The webpage is pretty simple - you type something in and it converts your text into a “spooky” font.
I noticed the URL has a ?text= parameter with our input. Anytime I see user input reflected in the response, especially with server-side processing, I think SSTI.
Threw in a quick test payload to check:
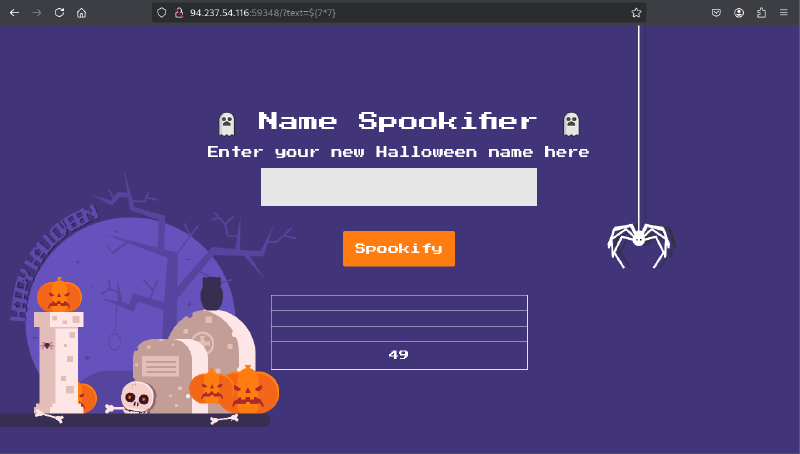
Bingo! SSTI confirmed. Now we just need to read the flag file. I tried ${system('cat flag.txt')} first but got a 500 error - probably sandboxed execution. Switched to Python’s open() function and it worked:
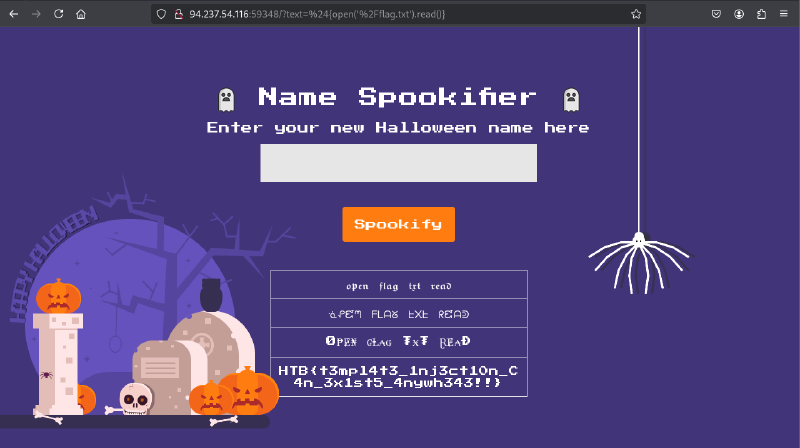
Flag: HTB{t3mpl4t3_1nj3ct10n_C4n_3x1st5_4nywh343!!}