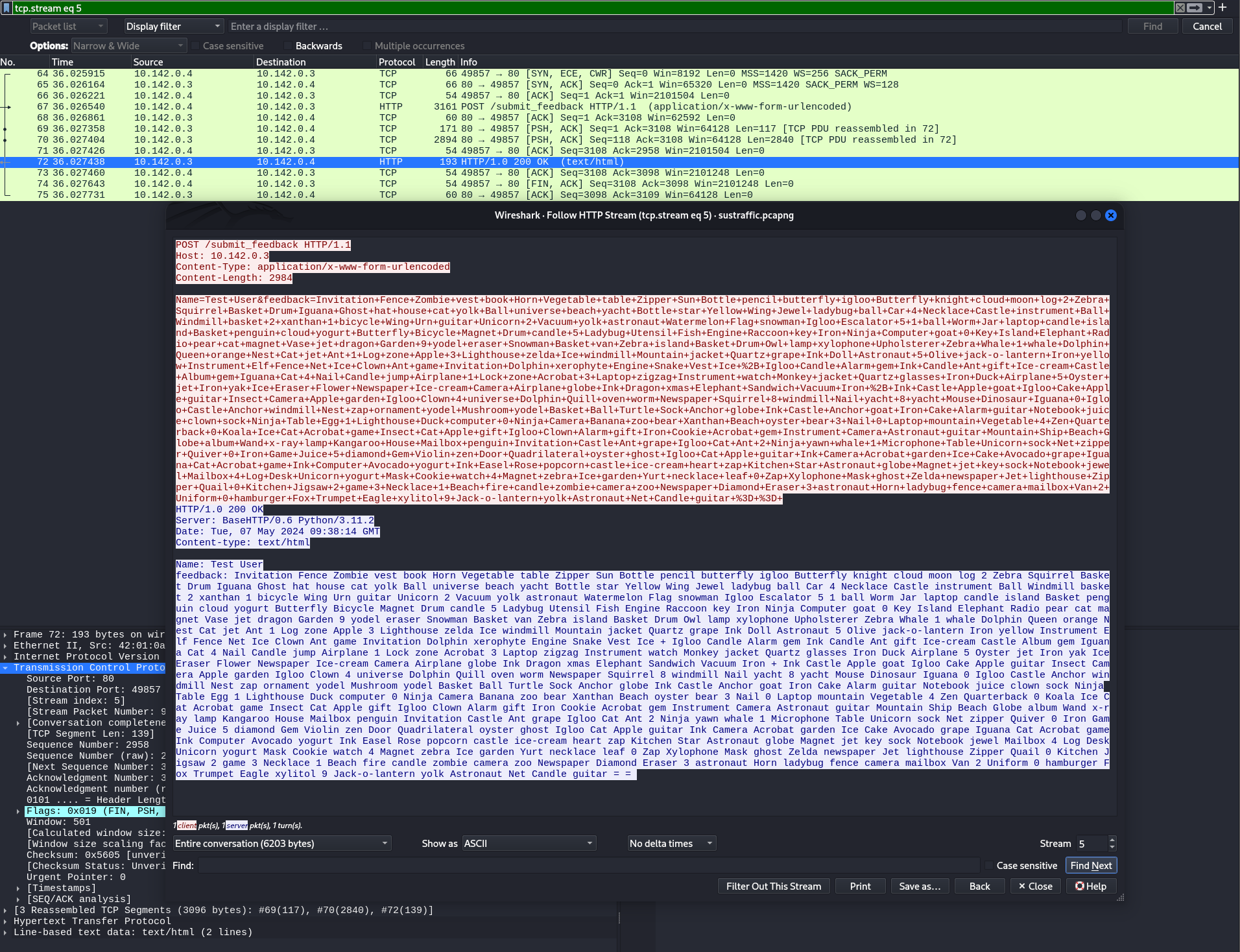
The packet that we are interested in is packet 72. Right click the packet and follow the HTTP stream.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
❯ cat sus_words.txt
Invitation Fence Zombie vest book Horn Vegetable table Zipper Sun Bottle pencil butterfly igloo Butterfly knight cloud moon log 2 Zebra Squirrel Basket Drum Iguana Ghost hat house cat yolk Ball universe beach yacht Bottle star Yellow Wing Jewel ladybug ball Car 4 Necklace Castle instrument Ball Windmill basket 2 xanthan 1 bicycle Wing Urn guitar Unicorn 2 Vacuum yolk astronaut Watermelon Flag snowman Igloo Escalator 5 1 ball Worm Jar laptop candle island Basket penguin cloud yogurt Butterfly Bicycle Magnet Drum candle 5 Ladybug Utensil Fish Engine Raccoon key Iron Ninja Computer goat 0 Key Island Elephant Radio pear cat magnet Vase jet dragon Garden 9 yodel eraser Snowman Basket van Zebra island Basket Drum Owl lamp xylophone Upholsterer Zebra Whale 1 whale Dolphin Queen orange Nest Cat jet Ant 1 Log zone Apple 3 Lighthouse zelda Ice windmill Mountain jacket Quartz grape Ink Doll Astronaut 5 Olive jack-o-lantern Iron yellow Instrument Elf Fence Net Ice Clown Ant game Invitation Dolphin xerophyte Engine Snake Vest Ice + Igloo Candle Alarm gem Ink Candle Ant gift Ice-cream Castle Album gem Iguana Cat 4 Nail Candle jump Airplane 1 Lock zone Acrobat 3 Laptop zigzag Instrument watch Monkey jacket Quartz glasses Iron Duck Airplane 5 Oyster jet Iron yak Ice Eraser Flower Newspaper Ice-cream Camera Airplane globe Ink Dragon xmas Elephant Sandwich Vacuum Iron + Ink Castle Apple goat Igloo Cake Apple guitar Insect Camera Apple garden Igloo Clown 4 universe Dolphin Quill oven worm Newspaper Squirrel 8 windmill Nail yacht 8 yacht Mouse Dinosaur Iguana 0 Igloo Castle Anchor windmill Nest zap ornament yodel Mushroom yodel Basket Ball Turtle Sock Anchor globe Ink Castle Anchor goat Iron Cake Alarm guitar Notebook juice clown sock Ninja Table Egg 1 Lighthouse Duck computer 0 Ninja Camera Banana zoo bear Xanthan Beach oyster bear 3 Nail 0 Laptop mountain Vegetable 4 Zen Quarterback 0 Koala Ice Cat Acrobat game Insect Cat Apple gift Igloo Clown Alarm gift Iron Cookie Acrobat gem Instrument Camera Astronaut guitar Mountain Ship Beach Globe album Wand x-ray lamp Kangaroo House Mailbox penguin Invitation Castle Ant grape Igloo Cat Ant 2 Ninja yawn whale 1 Microphone Table Unicorn sock Net zipper Quiver 0 Iron Game Juice 5 diamond Gem Violin zen Door Quadrilateral oyster ghost Igloo Cat Apple guitar Ink Camera Acrobat garden Ice Cake Avocado grape Iguana Cat Acrobat game Ink Computer Avocado yogurt Ink Easel Rose popcorn castle ice-cream heart zap Kitchen Star Astronaut globe Magnet jet key sock Notebook jewel Mailbox 4 Log Desk Unicorn yogurt Mask Cookie watch 4 Magnet zebra Ice garden Yurt necklace leaf 0 Zap Xylophone Mask ghost Zelda newspaper Jet lighthouse Zipper Quail 0 Kitchen Jigsaw 2 game 3 Necklace 1 Beach fire candle zombie camera zoo Newspaper Diamond Eraser 3 astronaut Horn ladybug fence camera mailbox Van 2 Uniform 0 hamburger Fox Trumpet Eagle xylitol 9 Jack-o-lantern yolk Astronaut Net Candle guitar = =
❯ cat extract_first_letter.py
import sys
def extract_first_letters_from_file(file_path):
try:
with open(file_path, 'r', encoding='utf-8') as file:
content = file.read()
words = content.split()
# print(f'words = {words}')
result = []
for word in words:
# Check if the word starts with a letter
if word[0].isalpha():
result.append(word[0])
else:
# Keep the symbol or number as-is
result.append(word)
return ''.join(result)
except FileNotFoundError:
print(f"Error: File '{file_path}' not found.")
except Exception as e:
print(f"An error occurred: {e}")
# Usage example: python extract_first_letters.py input.txt
if __name__ == "__main__":
if len(sys.argv) != 2:
print("Usage: python extract_first_letters.py <input_file>")
else:
file_path = sys.argv[1]
result = extract_first_letters_from_file(file_path)
if result is not None:
print("Result:", result)
❯ python3 extract_first_letter.py sus_words.txt
Result: IFZvbHVtZSBpbiBkcml2ZSBDIGhhcyBubyBsYWJlbC4NCiBWb2x1bWUgU2VyaWFsIE51bWJlciBpcyBBMDc5LUFERkINCg0KIERpcmVjdG9yeSBvZiBDOlxUZW1wDQoNCjA1LzA3LzIwMjQgIDA5OjIyIEFNICAgIDxESVI+ICAgICAgICAgIC4NCjA1LzA3LzIwMjQgIDA5OjIyIEFNICAgIDxESVI+ICAgICAgICAgIC4uDQowNS8wNy8yMDI0ICAwNzoyMyBBTSAgICAgICAgNjcsNTE1LDc0NCBzbXBob3N0LmV4ZQ0KICAgICAgICAgICAgICAgMSBGaWxlKHMpICAgICA2Nyw1MTUsNzQ0IGJ5dGVzDQogICAgICAgICAgICAgICAyIERpcihzKSAgMjksNjM4LDUyMCw4MzIgYnl0ZXMgZnJlZQ0KJ2g3N1BfczczNDE3aHlfcmV2U0hFTEx9JyANCg==
Now we can decode the text.
1
2
3
4
5
6
7
8
9
10
11
12
❯ base64 -d extracted_sus_words.txt
Volume in drive C has no label.
Volume Serial Number is A079-ADFB
Directory of C:\Temp
05/07/2024 09:22 AM <DIR> .
05/07/2024 09:22 AM <DIR> ..
05/07/2024 07:23 AM 67,515,744 smphost.exe
1 File(s) 67,515,744 bytes
2 Dir(s) 29,638,520,832 bytes free
'h77P_s73417hy_revSHELL}'
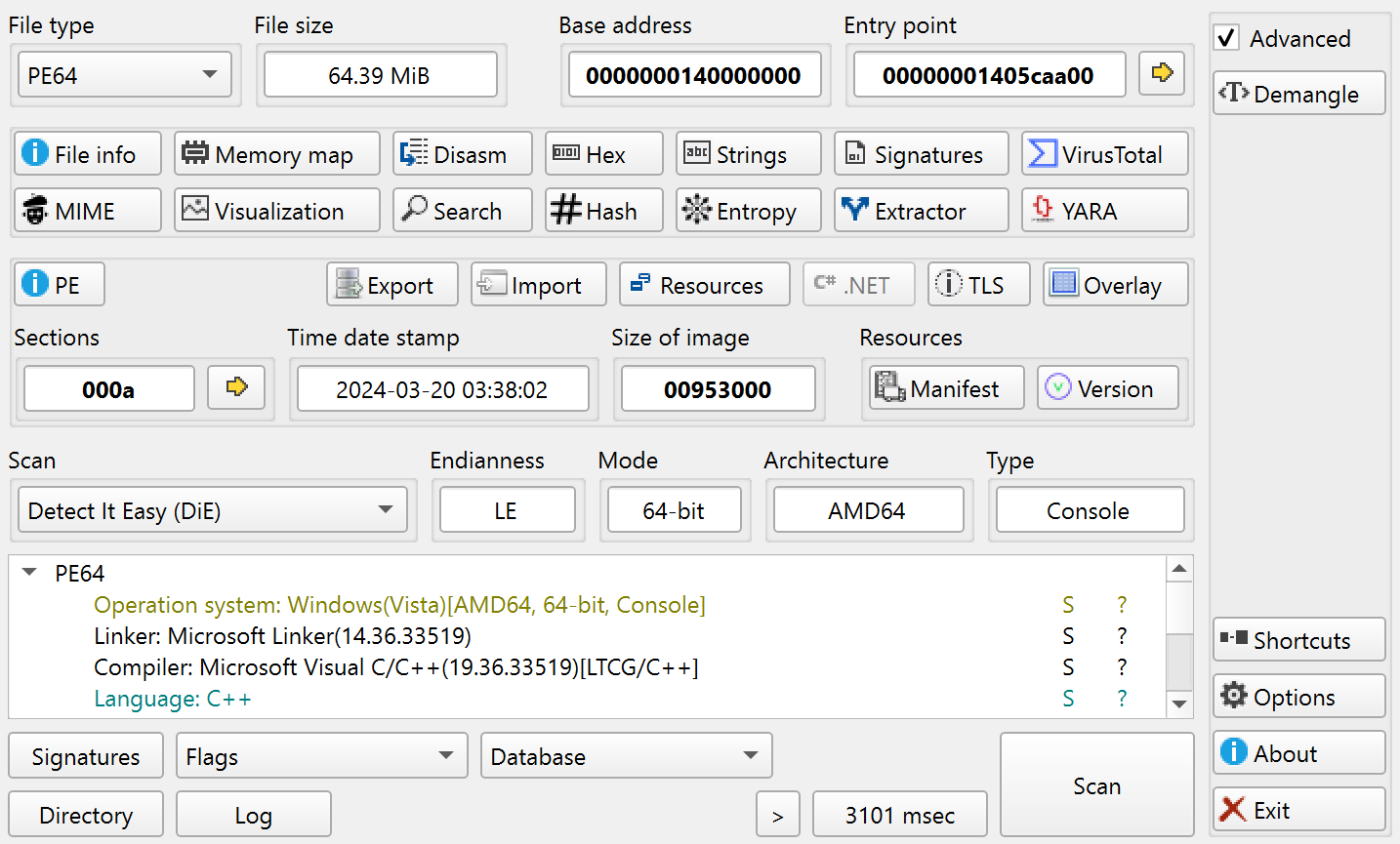
Putting the exe file in DetectItEasy shows that the file is a .NET executable.
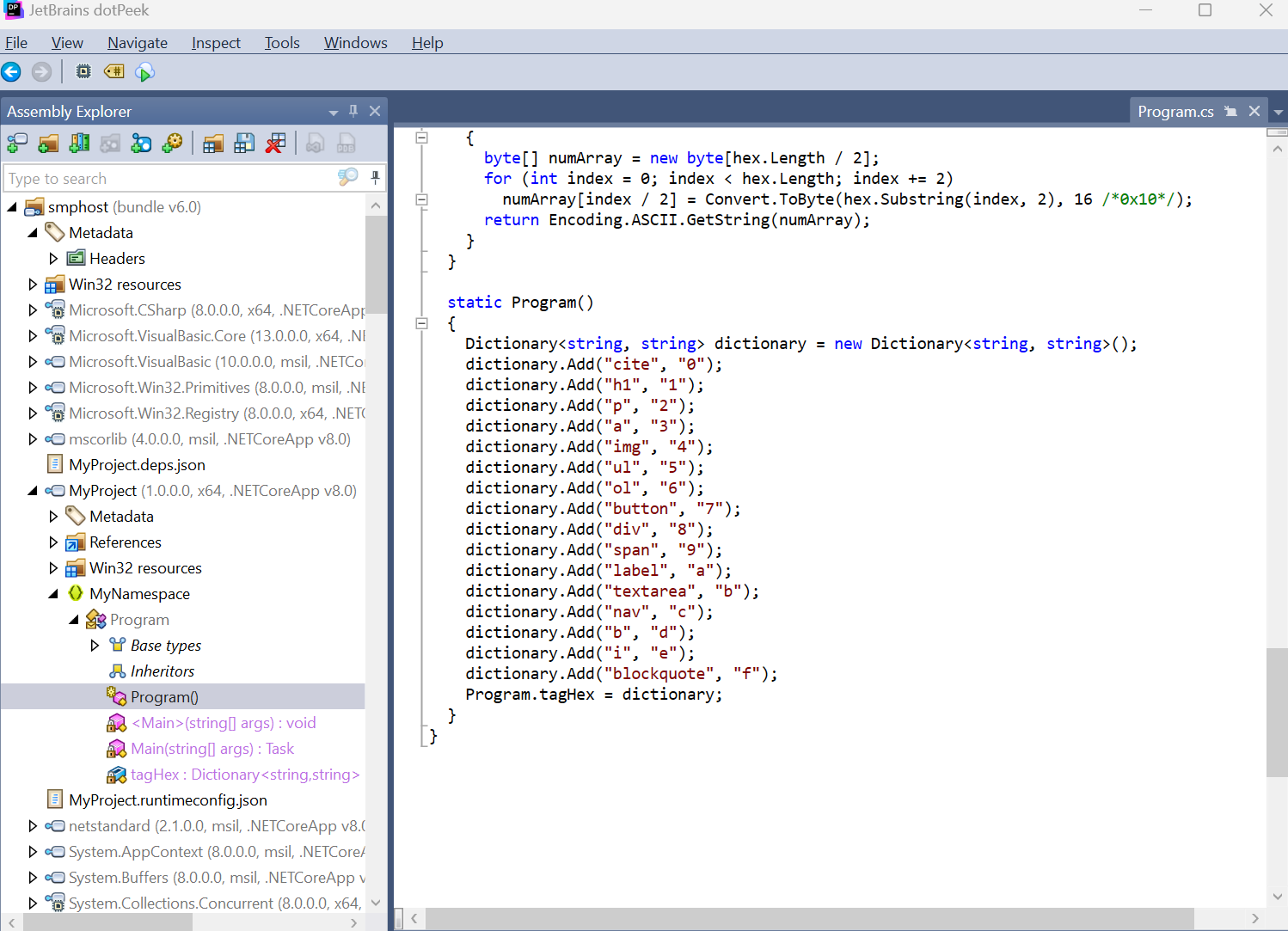
Putting the exe file into a .NET decompiler dotPeek shows us an interesting dictionary.
Lets go back to the pcapng to investigate for the usage of such values.
Packet 31 seems to fit the bill.
Lets copy the entire data into a file and create a python script that decodes the tags.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
❯ cat decode_tags_from_hex.py
import re
import sys
# Tag to hex mapping
tag_hex = {
"cite": "0", "h1": "1", "p": "2", "a": "3", "img": "4", "ul": "5", "ol": "6",
"button": "7", "div": "8", "span": "9", "label": "a", "textarea": "b", "nav": "c",
"b": "d", "i": "e", "blockquote": "f"
}
def decode_data(data):
decoded_str = ""
# Match opening tags and replace them with their corresponding hex values
matches = re.findall(r'<(\w+)[\s>]', data)
for match in matches:
if match in tag_hex:
decoded_str += tag_hex[match]
print("Hex String:", decoded_str)
try:
decoded_bytes = bytes.fromhex(decoded_str)
decoded_ascii = decoded_bytes.decode('ascii')
return decoded_bytes, decoded_ascii
except ValueError as e:
return f"Error decoding hex: {str(e)}", None
def decode_html(input_file):
try:
with open(input_file, 'r', encoding='utf-8') as f:
html_content = f.read()
except FileNotFoundError:
print(f"Error: File '{input_file}' not found.")
return None, None
return decode_data(html_content)
if __name__ == "__main__":
if len(sys.argv) != 2:
print("Usage: python3 file.py <input_file>")
sys.exit(1)
input_file = sys.argv[1]
decoded_bytes, decoded_html = decode_html(input_file)
if decoded_html:
print("\nDecoded ASCII:")
print(decoded_html)
print("\nDecoded Bytes:")
print(decoded_bytes)
else:
print("\nDecoding failed.")
❯ python3 decode_tags_from_hex.py hex_words.txt
Hex String: 646972202626206364205c55736572735c70616b6379626572626f745c446f63756d656e74735c2026262074797065204854427b54683474735f6430376e33375f
Decoded ASCII:
dir && cd \Users\pakcyberbot\Documents\ && type HTB{Th4ts_d07n37_
Decoded Bytes:
b'dir && cd \\Users\\pakcyberbot\\Documents\\ && type HTB{Th4ts_d07n37_'
Flag: HTB{Th4ts_d07n37_h77P_s73417hy_revSHELL}